Kubernetes security posture management (KSPM)
KSPM tools automate security and compliance for K8S environments.
Learn how Tenable Cloud Security KSPM, part of an identity-first cloud native application protection platform (CNAPP), accurately reveals, prioritizes and remediates security gaps in Kubernetes clusters across your cloud infrastructure.
Request a demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We'll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
More than 44,000+ organizations around the world rely on Tenable to help them understand and reduce cybersecurity risk
Cloud security that
fits your unique journey
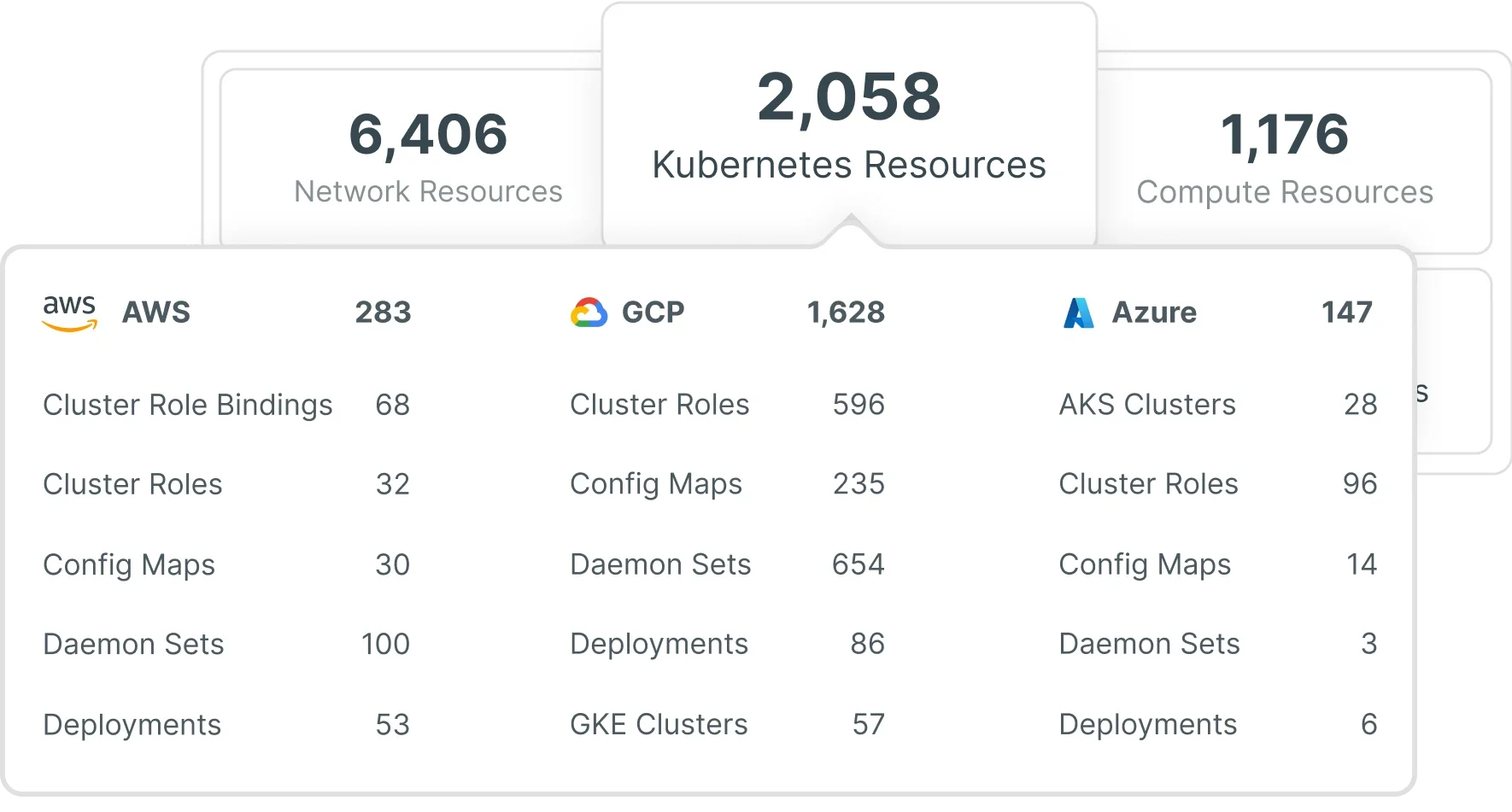
Enjoy a full, categorized asset inventory for AWS, Azure and GCP, letting you manage all cloud resources including workloads, identities, data, network and Kubernetes clusters, in one place. Continuously discover all resources in your environment and visualize them in a meaningful, multi-dimensional context.
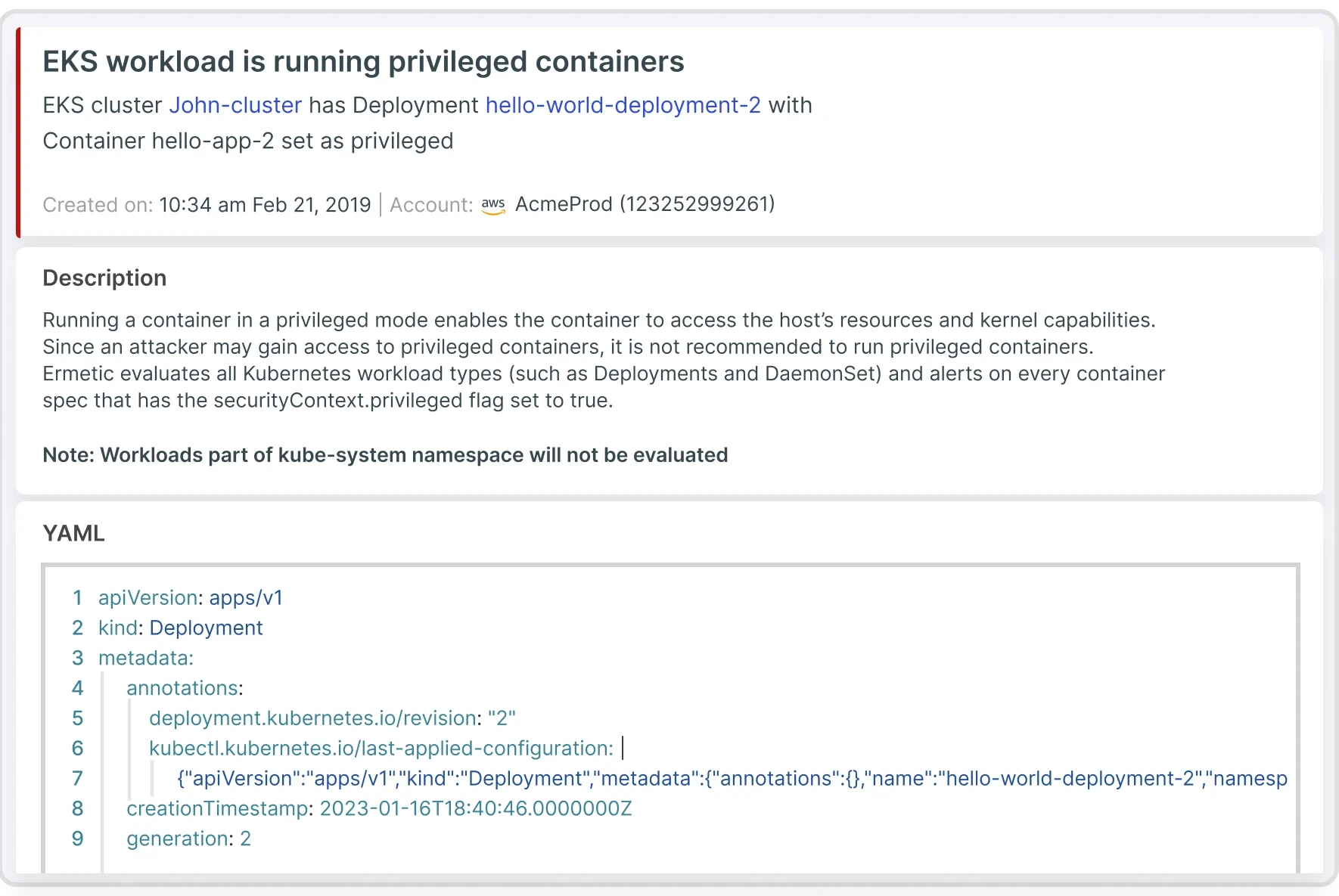
Get in touchLeverage full-stack risk analysis – including vulnerability scanning for containers – and guided remediation to the management of Kubernetes security posture. Contextualize container image scanning, visualizing network exposure, posture issues, IAM misconfigurations and other risks to prioritize which vulnerabilities potentially have the greatest impact.
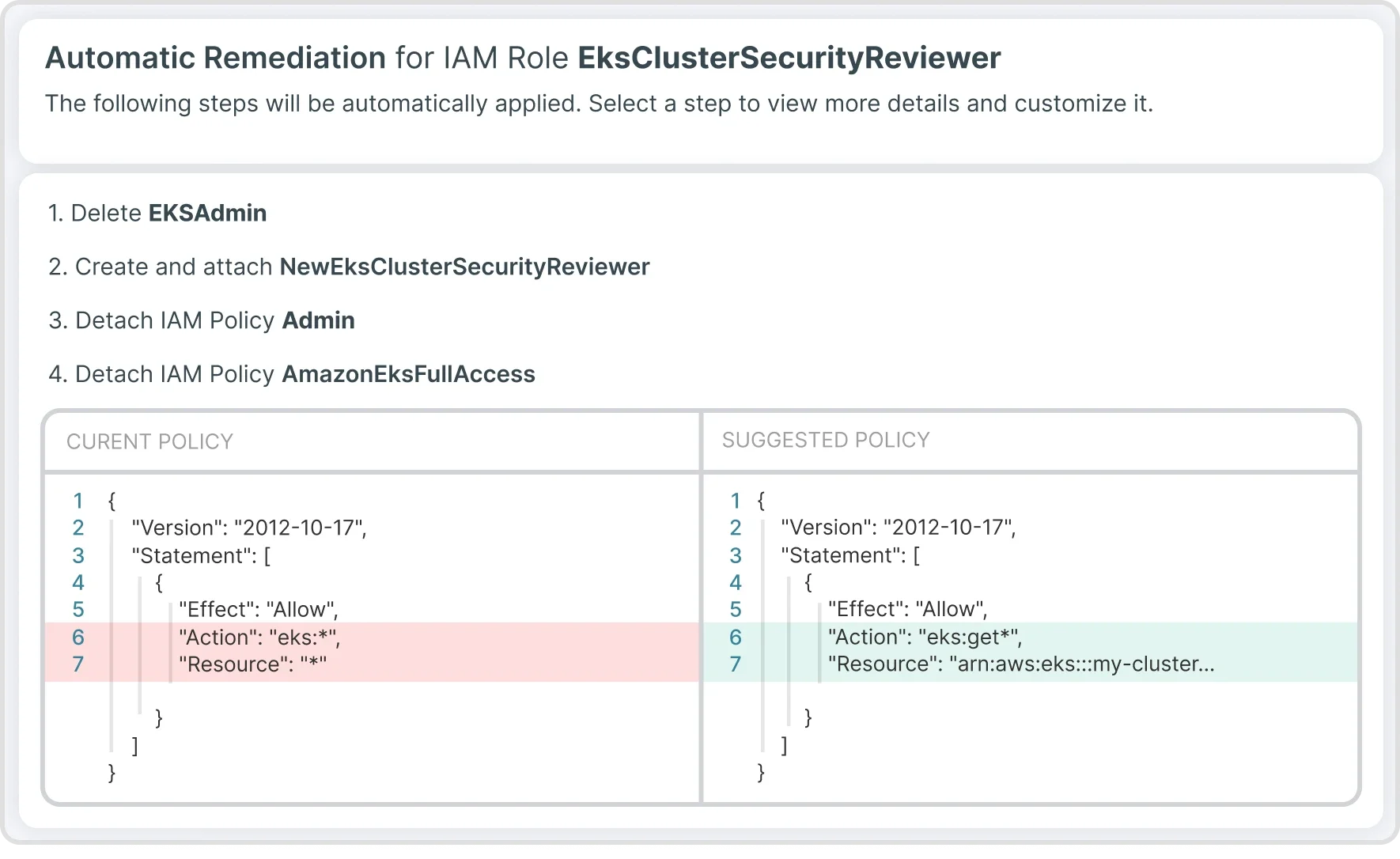
Get in touchTenable Cloud Security offers automated and guided remediation of misconfigurations, policy violations, and risky privileges within clusters and for the full cloud environment. Auto-remediate misconfigurations, policy violations, and risky privileges (including excessive and unused), in your multi-cloud environment.
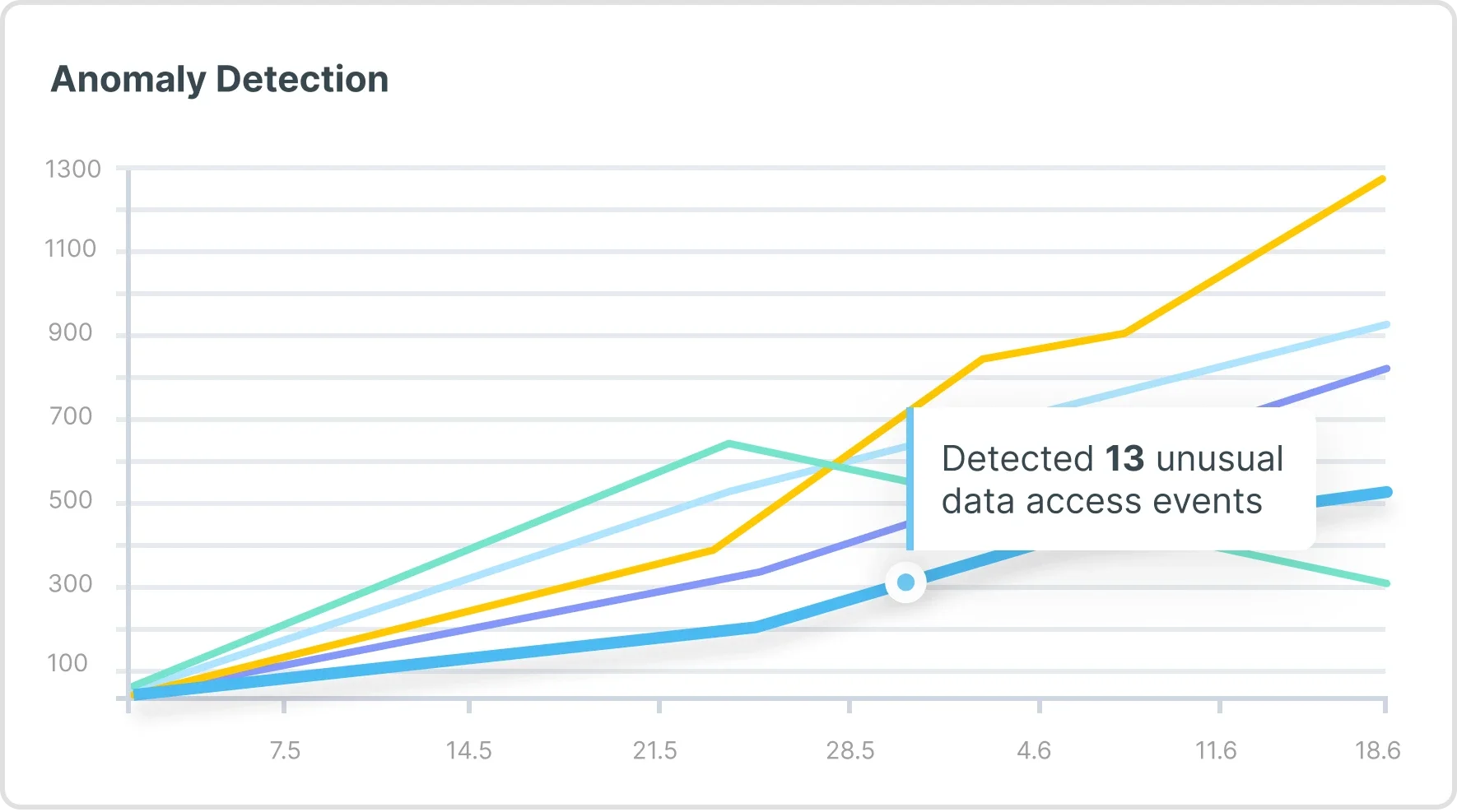
Get in touchAutomate threat detection of unusual activity through continuous risk analysis against behavioral baselines, helping identify anomalous and suspicious behavior that can endanger your most critical assets. Analyze cloud provider logs and correlate cloud threats with the underlying architecture to instantly reveal the context associated with each risk.
Get in touchContinuous multi-cloud compliance with tens of industry frameworks including CIS, GDPR, NIST, PCI-DSS, Kubernetes benchmarks and more, and custom checks. Produce detailed reports for internal compliance, external audit and daily security activities (e.g. asset inventory, misconfiguration, network configurations).
Get in touch