Modernize your defense and accelerate Zero Trust
Protect your mission with Tenable’s cyber risk solutions. Get unified visibility, vulnerability enumeration and prioritization and compliance reporting to reduce agency risk.

FedRAMP authorized and
CDM approved
Tenable Vulnerability Management and Web App Scanning are FedRAMP Moderate Authorized. Our products are approved for the General Services Administration’s (GSA) Continuous Diagnostics and Mitigation Program (CDM).

A cybersecurity platform for
federal agencies
Protect your mission with unified visibility to see, stop and close vulnerability exposures. Meet strict regulations and ensure compliance with Executive Orders, CISA Binding Operational Directives, FedRAMP certifications, NIST guidelines and more.
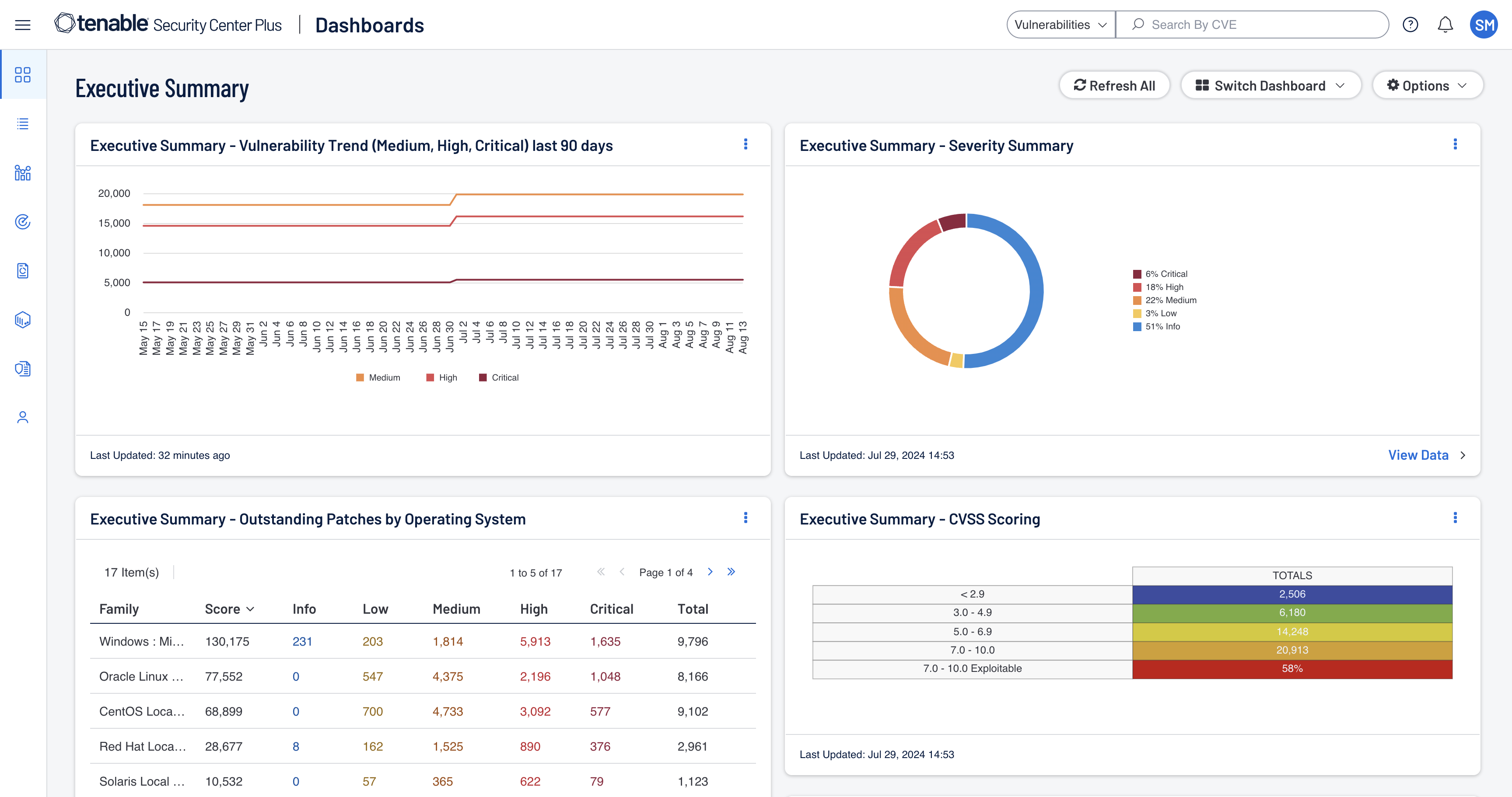
Discover your exposures and stop adversaries
Discovery is key. Discover, inventory and assess all assets and their vulnerabilities across your infrastructure- from IT to OT, container, web apps and identity systems.
Read the eBookSafeguard critical infrastructure
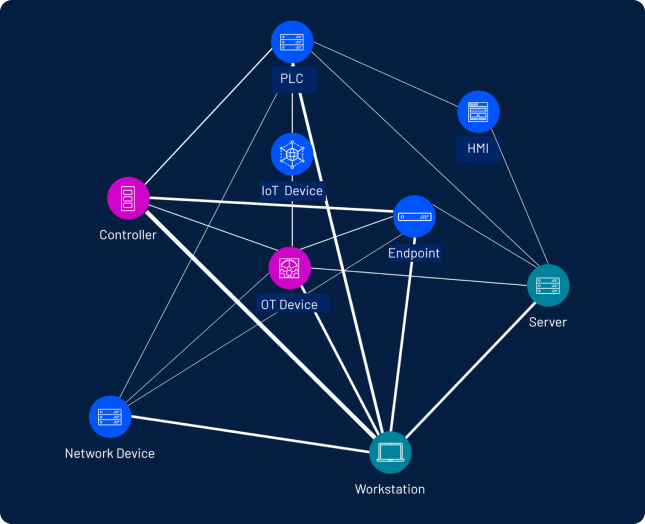
Ensure OT assets and cyber physical systems are secure and compliant. Adhere to federal mandates for safeguarding critical infrastructure with a unified IT/OT platform to close security blind spots and maximize the safety and reliability of federal OT environments.
Download the white paper View the infographicPreventive security integrated into your container ecosystem
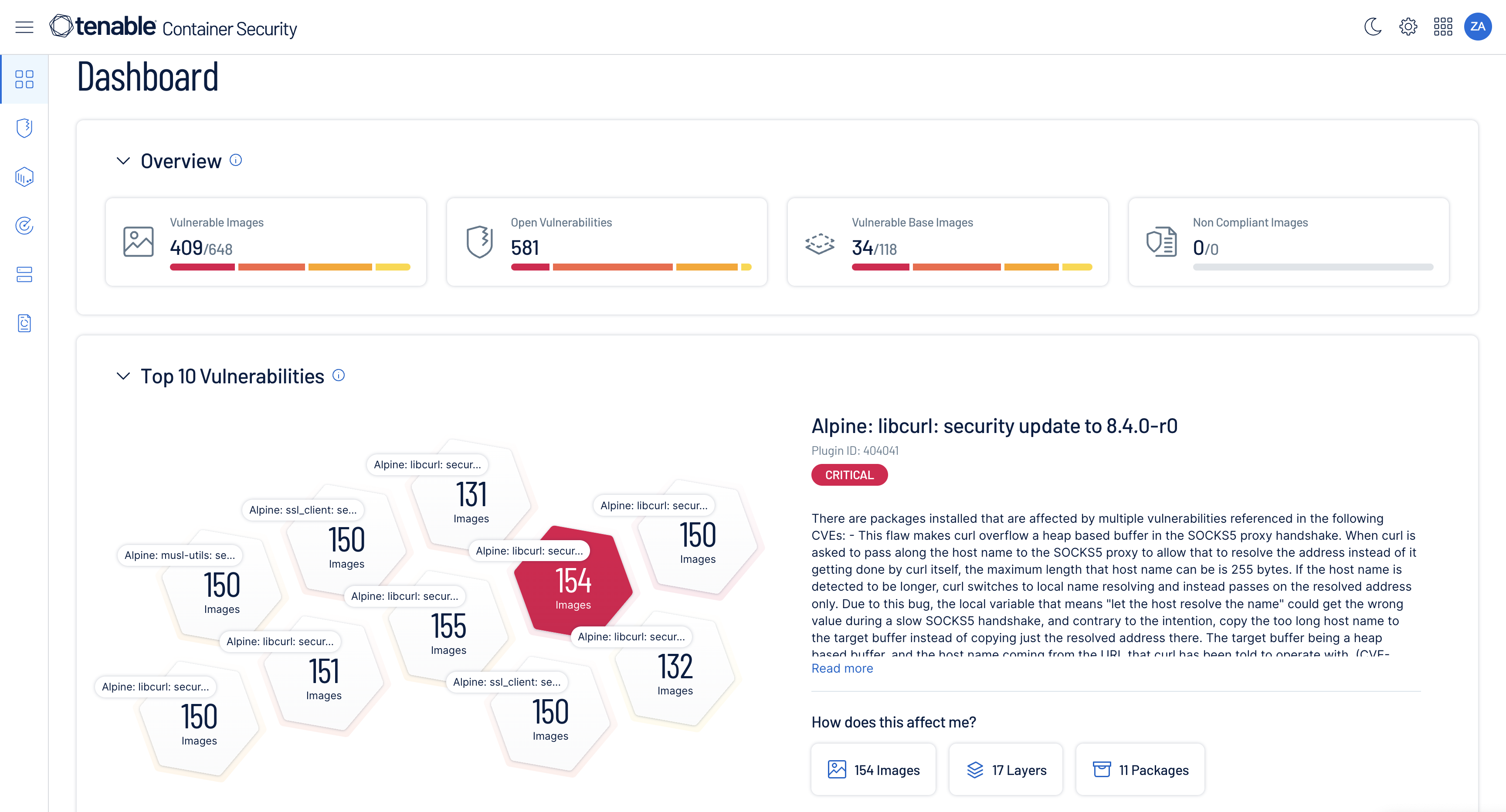
Understand your risk and expose vulnerabilities in container images with Tenable Enclave Security. Integrated container security makes it easy for DevOps teams to quickly fix container vulnerabilities before they hit production.
Read the datasheetAdvance your Zero Trust journey
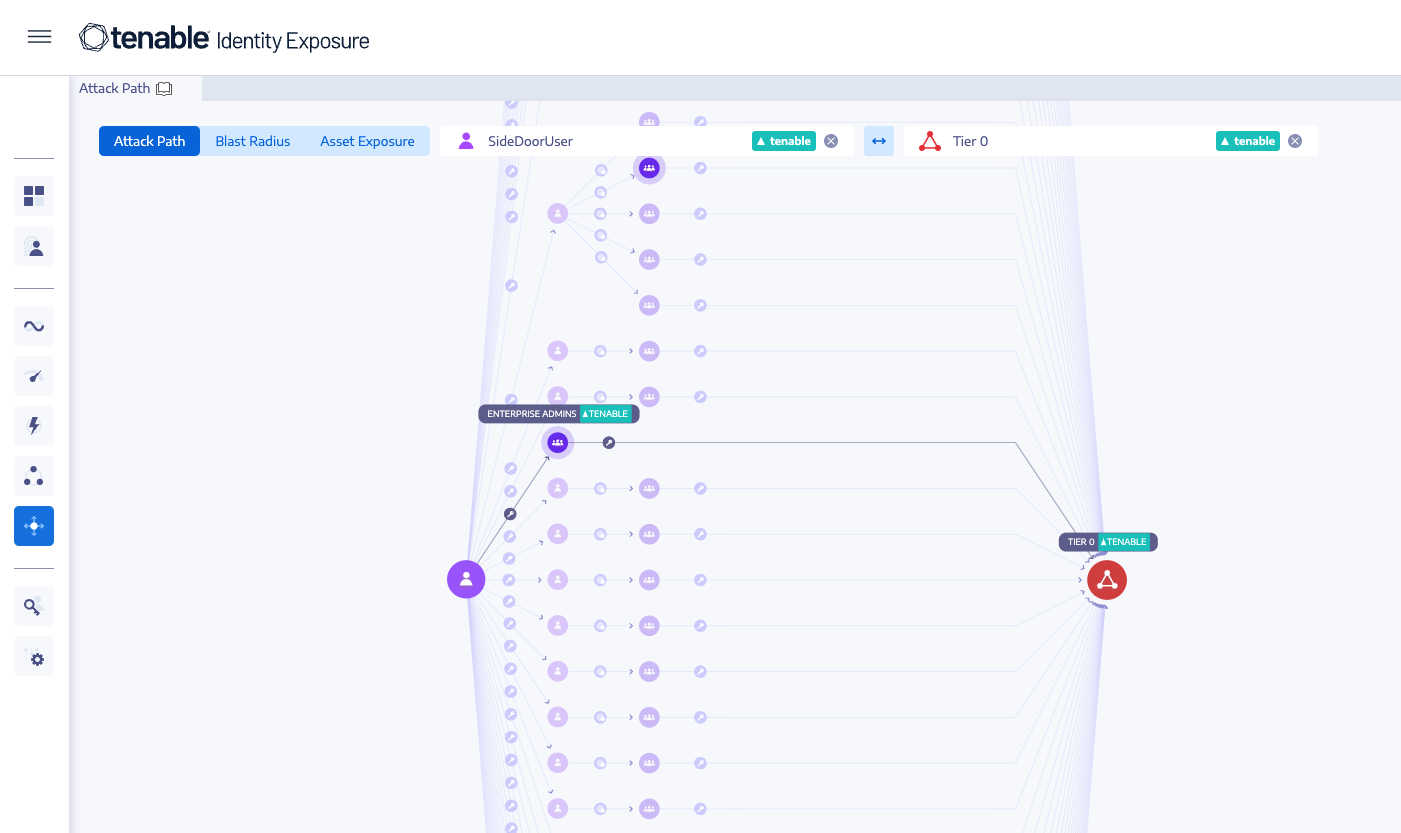
From providing foundational visibility into assets, users and vulnerabilities on your network, to securing your identity systems to prevent privilege escalation and lateral movement Tenable solutions fuel adoption and optimization across all Zero Trust pillars.
Read the white paper Download the solution briefIntroducing Tenable Enclave security
Know, expose and close IT and container vulnerabilities
Purpose built for secure environments
Supports the most stringent security requirements, including air-gapped, FedRAMP High and IL5. Deploy in commercial, on-prem or virtual private cloud environments.
Developer first container security
Detect and prevent insecure containers from being deployed to production. Scan registries, repositories, and CI/CD pipelines for full lifecycle visibility.
Unify siloed tools
Consolidate your security stack and centrally manage IT assets, containers, web applications and more from a single location.
Purpose built for secure environments
Supports the most stringent security requirements, including air-gapped, FedRAMP High and IL5. Deploy in commercial, on-prem or virtual private cloud environments.
Developer first container security
Detect and prevent insecure containers from being deployed to production. Scan registries, repositories, and CI/CD pipelines for full lifecycle visibility.
Unify siloed tools
Consolidate your security stack and centrally manage IT assets, containers, web applications and more from a single location.
Department of Defense
selected platform
Tenable was selected by DISA to power the Assured Compliance Assessment Solution (ACAS) program, protecting all DoD networks with vulnerability assessment and management, contextual insight, risk assessment and configuration and compliance auditing.
Learn more View the solution overview
Federal agency trusted partner
Tenable has a deep understanding of federal government needs and a history of transforming networks and reducing risk to federal agencies.
Industry leader in vulnerability research
Threat intelligence, data science insights, alerts and security advisories from the Tenable Research team integrated into all Tenable products.
Federal agency custom built templates
Generate preconfigured reports to prove compliance with federally mandated regulations and policies.
Accelerate
Zero Trust
Get visibility and assess risk across the five pillars of the Zero Trust Maturity Model.
Meet compliance mandates
Adhere to strict compliance mandates including Executive Orders, CISA Binding Operational Directives, NIST guidelines and more.
Related products
Related resources
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.
- Tenable Enclave Security
- Tenable Vulnerability Management
- Tenable Web App Scanning