Rethink security with a zero-trust approach
Adopt a zero-trust security strategy to proactively reduce the risk of lateral movement and data breaches across your attack surface.

Trust no one
Adopt a verify-everything strategy to eliminate attack paths and secure your organization against ransomware and other attacks.
Accelerate your zero-trust journey
Get foundational visibility into your attack surface to prioritize vulnerabilities and prevent attacks before they happen.

Trust depends on visibility
Visibility is at the foundation of zero trust. You can’t control access if you don’t know which assets, users and applications exist on your network.
Tenable exposure management solutions give you continuous visibility into all assets (and their vulnerabilities), across all attack surfaces — from IT to OT, code to cloud and Active Directory to Azure.
Learn more
Secure your hybrid identity infrastructure
Complex and evolving attacks put identity systems under increased pressure. As the foundation of a zero-trust strategy, protecting your hybrid identity infrastructure is critical to limiting lateral movement and enforcing least privilege access.
Tenable Identity Exposure safeguards Active Directory (AD) and Entra ID by:
- Uncovering misconfigurations and exposure points to fortify your identity systems.
- Detecting and responding to advanced attacks in real time.
- Enabling zero-trust principles with visibility, control and actionable insights.
Strengthen your zero-trust framework and protect your most critical systems with Tenable Identity Exposure.
Learn more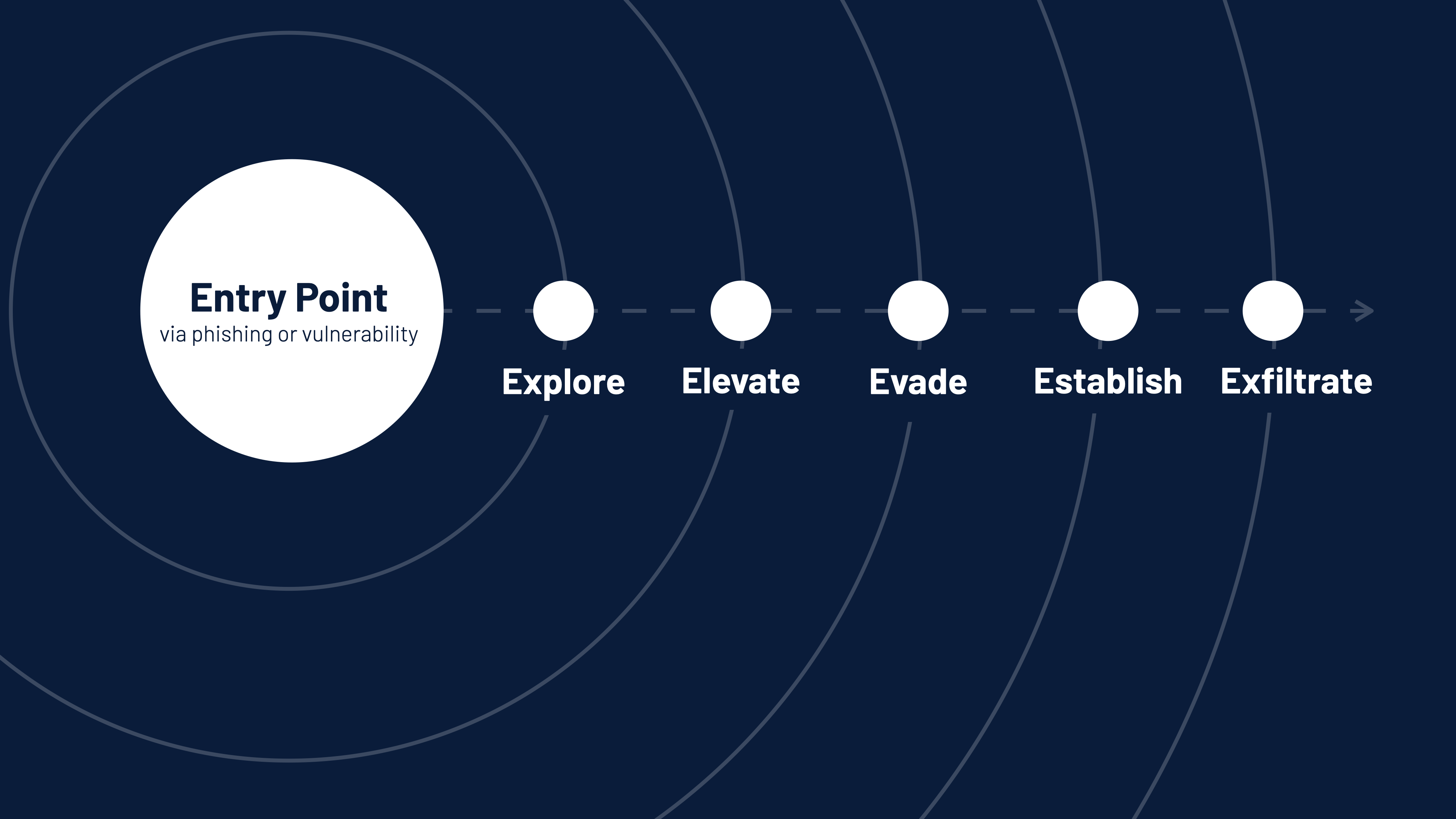
Prioritize based on risk
Proactive protection against ransomware, advanced threats and identity-based attacks starts with prioritizing risks across all areas of your environment.
The Tenable One exposure management platform provides risk-based prioritization across your entire attack surface — from IT and cloud, to identity systems like Active Directory (AD) and Azure. You can quickly identify which assets contain critical vulnerabilities, misconfigurations and excessive permissions along with access to detailed risk scores, asset criticality insights and identity exposure metrics. This holistic approach enables smarter trust decisions, ensuring you mitigate risks before threat actors can exploit them.
Learn moreKey business benefits
Related products
Related resources
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.
- Tenable Identity Exposure
- Tenable One
- Tenable Vulnerability Management