CVE-2019-3396: Vulnerability in Atlassian Confluence Widget Connector Exploited in the Wild

Attackers are targeting vulnerable Confluence instances after company published a fix for the vulnerability back in March 2019.
Background
On March 20, Atlassian published a Confluence Security Advisory to announce fixes for two vulnerabilities, CVE-2019-3395 and CVE-2019-3396.
CVE-2019-3395 is a critical server-side request forgery (SSRF) vulnerability in the WebDAV plugin in Confluence Server and Data Center versions released before June 18, 2018.
CVE-2019-3396 is a critical server-side template injection vulnerability in Confluence Server and Data Center Widget Connector that could lead to path traversal and remote code execution.
In the weeks since the publication of the advisory, attackers have been probing for and exploiting CVE-2019-3396 on vulnerable systems.
Analysis
On April 23, AlertLogic published a blog about attackers exploiting CVE-2019-3396 to install GandCrab ransomware. GandCrab was first spotted in January 2018 and distributed through the RIG and GrandSoft exploit kits. GandCrab has also been distributed through malicious spam emails.
On April 26, Trend Micro published a blog about the AESDDoS botnet leveraging CVE-2019-3396 to infect systems and launch distributed denial of service (DDoS) attacks against other hosts and even use the infected systems for cryptocurrency mining.
Proof of concept
Following Atlassian’s advisory for these vulnerabilities in March, proof-of-concept code began to appear throughout the early part of April [1, 2, 3, 4]. Soon after, in-the-wild attacks began.
Solution
Atlassian recommends upgrading to the latest version of Confluence, which is 6.15.1 at the time of publication.
- For users of 6.12.x versions prior to 6.12.3, upgrade to 6.12.3 or later and 6.14.x versions prior to 6.14.2, upgrade to 6.14.2 or later.
- For users of enterprise release versions 6.6.x prior to 6.6.12, upgrade to 6.6.12 or later and 6.13.x versions prior to 6.13.3, upgrade to 6.13.3 or later.
- For users of older versions from 1.x.x through 5.x.x and versions 6.0.x through 6.11.x, Atlassian recommends upgrading to 6.14.2, 6.13.3 or 6.6.12.
Identifying affected systems
A list of Nessus plugins to identify these vulnerabilities can be found here.
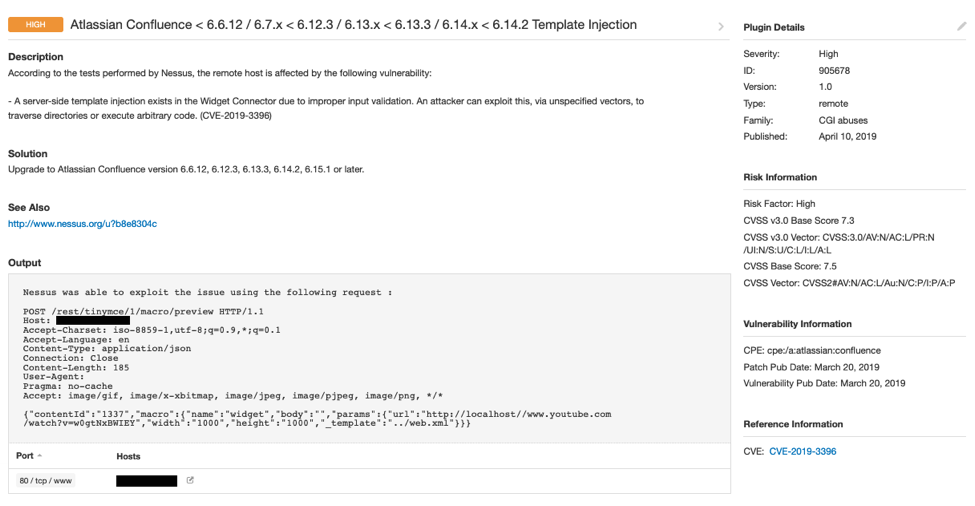
Below is a sample scan output for CVE-2019-3396.
Get more information
- Confluence Security Advisory - 2019-03-20
- Active Exploitation of CVE-2019-3396 Dropping Gandcrab Ransomware
- Trend Micro Blog on AESDDoS Botnet Malware
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
Related Articles
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning






