Gain Visibility Into Insider Activity and Uncover Insider Threats With Tenable SecurityCenter Continuous View
Data breaches associated with “insiders” – individuals considered trusted entities and granted privileged access to internal systems and data – are not the most common type of IT breach, but are one of the most costly with an estimated cost of over $400,000 per incident and an average victim loss of $15 Million/year1. The problem is so impactful that the FBI has a separate webpage dedicated to the topic.
Tenable Network Security helps organizations find and mitigate insider threats through its SecurityCenter Continuous View (SC CV) product. Tenable SC CV enables insider threat mitigation by taking a “whole picture” view of insider activity and leveraging its vulnerability scan, network monitoring and log analysis capabilities.
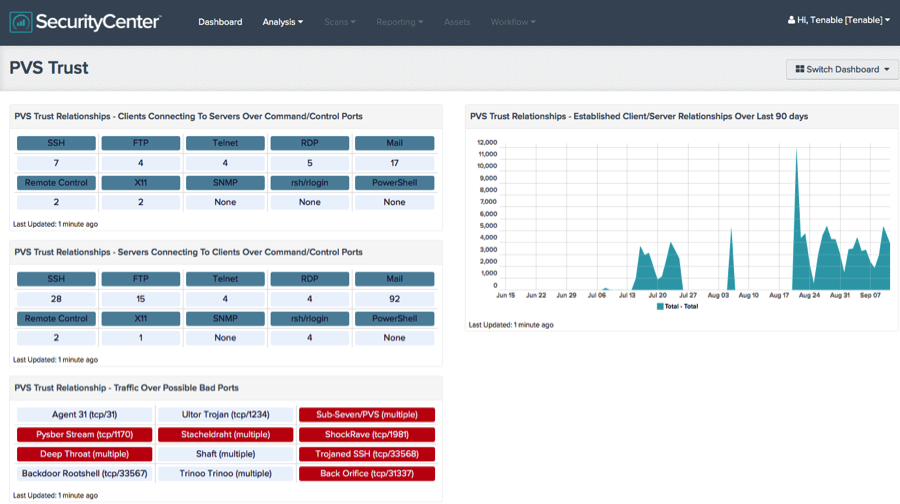
Tenable SC CV gathers intelligence about individuals, the user accounts they login with, the devices they use, the network paths they traverse, the applications they have established trust relationships and much more to build a comprehensive usage profile. Using this baseline information and then comparing to actual activity in real-time, SC CV can quickly identify anomalies in behavior and zero in on potential insider abuse before it can cause damage to the organization.
A complete discussion of Tenable’s Insider Threat Detection capability can be found here.
1 Source: Patrick Reidy, FBI presentation at BlackHat 2013
Related Articles
- Dashboards
- Insider Threats
- SecurityCenter






