Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps

Don’t miss OWASP’s update to its “Top 10 Risks for LLMs” list. Plus, the ranking of the most harmful software weaknesses is out. Meanwhile, critical infrastructure orgs have a new framework for using AI securely. And get the latest on the BianLian ransomware gang and on the challenges of protecting water and transportation systems against cyberattacks..
Dive into six things that are top of mind for the week ending Nov. 22.
1 - OWASP ranks top security threats impacting GenAI LLM apps
As your organization extends its usage of artificial intelligence (AI) tools, is your security team scrambling to boost its AI security skills to better protect these novel software products?
If so, then you might want to check out OWASP’s updated list of the main dangers threatening large language model (LLM) apps, which are popular generative AI apps that produce text, like ChatGPT.
OWASP — the Open Worldwide Application Security Project — released its first “Top 10 Risks for LLMs” last year. A significantly revised version of the list came out this week that OWASP says is based on a better understanding of LLM threats and use cases.
“The list guides developers, security professionals, and organizations as they prioritize their efforts to identify and mitigate critical generative AI application security risks,” reads an OWASP statement.
The new list, put together by the OWASP Top 10 for LLM Applications and Generative AI Project, seeks to help defenders secure generative AI LLM applications throughout their lifecycle, including development, deployment and management.

Each entry in the “OWASP Top 10 for LLM Applications 2025” report includes a description of the security risk; its different types; examples of attack scenarios; related frameworks and taxonomies; and more.
Here’s the list:
- Prompt injection
- Sensitive information disclosure
- Supply chain
- Data and model poisoning
- Improper output handling
- Excessive agency
- System prompt leakage
- Vector and embedding weaknesses
- Misinformation
- Unbounded consumption
“As LLMs are embedded more deeply in everything from customer interactions to internal operations, developers and security professionals are discovering new vulnerabilities — and ways to counter them,” reads the 45-page report.
For more information about AI security, check out these Tenable resources:
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood” (blog)
- “Know Your Exposure: Is Your Cloud Data Secure in the Age of AI?” (on-demand webinar)
- “Never Trust User Inputs -- And AI Isn't an Exception: A Security-First Approach” (blog)
- “Mitigating AI-Related Security Risks” (on-demand webinar)
- “How AI Can Boost Your Cybersecurity Program” (blog)
- “6 Best Practices for Implementing AI Securely and Ethically” (blog)
2 - 2024’s nastiest software weaknesses
Cybersecurity teams, take notice: The list of this year’s most critical software weaknesses is out, so that you can factor them into your vulnerability management and application security programs.
The “2024 CWE Top 25 Most Dangerous Software Weaknesses” rankings, published this week by the U.S. government, can also help software developers create safer applications. Meanwhile, procurement and risk managers can use the list when evaluating software vendors.
“Organizations are strongly encouraged to review this list and use it to inform their software security strategies,” reads a Cybersecurity and Infrastructure Security Agency (CISA) statement.
“Prioritizing these weaknesses in development and procurement processes helps prevent vulnerabilities at the core of the software lifecycle,” the statement adds.

Here are the top 10 software weaknesses for 2024:
- Improper neutralization of input during web page generation (“Cross-site scripting”) — CWE-79
- Out-of-bounds write — CWE-787
- Improper neutralization of special elements used in an SQL command (“SQL injection”) — CWE-89
- Cross-site request forgery (CSRF) — CWE-352
- Improper limitation of a pathname to a restricted directory (“Path traversal”) — CWE-22
- Out-of-bounds read — CWE-125
- Improper neutralization of special elements used in an OS command (“OS command injection”) — CWE-78
- Use after free — CWE-416
- Missing authorization — CWE-862
- Unrestricted upload of file with dangerous type — CWE-434
CISA compiled the list in collaboration with MITRE’s Homeland Security Systems Engineering and Development Institute (HSSEDI).
MITRE’s Common Weakness Enumeration (CWE) community project maintains a master list of software and hardware weaknesses that is updated three or four times per year. MITRE defines “weakness” as a condition that could contribute to the introduction of vulnerabilities.
The annual list of the top 25 software CWEs is a subset of the main list. Check out this page to learn about the methodology used to rank the year’s top 25 CWEs.
For more information about software security:
- “From Bugs to Breaches: 25 Significant CVEs As MITRE CVE Turns 25” (Tenable)
- “What is software security and why is it important?” (IEEE Computer Society)
- “Top 10 open source software security risks — and how to mitigate them” (U.K. National Cyber Security Centre)
- “4 Best Practices for Secure Application Development” (U.S. National Institute of Standards and Technology)
- “What is application security?” (TechTarget)
3 - DHS unveils secure AI framework for critical infrastructure
Those involved with artificial intelligence in critical infrastructure organizations have a new framework to help them safely develop and deploy AI.
Published by the U.S. Department of Homeland Security (DHS), the “Roles and Responsibilities Framework for Artificial Intelligence in Critical Infrastructure” outlines a set of voluntary tasks for five key types of participants in the adoption of AI in these organizations.
- Cloud and compute providers
- AI developers
- Critical infrastructure owners and operators
- Civil society, including research institutions, academia and professional associations
- Public sector
The framework aims to help evaluate how these players contribute across five areas of responsibility:
- Environment security
- Responsible design of systems and models
- Data governance implementation
- Safe and secure deployment
- Performance and impact monitoring
“This Framework intends to further AI safety and security in critical infrastructure, including the harmonization of safety and security practices, improve the delivery of critical services, enhance trust and transparency among entities, protect civil rights and civil liberties, and advance AI safety and security research,” reads the 35-page document.
For example, the table below illustrates how the framework envisions the responsibilities for cloud and compute providers, including reporting and managing vulnerabilities; ensuring data privacy and availability; and instituting best practices for access management.
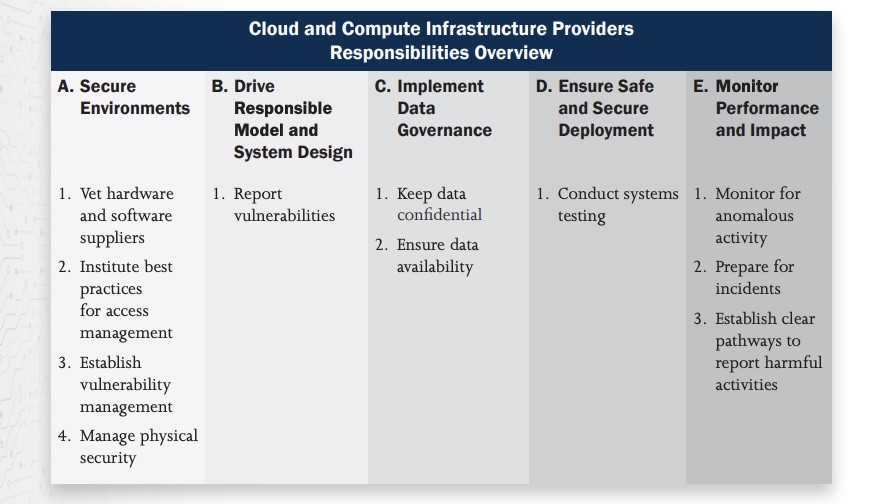
(Source: “Roles and Responsibilities Framework for Artificial Intelligence in Critical Infrastructure,” DHS, November 2024)
To get more details, check out:
- The full “Roles and Responsibilities Framework for Artificial Intelligence in Critical Infrastructure”
- The framework’s announcement “Groundbreaking Framework for the Safe and Secure Deployment of AI in Critical Infrastructure Unveiled by Department of Homeland Security”
4 - Report: Many U.S. water systems at risk from serious vulnerabilities
Vulnerabilities rated “critical” and “high” are present in the IT environments of 97 U.S. drinking water systems that collectively serve almost 27 million people, putting these systems at an elevated risk for cyberattacks.
That’s according to a report from the Environmental Protection Agency’s Office of Inspector General (OIG), whose findings are based on a passive assessment of the public-facing networks of about 1,000 drinking water systems.
“If malicious actors exploited the cybersecurity vulnerabilities we identified in our passive assessment, they could disrupt service or cause irreparable physical damage to drinking water infrastructure,” the report reads.

Another 211 drinking water systems have medium and low-risk vulnerabilities. Those facilities collectively serve almost 83 million people.
The vulnerabilities also put the drinking water facilities at risk for data theft, including of customer information and other confidential data. The OIG scanned the facilities’ public-facing networks in October of this year, analyzing about 75,000 IP addresses and almost 14,500 domains.
The findings highlight the challenges of securing critical infrastructure organizations’ IT networks against cyberthreats which could disrupt essential services for the general population, and, in this case, even compromise the safety of drinking water.
The OIG also found that the EPA lacks its own system that water and wastewater facilities can use to report cybersecurity incidents. It relies on CISA for this reporting capability.
For more information about securing operational technology (OT) systems in water plants, check out these Tenable resources:
- “Keep the Water Flowing for the DoD: Securing Operational Technology from Cyberattacks” (blog)
- “Tenable OT Exposure: Securing water facilities” (solution overview)
- “Safeguarding Your Water Utility” (on-demand webinar)
- “Enhancing Critical Infrastructure Cybersecurity for Water Utilities” (infographic)
- “The Constant Drip: EPA Water Regulations, Funding Sources, And How Tenable Can Help” (on-demand webinar)
5 - TSA proposes cyber requirements for rail, pipeline operators
New cybersecurity risk management (CRM) requirements may soon apply to rail and pipeline operators in the U.S.
The Transportation Security Agency (TSA) has proposed a set of rules aimed at enhancing the cybersecurity capabilities of freight railroads, passenger railroads, rail transit and pipeline facilities.
“The requirements proposed in this rule would strengthen cybersecurity and resiliency for the surface transportation sector by mandating reporting of cybersecurity incidents and development of a robust CRM program,” reads the TSA’s Notice of Proposed Rulemaking published in the Federal Register.

Specifically, the owners and operators of these rail and pipeline services would need to adopt a cybersecurity assessment program (CAP) approved by the TSA. The program would need to contain three core elements:
- An annual, enterprise-wide evaluation that compares the organization’s current cybersecurity capabilities with the target capabilities, which need to include outcomes outlined in the TSA’s proposed rules and in NIST’s Cybersecurity Framework.
- The development of a Cybersecurity Operational Implementation Plan (COIP) that includes:
- an identification of critical cybersecurity systems
- concrete measures to monitor and protect these systems
- specific measures to detect, respond to and recover from cyber incidents
- A schedule for assessments, an annual report of assessment results, and identification of unaddressed vulnerabilities.
The TSA expects that the cybersecurity risk-management requirements will include:
- Adopting patch management, system segmentation and firewalls
- Having backups to restore systems, recover data and continue operations
- Continuous network monitoring
- Drawing up an incident response plan
The proposed rules are open for public comment until February 5, 2025.
6 - New data released about BianLian ransomware group tactics
A U.S. government advisory about the BianLian ransomware gang has been updated with new information about its tactics, techniques and procedures (TTPs) and indicators of compromise (IoCs).
Likely based in Russia, BianLian is a “ransomware developer, deployer and data extortion cybercriminal group” that has attacked critical infrastructure organizations in the U.S. and Australia since mid-2022, according to the advisory.

Here’s how the advisory, updated this week and authored by CISA, the FBI and the Australian Cyber Security Centre, describes BianLian’s modus operandi:
- Access victims’ systems using valid Remote Desktop Protocol (RDP) credentials.
- Utilize open-source tools and command-line scripting to discover and harvest more credentials.
- Exfiltrate data via file transfer protocol (FTP) and other methods.
- Extort money from victims by threatening to release the stolen data.
The authoring agencies urge cybersecurity teams to take these actions immediately to protect themselves from BianLian cyberattacks:
- Strictly limit your use of Microsoft’s RDP and other similar remote desktop services.
- Disable command-line and scripting activities and permissions.
- Restrict PowerShell usage and update to the latest version of Windows PowerShell or PowerShell Core.
To get all the details about BianLian’s TTPs and IOCs, and about the mitigation recommendations, read:
- The CISA alert “CISA and Partners Release Update to BianLian Ransomware Cybersecurity Advisory”
- The full, updated advisory “#StopRansomware: BianLian Ransomware Group”
For more information about ransomware:
- “Ransomware Is ‘More Brutal’ Than Ever in 2024” (Wired)
- “Ransomware on track for record profits, even as fewer victims pay” (SC Magazine)
- “How Can I Protect Against Ransomware?” (CISA)
- “How to prevent ransomware in 6 steps” (TechTarget)
- “Steps to Help Prevent & Limit the Impact of Ransomware” (Center for Internet Security)
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- OT Security
- Risk-based Vulnerability Management


