Reduce runtime alert noise
with IaC security testing
Leverage pre-built policies to secure all types of infrastructure as code (IaC)
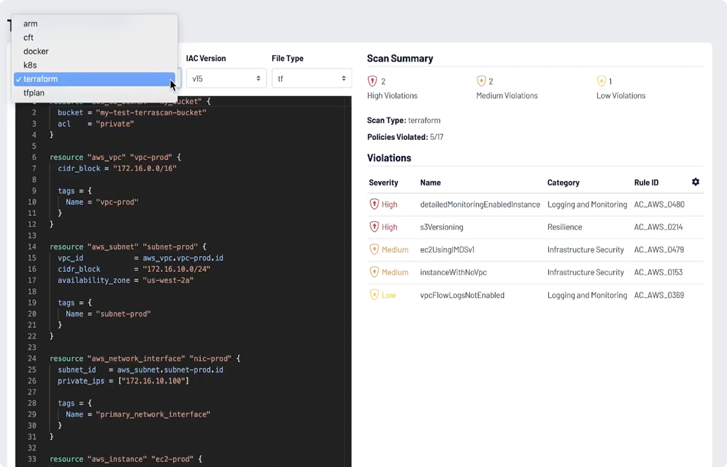
Detect misconfigurations and other security policy violations across infrastructure as code (IaC) to mitigate risk before production release.
See howThis 45-second video shows how Terrascan prevents cloud security issues by scanning code that provisions cloud infrastructure.
Stop policy violations at the source
As you embrace cloud-native tools such as Terraform, Kubernetes, Helm and AWS CloudFormation, it is important to ensure you’re adhering to security best practices and compliance requirements.
Shift left and reduce risk with
IaC security
Integrate cloud IaC security into your trusted tools
Enforcing security and compliance policies throughout the development lifecycle is necessary to minimize risks and scale cloud adoption. You can integrate Terrascan into your GitOps pipelines to scan IaC from code repositories such as GitHub, Bitbucket and GitLab. It can also act as a guardrail during the CI/CD phase to detect violations and block risky deployments. Terrascan is included in Nessus, which enables Nessus users to expand the scope of their security assessments to include validation of modern cloud infrastructure before deployment.
Learn moreEmpower developer teams to validate configurations
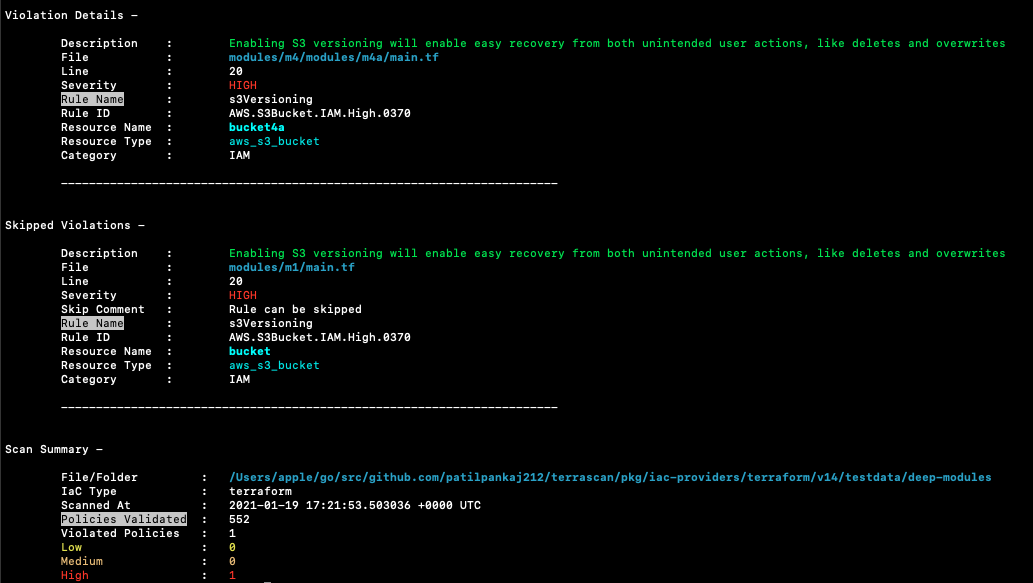
Terrascan provides a hassle-free way for your developers to run IaC security tests as part of local build processes when they are easiest and cheapest to fix. Policy as code (PoC) hardens configurations and provides an easy way to automate the process of detecting misconfigurations. Simply plug Terrascan into your workflows and it will automatically examine your configurations for common problems so you don’t need to do it manually.
Learn moreContribute and join the Terrascan community
Terrascan provides more than 500 out-of-the-box policies so you can scan IaC against common policy standards such as the CIS Benchmark. It leverages the Open Policy Agent (OPA) engine so you can easily create custom policies using the Rego query language.
With more than 4,000 GitHub stars and counting, users all over the world have developed Terrascan, bringing together the brightest minds in cloud security to create a scalable and functional project for safer cloud infrastructure. As a Cloud Native Computing Foundation (CNCF) member project, Terrascan thrives on community collaboration.
Learn moreLearn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security
 AWS
AWS Azure
Azure Google Cloud
Google Cloud