Business at the Speed of Cloud Tenable Cloud Security
At Tenable Cloud Security we work hard to constantly provide innovative and actionable features for our customers in order to easily and rapidly boost their cloud security. Tenable Cloud Security CNAPP secures the full cloud stack from infrastructure, to workloads, identities, data and AI resources. Learn more about our latest cloud security innovations below.
What's new
Eliminate standing permissions and reduce cloud risk with time-bound, on-demand access—now part of Tenable Cloud Security. No separate procurement needed!
To fully secure the cloud, identities must also be secured. This is achieved by enforcing least-privilege access for both human and machine identities. Tenable Cloud Security is the only CNAPP in the market that integrates the two critical capabilities required to enforce least-privilege access in the cloud: CIEM and Just-in-Time access (JIT). Tenable customers can now use their existing (or future!) Tenable Cloud Security license to enable and use JIT.
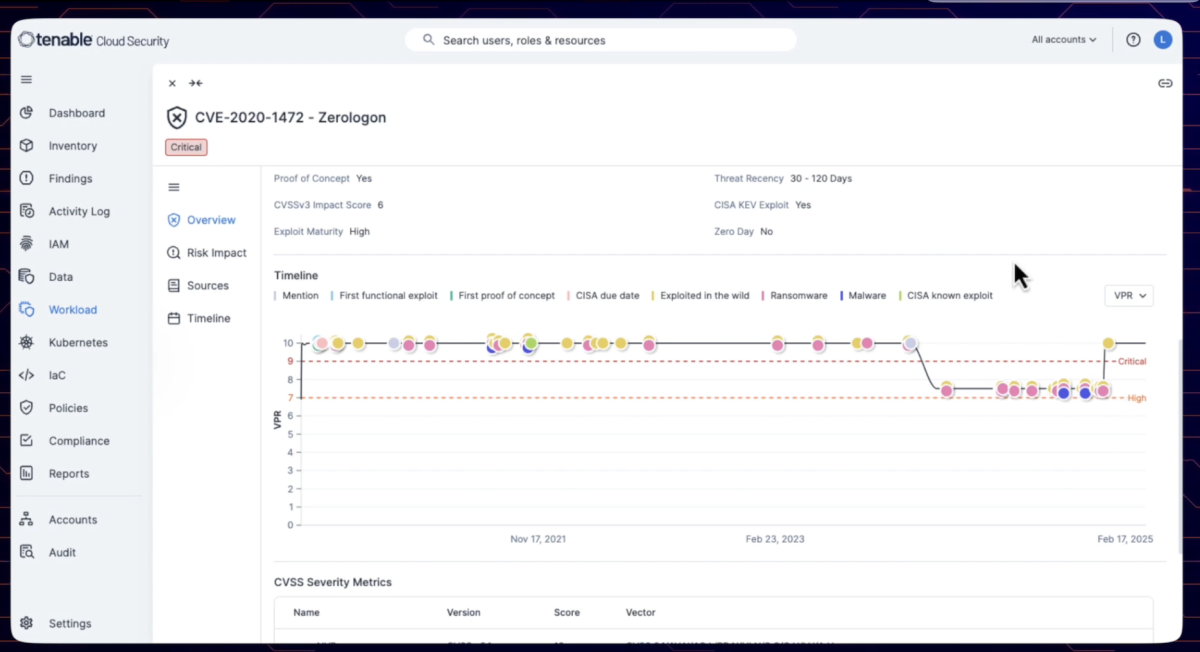
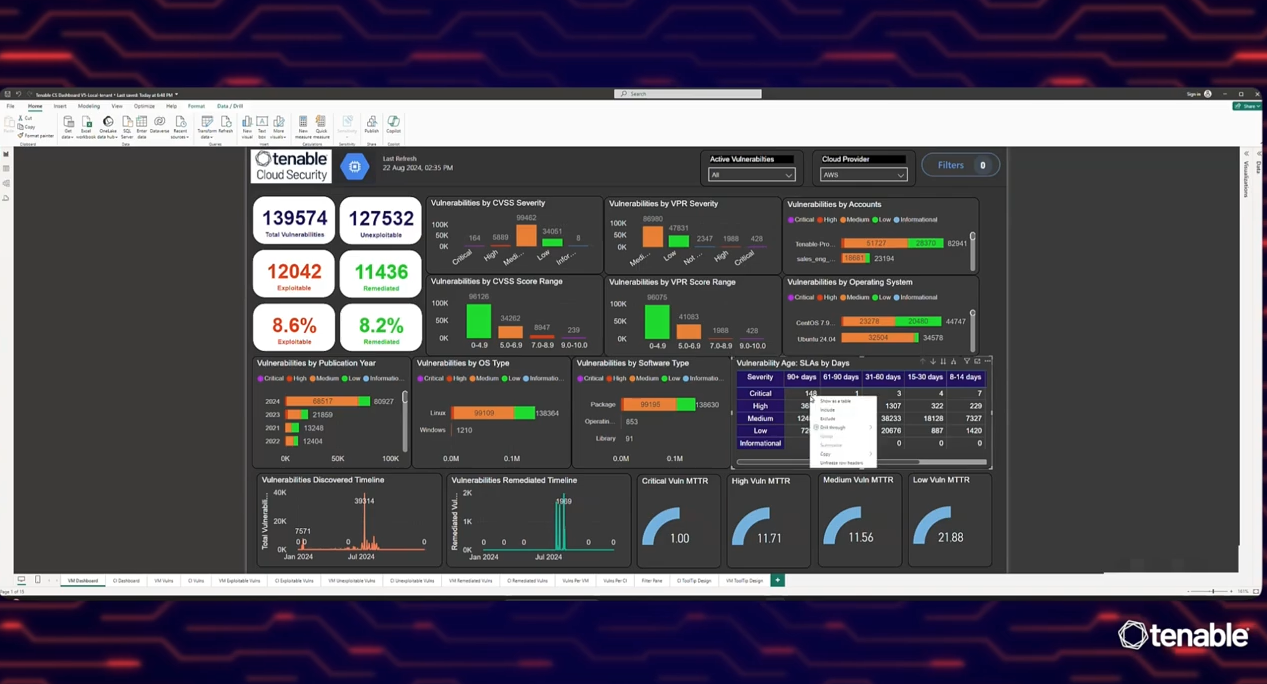
Managing vulnerabilities in cloud workloads just got smarter with Tenable Cloud Security’s new and improved vulnerability profile ! Easily look up vulnerabilities by ID or name and get in-depth insights, including threat factors, exploit maturity, and real-time security ratings like EPSS and VPR. Track vulnerabilities over time with a detailed timeline of relevant key events for each of them, from first discovery to real-world exploits. Plus, understand exactly how vulnerabilities impact your organization by pinpointing affected VMs and containers, along analysis of security findings, access management, and even cloud activity logs—all in one place! See how Tenable Cloud Security helps you simplify and strengthen your cloud workload protection.
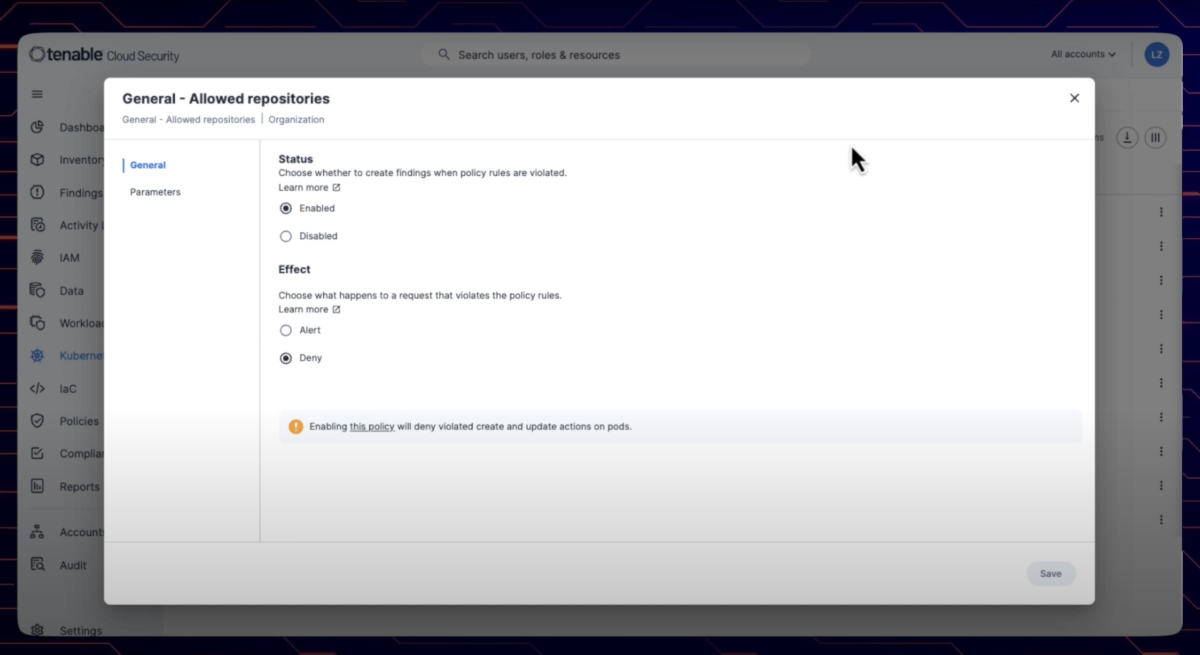
Admission controllers are a great feature in K8s clusters for shifting left the enforcement of security policies, but the learning curve for using them confidently may deter from using them at scale. For this reason Tenable Cloud Security now provides the ability to easily install and manage admission controllers on onboarded K8s clusters allowing to easily enable / disable policies, set them to deny changes or simply alert on them, edit policy variables without writing or knowing rego and intuitively consuming logs of policy violations.
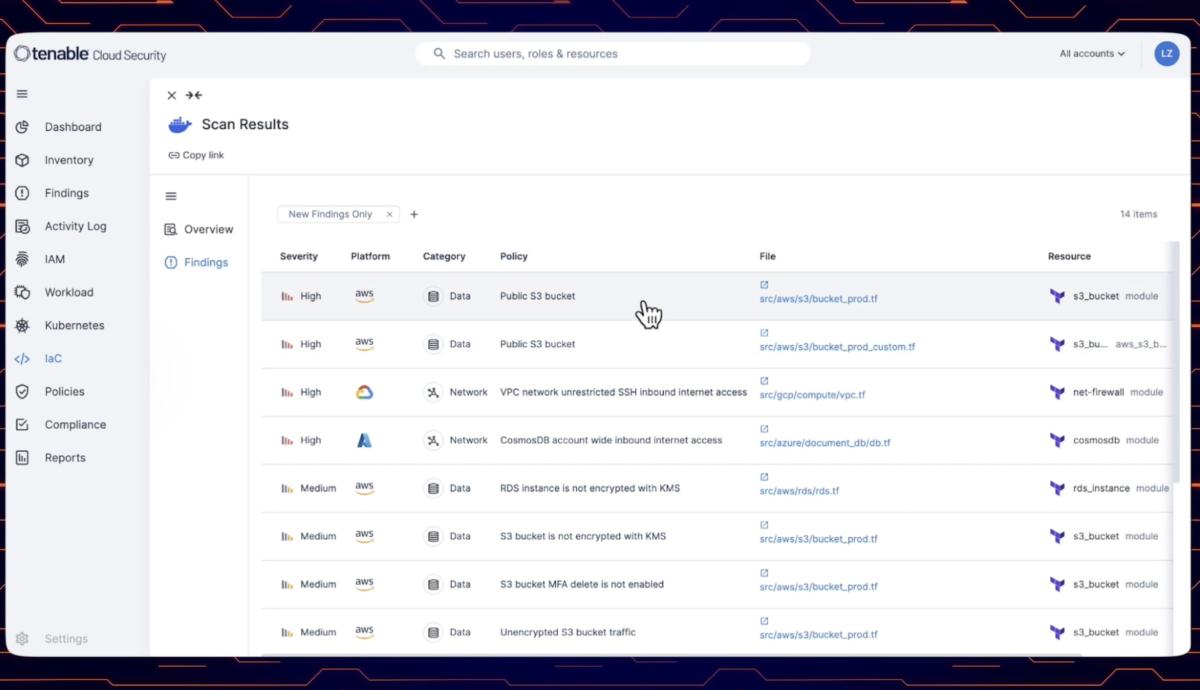
Most people have heard about shifting security left by scanning infrastructure as code for misconfigurations, but, did you know that infrastructure provisioning code can itself be malicious? As part of recent research done by one of our senior researchers, Shelly Raban - she was able to create a proof-of-concept and show how certain Terraform commands can leak sensitive data - even before hitting "apply"!
Learn all about this attack vector, how it can affect your environments and how you can use Tenable Cloud Security in order to detect it.
You can also read the release notes.
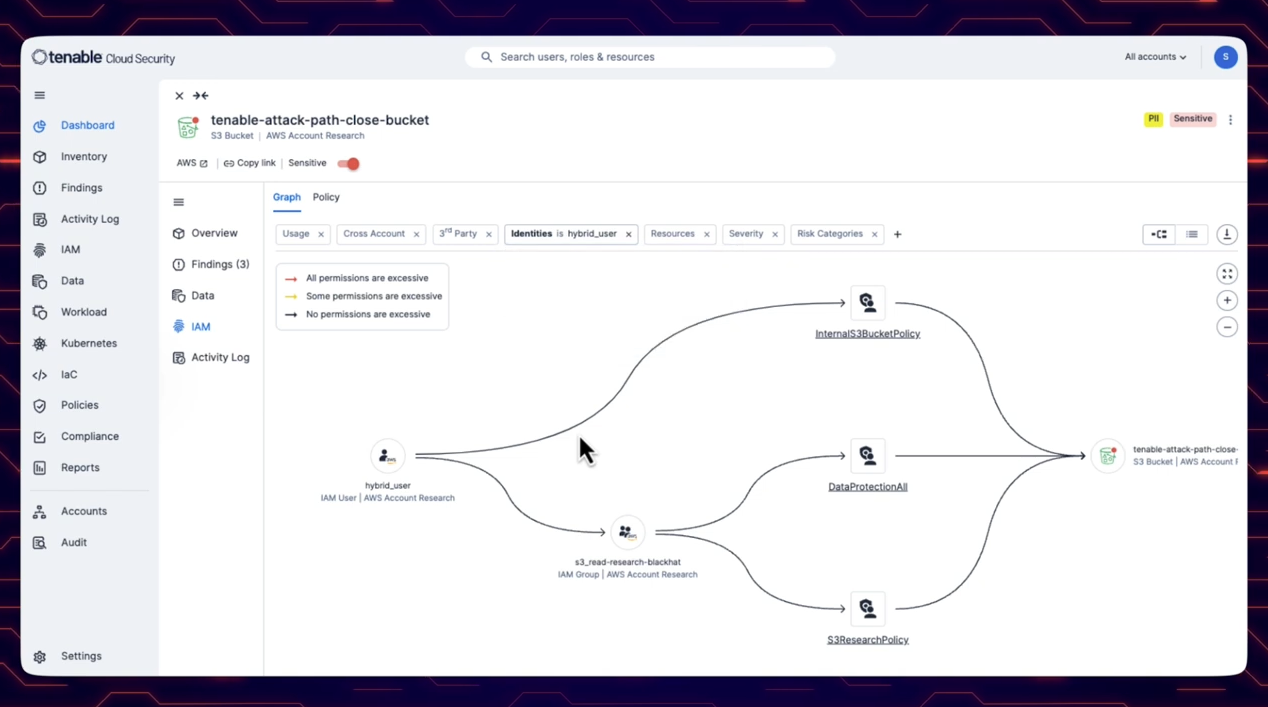
We are excited to announce the release of cloud attack path analysis with Tenable One! Tenable Cloud Security isn't just cloud security. It's part of the larger Tenable exposure management ecosystem - and that can make a world of difference. As risks don’t live in silos and adversaries don’t attack in a box, being able to use solutions from one vendor for different types of infrastructure (on-prem, cloud, OT, ...) to detect potential attack paths is crucial. Watch this short demo video to learn how the Tenable One platform unifies insights to clearly illustrate potential attack paths that may expose sensitive data and mission critical resources.
Tenable Cloud Security now offers a powerful vulnerability scanning API, designed to help cloud security teams tailor their vulnerability management processes. In this demo, we showcase how one of our strategic customers uses the API to track vulnerabilities, query detection and remediation times, and visualize the data in a customized dashboard. Learn how they effortlessly track critical metrics like Mean Time to Remediation, and leverage the Tenable Cloud Security console for deep insights into their cloud workloads. This API empowers you to build flexible solutions that meet your unique cloud security needs, with ease and clarity.
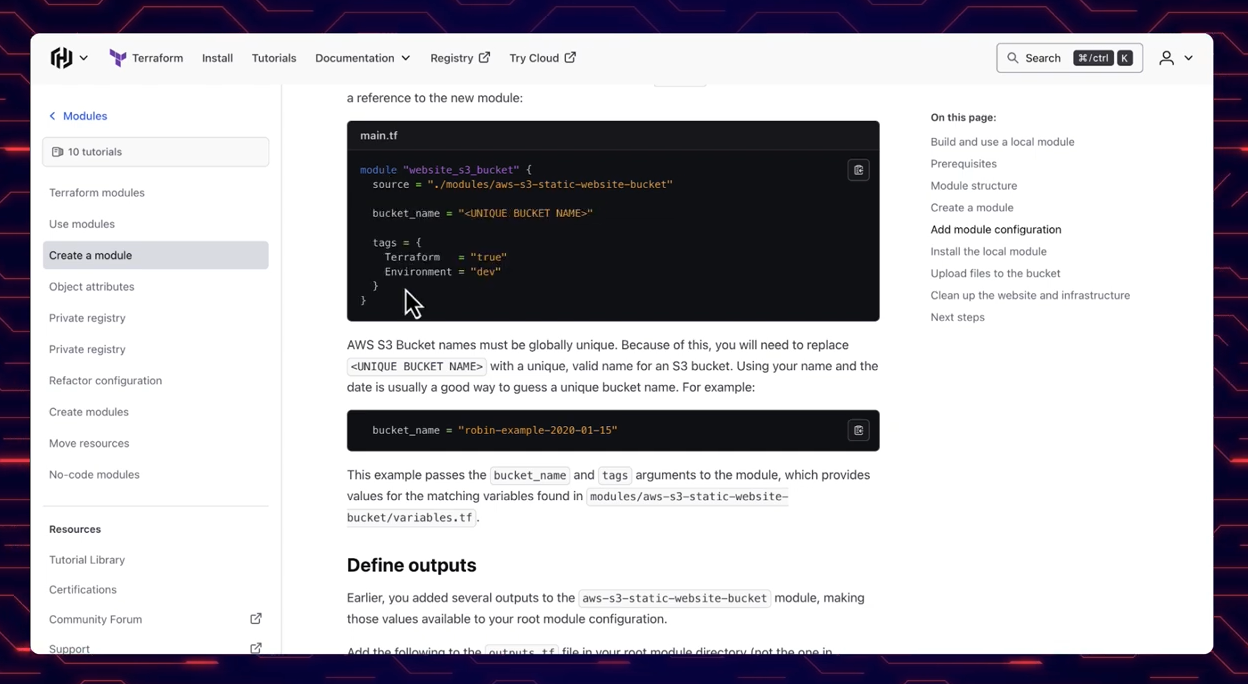
Tenable Cloud Security now supports scanning Terraform modules, which enhances your security posture by considering the broader context of modularized code. Tenable analyzes modules (local or remote) that are being called by your Terraform code files, resolving variables and resource definitions in the modules to discover potential misconfigurations in your code.
Continuously monitor cloud environments for data exposure and ensure regulatory compliance with new DSPM capabilities. Identify new data resources, and then scan those resources for sensitive data. When sensitive data is discovered it is mapped to known data types, which are grouped into different categories such as Personally Identifiable Information (PII), Protected Health Information (PHI) and Digital Identity identifiers.
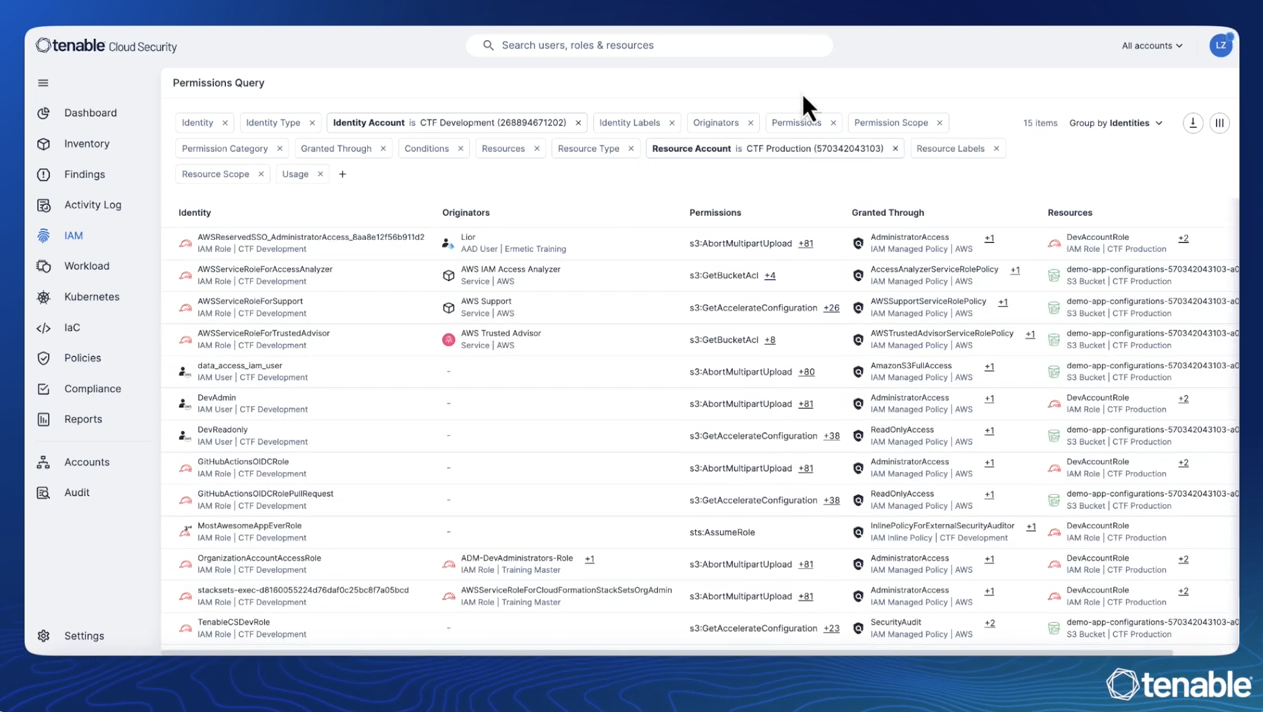
Related Blog: The Data-Factor: Why Integrating DSPM Is Key to Your CNAPP StrategyDocumentation
Most people know Tenable’s cloud security solution is a holistic security platform for cloud environments that provides a suite of security abilities such as workload protection, posture, identity, network analysis, and posture security management However, one of our most popular features is the ability to manage just-in-time access to cloud resources, which allows system administrators to avoid providing permanent access. Following up on market demand, we’ve expanded this ability to manage memberships to groups in identity providers. This is a very popular mechanism for providing access to SaaS applications, and thus, Tenable cloud security can also allow you to avoid giving users permanent access to such applications.
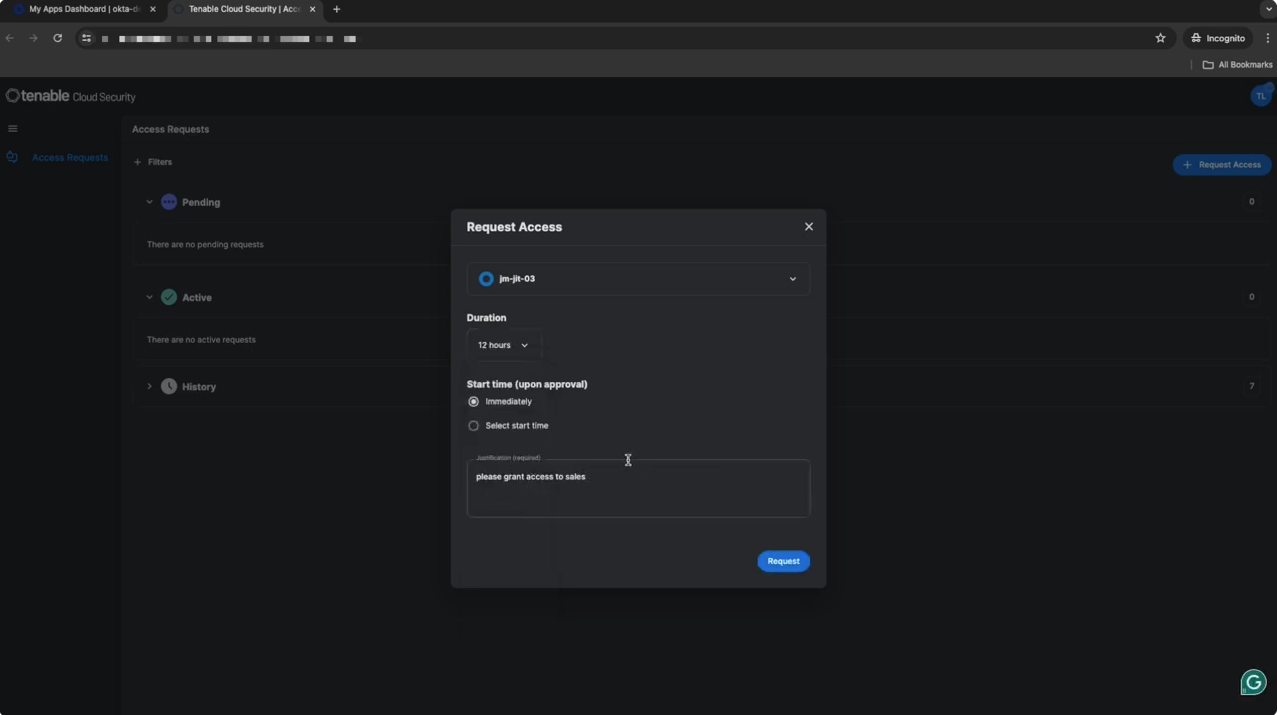
Related Blog: Improving Your Cloud Security Using JIT Access for Sensitive SaaS Applications
