Kubernetes security posture management for multi-cloud environments
Full-stack protection for Kubernetes
Managing your Kubernetes security posture is challenging. The dynamic nature of Kubernetes clusters, with pods and containers spinning up and down quickly, creates security blind spots. At the same time, Kubernetes provides many configuration options, and misconfigurations can lead to security vulnerabilities. To avoid these pitfalls, you need to manage Kubernetes security in a consistent and automated way.
See how
Kubernetes security delivered as part of an identity-first cloud native application protection platform (CNAPP)
Tenable helps you take the guesswork out of securing Kubernetes by providing you with the visibility you need to understand what’s running and at risk in your Kubernetes environments. With Tenable Cloud Security, you can integrate Kubernetes security into your overall exposure management efforts and minimize the risks associated with accelerated cloud adoption.
Get unified visibility to reduce risk across Kubernetes environments
Full-stack visibility across multi-cloud Kubernetes clusters
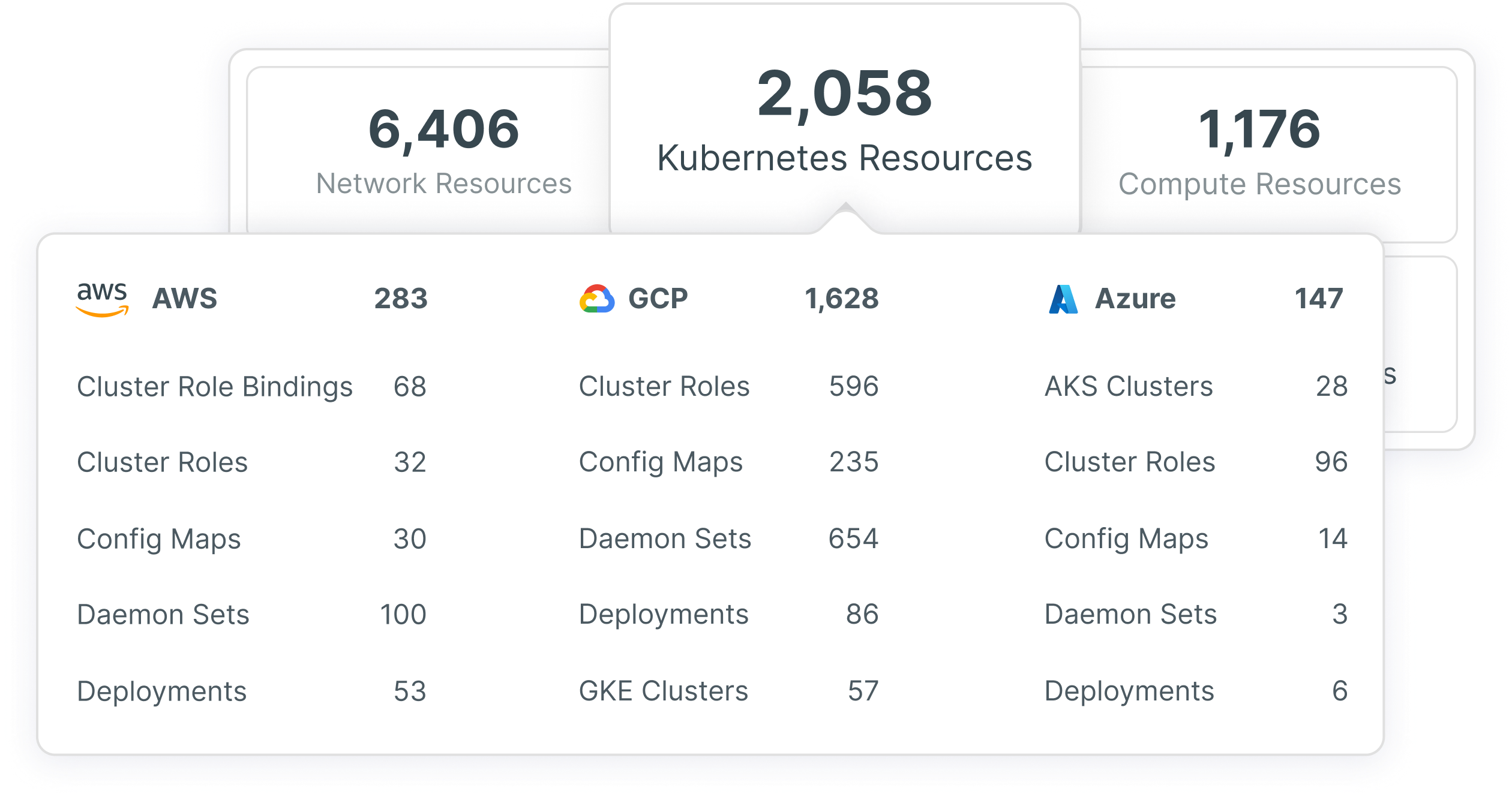
With Tenable Cloud Security, you can effortlessly manage all your multi-cloud resources, including workloads, identities, data, network, and Kubernetes clusters, in one convenient location. Tenable continuously discovers and presents all resources in a meaningful, multi-dimensional context, empowering you to easily investigate configurations, permissions, and relationships. Additionally, we seamlessly integrate Kubernetes inventory data by querying the cloud APIs and Kubernetes API for each cluster, as well as through continuous, agentless scanning of Kubernetes node configuration and containers within each node.
Contextual risk analysis and automated compliance reporting
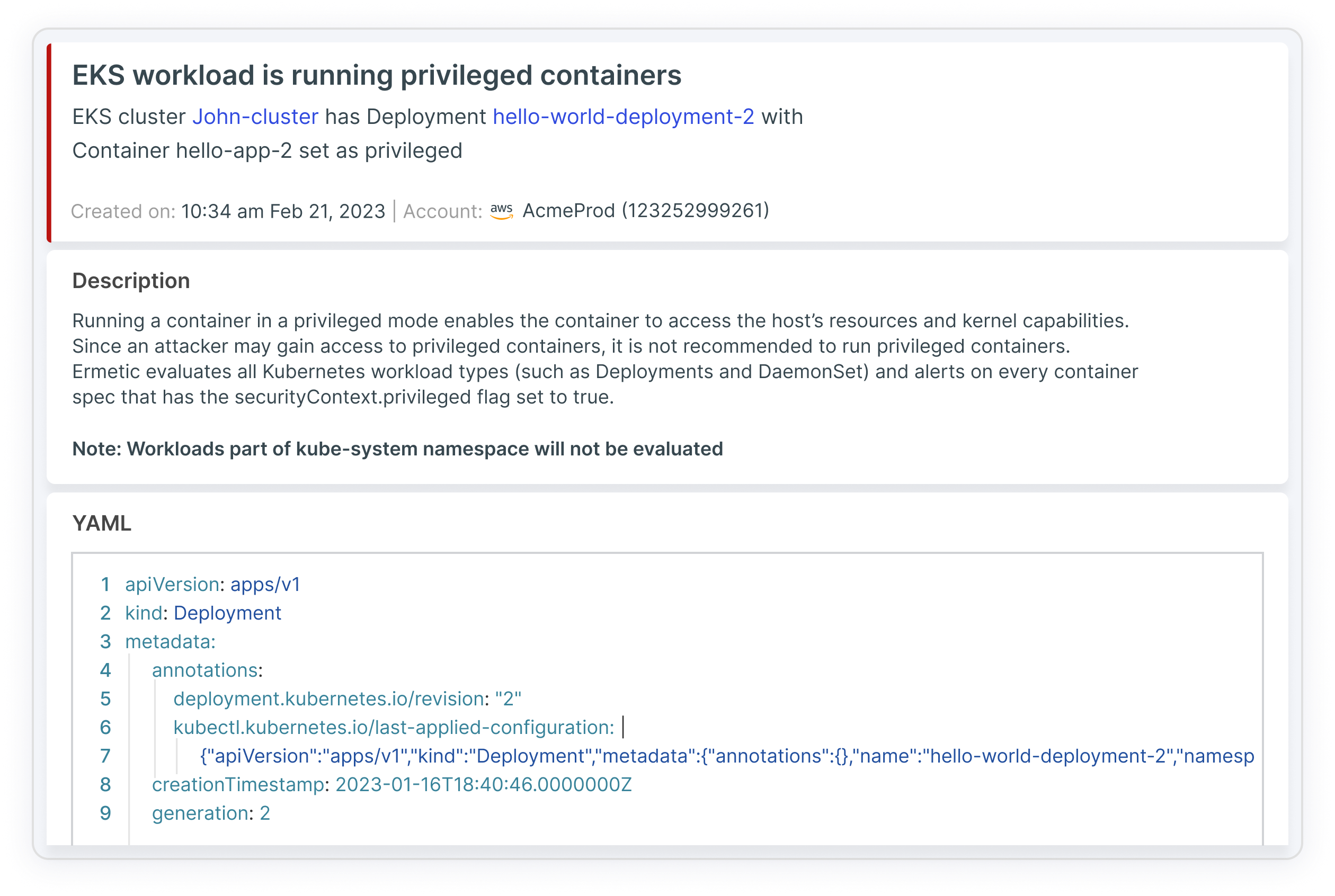
Tenable simplifies Kubernetes security by enabling you to scan containers for vulnerabilities, visualize network exposure, posture issues, IAM misconfigurations and misconfigurations defined in Kubernetes manifests and other risks – all within a single solution. We then help you focus on what matters most by prioritizing vulnerabilities that can expose sensitive resources and have the greatest impact on your assets. Additionally, Tenable automates compliance and security against industry standards including GDPR, NIST, PCI-DSS and CIS for Kubernetes benchmarks. You can generate detailed reports for internal compliance, external audits and daily security activities such as asset inventory and network configurations.
Prevent risks with anomaly detection and automated remediation
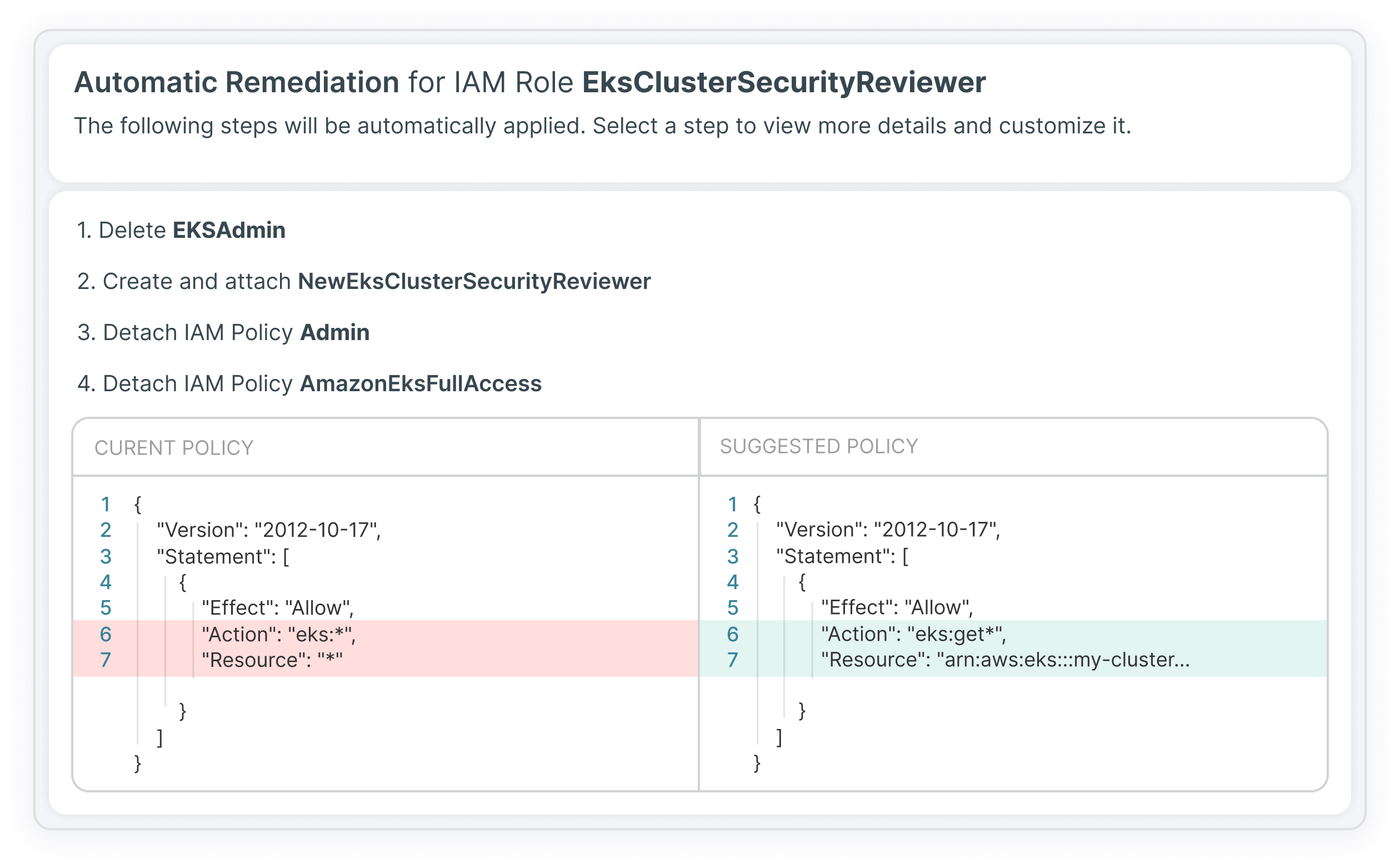
With Tenable Cloud Security, you can take a more preventive approach to Kubernetes security, automating threat detection by analyzing cloud provider logs and correlating them with the underlying architecture to identify unusual and suspicious behavior. It allows your incident response teams to investigate risks in context and integrates with SIEM solutions and ticketing/notification systems for faster response. In addition, you can take advantage of guided remediations for misconfigurations, policy violations and risky privileges in your multi-cloud environment.
"The biggest benefit of working with [Tenable Cloud Security], it's the discoverability component. It really lifts the veil on what is an opaque system."
MICHAEL BISHOPDir. Architecture and Engineering, BarkBox
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security