Tenable
Open Source
Community-driven technology to reduce cloud exposures
We’re on a mission to empower everyone to secure their cloud environment. With intuitive open source tooling, the cloud native community can work together to isolate and eradicate cloud exposures, ultimately creating a more secure cloud environment for all.

Join the Tenable open source community
Tenable open source community projects
Uniting security professionals, students and open source contributors to foster innovation.
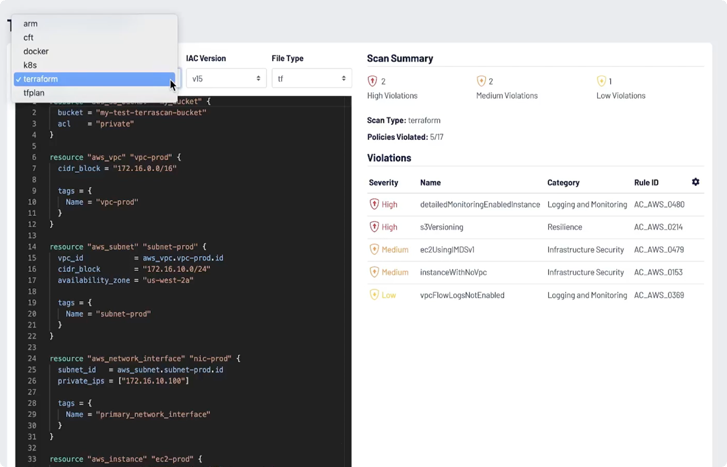
Terrascan by Tenable
With Terrascan, you can scan nearly all infrastructure as code (IaC) types for misconfigurations and compliance violations with more than 500 out-of-the-box policies. Terrascan leverages the Open Policy Agent (OPA) engine so you can easily create custom policies using the Rego query language. Integrate into your CI/CD, use locally or test code in your browser to see how effective preventive security can be. With 4,000 GitHub stars and 1.8 million downloads, Terrascan is one of the most beloved open source cloud security tools in the world.
Try it nowThis 45-second video shows how Terrascan reduces cloud exposures by scanning code that provisions cloud infrastructure.

CNAPPgoat
CNAPPgoat is an open source project for safe testing of cloud security skills, processes and tools in an easy-to-deploy-and-destroy sandbox environment. This enables defenders to test detection and prevention mechanisms against vulnerabilities and misconfigurations, while providing offensive professionals practice environments. With a large and expanding library of scenarios, DevSecOps teams can validate defenses in customized environments and simulate unsecured and vulnerable assets.
Learn more
Access undenied AWS
Access Undenied on AWS is an open source command-line interface (CLI) tool that analyzes and gives context to AWS CloudTrail AccessDenied events. It works by scanning the environment to identify and explain event reasons and offers actionable least-privilege remediation suggestions. Give the tool a CloudTrail event with an “Access Denied” outcome, and it will tell you how to fix it within seconds.
Learn moreRelated products
Related resources
- Tenable Cloud Security