Tenable
Nessus® Professional
Vulnerability assessment to stay one step ahead of attackers
Overcome scarce resources and limited time to keep pace with attackers and proactively find and fix vulnerabilities across your constantly changing attack surface.
Trust the No. 1 vulnerability assessment solution to give you peace of mind in a constantly changing security world. Trust Tenable Nessus.
Buy Nessus Pro
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Nessus
Expert
Pro
With Advanced Support for Nessus Pro, your teams will have access to phone, Community, and chat support 24 hours a day, 365 days a year. This advanced level of technical support helps to ensure faster response times and resolution to your questions and issues.
Advanced Support Plan Features
Phone Support
Phone support 24 hours a day, 365 days a year, available for up to ten (10) named support contacts.
Chat Support
Chat support available to named support contacts, accessible via the Tenable Community is available 24 hours a day, 365 days a year.
Tenable Community Support Portal
All named support contacts can open support cases within the Tenable Community. Users can also access the Knowledge Base, documentation, license information, technical support numbers, etc.; utilize live chat, ask questions to the Community, and learn about tips and tricks from other Community members.
Initial Response Time
P1-Critical: < 2 hr
P2-High: < 4 hr
P3-Medium: < 12 hr
P4-Informational:
< 24 hr
Support Contacts
Support contacts must be reasonably proficient in the use of information technology, the software they have purchased from Tenable, and familiar with the customer resources that are monitored by means of the software. Support contacts must speak English and conduct support requests in English. Support contacts must provide information reasonably requested by Tenable for the purpose of reproducing any Error or otherwise resolving a support request.
Knowledge is power
Eliminate attack paths by gaining the insights you need.
Keeping pace with attackers is hard – especially with the constant barrage of new vulnerabilities and an ever-changing attack surface.
Since 1998, Nessus has helped security teams stay a step ahead. It provides the visibility, accuracy and speed you need to protect your organization against unacceptable risk.
This 4:30 Nessus Professional video demonstrates how you can streamline vulnerability assessments.Try Nessus now for free.

#1 in vulnerability assessment. Trusted by customers.
Built by practitioners
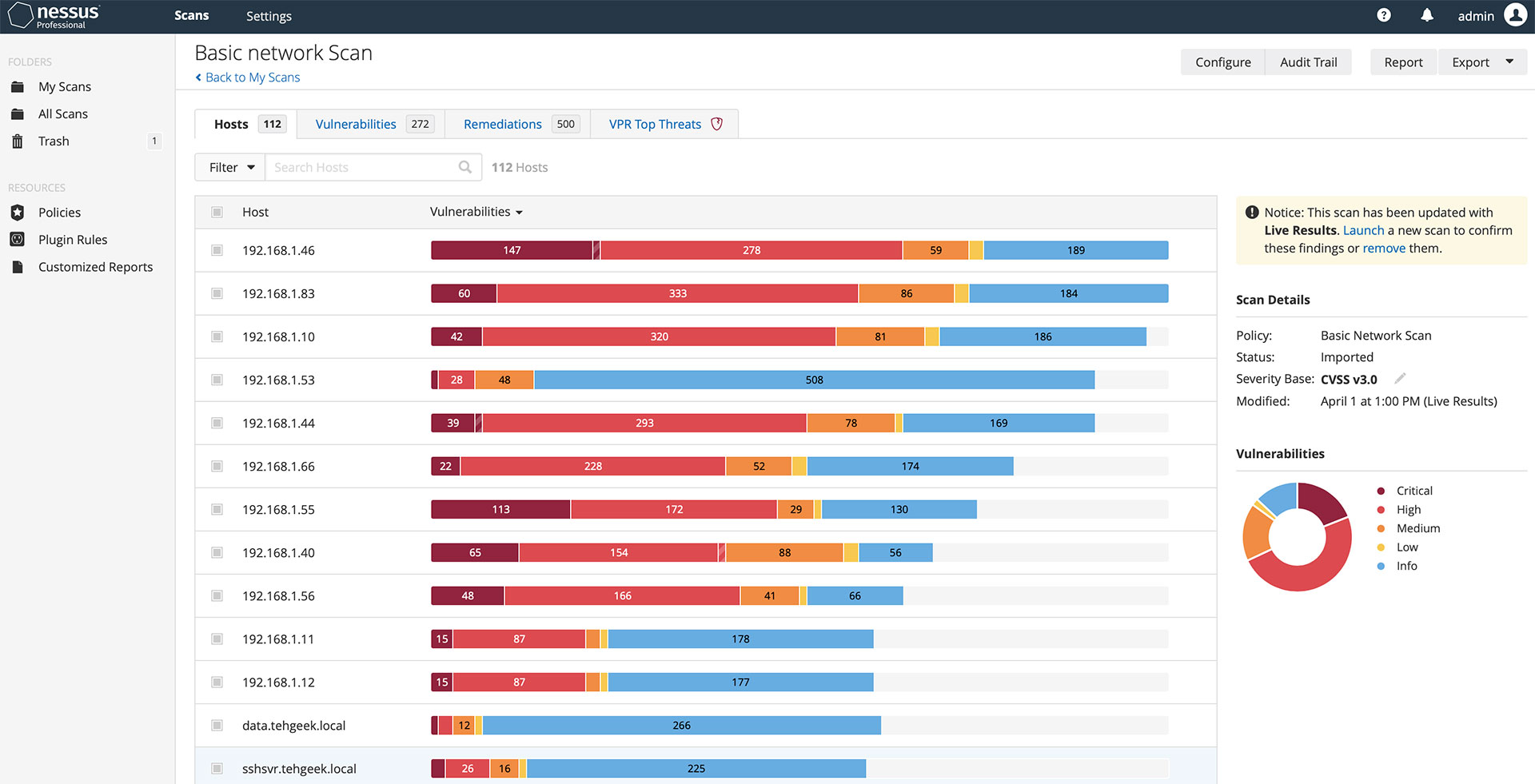
Nessus is built from the ground-up with a deep understanding of how security practitioners work. Every feature in Nessus is designed to make vulnerability assessment simple, easy and intuitive. The result: less time and effort to assess, prioritize and remediate issues. Learn more about the features here.
-
Deploy on any platform
Nessus can be deployed on a variety of platforms, including Raspberry Pi. Regardless of where you are, where you need to go or how distributed your environment is, Nessus is fully portable.
-
Efficiency and accuracy
Dynamically compiled plugins increase scan performance and efficiency, enabling faster completion of the first scan and time to value. -
Leverage IaC security scanning
Download and start scanning with Terrascan to secure your Infrastructure as Code (IaC) before deployment. -
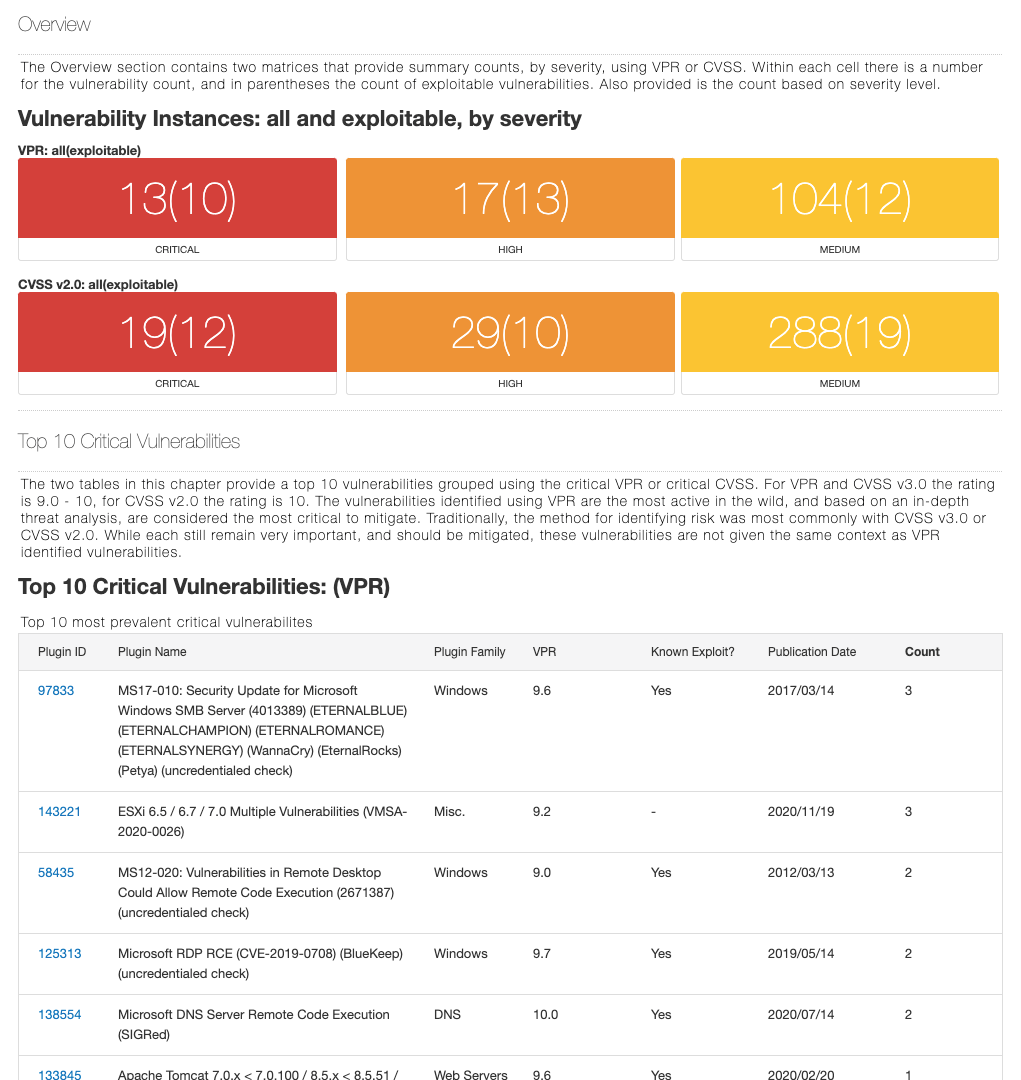
Zero in on threats that matter most
With market-leading coverage, Nessus knows every vulnerability. The power of Nessus lets you prioritize vulns by leveraging a variety of inputs, including EPSS, CVSS, and Tenable VPR to then triage and address the threats that matter most. -
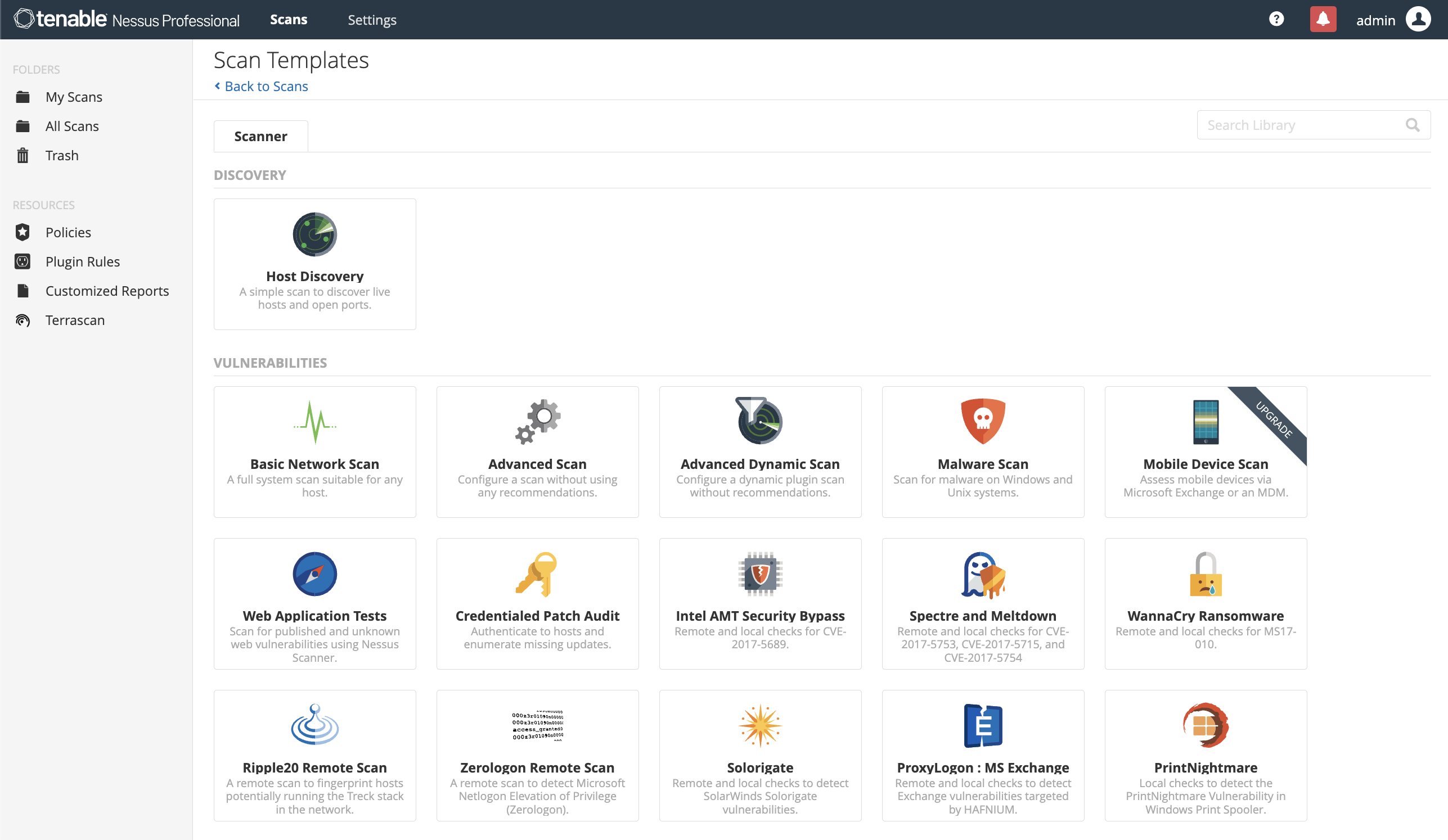
Pre-built policies and templates
More than 450 pre-configured templates help you quickly understand where you have vulnerabilities. Easily audit configuration compliance against CIS benchmarks and other best practices. -
Customizable reporting & troubleshooting
Customizable reporting capabilities can be optimized to meet specific needs and are exportable in formats that are most suited for your security process. -
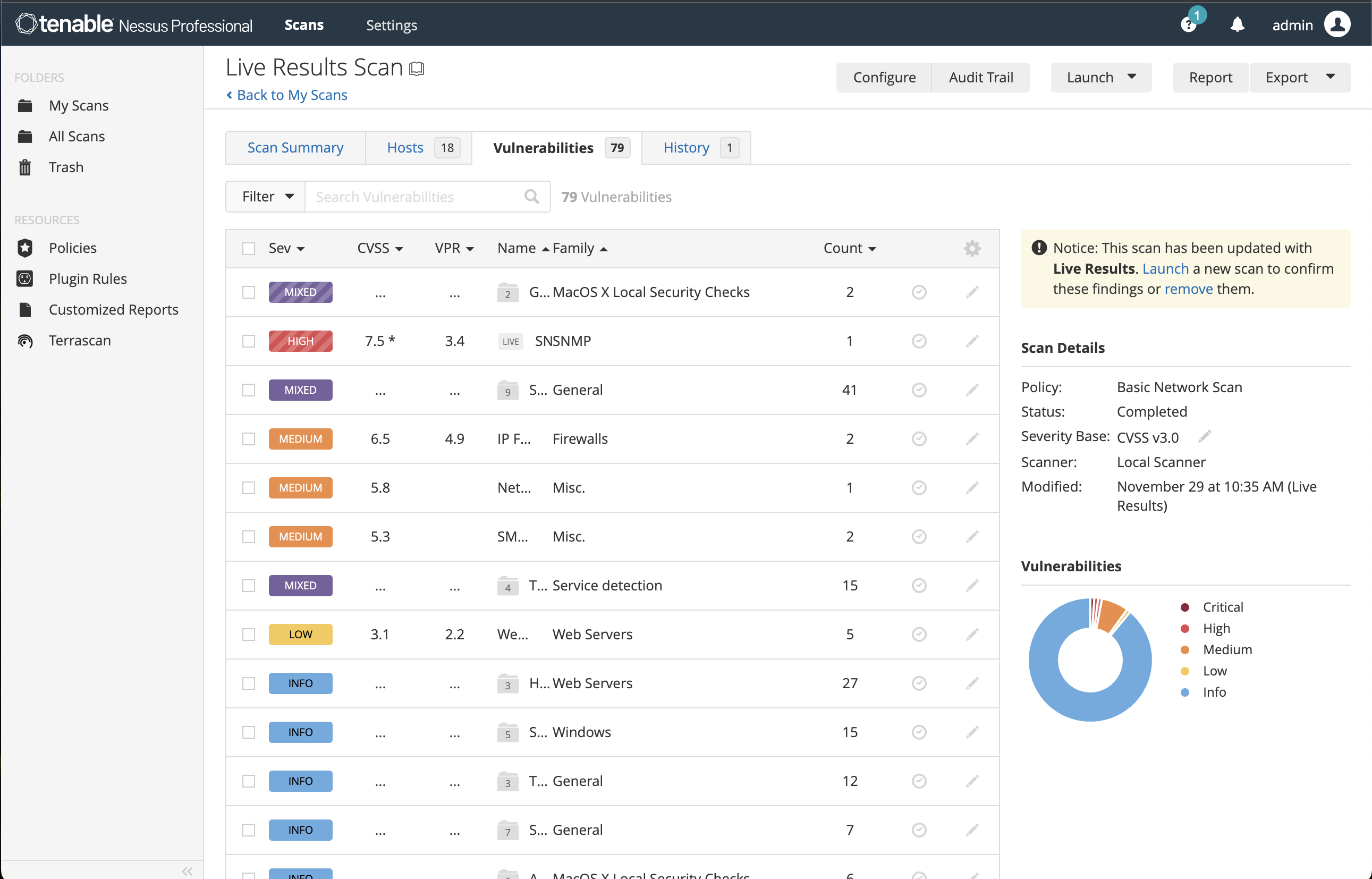
Live results
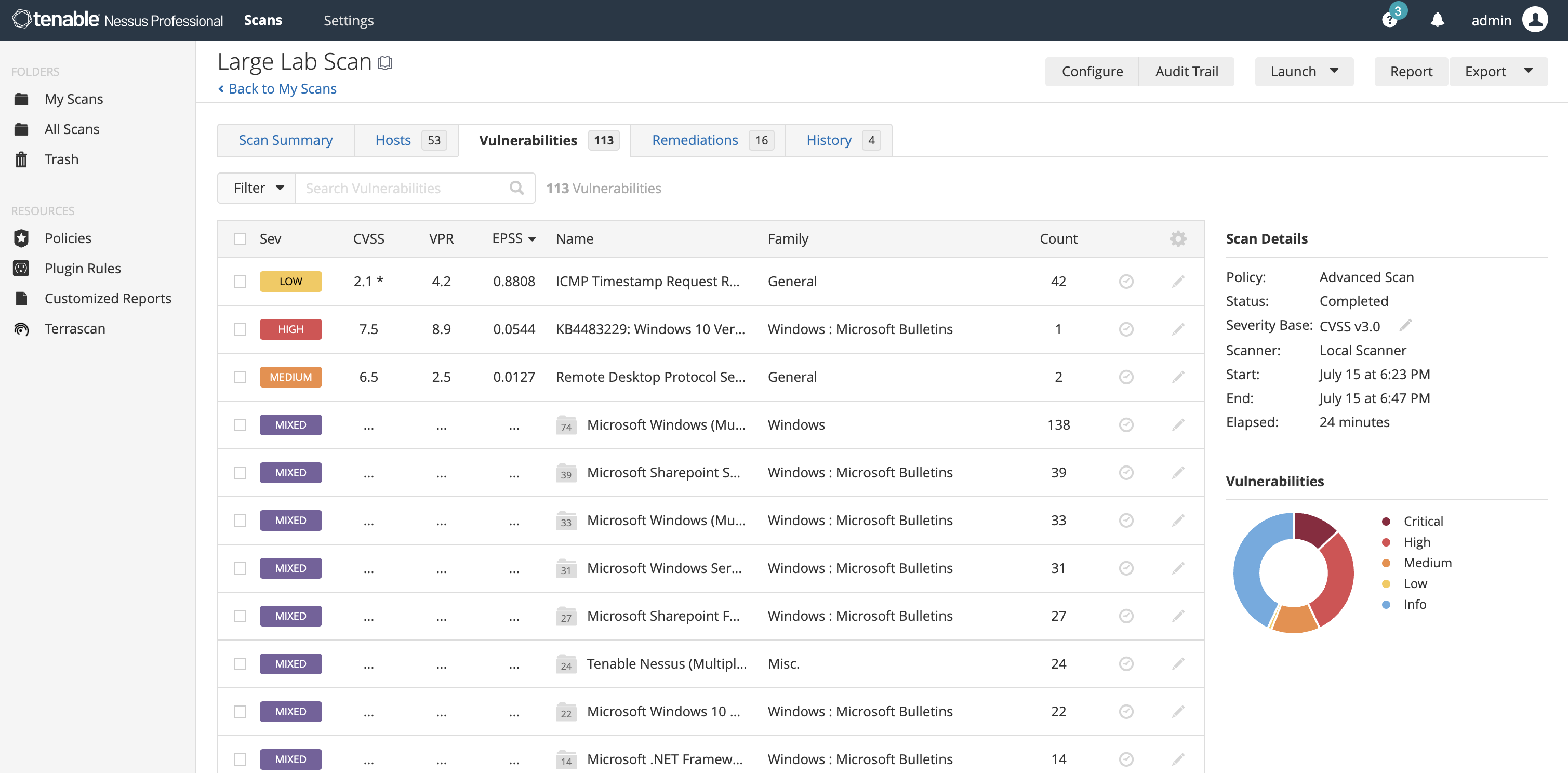
Live Results automatically performs an offline vulnerability assessment with every plugin update, showing you where you may have vulnerabilities based on your scan history. From here you can easily run a scan to validate the presence of the vulnerability that accelerates accurate detection and prioritization of issues. -
Ease of use
Nessus is designed with an intuitive approach to navigation and user experience. This includes a resource center to guide you with actionable tips and guidance on the next steps to take. -
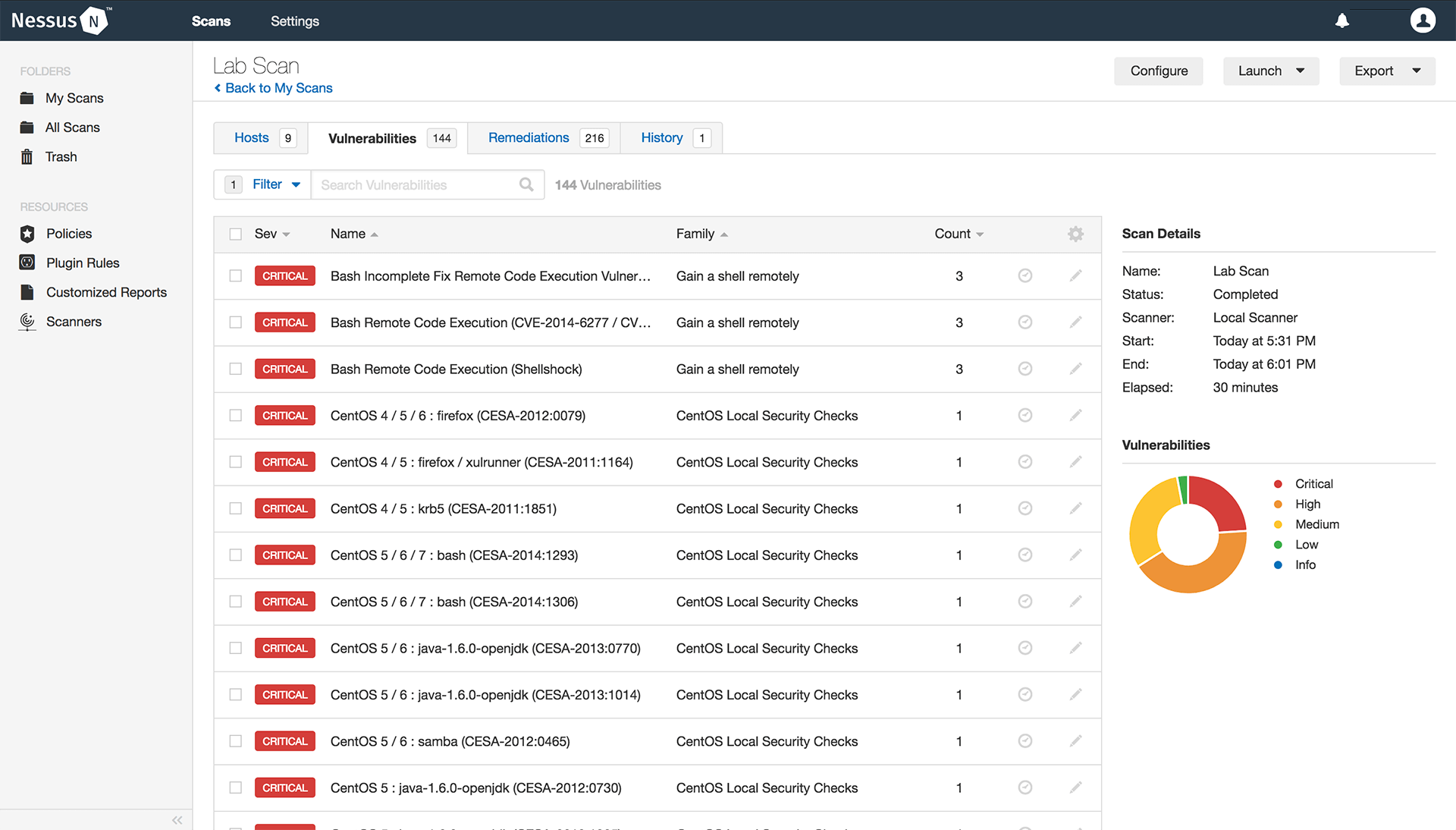
Grouped view
Similar issues or categories of vulnerabilities are grouped together and presented in one thread, simplifying the time to research and prioritize issues for remediation. Snoozing lets you select specific issues to disappear from view for a specified period of time. So you only focus on the issues that matter at that time.
Nessus Pro benefits
Key use cases for Nessus
Nessus is the world’s No. 1 vulnerability scanning solution. Learn how Tenable customers put it to work in a range of critical situations.

Network pen testers play a unique role in the IT security ecosystem.
Before executing full breach simulations, pen testers use Nessus first to find where those major vulnerabilities are hiding.
Read more
Cybersecurity students are invaluable to this highly specialized field.
Professors use Nessus with cybersecurity students in vulnerability assessment and management courses as a foundational tool to get them up to speed on the essentials of uncovering vulnerabilities.
Read more
Cybersecurity consultants play pivotal roles in a constantly shifting threat and vulnerability landscape.
Cybersecurity consultants use Nessus to scour clients’ networks for vulnerabilities and create comprehensive reports that summarize security posture and contain key suggestions for remediation.
Read more
In years past, small and medium-sized businesses might have considered themselves effectively immune to cyberattacks.
With Nessus, even small companies that lack full-time cybersecurity staff can stay on top of vulnerabilities, customizing comprehensive scans to meet unique business needs.
Read moreTo learn more about Nessus features and functionality, visit our Nessus documentation page.
To learn more about purchasing options, please contact your preferred reseller or visit our online store.
Nessus on-demand training
Interested in learning how to use Nessus? Our on-demand course enables the student, pen tester, consultant and security practitioner, through a series of targeted videos, to develop the building blocks for effective use of the Nessus vulnerability assessment solution. From asset discovery to vulnerability assessment to compliance, participants will learn to effectively utilize Nessus in a variety of business use cases.
Course topics
60+ targeted videos and demonstrations covering these topics:
- Introduction to cybersecurity
- Installation
- Configuration
- Vulnerability assessment
- Compliance assessment
- Analysis
Nessus Pro—
Built for security professionals like you
Get the world’s most widely deployed vulnerability assessment solution.
Buy Nessus Pro
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Nessus
Expert
Pro
With Advanced Support for Nessus Pro, your teams will have access to phone, Community, and chat support 24 hours a day, 365 days a year. This advanced level of technical support helps to ensure faster response times and resolution to your questions and issues.
Advanced Support Plan Features
Phone Support
Phone support 24 hours a day, 365 days a year, available for up to ten (10) named support contacts.
Chat Support
Chat support available to named support contacts, accessible via the Tenable Community is available 24 hours a day, 365 days a year.
Tenable Community Support Portal
All named support contacts can open support cases within the Tenable Community. Users can also access the Knowledge Base, documentation, license information, technical support numbers, etc.; utilize live chat, ask questions to the Community, and learn about tips and tricks from other Community members.
Initial Response Time
P1-Critical: < 2 hr
P2-High: < 4 hr
P3-Medium: < 12 hr
P4-Informational:
< 24 hr
Support Contacts
Support contacts must be reasonably proficient in the use of information technology, the software they have purchased from Tenable, and familiar with the customer resources that are monitored by means of the software. Support contacts must speak English and conduct support requests in English. Support contacts must provide information reasonably requested by Tenable for the purpose of reproducing any Error or otherwise resolving a support request.
Learn more
- Tenable Nessus