Tenable versus Microsoft
“Good enough” VM from Microsoft is not good enough
In March 2022, Tenable Research discovered two vulnerabilities (one critical) in the Microsoft Azure platform and both were exploitable. Microsoft downplayed the risk and it took the company 89 days to privately acknowledge the severity of the issue.
Why customers choose Tenable over Microsoft
Compare Tenable to Microsoft
Vulnerability and coverage accuracy
89K CVEs the industry’s broadest coverage
Not published
Prioritization
Exposure view combines Tenable’s vulnerability priority rating with an asset criticality score
Does not consider important business context
Scope of coverage
Wide variety of assets - endpoints, network devices, operational technology (OT), cloud workloads, web apps
Limited to the endpoints with an agent and basic SNMP-based capability
Dashboarding and reporting
Extensive library of dashboards and reports
Lack of dashboards and reports
Vulnerability management tool ecosystem
Integration and support for the 3rd party remediation tools, remediation workflow
Minimal integration with remediation tools like BigFix
Scanning technologies
Agent-based and agentless
Agent-based with limited support for network scanning
#1 in vulnerability management
Featured
IDC ranks Tenable as #1 in worldwide Device Vulnerability Management market share for the sixth consecutive year.
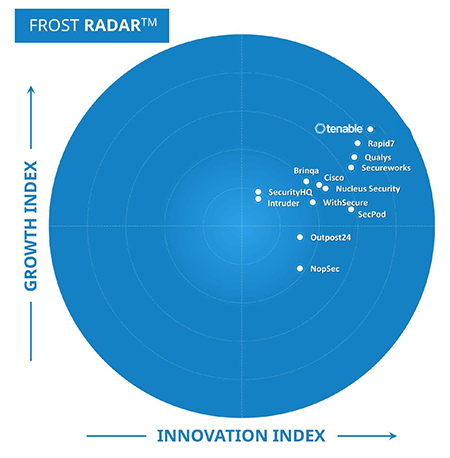
Read the reportTenable is named a leading force in vulnerability management and top-ranked among 13 vendors in both the Growth and Innovation indexes in the Frost Radar, Vulnerability Management, 2023.
Read the reportCompetitive guide: Security Leaders’ Guide to Comparing Tenable and Microsoft
Read the reportSee Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.
- Tenable Vulnerability Management