Start your free trial now
Get started with Tenable’s
exposure management solutions
From IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
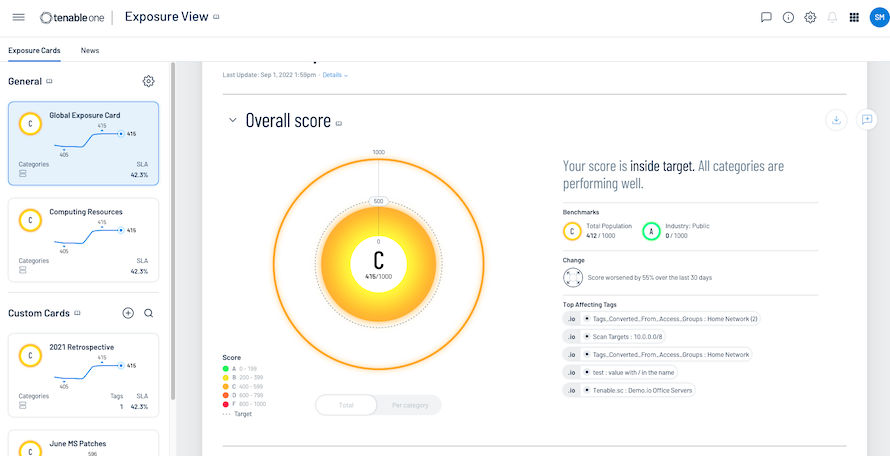
Tenable One
Exposure management for your modern attack surface
Get comprehensive visibility across your modern attack surface with Tenable One, an exposure management platform to help your teams translate technical asset, vulnerability and threat data into clear business insights and actionable intelligence.
- Gain a unified view of all types of assets and associated vulnerabilities, on-prem or in the cloud
- Anticipate the consequences of a cyber attack
- Effectively communicate business-aligned cyber risk with peer benchmarking
“Buying security tools can be complex with various add-ons that make pricing hard. I consolidate security tools as much as I can, and with Tenable One it's all included and streamlined.”
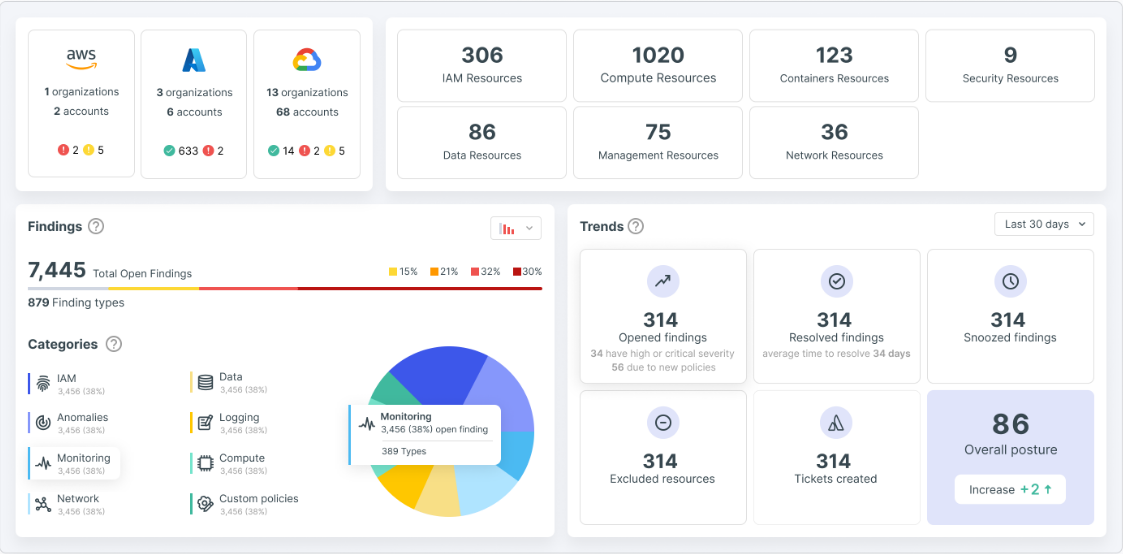
Tenable Cloud Security
Experience unified cloud security posture and vulnerability management with Tenable Cloud Security
Address your biggest risks in the cloud with Tenable Cloud Security. Get a unified CNAPP and industry-leading CIEM that will give you context and prioritization guidance to make efficient and accurate remediation decisions. Enjoy an intuitive user interface that makes it easy to spot and quickly address risks, even if you're not a cloud security expert.
- Simplify even the most complex issues with powerful visualizations and step-by-step remediation
- Secure cloud identities, permissions and secrets, enforcing least privilege and zero trust across clouds
- Automate audits and compliance reporting
- Accelerate security across the organization with better collaboration across DevSecOps and IAM teams
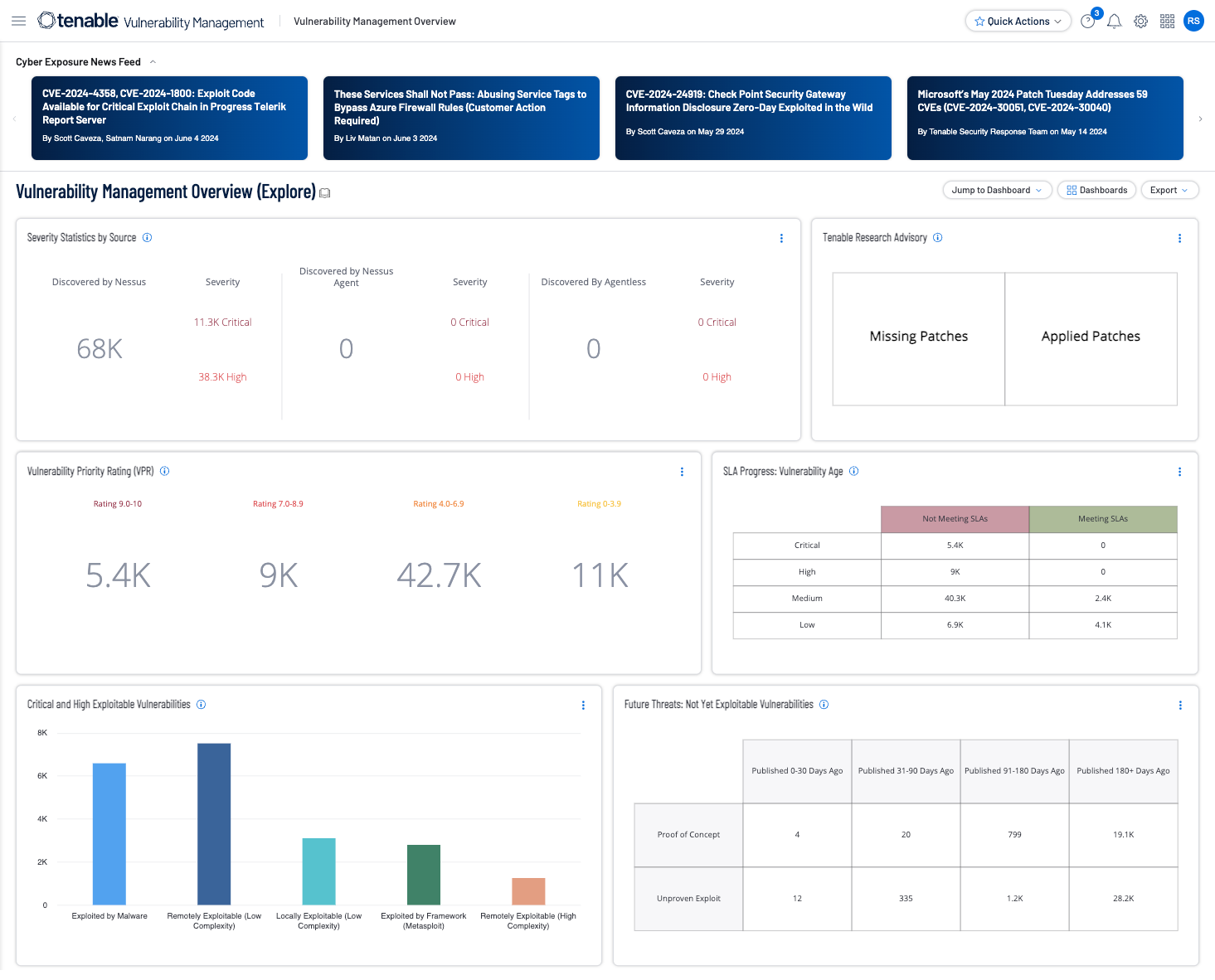
Tenable Vulnerability Management
See everything. Predict what matters. Managed in the cloud.
Get a risk-based view of your entire attack surface—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between—so you can quickly identify, investigate and prioritize vulnerabilities. Powered by Nessus technology, Tenable Vulnerability Management provides the industry's most comprehensive vulnerability coverage with the ability to predict which security issues to remediate first.
- Built for cybersecurity leaders and practitioners
- Predict critical vulnerabilities to know what to fix first
- Provide unified visibility and a continuous view of all types of assets
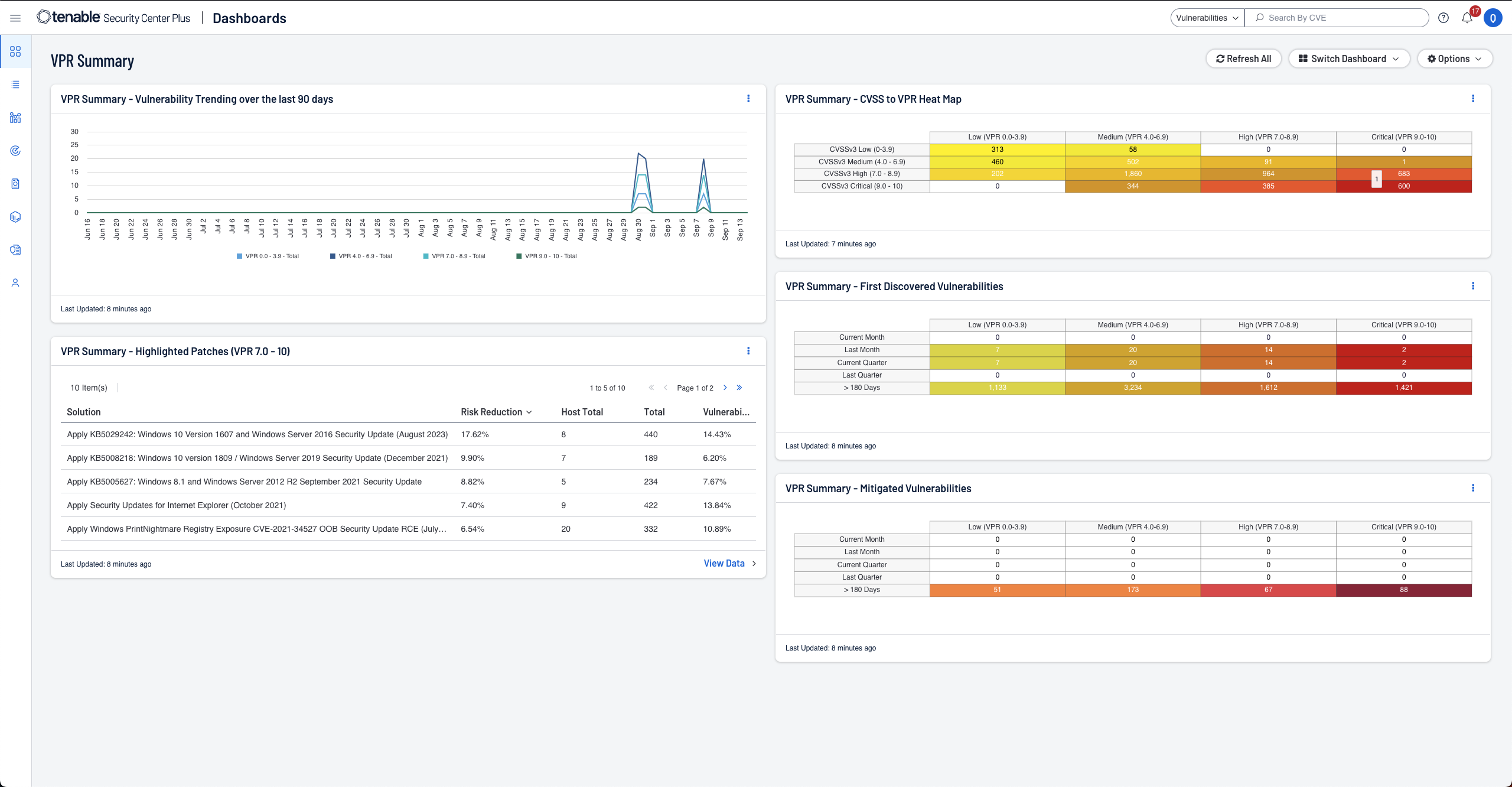
Tenable Security Center
See everything. Predict what matters. Managed on-prem.
Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities. Powered by Nessus technology, Tenable Security Center provides the industry's most comprehensive vulnerability coverage with real-time continuous assessment of your network to predict which security issues to remediate first.
- Built for cybersecurity leaders and practitioners
- Predict critical vulnerabilities to know what to fix first
- Streamline compliance reporting against regulatory mandates
Tenable OT Security
Get the operational technology you need. Reduce the risk you don’t.
Get the operational technology (OT) security you need and reduce the risk you don't with Tenable OT Security asset inventory, vulnerability management, forensics support and configuration controls. With complete visibility into your converged OT/IT infrastructure, you can maximize the safety and security of your OT environment.
- Built for cybersecurity (OT/IT) and compliance practitioners
- Comprehensive visibility into OT devices with active querying
- Unified OT and IT security in a single platform
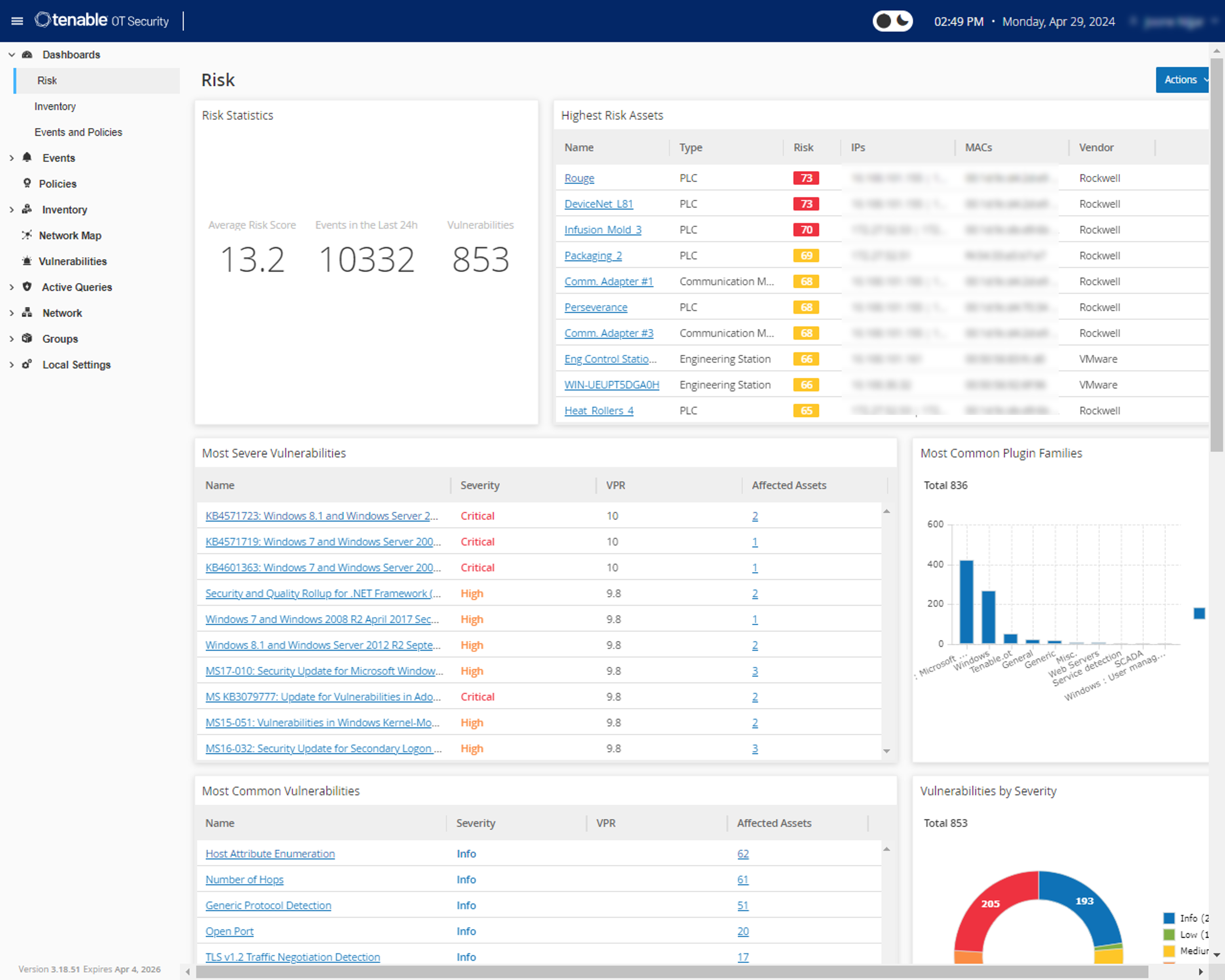
Tenable Identity Exposure
Detect and respond to Active Directory (AD) attacks in real time
Discover and prioritize Active Directory (AD) vulnerabilities and misconfigurations to eliminate attack paths before attackers exploit them. Tenable Identity Exposure prevents and detects sophisticated Active Directory attacks such as Brute Force, DCShadow, DCSync, password spraying and more, without agents and privileges. You can deploy Tenable Identity Exposure anywhere, on-prem or leverage the cloud.
- Discover underlying issues affecting Active Directory
- Identify dangerous trust relationships
- Catch every change in your Active Directory
- Reduce exposures with step-by-step remediation guidance
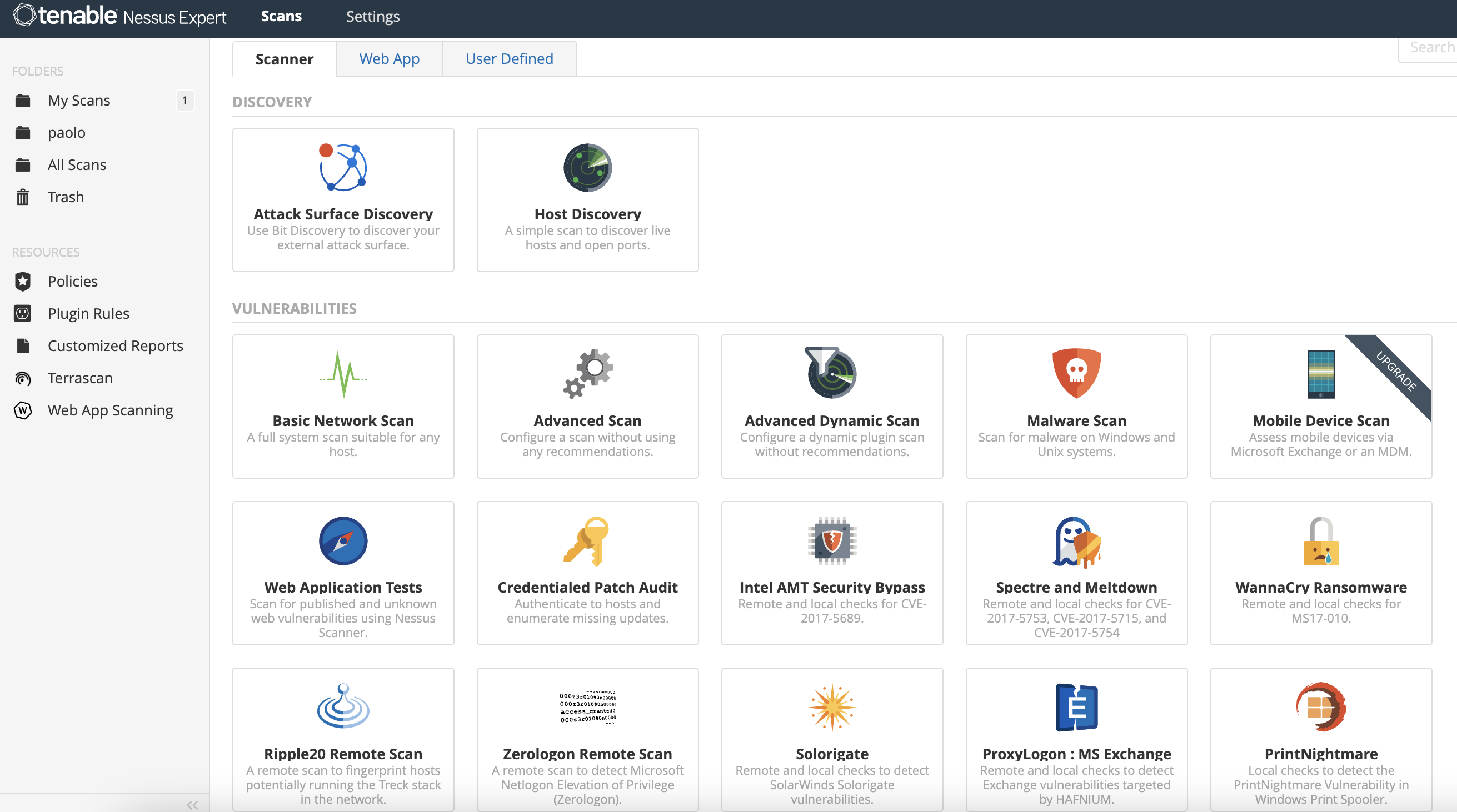
Tenable Nessus
Built for the modern attack surface
Nessus is one of the most widely deployed cybersecurity technologies on the planet built for the modern attack surface. Every feature makes vulnerability assessment simple, easy and intuitive. With Nessus, you’ll spend less time and effort assessing, prioritizing and remediating vulnerabilities so you can stay one step ahead of attackers.
- Ideal for consultants, pen testers, developers and SMB's
- Industry’s deepest and broadest CVE coverage
- VA coverage for IT assets, web applications, cloud infrastructure and attack surface discovery
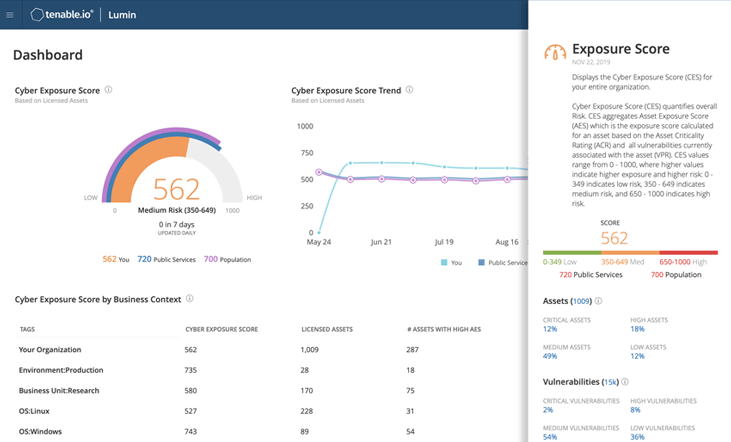
Tenable Lumin
Calculate, communicate, compare and manage cyber risks
For the first time ever, you can visualize and explore your cyber risk, track risk reduction over time, and benchmark against your peers. Tenable Lumin is an advanced visualization, analytics and measurement solution to transform vulnerability data into meaningful insights to help you manage cyber risk across your entire organization.
- Built for cybersecurity leaders and practitioners
- Calculate, communicate and compare cyber risk
- Prioritize remediation based on cyber risk reduction
- Tenable Attack Surface Management
- Tenable Cloud Security
- Tenable Identity Exposure
- Tenable Lumin
- Tenable Nessus
- Tenable One
- Tenable OT Security
- Tenable Security Center
- Tenable Vulnerability Management
- Tenable Web App Scanning