Cybersecurity Snapshot: CISA Calls for Stamping Out Buffer Overflow Vulnerabilities, as Europol Tells Banks To Prep For Quantum Threat

Check out best practices for preventing buffer overflow attacks. Plus, Europol offers best practices for banks to adopt quantum-resistant cryptography. Meanwhile, an informal Tenable poll looks at cloud security challenges. And get the latest on ransomware trends and on cybercrime legislation and prevention!
Dive into six things that are top of mind for the week ending Feb. 14.
1 - CISA, FBI offer buffer overflow prevention tips
The U.S. government is urging software makers to adopt secure application-development practices that help prevent buffer overflow attacks.
This week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) called buffer overflow vulnerabilities “unforgivable defects” that put national and economic security at risk.
“CISA and FBI urge manufacturers to use proven prevention methods and mitigations to eliminate this class of defect while urging software customers to demand secure products from manufacturers that include these preventions,” the agencies wrote in a joint fact sheet.
Buffer overflows happen when data written to a computer’s memory buffer exceeds the buffer’s capacity. This can lead to issues such as system crashes, data corruption and remote code execution.

These are some of the recommendations the agencies offered for preventing buffer overflows in the fact sheet titled “Malicious Cyber Actors Use Buffer Overflow Vulnerabilities to Compromise Software.”
- Use memory-safe languages when developing software.
- Implement compile time and runtime protections using compiler flags.
- Rigorously test your software products using static analysis, fuzzing and manual reviews throughout the development cycle.
- Analyze the root cause of past buffer overflow vulnerabilities to detect trends and patterns.
CISA and the FBI also highlighted these buffer overflow vulnerabilities:
CVE-2025-21333
CVE-2025-0282
CVE-2024-49138
CVE-2024-38812
CVE-2023-6549
CVE-2022-0185
For more information about buffer overflow attacks and vulnerabilities:
- “Buffer Overflow” (OWASP)
- “What is Buffer Overflow?” (Cybersecurity News)
- “How to mitigate buffer overflow vulnerabilities” (Infosec Institute)
- “How to prevent buffer overflow attacks” (TechTarget)
VIDEOS
What is a Buffer Overflow Attack? (TechTarget)
Buffer Overflow Attacks Explained (Tech Sky)
2 - Europol to banks: Prepare for quantum computing threat
Financial institutions in Europe must get ready to face the cyberthreat that quantum computers will pose to data security and data privacy when these powerful systems become widely available.
That’s the message from Europol’s new document “Quantum Safe Financial Forum - A call to action” which urges the European financial sector to prioritize adopting post-quantum cryptography.
Here’s the problem: Quantum computers will be able to decrypt data protected with existing public-key cryptographic algorithms, which is why post-quantum algorithms are being developed, with several already available for use.
Estimates about when these quantum computers will be ready range anywhere from five years to 15 years from now. However, the process for organizations to transition towards quantum-resistant cryptography will be lengthy and complicated.

In addition to adopting post-quantum cryptography, banks and other financial institutions should take this opportunity to boost their cryptography management practices, according to Europol.
However, the financial sector won’t be able to go through this journey unassisted. “Achieving this complex goal requires immediate action and a coordinated effort involving industry peers, vendors, policymakers, and society,” the document reads.
Europol recommendations for adopting post-quantum cryptography include:
- To prioritize the shift to quantum-resistant cryptography, banks should update how they manage cryptography; train IT teams on cryptography; and allocate the required resources.
- To update cryptographic management, banks should, for example, integrate this practice into general IT asset management; inventory cryptographic assets; and implement policy compliance checks.
- Banks, governments, vendors and law enforcement agencies must collaborate, coordinate their efforts and share knowledge towards the common goal of securing data against quantum attacks.
- Regulators should refrain from creating new rules and instead focus on collaborating with the private sector on a set of common, consistent guidelines for quantum-safe cryptography.
For more information about the threat from quantum computing:
- “Is Quantum Computing a Cybersecurity Threat?” (American Scientist)
- “Quantum and the Threat to Encryption” (SecurityWeek)
- “Quantum Computing Advances in 2024 Put Security In Spotlight” (Dark Reading)
- “Quantum computing could threaten cybersecurity measures. Here’s why – and how tech firms are responding” (World Economic Forum)
- “Quantum Computing–Quantifying the Current State of the Art to Assess Cybersecurity Threats” (MITRE)
3 - A temperature check on cloud security challenges
During this week’s webinar “How does an industry leader like Tenable protect its own cloud environments?,” we asked attendees about their main cloud security challenges. Check out how they responded.
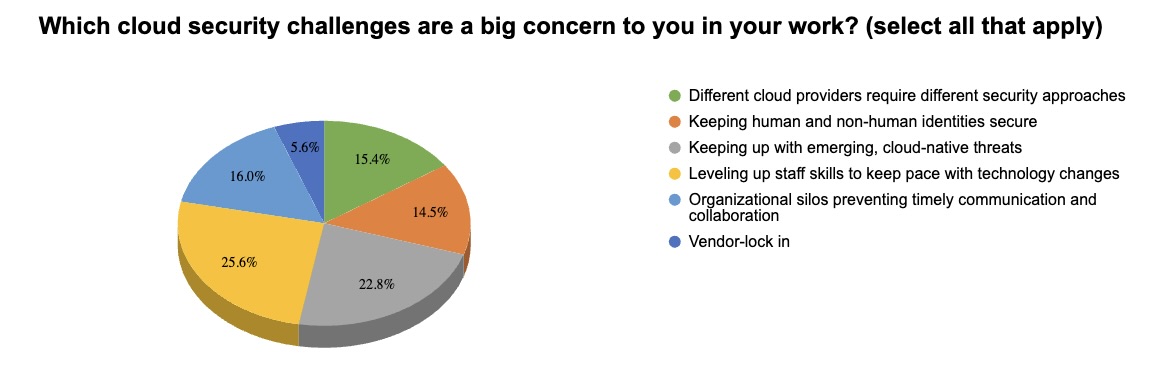
(Source: 138 webinar attendees polled by Tenable, February 2025)
Interested in learning how Tenable’s security team uses Tenable Cloud Security to safeguard our cloud environments? Watch the on-demand webinar, in which Phillip Hayes, Tenable’s Director of Information Security, and Michael Garman, Tenable’s Senior Manager of Technology Engineering, discuss a variety of cloud security best practices.
For more information about Tenable’s cybersecurity best practices, check out these Tenable blogs:
- "Establishing a Cloud Security Program: Best Practices and Lessons Learned"
- "How To Clean Up Your Cloud Environment Using Tenable Cloud Security"
- "Walking the Walk: How Tenable Embraces Its "Secure by Design" Pledge to CISA"
- "Strengthening the Nessus Software Supply Chain with SLSA"
- "Making Zero Trust Architecture Achievable"
- "Tenable’s Software Update Process Protects Customers’ Business Continuity with a Safe, Do-No-Harm Design"
4 - Google: Curbing cybercrime requires international collaboration
Governments must understand that financially motivated cyberattacks impact not only their specific victims but also endanger national security, and as such merit heightened attention from the public sector.
That’s a key takeaway from “Cybercrime: A Multifaceted National Security Threat,” a report released this week by Google’s Threat Intelligence Group.
Although cybercrime accounts for a majority of malicious cyber activity, it gets short shrift from national security cyber defenders, who instead place most of their focus on state-backed groups, the report states.
“While the threat from state-backed hacking is rightly understood to be severe, it should not be evaluated in isolation from financially motivated intrusions,” the authors wrote.

“Financially motivated cyber intrusions, even those without any ties to state goals, harm national security. A single incident can be impactful enough on its own to have a severe consequence on the victim and disrupt citizens' access to critical goods and services,” the report reads.
So how can governments more effectively tackle national-security cyberthreats from profit-seeking cybercriminals? Here are some of Google’s recommendations for government policymakers globally:
- Raise cybercrime to a national security priority, including collecting and analyzing data on cybercrime groups; and boosting law enforcement’s capacity to fight cybercrime.
- Promote adoption of strong cyber defenses across all industries by, for example, incentivizing organizations to adopt security best practices.
- Deploy legal, technical and financial measures to dismantle the infrastructure supporting cybercrime operations.
- Strengthen international collaboration by sharing cyberthreat information, conducting joint investigations and taking coordinated actions against cybercrime networks.
- Enhance efforts to educate individuals and organizations about online safety, cyber best practices and cyber incident reporting.
For more information about cybercrime trends:
- “Insider fraud and AI threats top forecasts of 2025 cybercrime” (American Banker)
- “Cybercrime Tactics and Demands Are Getting More Aggressive” (Bloomberg)
- “3 Cybercrime Trends Tech Pros Must Watch in 2025” (Dice)
- “UN General Assembly adopts milestone cybercrime treaty” (United Nations)
- “Major cybercrime crackdowns signal shift in global cybersecurity strategies” (The Conversation)
5 - Bipartisan U.S. bill seeks tougher punishments for cybercrimes
A bill introduced by two U.S. senators this week would update an existing computer crime law in order to dial up penalties for cybercrime conspiracies.
Currently, the U.S. government charges suspects accused of conspiracies to commit cybercrimes under a general statute, instead of under the Computer Fraud and Abuse Act (CFAA).

While the maximum penalty under the general conspiracy statute is five years in prison, the new conspiracy charge that would be added to the CFAA via the “Cyber Conspiracy Modernization Act” could result in jail time ranging between 10 years to life imprisonment.
“The ‘Cyber Conspiracy Modernization Act’ would amend the CFAA to create a specific penalty for the crime of conspiracy under the CFAA,” reads a statement from Sen. Mike Rounds (R-S.D.) who introduced the bill along with Sen. Kirsten Gillibrand (D-N.Y.)
6 - Report: Global ransomware attacks up in 2024
Ransomware attacks grew 15% worldwide last year, compared with 2023, as ransomware gangs showed a growing interest not just in encrypting data but in stealing it to further monetize it.
That’s according to NCC Group’s “Cyber Threat Intelligence Annual Report 2024,” which also found that the industrials sector was the hardest hit, suffering 27% of ransomware attacks, a sign of ransomware groups' focus on critical infrastructure organizations.

A trend that developed last year was the increasing interest among ransomware gangs on swiping data, not just locking it up in exchange for payment. Why? Stealing data is “faster, easier and more profitable,” according to NCC Group.
“Stolen information can be leveraged for extortion, fraud, identity theft, or even future breaches, making it a highly valuable commodity in the hands of cybercriminals,” reads the report.
The 5,263 ransomware attacks observed by NCC Group in 2024 were the most since it started monitoring them in 2021. Despite getting hit by law enforcement operations, LockBit ranked first among ransomware groups with 10% of all attacks, followed by RansomHub.
For more information about ransomware:
- “Ransomware: Predictions and Actions in 2025” (SC Magazine)
- "Stop Ransomware Guide" (CISA)
- “New ransomware group Funksec is quickly gaining traction” (CSO)
- “Ransomware isn't always about the money: Government spies have objectives, too” (The Register)
- “How ransomware attacks like Columbus' happen” (Axios)
- Cloud
- Cybersecurity Snapshot
- Federal
- Government


