Cybersecurity Snapshot: Five Eyes Rank 2023’s Most Frequently Exploited CVEs, While CSA Publishes Framework for AI System Audits

Check out the CVEs attackers targeted the most last year, along with mitigation tips. Plus, a new guide says AI system audits must go beyond check-box compliance. Meanwhile, a report foresees stronger AI use by defenders and hackers in 2025. And get the latest on cloud security, SMBs' MFA use and the CIS Benchmarks.
Dive into six things that are top of mind for the week ending Nov. 15.
1 - Report ranks 2023’s most frequently exploited vulnerabilities
Wondering what were attackers’ preferred vulnerabilities last year? Cyber agencies from the Five Eyes countries have ranked these go-to bugs in a joint advisory titled “2023 Top Routinely Exploited Vulnerabilities.”
Published this week, the advisory details the 47 Common Vulnerabilities and Exposures (CVEs) that attackers most often exploited in 2023, along with their associated Common Weakness Enumerations (CWEs).
The advisory also offers prevention and mitigation recommendations both to end-user organizations, and to software vendors and developers.
A key takeaway: the majority of the CVEs listed were initially exploited as zero-days, unlike in 2022, when fewer than half were. In addition, the report found that attackers typically strike gold with vulnerabilities that are less than two years old.

Here are some of the recommendations from the authoring cyber agencies in Australia, Canada, New Zealand, the U.K. and the U.S. for end-user organizations:
- Update software, including operating systems, applications and firmware, and prioritize patching CVEs included in CISA’s Known Exploited Vulnerabilities (KEV) catalog, especially those listed in the report.
- Maintain a continuously updated inventory of all your assets – both hardware and software, and on-prem and in the cloud.
- Deploy an automated, centralized patch-management system and adopt a patch-management process.
- Document the secure baseline configurations for all IT/OT systems.
- Require phishing-resistant multi-factor authentication for all users and on all VPN connections.
- Adopt the principle of least privilege when configuring access control.
- Secure internet-facing devices.
- Monitor your attack surface continuously.
- Contractually require your software vendors to provide you with software bills of materials (SBOMs) for their products, and inquire whether they employ secure-by-design principles.
The five CVEs atop the list are:
To get all the details, read the full advisory “2023 Top Routinely Exploited Vulnerabilities.”
For more information about vulnerability management, check out these Tenable resources:
- “From Bugs to Breaches: 25 Significant CVEs As MITRE CVE Turns 25” (blog)
- “Turning Data into Action: Intelligence-Driven Vulnerability Management” (blog)
- “Context Is King: From Vulnerability Management to Exposure Management” (blog)
- “Secure Your Sprawling Attack Surface With Risk-based Vulnerability Management” (blog)
- “Mitigating AI-Related Security Risks: Insights and Strategies with Tenable AI Aware” (on-demand webinar)
2 - CSA: AI systems require holistic audits
When it comes to auditing artificial intelligence (AI) systems, auditors need to go beyond basic regulatory compliance requirements, and instead aim to assess their trustworthiness in a holistic, comprehensive manner.
That’s the main message in the Cloud Security Alliance’s new report “Artificial Intelligence (AI) Risk Management: Thinking Beyond Regulatory Boundaries,” which was published this week and offers a risk-based framework for auditing AI systems throughout their lifecycle.
While it’s critical for AI audits to be accurate, “trust in AI can only be achieved through a far-reaching approach to auditing that goes beyond what’s required,” researcher Ryan Gifford, a leader in the CSA’s AI Governance & Compliance Working Group, said in a statement.

The paper addresses a wide range of AI audit elements, including AI governance; the role of data and sensors; applicable laws, regulations and standards; data and privacy; algorithms, training methods and models; and security systems – to name just a few.
The 101-page document also includes hundreds of suggested questions to include in an AI audit, covering 25 topics.
For example, the paper suggests 19 questions to ask about AI security systems, organized into seven sub-categories, including authentication and access control; data sanitization; encryption and key management; and security monitoring.
These are just a few of the questions in the AI security systems section:
- How are security vulnerabilities actively identified and mitigated in software and hardware components? Through regular updates and patching?
- How is security data from multiple sources integrated and analyzed to provide a centralized platform for threat detection, incident response, and comprehensive security monitoring?
- How is the legitimacy of people and system accounts requesting access confirmed?
- Which authentication methods are used to ensure that only authorized entities gain access?
For more information about AI system audits:
- “Auditing AI: The emerging battlefield of transparency and assessment” (Thomson Reuters)
- “AI transparency: What is it and why do we need it?” (TechTarget)
- “US agency calls for audits of AI systems to ensure accountability” (Roll Call)
- “Navigating the AI Audit: A Comprehensive Guide to Best Practices” (Law.com)
- “Trust but verify: Digging into audits for AI algorithm bias” (TechTarget)
3 - Google: Attackers will deepen AI use in 2025
Expect the AI cyberwars to get nastier and more sophisticated next year.
In 2025, hackers will double down on their use of AI to boost their cyberattacks, while security teams will further leverage AI security tools to improve their cyberdefenses.
That’s one of the main takeaways from Google Cloud’s “Cybersecurity Forecast 2025” report, released this week.
“While AI is rapidly bringing new tools for threat detection and response, it also provides malicious actors with powerful capabilities for social engineering, disinformation, and other attacks,” reads the report.
Here are some ways in which Google Cloud expects cyberattackers to more aggressively employ generative AI tools, LLMs, deepfakes and other AI technologies in 2025:
- To further scale and enhance social engineering attacks, including phishing and vishing
- To supercharge cybercrime and cyberespionage
- To research vulnerabilities they can exploit
- To streamline and accelerate development of malicious code
- To rapidly create content for disinformation campaigns
“As AI capabilities become more widely available throughout 2025, enterprises will increasingly struggle to defend themselves against these more frequent and effective compromises,” the report reads.
By the same token, cybersecurity teams will move into what the report calls “a second phase” of AI use. During the first phase, defenders used AI tools for repetitive tasks, such as summarizing reports and querying data sets. In 2025, cybersecurity teams will extend their AI use towards “semi-autonomous” security operations.
“This includes being able to parse through alerts - even with false positives - to create a list of the highest priority items, enabling security teams to further triage and remediate the risks that matter most,” the report reads.
However, the output of these AI security operations will still need to be verified by a security professional.
The report also looks at how trends like geopolitical cyberthreats, ransomware and infostealer malware are likely to develop in 2025.
For more information about cloud security trends:
- “Who’s Afraid of a Toxic Cloud Trilogy?” (Tenable)
- “Top Ten Cloud Security Mitigation Strategies” (U.S. National Security Agency)
- “What is cloud security management? A strategic guide” (TechTarget)
- “How to choose, configure and use cloud services securely” (U.K. National Cyber Security Centre)
- “How To Protect Your Cloud Environments and Prevent Data Breaches” (Tenable)
4 - Tenable poll looks at cloud security practices
During our recent webinar “Empower Your 2025 Cloud Security Planning with Tenable's Data Insights,” we informally polled attendees about cloud security issues, such as workloads afflicted by the “toxic trilogy” of cloud risks. Check out the results!
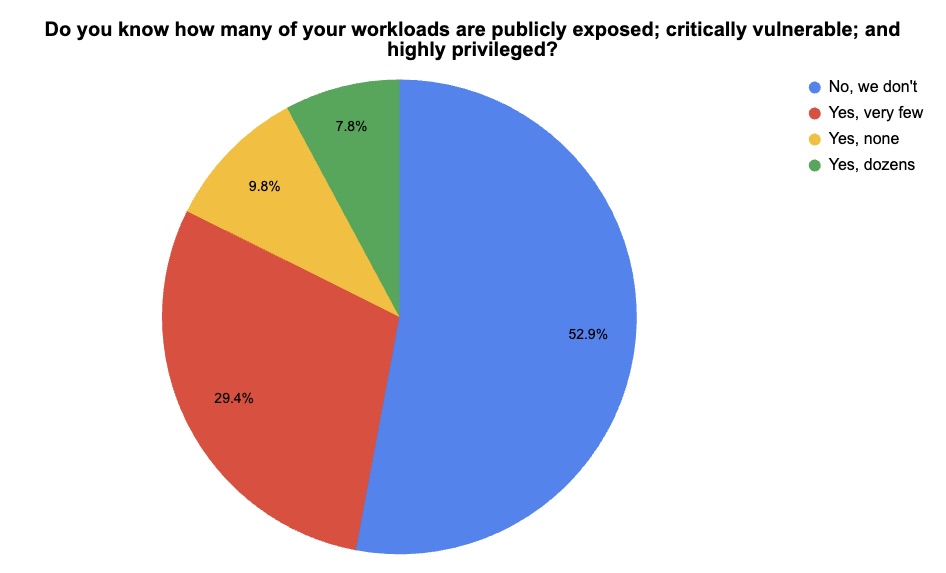
(51 webinar attendees polled by Tenable, November 2024)
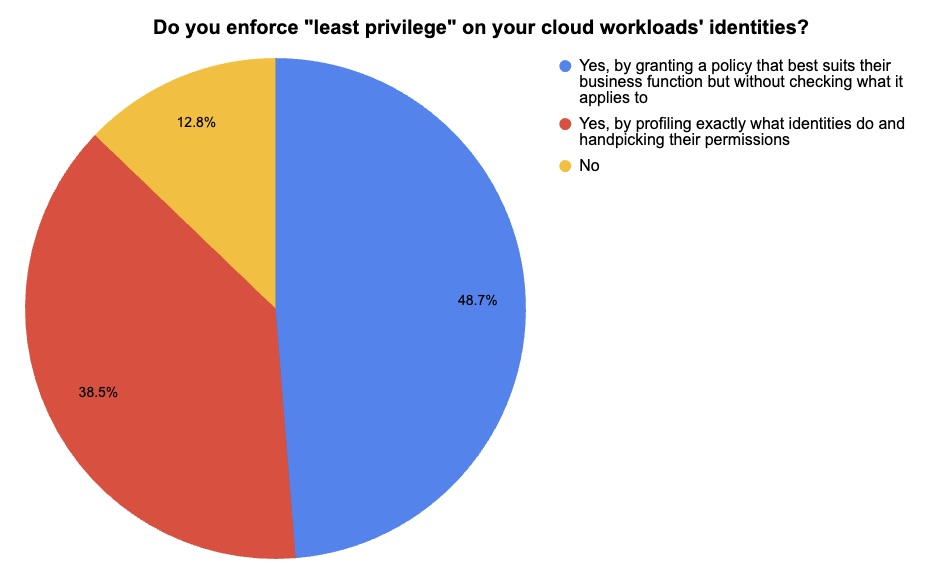
(39 webinar attendees polled by Tenable, November 2024)
Check out this on-demand webinar for a discussion of the valuable insights in the new “Tenable Cloud Risk Report 2024,” including concrete recommendations for improving your organization’s cloud security.
5 - Report: MFA widely underused, misunderstood by SMBs
A majority of small and medium-sized businesses (SMBs) surveyed about multi-factor authentication (MFA) haven’t adopted this identity and access management (IAM) technology and ignore its security benefits.
That’s a key finding from a report based on a global survey of almost 2,300 SMBs conducted by the Cyber Readiness Institute (CRI) and published this week.
“MFA is no longer a luxury or optional security measure - it is a fundamental necessity in today’s digital landscape. The time for SMBs to act is now,” the report reads.
Specifically, 65% of SMBs polled said they haven’t implemented MFA, and most of them (61%) have no plans to adopt MFA in the foreseeable future.
Barriers to adoption include:
- the cost to acquire and deploy MFA tools
- lack of technical expertise to choose the right product
- lack of awareness about MFA's benefits
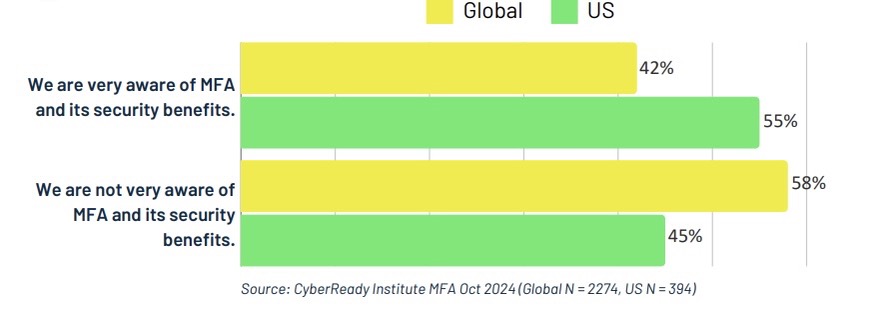
A bright spot for MFA adoption is the U.S., where SMBs buck the global trend, with 89% of respondents saying they’ve adopted the technology, and 55% saying they’re “very aware” of MFA and its benefits.
The following best describes the level of awareness you have of MFA and the related security benefits at your company
So what can be done to promote MFA adoption among SMBs? Here are some recommendations from the report:
- Government agencies, industry groups, non-profit organizations and cybersecurity vendors should collaborate on campaigns to educate SMBs about the benefits of MFA.
- Software vendors should include MFA capabilities as part of broader software packages at no additional cost.
- Governments should offer incentives to SMBs, such as tax breaks and subsidies, while larger businesses should reward their SMB partners that adopt MFA.
- Vendors, government agencies and industry groups should offer SMBs technical assistance after they adopt MFA to ensure their continued success with the technology.
To get more details, read:
- The CRI report “Unlocking MFA Adoption: Why Small and Medium-Sized Businesses Must Act Now to Strengthen Their Cybersecurity”
- The report’s announcement “New Study Underscores Slow Adoption of Multifactor Authentication By Global SMBs”
6 - CIS Benchmarks for Apple, Azure, Oracle get updated
The Center for Internet Security (CIS) just announced the latest updates to its CIS Benchmarks, including the ones for Azure Kubernetes Service (AKS), Oracle Cloud Infrastructure for Kubernetes (OKE) and several versions of Apple's macOS.
Specifically, these CIS Benchmarks were updated in October:
- CIS Amazon Web Services Foundations Benchmark v4.0.0
- CIS Apple macOS 13.0 Ventura Benchmark v3.0.0
- CIS Apple macOS 14.0 Sonoma Benchmark v2.0.0
- CIS Apple macOS 13.0 Ventura Cloud-tailored Benchmark v1.1.0
- CIS Azure Kubernetes Service (AKS) Benchmark v1.6.0
- CIS MongoDB 6 Benchmark v1.2.0
- CIS MongoDB 7 Benchmark v1.1.0
- CIS Oracle Cloud Infrastructure for Kubernetes (OKE) Benchmark v1.6.0
- CIS SUSE Linux Enterprise 12 Benchmark v3.2.0
In addition, these three new CIS Benchmarks were released:
- CIS Apple iOS 18 Benchmark v1.0.0
- CIS Apple iPadOS 18 Benchmark v1.0.0
- CIS Apple macOS 15.0 Sequoia Benchmark v1.0.0

The CIS Benchmarks’ secure-configuration guidelines are designed to help security teams harden software against attacks. There are currently more than 100 Benchmarks for 25-plus vendor product families. There are CIS Benchmarks for cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks November 2024 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
- AI
- Cloud
- Compliance
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government


