Cybersecurity Snapshot: NIST Program Probes AI Cyber and Privacy Risks, as U.S. Gov’t Tackles Automotive IoT Threat from Russia, China

A new NIST program will revise security frameworks like NIST’s CSF as AI risks intensify. Plus, the U.S. may ban cars with Russian and Chinese IoT components. Meanwhile, the CSA adds AI insights to its zero trust guide. And get the latest on cybersecurity budgets, SBOMs and the Ghost cybercrime platform!
Dive into six things that are top of mind for the week ending September 27.
1 - NIST unveils program for AI privacy and cybersecurity
How will AI advancements impact risks to cybersecurity and privacy? How should existing frameworks be adapted? What new resources will have to be developed?
These are some of the key questions the new Cybersecurity, Privacy, and AI Program from the National Institute of Standards and Technology (NIST) will seek to answer.
The program will focus both on “the cybersecurity and privacy of AI” and on “the use of AI for cybersecurity and privacy,” Katerina Megas, who leads the NIST Cybersecurity for the Internet of Things (IoT) Program, wrote in a blog.
“The program will coordinate with other NIST programs, federal agencies, and commercial entities as needed to ensure a holistic approach to addressing AI-related cybersecurity and privacy challenges and opportunities,” Megas wrote.

Part of the program is the creation of a “community profile” to adapt security frameworks, starting with the NIST Cybersecurity Framework (CSF), as AI technology – and its risks – quickly evolve.
For starters, the AI community profile will focus on:
- Cybersecurity and privacy risks faced by organizations that use AI
- Defenses against AI-enabled attacks
- Ways for organizations to use AI to boost their cyber defenses and privacy protections
To join the AI community profile effort, you can visit the project’s home page and enter your information.
For more information about AI and cybersecurity, check out these Tenable blogs:
- “Do You Think You Have No AI Exposures? Think Again”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
- “Never Trust User Inputs -- And AI Isn't an Exception: A Security-First Approach”
- “AI Is About To Take Cybersecurity By Storm: Here's What You Can Expect”
- “Compromising Microsoft's AI Healthcare Chatbot Service”
2 - U.S. gov’t to ban cars with Russian, Chinese IoT components
Citing national security concerns, the U.S. Department of Commerce wants to ban digitally connected vehicles that have components made in Russia and China, a move that spotlights automotive IoT’s cyber risk potential.
Specifically, the proposed rule would impact vehicle-connectivity systems (VCS) and automated driving systems (ADS). VCS wares enable vehicles to exchange data with external systems via Bluetooth, cellular, satellite and Wi-Fi modules. Meanwhile, ADS equipment allows vehicles to operate without a driver.
“Commerce has determined that certain technologies used in connected vehicles from the PRC and Russia present particularly acute threats. These countries of concern could use critical technologies within our supply chains for surveillance and sabotage to undermine national security,” reads a White House statement issued this week.

For example, Russia and China could use connected cars to capture data about U.S. geographical areas, infrastructure and critical infrastructure facilities. They could also tamper with the operation of the vehicles.
VCS and ADS software made by manufacturers “with a sufficient nexus” to the Chinese and Russian governments would be banned starting with 2027 vehicle models. Meanwhile, VCS hardware would be prohibited starting with 2030 vehicle models.
For more information about automotive cybersecurity and protecting automotive IoT devices:
- “Cybersecurity Concerns Rise in the Automotive Industry” (IoT World Today)
- “Software-Defined Vehicle Fleets Face a Twisty Road on Cybersecurity” (Dark Reading)
- “Increased Automotive Data Use Raises Privacy, Security Concerns” (Semiconductor Engineering)
- “The Internet of Things (IoT) in the Automotive Market: Driving the Future of Transportation” (IoT Business News)
- “Internet Connected Cars are vulnerable to attacks: Report” (CISO Mag)
3 - CSA updates zero trust paper with AI insights
Need clarity on how artificial intelligence intersects with the zero trust security model? Check out the new version of the Cloud Security Alliance’s “Zero Trust Guiding Principles” paper, which has been updated throughout with references to AI.
At a high level, version 1.1 of the paper addresses how AI can help you adopt a Zero Trust framework, and it also explains how zero trust can help you secure your AI systems.
“AI can aid with the implementation of a Zero Trust initiative, and Zero Trust principles should be applied in securing the use of AI, including AI models and training data,” the paper reads.
The first version of “Zero Trust Guiding Principles,” published in mid-2023, barely touched on the confluence of AI and zero trust. Thus, this revision is worth checking out even for people who read version 1.0.

The main goal of the “Zero Trust Guiding Principles” paper is to clearly explain zero trust, a concept that, according to the paper, “is often misunderstood and overcomplicated.”
“When properly understood, Zero Trust philosophy and strategy are valuable tools that organizations can use to enhance security, increase resilience, and guide digital transformation,” the paper reads.
Eleven guiding principles are discussed in the paper, including:
- Begin by determining your intended outcomes, which can be things like cutting costs, boosting your governance and compliance program and reducing IT complexity.
- Breaches will happen, so focus on strengthening your resilience.
- Be clear about the level of risk your organization can tolerate.
- Start small and look for quick wins.
- Monitor continuously.
For more information about the intersection of AI and zero trust:
- “The Future of Zero Trust with AI: Exploring How AI Automates and Enhances Security” (Security Boulevard)
- “Four Pragmatic Ways AI is Already Improving Zero Trust Network” (The Fast Mode)
- “Zero Trust and AI: Better Together” (Mastercard)
- “Confronting Shadow Access Risks: Considerations for Zero Trust and Artificial Intelligence Deployments” (Cloud Security Alliance)
- “Zero Trust AI Governance” (AI Now Institute)
4 - CISO survey: Security budgets up 8% over 2023
Cybersecurity budgets grew 8% on average in 2024, compared with last year, as cybersecurity’s slice of the overall IT budget increased to 13.2% – almost five percentage points higher than in 2020.
Those stats come from the “2024 Security Budget Benchmark Summary Report” by IANS Research and Artico Search, based on a survey of 750-plus CISOs in the U.S. and Canada.
The major drivers of budget increases were the occurrence of a security incident or breach; and a change in an organization’s risk tolerance. Each triggered an average cybersecurity-budget increase of 26% in 2024.
Other major triggers for cybersecurity budget increases were a company repositioning; regulatory requirements; and company growth. Any of these three led to an average budget bump of 17%.
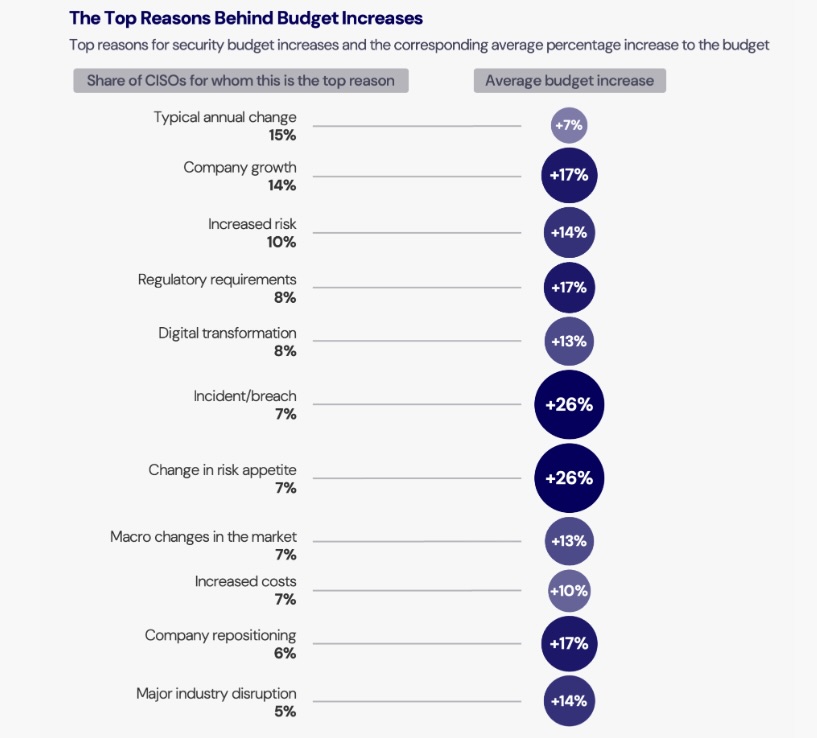
(Source: “2024 Security Budget Benchmark Summary Report” by IANS Research and Artico Search, September 2024)
While the 8% average growth in cybersecurity budgets was higher than the 6% recorded in 2023, it’s smaller than the double-digit percentage increases reported in 2021 and 2022 – 16% and 17% respectively.
“During those years, many organizations were still in catch-up mode regarding their cybersecurity programs,” reads an IANS blog about the 2024 cybersecurity budgets report.
That budget “hypergrowth” period has ended, as many organizations have brought their cybersecurity spending up to appropriate levels. At these organizations, the cybersecurity function “is better understood due to increased collaboration among CISOs, the leadership team and the board of directors,” the blog reads.
Overall, about two thirds of respondents reported a budget increase in 2024, while a quarter of respondents said their budget stayed flat and 12% experienced a cut.
Meanwhile, as a percentage of revenue, security budgets grew from 0.50% to 0.69% compared with last year.
To get more details, check out:
- The blog “2024 Security Budget Benchmark Report: Key Findings”
- The “2024 Security Budget Benchmark Summary Report”
For more information about cybersecurity budget trends:
- “Cybersecurity Budgets in 2024: What Tech and Security Pros Need to Know” (Dice)
- “Almost 60% of corporate cybersecurity budgets are higher this year: report” (CFO Dive)
- “Budgets rise as IT decision-makers ramp up cyber security spending” (ComputerWeekly)
- “The C-suite playbook: Putting security at the epicenter of innovation” (PwC)
5 - NCSC outlines SBOM basics
Not entirely clear about what a software bill of materials (SBOM) is and how it can help your organization better secure its software supply chain? A new article from the U.K. National Cyber Security Centre (NCSC) could help clear things up for you.
Titled “SBOMs and the importance of inventory,” the article explains why – in theory – an SBOM can offer valuable visibility into the components of a piece of software. It also points out that an SBOM’s efficacy will depend on a variety of factors, including:
- Your organization’s software development processes and practices
- Your staff’s experience
- Your organization’s risk tolerance
In other words, an SBOM isn’t a silver bullet.
“The mere presence of an SBOM does not guarantee that a supply chain is secure, and is not the answer to resolving all your supply chain risks,” the article reads.
To get all the details, read the article: “SBOMs and the importance of inventory,”
For more information about SBOMs:
- “CISA Aiming to Improve SBOM Implementation With New Guidance” (Bank Infosecurity)
- “US Government and OpenSSF Partner on New SBOM Management Tool” (Infosecurity Magazine)
- “How to create an SBOM, with example and template” (TechTarget)
- “SBOMs – Software Supply Chain Security’s Future or Fantasy?” (SecurityWeek)
- “SBOMs and security: What IT and DevOps need to know” (TechTarget)
VIDEOS
Leveraging SBOM Practices to Facilitate Risk Reduction (Carnegie Mellon University)
An SBOM Primer (The Linux Foundation)
6 - Int’l police operation dismantles Ghost criminal comms platform
Ghost, an encrypted communications platform built for cybercriminals about nine years ago, has been taken down.
That’s according to the Australian Federal Police (AFP), which led a multi-national law enforcement effort dubbed Operation Kraken that has netted at least 38 arrests.
Among those arrested is a 32-year old Australian man charged with the creation and management of Ghost, whose messages the AFP decrypted and read.
The man, the first Australian accused of masterminding and managing a global criminal platform, allegedly sold modified smartphones with a subscription to an encrypted network.
Ghost became popular among cybercriminals thanks to its sophisticated security offerings, including its use of three encryption standards and a self-destruct mechanism for messages.
“This allowed criminal networks to communicate securely, evade detection, counter forensic measures, and coordinate their illegal operations across borders,” reads an Europol statement.
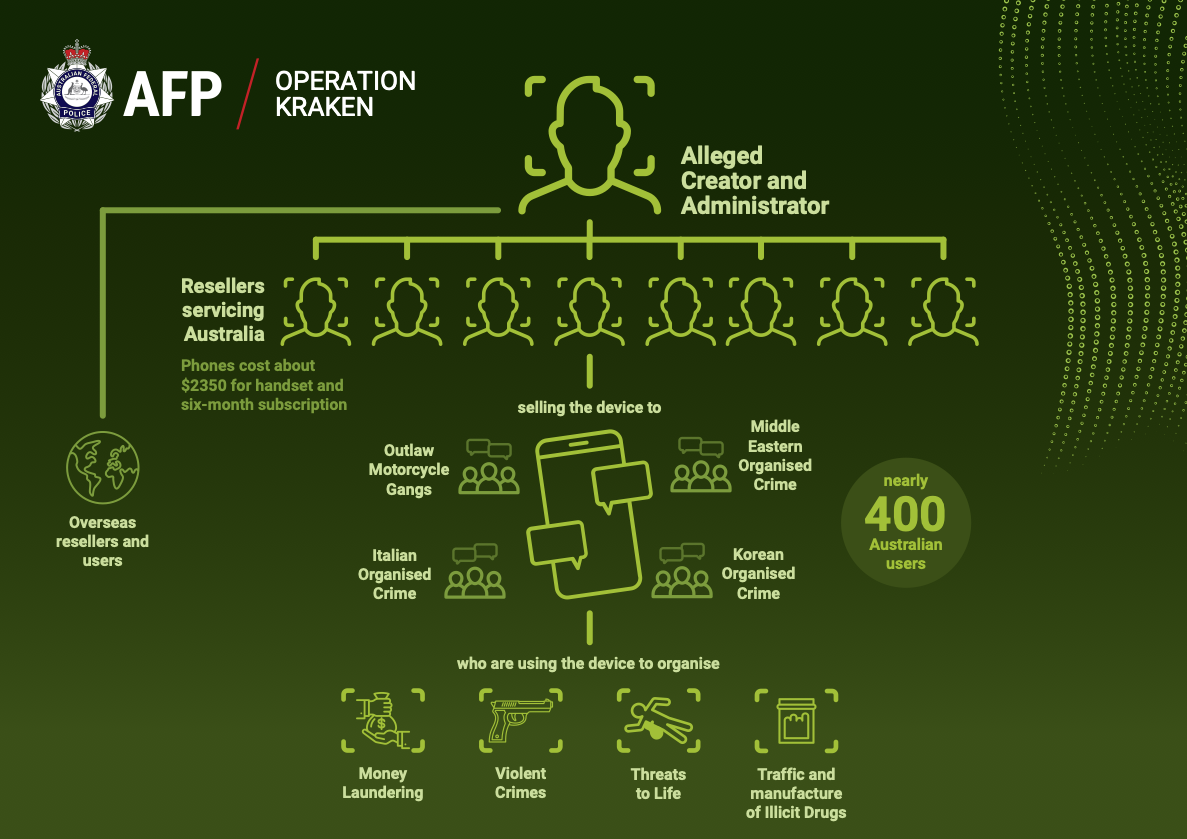
About 50 Australians face serious charges for using Ghost to sell illicit drugs, launder money, order killings and threaten to commit acts of violence.
Related law-enforcement action took place in Canada, Italy, Ireland and Sweden.
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Risk-based Vulnerability Management


