Frequently Asked Questions About Model Context Protocol (MCP) and Integrating with AI for Agentic Applications

The emergence of Model Context Protocol for AI is gaining significant interest due to its standardization of connecting external data sources to large language models (LLMs). While these updates are good news for AI developers, they raise some security concerns. In this blog we address FAQs about MCP.
Background
Tenable Research has compiled this blog to answer Frequently Asked Questions (FAQ) regarding Model Context Protocol (MCP).
FAQ
What is Model Context Protocol (MCP)?
Model Context Protocol (MCP) is an open-source standard created by Anthropic that provides a universal method to connect external data and actions to large language models (LLMs). It provides the methods to allow an LLM to detect what resources it has at its disposal, and understand when and why it would use those resources to answer or enhance the task it is working on.
Examples of external data that an AI could access include local file systems, databases, APIs, SaaS applications and more.
In a way, the MCP allows an LLM to provide a deterministic request of data or actions to assist in answering questions with data outside of its training.
MCP is quickly becoming a standard that many AI companies are implementing.
Why is there so much interest in MCP?
MCP is gaining significant interest due to its standardization of connecting external data sources to LLMs. A developer can now write an integration for an LLM once and use it across a variety of tools and LLMs that utilize MCP. "App stores" and "marketplaces" of MCP servers are available for quick integration into your environment. Services to help create custom MCP servers specifically for you are available.
Is this the first time LLMs could interact with external data and sources?
Agentic AI, which has the capacity to act autonomously, can take actions and work with external sources, but implementation is unique to each tool. Solutions like LangFlow help by standardizing some of the tooling and can interact with multiple LLMs within its specific framework. However, the MCP specification takes this standardization to the next level, where an integration can be created and used across multiple solutions.
How do I get started working with MCP?
MCP requires a host application, colloquially called a client and a server. The host application orchestrates communication between an LLM and the interfaces that communicate with the MCP servers.
The foundational example is using Claude Desktop to add a filesystem MCP server, as outlined at Quickstart for Claude Desktop Users. This example shows what it takes to add a filesystem server to Claude Desktop to provide local filesystem information to Claude.ai. While Claude Desktop is the proving ground for MCP servers, many other clients exist that improve the user experience.
Online directories of MCP clients and servers are becoming available, such as MCP Clients | Glama and Open-Source MCP Servers | Glama.
How does MCP work?
MCP uses a client/server architecture to allow LLMs to interact with external data. This is accomplished using three primary components; host, client and server.
- A host application is used to manage the interaction between LLMs and a number of MCP clients. Many popular MCP hosts include Claude Desktop, Claude Code, Cursor, Windsurf, and editor integrations like Cline and Continue.
- The client is an interface that runs in the host application and allows the LLM to interact with the server by maintaining a one-to-one connection with a server.
- The server is a small application that communicates with the client using the MCP protocol, and provides standardized processes to list various capabilities as well as responds to requests for relevant data or actions.
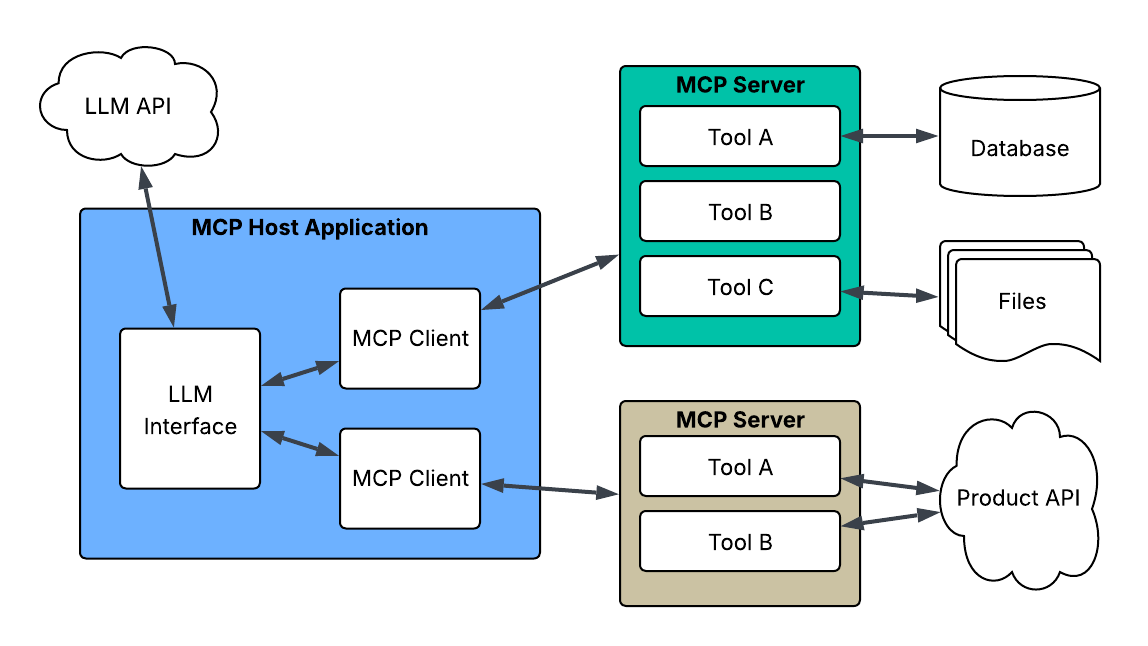
Source: Tenable, April 2025
While these components are discussed as separate components, they can be a part of a single application or separate applications. The most common configuration seen at time of publishing this FAQ consists of the client integrated into the host application and communicating to the server over secure transports using JSON-RPC.
What type of capabilities do MCP servers offer?
MCP servers offer different capabilities to clients to support the retrieval of data along with actions taken on data. The following capabilities are available:
- Resources are data stores available for the LLM to keep track of. These can include files, database schema information and console logs. Resources are loaded at time of a chat initiation and should be used to avoid repeated requests of static data.
- Tools take actions. Examples include retrieving content from files, inserting data into a database, replying to emails and more.
- Prompts allow the server to provide useful and reusable prompts to the client. Many implementations of the application hosts allow methods to list the prompts using a "quick list" concept, such as hitting a "/" key to bring up a list of prompts that are available. The prompts can also be used as templates that can be dynamically populated with user inputs.
Currently, "tools" are the most impactful capability offered by MCP and what garners much of the media's attention.
Is it safe for me to use MCP servers?
MCP relies heavily on trust.
- Trust that the host application is controlling access to the clients
- Trust that the client is using secured transports with the server
- Trust that the server has implemented secure practices when it is accessing resources
Users should seek out MCP servers from reputable sources. However, always remember to "trust but verify," and do not install unknown software in your environment.
How does the MCP host implement security?
The host application should implement controls that allow the user of the application to approve tools prior to using them. Many of the mainstream applications already have methods to verify that the tool usage is acceptable. For example, on the first time attempting to call the tool, Claude Desktop provides a choice of "use once" or "use for the entire chat session." Other applications, like Cline, may have a method to "auto approve" different tools or applications. The amount of information provided to the user in these verification dialogs can vary.
What controls are available for transport security?
There are two primary transports; STDIO and Server Sent Events (SSE).
- When the client and server exist on the same computer, STDIO is the preferred transport. STDIO sends the output of the client straight to the input of the server and the output of the server to the client. The transport can only be attacked if the local system is compromised.
- When the client and server do not exist on the same computer then SSE is used to transport the JSON messages over HTTP connections. This allows the communication to use standard HTTP security options, such as SSL transports and Open Authentication (OAuth) authorization.
Ok, so what are the biggest risks to using MCP?
The biggest risk to using MCP is the injection of malicious servers. Since all registered servers have a single point of reference in the host application and LLM, malicious servers can poison the LLM or abuse the tools of other legitimate servers. As the MCP ecosystem matures we expect to see formalization of concepts like MCP security certification, server integrity monitoring and standardization of logging for monitoring. We will begin to see MCP “App Stores” where collections of MCP servers can be easily pulled into existing tools from a central repository.
The specification for MCP highly recommends authentication and authorization for remote servers, but it is not required. However, developers of MCP servers may not consider the network security of the MCP servers and not implement these recommendations.
Any MCP servers that are remotely accessible can be susceptible to man in the middle attacks or remote attacks. Make sure any MCP servers that use a network based transport have implemented strong authentication and authorization.
What can I do to protect my information while using MCP?
As the technical solutions and capabilities for securing MCP solutions evolve the current recommendations are to use solid cybersecurity best practices. Some of the top things that you can do include the following:
- Detect and inventory your MCP installations and configurations across your environment. With MCP being in early adoption, this is not as simple as monitoring a centralized server, but more likely requires close inspection of endpoints for configuration files. Knowledge and approval of MCP usage is key to maintaining integrity in the environment.
- Control access and monitor the resources that MCP servers are accessing. Whether the resources are local to the endpoints or SaaS applications, monitoring the access of these resources through logging and auditing is a requirement.
- Train the people that are using MCP in their job duties. Make sure they understand the impact of a tool before authorizing its use. The core topics of the MCP specification is that the user must consent and authorize operations before use, and training will provide the understanding required to make that determination.
Is Tenable looking into safety and security concerns surrounding MCP implementations?
Yes, Tenable Research is actively researching MCPs and will be sharing more of our findings in future publications on the Tenable blog.
Get more information
- Exposure Management


