How Exploitable Are You?

As part of the vulnerability management team I am often asked, “Just how exposed are we to the vulnerabilities in this report?” Thinking about the question, I like to first understand the relationship between vulnerability and exploitability. Next, I want to understand the likelihood a vulnerability can be exploited. From these two steps, I can begin to communicate the exploitability of our assets to management and data owners. Tenable.io helps you better understand the question “How Exploitable are You” by the data presented in the Exploitable by Malware dashboard.
Vulnerabilities
In computer security, a vulnerability is a weakness that enables a malicious or unsuspecting user to gain access to privileged or unauthorized information. In the simplest form, a misconfiguration of file level permissions can grant unauthorized users access to a file, folder, application, or service that is unauthorized. In a more complex example, chunks of uninitialized memory may be mixed with valid data as discovered in Cloudflare services. Regardless of how simple or complex the vulnerability, the question quickly becomes can the vulnerability be exploited?
Exploits
An exploit is a piece of software, string of data, or series of commands that can be used to cause some unintended or unanticipated behavior of a computer system. The development of code used to exploit systems can be very difficult to develop in some cases and in others very simple.
Frameworks
Several well known security researchers decided that to truly test and understand the nature of exploiting a vulnerability, a framework was needed. A framework is an abstraction in which the foundation of the software provides the generic functionality, and users can write code modules to perform specific tasks. In this case, the developers of Metasploit, Core Impact and several others created a framework to leverage common attack techniques and delivery methods, while the users of the framework create the actual exploits. These frameworks can be used by inexperienced attackers to create an attack that may look much more sophisticated, because most of the hard work has been created by the framework. Once you understand how to leverage the framework to exploit a buffer overflow, replicating the attack can seem trivial. As the frameworks become more popular, the industry is seeing a rise in malware code that may have been developed using different frameworks.
The Tenable.io solution
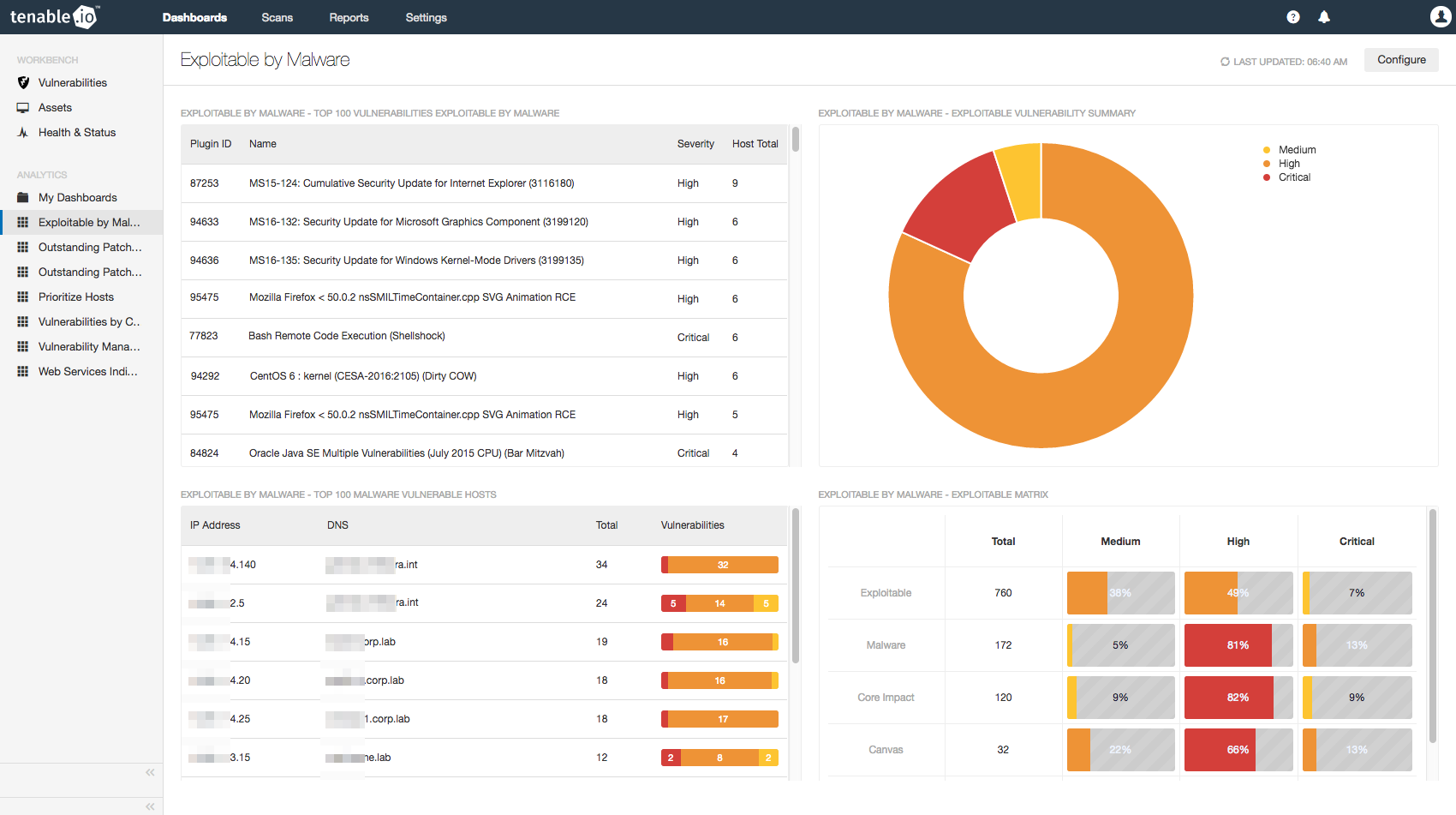
Tenable.io can easily identify systems that are more exploitable than other systems
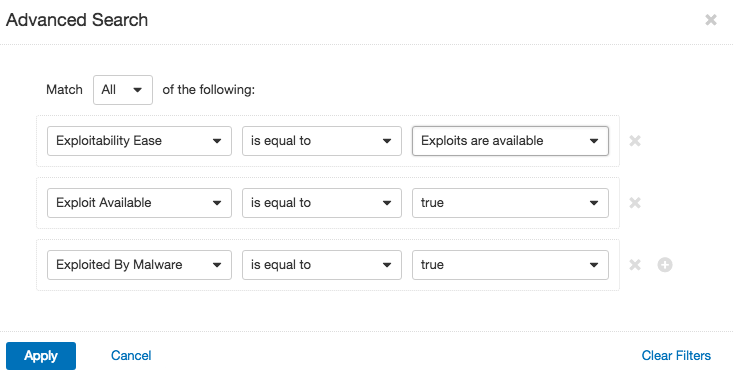
Tenable.io™ can easily identify systems that are more exploitable than other systems. There are several exploitability-related search fields, along with several fields that are related to common exploit frameworks. When using the Workbench, you can select the Advanced link and then add filters :
Now that you are able to identify the assets that are the most exploitable, you can determine if the systems are exploitable by known malware or by exploit frameworks. The field called Exploitable by Malware means that the exploit is known to exist in the wild. When performing the threat analysis, I like to include this as a key factor in assessing the risk to the asset. When identifying the assets that are exploitable by malware, I try to understand why the asset has not been patched. All too often, systems are not getting patched due to inconsistent patch cycles, inadequate patch management solutions, and overall lack of understanding about how the applications process data. Gaining an understanding of an application’s business function and criticality to overall business needs will lead to a more successful vulnerability management program.
Recently, in a discussion session with a university customer, we identified over 50 servers that have been running for over 4 years with no notable user activity. We reviewed the vulnerability state of these systems, and they were not only exploitable by malware, but also by many of the exploit frameworks. As we discussed how these systems could be either patched or removed, we began to see a bigger problem in the network. Many of the servers that were running, were either underutilized or not used at all. We then discussed the mitigation strategies with IT operations and received a lot of pushback based on the fact that none of the current admins knew why the systems were online and who owned the systems. The customer ultimately choose to implement a lengthy review process with all department heads in an attempt to establish ownership.
Regardless of your approach to mitigating risks identified by Tenable.io﹘by applying patches, configuring mitigation controls, or operating system hardening﹘the first step is to clearly qualify the risks into actionable tasks and deliverables. Tenable.io provides information security professionals with the tools and resources needed to perform a detailed qualitative analysis of the risk that threatens business assets. The Exploitable by Malware dashboard provides insight into your current risk exposure to exploitable vulnerabilities for both malware and exploit frameworks.
The Exploitable by Malware dashboard provides insight into your current risk exposure to exploitable vulnerabilities for both malware and exploit frameworks
Try Tenable.io
Tenable.io provides accurate information on how well your organization is addressing security risks, and helps track improvements over time. Get a free trial of Tenable.io Vulnerability Management for 60 days.
- Executive Management
- Vulnerability Management