How to Secure and Audit an Amazon Web Services Three-tier Web Architecture

In 2016, Tenable was the first Center for Internet Security (CIS) member to receive certification for the Amazon AWS Foundations benchmark. We’re pleased to announce that we’ve continued our leadership in orchestrating compliance for Amazon Web Services (AWS) environments by becoming the first and only vendor to obtain CIS certification for the AWS Three-tier Web Architecture benchmark.
AWS Three-tier Web Architecture overview
There are numerous considerations when you’re contemplating building an AWS web architecture in the AWS cloud. One popular pattern to use is an AWS three-tier architecture consisting of internet, application and database tiers. The internet tier, or web tier, contains the web servers necessary to drive functionality from the application tier. The application tier represents the user components, and the data tier consists of storage media which hold the data relevant to the application. Tenable.io® and the CIS benchmark assist customers with compliance and improve their overall security for an AWS Three-tier architecture.
Why audit an AWS Three-tier Web Architecture?
CIS security benchmarks provide organizations a baseline for securing resources and products. AWS is at the forefront of the cloud computing services. With the complexities associated with the cloud, this benchmark along with Tenable.io assists those customers searching to secure their AWS overall security posture. A secure AWS architecture is vital for an organization’s security hygiene. An example setting found in the benchmark is enabling encryption at rest within Relational Database Service (RDS). Without this configuration, an organization is risking their confidentiality of data stored in RDS.
In today’s security landscape filled with data transformation, it’s paramount to protect and audit your AWS environment. Tenable customers now have the ability to continue closing their Cyber Exposure gap by auditing their AWS Three-tier Web Architecture based upon the CIS benchmark.
CIS Amazon Web Services Three-tier Web Architecture Benchmark
CIS released the AWS Three-tier Web Architecture benchmark on the heels of releasing the latest CIS AWS Foundations Benchmark update. The AWS Three-tier Architecture Benchmark expands on the security configurations found in the Foundations Benchmark. It’s recommended that configurations found in the Foundations Benchmark be applied prior to completing the security settings found in the Foundations Benchmark. The following services are within scope of the benchmark:
- Elastic Compute Cloud (EC2) - API Version 2016-04-01
- Virtual Private Cloud (VPC) - API Version 2016-04-01
- Identity and Access Management (IAM) - API Version 2010-05-08
- AWS Config - API Version 2014-11-12
- CloudFront CDN - API Version 2016-01-13
- CloudWatch - API Version 2010-08-01
- Amazon Relational Database Service (RDS) - API Version 2014-10-31
- Simple Notification Service (SNS) - API Version 2010-03-31
- AWS Certificate Manager (ACM) - API Version 2015-12-08
- Key Management Service (KMS) - API Version 2014-11-01
The benchmark is divided into multiple sections:
Data protection
Data protection provides the security configurations necessary for protecting data that’s in transit and at rest. Key recommendations include:
- Ensuring databases running on RDS and all EBS volumes are encrypted
- Elastic Load Balancing (ELB) have the appropriate SSL Certificate and are using HTTPS listener
- All S3 buckets have secure policies enabled that require encryption for objects stored in buckets
Identity and access management
Identity and access management expands on the Identity and Access Management (IAM) section found in the Foundations benchmark. It builds upon the level of security for identification and access to the different AWS resources:
- Ensuring IAM policies exist for the EC2 IAM roles
- AutoScaling Group Launch-Configurations are configured appropriately
- SNS Topics do not allow the “Everyone” group to publish and subscribe
Business continuity
In today’s world, cybersecurity concerns and business continuity are inseparable. This section provides recommendations to help organizations build an effective AWS resiliency plan:
- Auto-Scaling Groups are associated with an ELB and are configured for multiple Availability Zones (AZs)
- Amazon Machine Images (AMIs) are configured for the Auto-Scaling Launch Configuration
- RDS backup retention policies are set in place
Event monitoring and response
Event monitoring and response builds off the Foundations Benchmark and includes detecting and responding to AWS events:
- SNS topics include appropriate notification for CloudWatch alarms
- RDS event subscriptions are enabled
- CloudWatch alarms are created for logs
Audit and logging
Continuing off the auditing and logging section for the Foundation benchmark, this section provides configurations necessary to support auditing AWS:
- Logging for ELB and CloudFront is enabled
- CloudWatch log groups are created
- Config rules for encrypted volumes are applied
- Config rules for EIPs are attached to EC2 instances
Networking
The networking section adds recommendations that provide security for the default virtual private cloud (VPC):
- Enable CloudFront content distribution network
- Ensure subnets are configured for each tier
- Routing tables have the default route defined to allow connection to the VPC gateway
- ELB Security Group is configured to accept HTTPS only
How to audit AWS Three-tier Architecture with Tenable using the CIS benchmark
To get started, log into Tenable.io and create a new Audit Cloud Infrastructure scan. In your scan configuration, select the Compliance tab. Under Amazon AWS, CIS Amazon Web Services Three-tier Web Architecture Benchmarks are now available. Due to AWS flexibility, the audit utilizes variables to ensure the checks are specific to your environment.
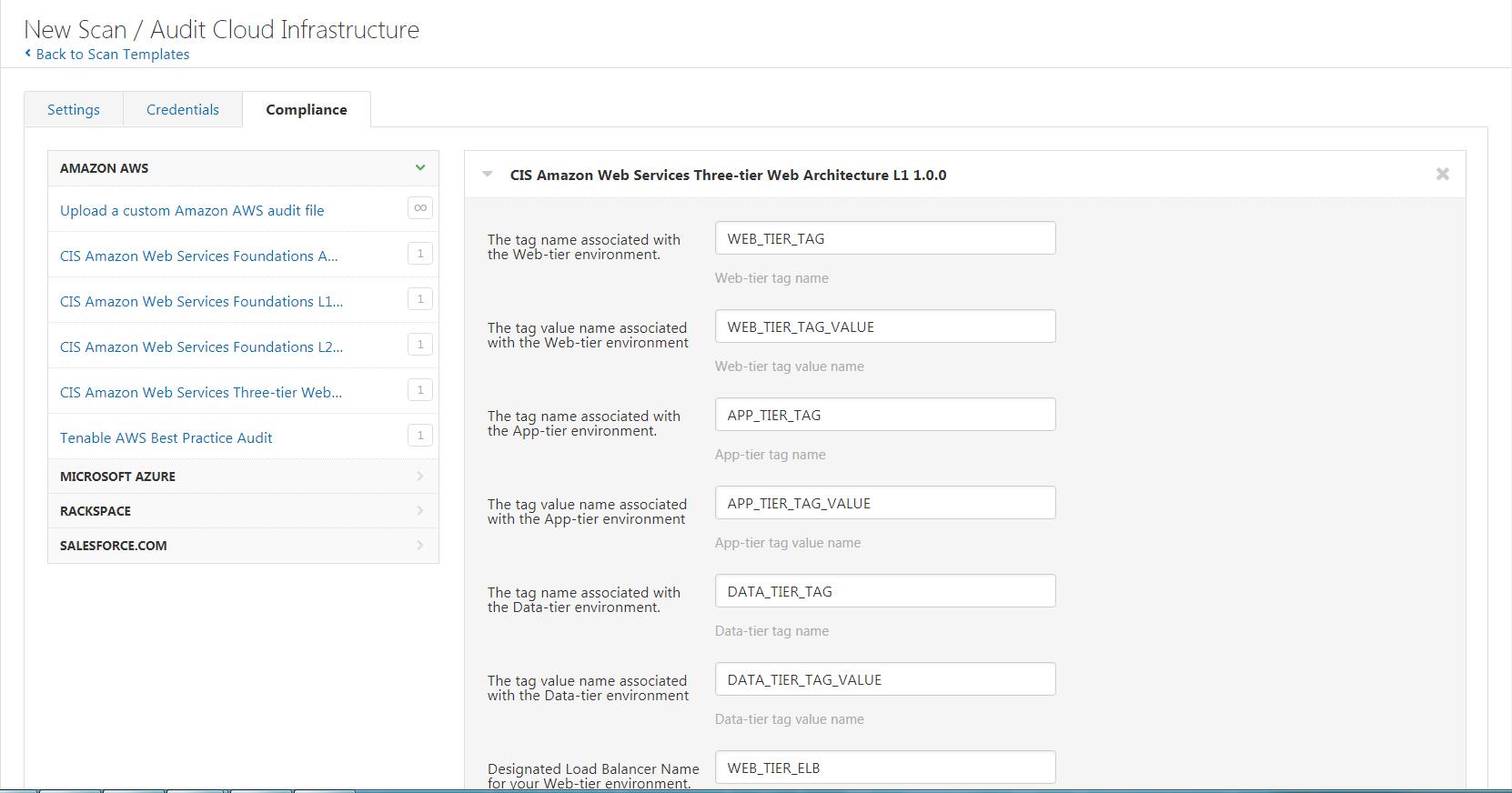
Once the configuration is saved, run the scan and review the results. Below is sample output from a scan.
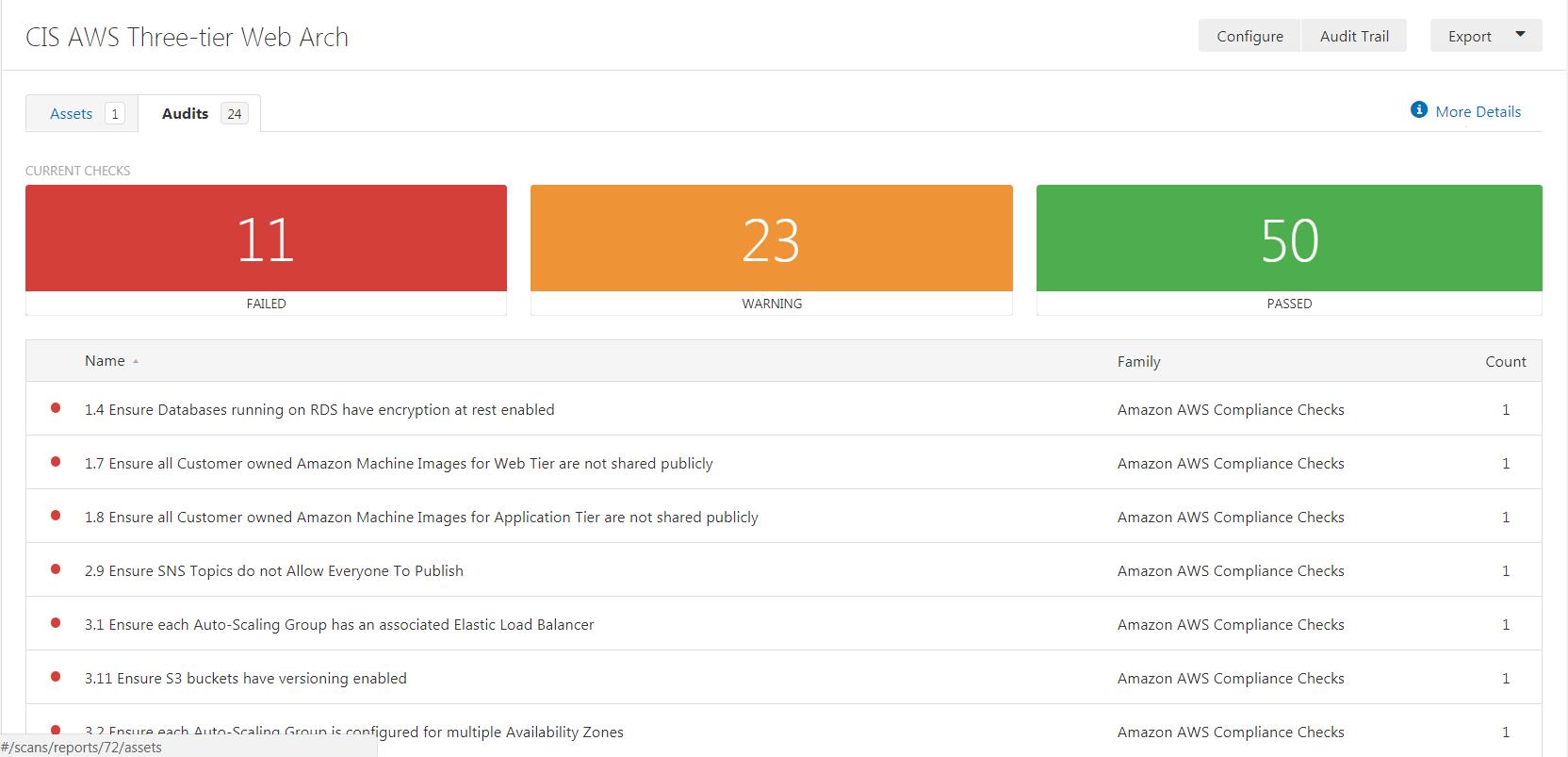
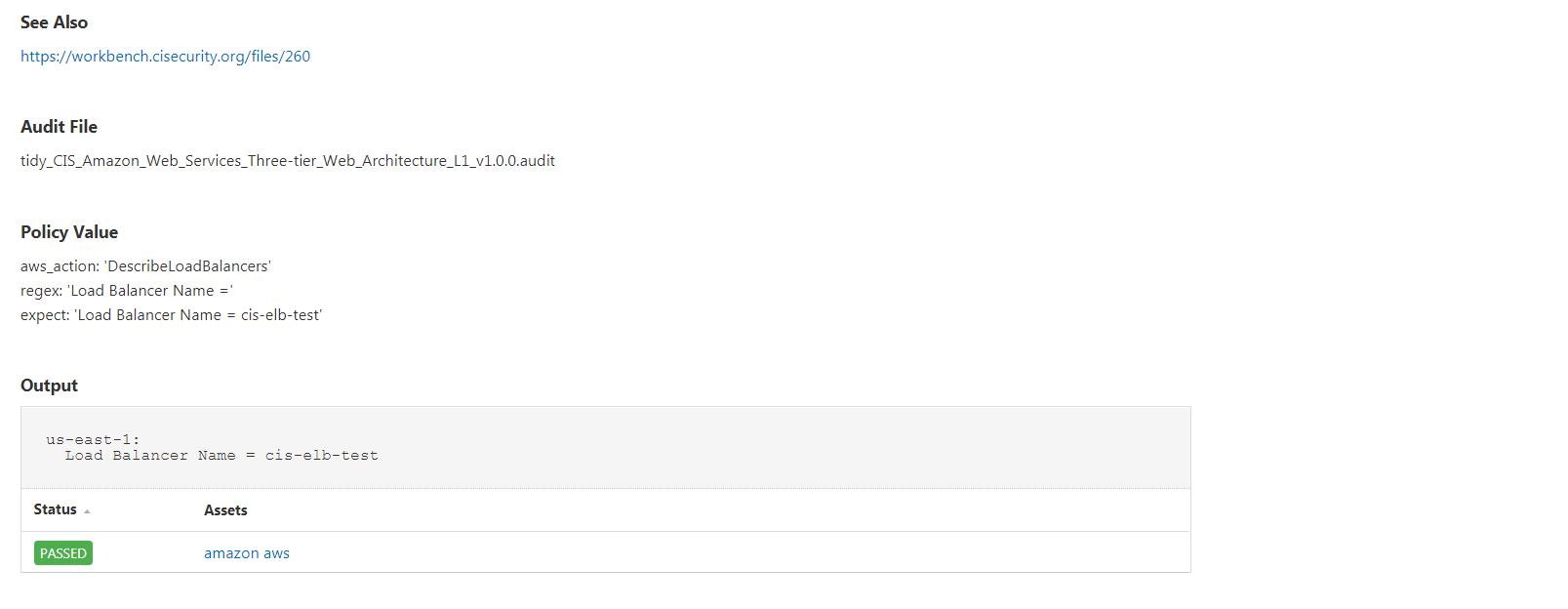
Below is a closer view of one of the results. This page shows:
- Pass/fail status
- Remediation steps, if necessary
- Individual results from the systems scanned
- Reference information to cybersecurity frameworks
Reduce your Cyber Exposure gap
We can help you reduce your organization's Cyber Exposure gap. One way of orchestrating this is by continuously updating our compliance audits and obtaining CIS certifications.
With Tenable.io, you can gain full visibility and maintain compliance across many public cloud infrastructures. In addition to AWS compliance scanning, Tenable offers solutions for Microsoft Azure, Rackspace and OpenStack. Start your free, 60-day Tenable.io trial now.