IDC Ranks Tenable No. 1 in Worldwide Device Vulnerability Management Market Share for the Fifth Consecutive Year

The research firm’s latest report also provides market insights that security professionals can use to improve their vulnerability management strategy.
IDC recently published its “Worldwide Device Vulnerability Management Market Share, 2022: Exposures Present a Clear and Present Danger''1 report, which presents the worldwide device vulnerability management market shares for 2022. For the fifth consecutive year, Tenable ranks first in market share.
The IDC report noted: “In August 2023, Tenable announced upcoming generative AI capabilities in Tenable One. ExposureAI will help summarize issues for customers around the significance of a discovered vulnerability in their environment and recommend how they should fix the issue. Users may also query the system using natural language. In October 2023, Tenable completed its acquisition of Ermetic, which offers CIEM and CNAPP. Tenable intends to incorporate these functions into the Tenable One Exposure Management Platform to discover additional vulnerabilities and misconfigurations in both on-premises and cloud environments.”
IDC’s report excerpt also provides insights into market developments, as well as advice for technology suppliers to ensure they’re aligned with future market needs. We believe Tenable’s vision and strategy aligns with advice from IDC, validating that we are well positioned to help your needs now and into the future.
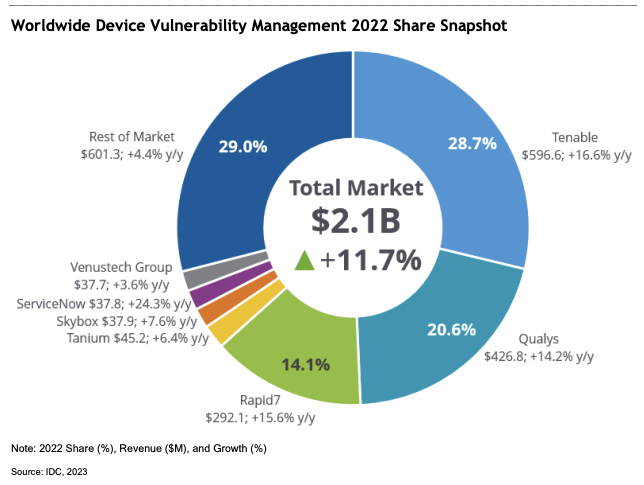
"Device vulnerability management vendors are turning their attention to offering holistic platforms that aggregate exposures and enable organizations to measure and communicate a unified view of cyber-risk," said Michelle Abraham, Research Director, Security and Trust at IDC. "Taking a proactive approach to cybersecurity through continuous monitoring of exposures helps organizations reduce their attack surface and, in some cases, their cyber insurance premiums, so the vulnerability management solution pays for itself."
IDC notes that although organizations have invested in vulnerability scanning tools, many still do not utilize their capabilities. IDC recommends a variety of features that vulnerability management vendors should offer their customers. Those recommendations, along with how we believe Tenable offers those capabilities within our Tenable One Exposure Management Platform, are listed below:
IDC Recommendation: Increase scanning frequency and prioritize high-risk vulnerabilities. Device vulnerability management vendors should guide customers towards a mature vulnerability management program by increasing scanning frequency and prioritizing high-risk vulnerabilities. This way, customers will benefit from a proactive approach to threat mitigation and from a more robust and proactive security posture. By following this recommendation, the vulnerability management platform will not only identify vulnerabilities but also guide efficient remediation efforts based on the risk level, reducing the likelihood of successful attacks.
Tenable opinion: Tenable offers advanced risk prioritization algorithms to automatically identify and flag high-risk vulnerabilities. By providing clear insights into the potential impact of these vulnerabilities, Tenable helps customers in making informed remediation decisions.
IDC Recommendation: Provide details on all assets, including those not in the configuration management database (CMDB). Device vulnerability management vendors should offer customers a comprehensive view of all assets, including those not traditionally recorded in the CMDB (such as mobile devices, proprietary storage devices, and network appliances), to eliminate blind spots and establish a baseline for effective risk management.
This broader asset visibility gives customers a holistic understanding of their attack surface, reducing the risk of overlooking critical assets.
Tenable opinion: With integrations with popular asset management tools, Tenable ensures users will have a comprehensive asset view. Tenable provides easy-to-use connectors for quick and seamless integration, minimizing the implementation efforts for buyers. For example, our integration with ServiceNow streamlines asset management processes, enhancing overall operational efficiency.
IDC Recommendation: Move beyond CVEs to holistic exposure management. Device vulnerability management vendors should bring more point tools together (such as device vulnerability scanners, attack surface management (ASM), cloud platforms, cybersecurity asset management, and IoT/OT scanners) to move vulnerability management beyond CVEs to offer holistic exposure management.
This gives customers a comprehensive approach to vulnerability management, gaining insights into various threat vectors. Customers also benefit from informed decision-making and effective communication of cyber risk to both security executives and practitioners.
Tenable opinion: Tenable provides a centralized platform that integrates multiple tools seamlessly. The Tenable platform ensures compatibility with a wide range of systems and tools to create a unified and comprehensive view of exposure across different attack surfaces.
IDC Recommendation: Offer attack path visualizations and summaries. Device vulnerability management vendors should offer attack path visualizations and summaries for customers to understand exposure chains, which may not be evident when scoring individual vulnerabilities.
This way, customers can visualize risks, understand relationships, and identify choke points, enabling informed decisions based on a dynamic understanding of the attack surface.
Tenable opinion: Tenable’s Attack Path Analysis, available within Tenable One, has intuitive visualization tools that clearly depict exposure chains and relationships. We provide customization options to tailor visualizations to the specific needs and preferences of different organizations.
IDC Recommendation: Utilize machine learning for identifying unusual configurations. Device vulnerability management vendors should take advantage of machine learning to identify unusual configurations that may create exposures for customers.
With this recommended capability, customers benefit from a proactive approach to identifying and mitigating potential exposures, reducing the likelihood of successful attacks.
Tenable opinion: Tenable Research invests in ongoing research and development to stay ahead of emerging threats. Our product and research teams regularly update our machine learning models to adapt to evolving attack techniques and ensure accurate identification of unusual configurations. We are able to provide clear insights into the AI-driven decision-making process to build trust with buyers.
According to the IDC report: “Organizations have more options for unified exposure management platforms from start-ups and longtime vendors alike. These solutions enable the aggregation of exposures from device vulnerability scanners, alongside tools such as application security tests, attack surface management (ASM), cloud platforms, cybersecurity asset management systems, and IoT/OT scanners. Offering greater visibility of a unified IT environment, the new exposure management platforms use AI algorithms to present the prioritized risk of CVEs and other exposures, so the security team knows where to start.”
Having these recommended capabilities and features is essential for customers to stay ahead in the rapidly evolving cybersecurity landscape. Leveraging the Tenable One Exposure Management Platform and our innovative solutions, we provide a comprehensive and proactive approach to device vulnerability management. Empowering you to strengthen your security posture and manage exposure effectively, we help you prioritize risk, offer detailed asset visibility, integrate diverse tools, provide attack path visualizations, and leverage machine learning.
Remaining at the forefront of vulnerability and exposure management, we are committed to delivering innovative solutions aligned with market trends and future requirements. Trust us to navigate the evolving attack surface, ensuring your resilience against emerging threats.
1Worldwide Device Vulnerability Management Market Shares, 2022: Exposures Present a Clear and Present Danger
Learn more
- Read the IDC “Worldwide Device Vulnerability Management Market Share, 2022: Exposures Present a Clear and Present Danger'' report for more information on DVM vendors and market insights
- Read the press release
- Visit our Tenable One landing page to learn more about our exposure management platform
- Exposure Management
- Research Reports
- Risk-based Vulnerability Management
- Vulnerability Management

