libssh Vulnerable to Authentication Bypass (CVE-2018-10933)

A newly announced vulnerability in libssh, a multiplatform library that supports the Secure Shell (SSH) protocol, allows attackers to bypass authentication and gain full control over vulnerable servers.
Background
On October 16, the libssh team published an important security update for a vulnerability in libssh versions 0.6 and above. libssh is a multiplatform library written in C that supports the SSH protocol and can be used to implement client and server applications. The security update addresses CVE-2018-10933, an authentication bypass vulnerability. Tenable confirms our products are not vulnerable to CVE-2018-10933.
Impact assessment
Using Shodan, a search engine for internet-connected devices, we found nearly 2,000 devices are running libssh versions 0.6 and above. However, the full scope of libssh use is unclear. Additionally, it has been reported that vulnerable instances of libssh need to be running in server mode, not client mode, which may limit the impact of this vulnerability.
Vulnerability details
When authenticating to a server using libssh, it expects to receive a “SSH2_MSG_USERAUTH_REQUEST” message to initiate authentication. However, servers running vulnerable versions of libssh can be presented with a “SSH2_MSG_USERAUTH_SUCCESS” message, which would allow anyone to access the server without providing any credentials.
Below is a screenshot of Tenable Research confirming this vulnerability on a test system in our lab:
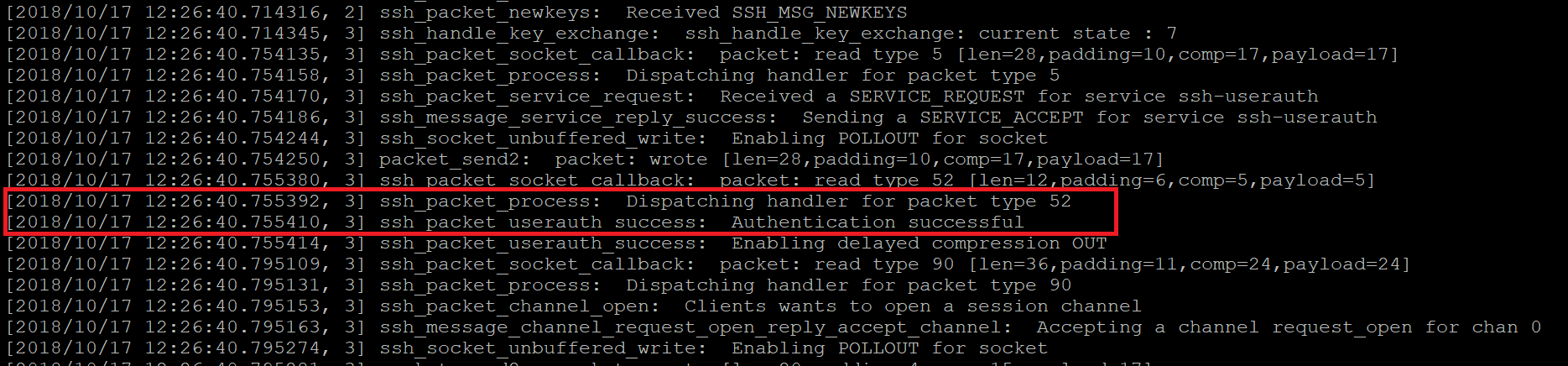
Urgently required actions
This vulnerability has been addressed in libssh versions 0.8.4 and 0.7.6, so it is important to update servers once server distributions release patches. Additionally, if software creators implement the libssh library in server mode, they should update to the latest version of the library.
Updated on Oct. 19, 2018: Several distributions have released patches to address this vulnerability, including Debian, Ubuntu and SUSE. Additionally, Cisco and F5 Networks have released security advisories for their products. Cisco is currently investigating its product line to determine whether any are affected by the libssh vulnerability. F5 Networks released an advisory for BIG-IP application delivery controllers and lists the Advanced Firewall Manager (AFM) as vulnerable but the company has not yet provided a patch.
Identifying affected systems
A list of Nessus plugins to identify this vulnerability can be found here.
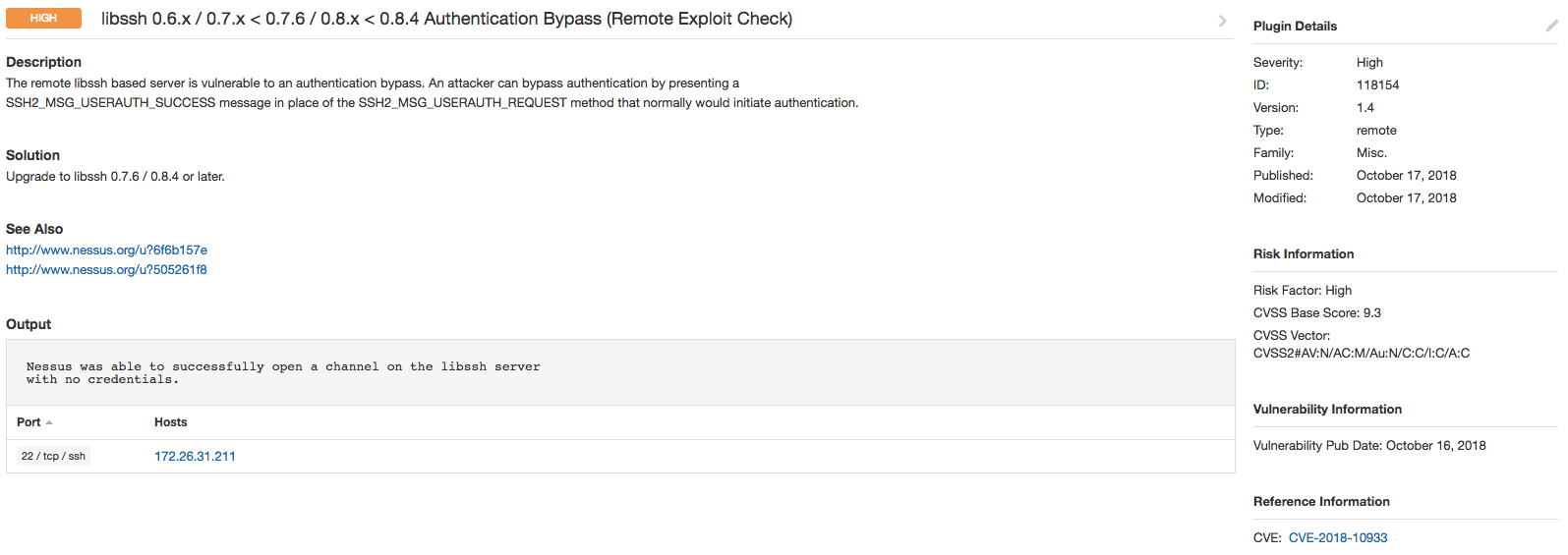
The output of plugin 118154, the exploit plugin, can be seen below.
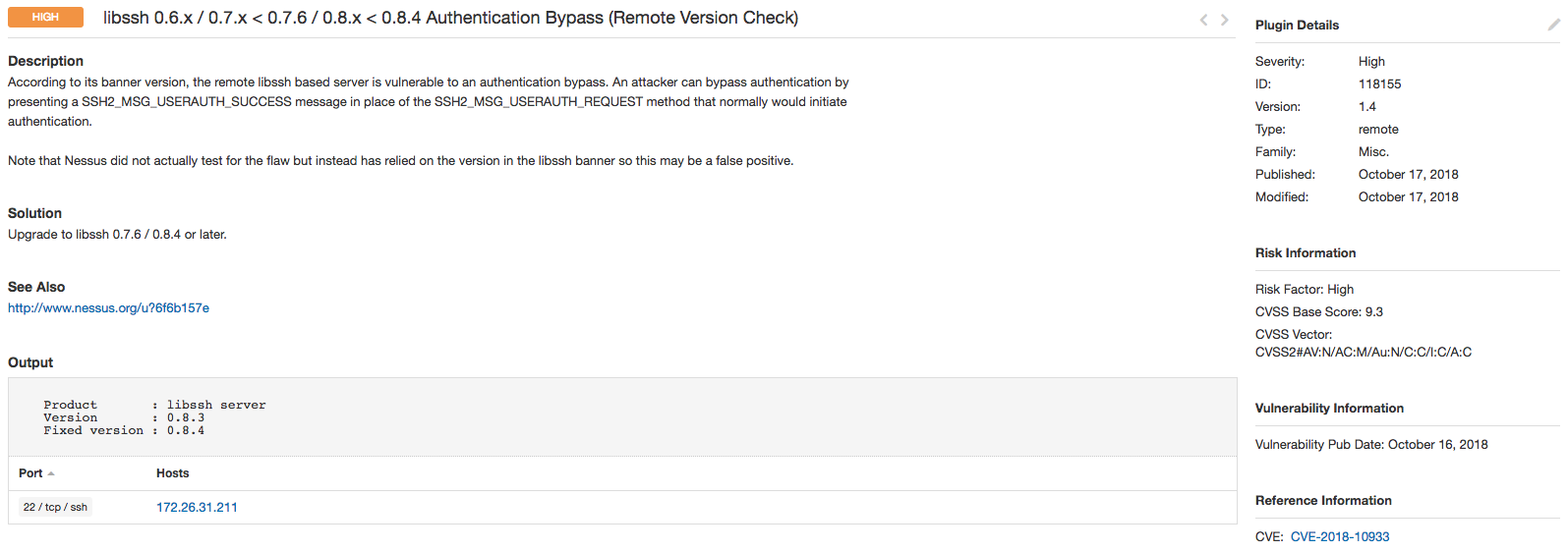
This image shows the output of plugin 118155, which checks the libssh version. Please note this will only report when the Accuracy is set to “Show potential false alarms.”
Get more information
- libssh 0.8.4 and 0.7.6 security and bugfix release
- Trivial authentication bypass in libssh leaves servers wide open
Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

