Shifting Left in the Cybersecurity Defense Lifecycle

Identifying your risk posture should be the first objective of all cybersecurity programs. Yet, this is where organizations often fail, due to weak visibility and understanding during the crucial “identify” phase of the cybersecurity lifecycle. Focusing on protect, detect, respond, recover without an understanding of risk posture leads to failed security strategies.
The cybersecurity defense lifecycle has a NIST Framework created for the purpose of helping organizations reduce and better manage cyber risks. It depicts the phases of a continuous lifecycle on a continuum like so: identify->protect->detect->respond->recover (Figure 1).

Figure 1: NIST Cybersecurity Framework.
The cyber defense industry has had a huge focus in recent years on innovations relevant to the protect, detect and respond/recover aspects of this lifecycle. The cybersecurity landscape has been exploding with several hundreds of vendors (~500) in an ever-increasing number of areas and specializations. How do you know whether you need every one of these tools in your toolbox or just a couple?
It all starts with the “identify” stage, which begins with an initial understanding of your own risk posture that then develops into a more comprehensive risk management strategy with a focus on reducing your cyber exposure. This beginning allows for a measured response, rather than a spray-and-pray approach that is unlikely to yield the results you're looking for. Understanding your own risk posture requires getting a continuously updated picture of your assets and information about the importance of those assets, and with a picture of the attack surface exposed by those assets directly or indirectly. Combining this level of insight with the risk introduced by humans -- whether inside or outside your organization -- gives you a much better picture of risk.
In the past, identification of assets was a relatively uncomplicated problem to solve. Your assets were physical assets that you knew, you could touch and, for the most part, they never left the building. As you move from that world into the world of BYOD, IoT, virtual machines, public cloud, containers and now serverless computing, those assets can be increasingly ephemeral and hard to discover and control. Furthermore, there’s been a significant increase in the sheer number of vulnerabilities over the past several years, with last year exhibiting a significant spike and this year on target to come close to or even exceed last year (Figure 2). The ever-changing elastic attack surface created by the evolution of assets from physical to increasingly ephemeral has created a massive gap in an organization’s ability to truly understand its Cyber Exposure at any given time. We call this the Cyber Exposure gap.
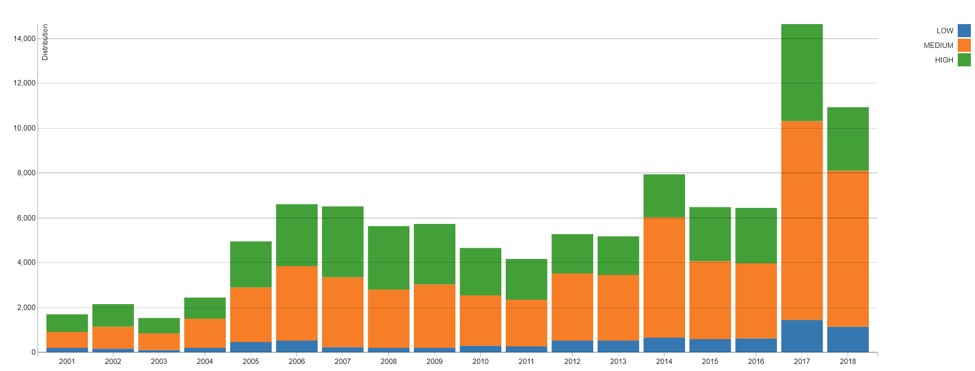
Figure 2: Vulnerability distribution trends over time (Source: NVD).
Recent high-profile breaches like Equifax, which was identified as being due to not patching an Apache Struts vulnerability for months, has led to significant focus on accelerating the time it takes to fix vulnerabilities across the corporate landscape.
This isn’t and hasn’t been an easy problem to solve for most organizations. The complexity of dealing with the vulnerabilities found in an organization has been increasing multiplicatively as a result of the sheer number of vulnerabilities across an ever-changing and expanding asset landscape. This is further complicated by having to consider the effect of a large variety of security products that could mitigate a vulnerability under specific circumstances and configurations. Last, but not least, is the fact that the process of fixing these vulnerabilities now also spans a variety of human owners and operators due to the varied nature of assets today.
In addition to the effort required to understand the current cyber exposure of an organization, future technology adoption decisions are also facing security considerations such as:
- Will adopting technology X increase risk and how do we mitigate it?
- How do I keep a view of my ever-changing cyber risk posture so that I always know where to pay attention?
- How do I become more proactive in closing the cyber exposure gap?
So, where should we start?
The weakest spots in an organization’s security posture occur at the intersection of attack surface, avenues of attack (attack vectors) and obstacles/ (lack of) controls in place. Identifying these weak spots should be the first objective of all cybersecurity programs. This is also where several fail, due to weak visibility and understanding during that crucial “identify” phase.
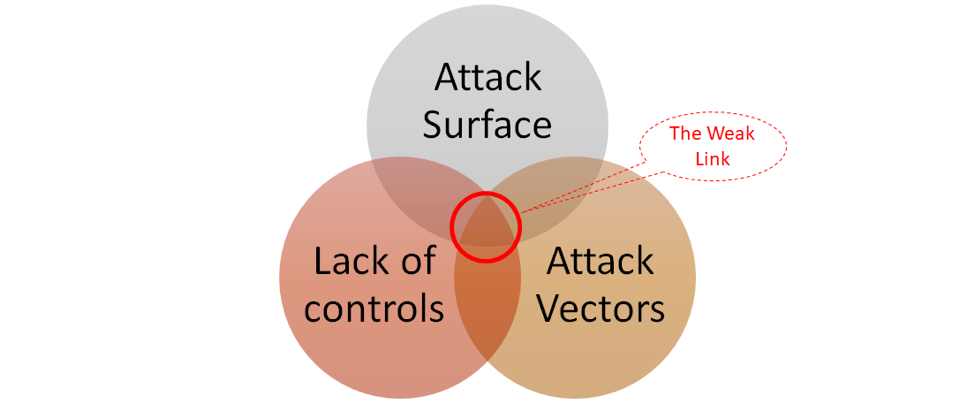
As a practice, we would all be better off with shifting further left in the lifecycle to address the right problems with the right solutions. That said, it isn’t enough to merely shift left at the start of your program for better cyber hygiene, it has to be an active part of your program, where it is revisited and continuously assessed.
Where are the top vulnerabilities found in the enterprise? Read the Vulnerability Intelligence Report from Tenable Research to find out.
- NIST
- Security Frameworks
- Vulnerability Management
- Vulnerability Scanning
