Tenable SecurityCenter Continuous View Sheds Light On Shadow IT Usage
Note: Tenable SecurityCenter is now Tenable.sc. To learn more about this application and its latest capabilities, visit the Tenable.sc web page.
Tenable’s SecurityCenter Continuous View makes it easy for companies to detect the use of cloud services and identify data stored in the cloud
While the exact extent of cloud services in companies can be debated with figures from 40% penetration to close to 90% penetration, the fact is hardly arguable that cloud applications with sensitive data stored in the cloud is widely prevalent. “Shadow IT”, including Gmail, Salesforce.com, DropBox, Webex and many other cloud services are used both formally and covertly in most organizations today, introducing a serious security concern for IT and compliance professionals. These services expose corporate data via insecure mechanisms like web-mail or by allowing external parties access past perimeter defenses via tools like GotoMyPC. They also offer hackers a single, high value target that invites watering-hole type attacks, and which once compromised, provides a treasure trove of data from millions of customers.
Cloud services accessed by your users can now be detected in Tenable SecurityCenter CV via our Passive Vulnerability Scanner and logs from on-premises web proxies, firewalls and DNS servers, helping IT security analysts improve their understanding of cloud service adoption and use in their environments.
What Can I Discover?
The plugins are consolidated in the “Cloud Services” LCE plugin, and focus on detecting services that can use and store sensitive corporate data including:
- cloud based email,
- SaaS CRM, ERP systems
- online notes services
- file storage/sharing applications
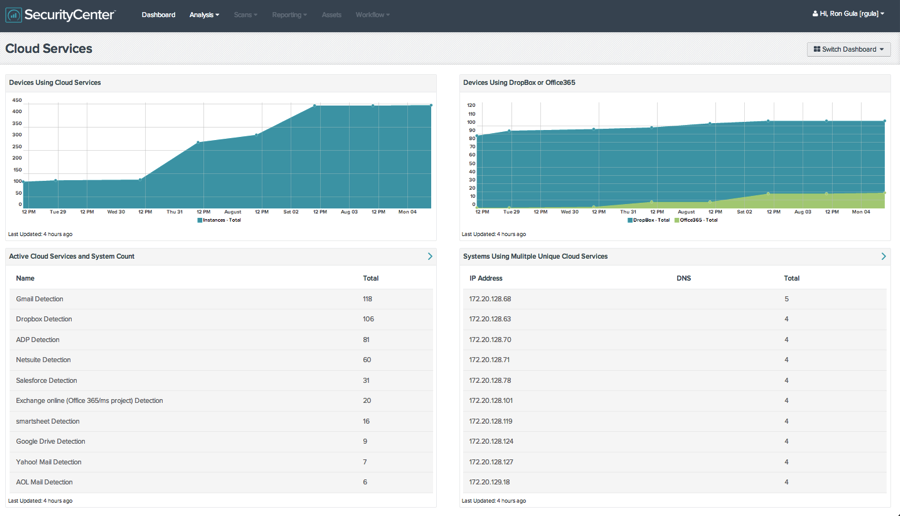
Report Cloud Usage, Mitigate Cloud Application Risk
The cloud services and applications are also reported within the Tenable SecurityCenter CV system in the form of actionable dashboards. By running these detections, analysts can uncover crucial information about cloud service usage, including the number of devices accessing specific services (e.g. how many devices use DropBox?) and specific devices/users relying heavily on cloud services. This allows analysts to understand not only cloud usage in their environment, but also the corresponding risk associated with the devices and cloud applications.
Continuous Monitoring Must Cover Cloud Usage
Sophisticated IT departments are realizing the importance of adopting a continuous monitoring approach to security and understand the need for visibility into cloud usage by their users.

By using Tenable SecurityCenter CV, security analysts can:
- discover the devices in their environment that are communicating with cloud applications
- prioritize their response to cloud usage based on the risk posed (if any) by such usage, including classifying devices and analyzing any associated attack-paths
- integrate the cloud services usage information Tenable provides with other Tenable sensors like vulnerability assessment and log collection in real-time
- take action to prevent the use of unauthorized cloud services
In addition to the cloud services Tenable SecurityCenter CV already detects, Tenable is adding more cloud service discovery and assessments continuously as new applications move to the cloud. For more information please refer to the SecurityCenter Continuous View product page.
- Cloud
- Dashboards
- SecurityCenter
