What Is Exposure Management and Why Does It Matter?

Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In our first blog in this new series, we get you started with an overview of the differences between the two and explore how cyber exposure management can benefit your organization.
Traditional vulnerability management has always been about identifying and fixing vulnerabilities — hopefully as quickly as they arise. In practice, even with reasonable service level agreements (SLAs), IT usually has to mitigate those risks. But they’re not always placed at the top of the IT priority list, leaving open a window that attackers can use to gain a foothold. The growth in CVEs (in 2021, there were 20,161 new CVEs; by 2024, that figure had almost doubled to 40,077) has resulted in teams being overwhelmed chasing down vulnerabilities. But CVEs are only part of the picture.
A report from the U.S. Cybersecurity and Infrastructure Security Agency reveals that 90% of initial access to critical infrastructure comes via identity compromise — like phishing, compromised passwords, identity systems and misconfigurations. Just as alarming, the Tenable Cloud Risk Report 2024 shows that 74% of organizations have publicly exposed storage assets, including those containing sensitive data. That same research found that 84% of organizations possess unused or longstanding access keys with critical or high severity excessive permissions, which creates a significant security gap.
Faced with these challenges, most security leaders lack a cohesive, enterprise-wide understanding of risk. As new technologies are regularly adopted, they come accompanied by new threats. In response, most security teams simply add a new siloed security tool and team to defend that new attack surface. As a result, security has become disjointed. And, although vulnerability management is a critical ingredient in cybersecurity, it only looks at a portion of preventable risk. The end result is fragmented visibility with gaps that leave organizations vulnerable.
This is where exposure management comes in. It gives security leaders the processes and technologies they need to continuously assess the accessibility, exploitability and criticality of digital assets across all systems, applications, devices, resources and identities. As a result, security leaders can proactively answer questions about their organization’s exposure risk.
What is exposure management in cybersecurity?
If you explore risk-based exposure management vs. vulnerability management, you'll see an evolution that provides a more holistic, programmatic approach to cost-effective decision making. It breaks down silos and factors in findings such as the likelihood of attack, identity permissions, attack path viability and business criticality. This enables security teams to prioritize true exposure and mobilize responses to the most impactful risks first. And it means you can more readily handle those questions from the board.
Exploring the security continuum
To understand where the importance of continuous exposure management fits in the context of your overall cybersecurity program, let’s explore the security continuum.
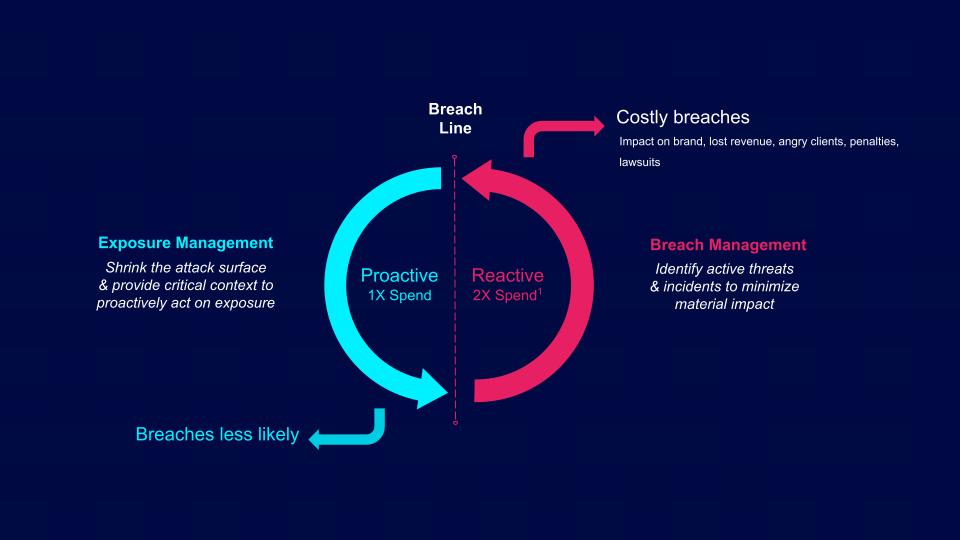
Source: Tenable, March 2025
The breach line sits at the center. Everything to the right is the world of reactive security. In this case, attacks or breaches are already underway. To the left of the breach line is the world of proactive security.
Reactive security is all about managing active threats and incidents. The goal is to minimize potential material impact. For this reason, the greater share of investment has gone into reactive security in recent years.
But with more governing bodies now requiring disclosure of breaches, such as the U.S. Securities and Exchange Commission (SEC), the burden is changing.
In addition to regulatory pressures, breaches are often accompanied by revenue impact, and incalculable damage to brand, customer loyalty and investor interest. All of this underscores the need for a more effective approach to proactive security, such as exposure management.
As a result, exposure management is being embraced by a variety of organizations — from multinational telecommunications companies to public sector agencies — because it fights three core challenges that every organization faces:
- Siloed visibility of the attack surface: The attack surface has evolved, with vendors creating myriad tools that focus on specific technology domains, such as IT, cloud, identity, OT/IoT and apps. Each of these tools often handles a subset of potential risk — across vulnerabilities, misconfigurations or privileges. This siloed approach to attack surface management leaves visibility gaps that attackers can exploit.
- Little context: Fragmented data also makes it impossible to understand the attacker’s perspective — the asset, identity and risk relationships that form viable attack pathways leading to crown jewel assets. The collection of tools also does little to help security leaders understand the potential material impact of exposures on revenue, business processes and mission-critical data.
- Inability to mobilize resources: Individual security tools provide a fragmented patchwork of remediation guidance and workflows, and limited ways to measure and communicate progress. As a result, it’s a significant challenge for security teams to figure out the best remediations as well as how and where to mobilize resources and track remediation status.
How exposure management helps
Exposure management helps by providing complete visibility into the attack surface and the critical context teams need to prioritize true business exposure. That means security teams are unburdened and can be more efficient while being less reactive. Let’s dig a bit deeper and explore how, in five steps, exposure management helps improve your security posture.
Step 1: Know your attack surface
Exposure management platforms discover and aggregate asset data across the entire external and internal attack surface, including cloud, IT, OT, IoT, identities and applications, providing a holistic view of the attack surface.
Step 2: Identify all preventable risk
Exposure management detects the three preventable forms of exposure attackers use to gain initial access and move laterally: vulnerabilities, misconfigurations and excessive privileges. Security teams can quickly identify the assets that pose the greatest potential risk to the organization.
Step 3: Align with business context
Asset tagging enables security staff to logically group assets across technology domains and align them with an important business function, service or process. Cyber exposure scores provide quick business-aligned views of exposure and show changes in exposure over time.
Step 4: Remediate true exposure
Detailed mapping of asset, identity and risk relationships reveal attack paths which lead to an organization’s crown jewels. This gives the security staff the attacker’s perspective, which is critical to separate noisy findings from true exposures that can have a material impact on the organization.
Step 5: Continuously optimize investments
The ability to quantify your overall cyber exposure score and compare it with the benchmark score of peers in your industry streamlines budget justification, while helping security leaders answer the critical question: “Are we secure?”
We explore each of these steps in more detail in the white paper “Attackers Don't Honor Silos: Five Steps to Prioritize True Business Exposure.”
By bridging and integrating people, process and technology across traditional silos, exposure management enhances collaboration and efficiency , and it frees security leaders and IT teams to focus on strategic initiatives rather than the latest crisis.
Who can benefit from exposure management?
The benefits of exposure management can be transformative. Whether you’re a practitioner who’s stretched thin, a manager who struggles with understanding risk, or a C-level executive who worries about it all, exposure management can help.
- Security practitioners: The backbone of any security organization, practitioners do the heavy lifting. They’re notoriously self-sufficient, but they do need a couple of things: visibility into the attack surface and a unified view of all assets. This is what an exposure management platform brings to the table — making it simpler to prioritize remediating software vulnerabilities, misconfigurations and improperly assigned credential entitlements.
- Security managers: Just a bit further up the chain, security managers need insight and context about threat exposures, assets and privileges to marshal resources across teams and handle their most pressing security needs. An exposure management platform provides the shared visibility and insights needed to drive better collaboration across teams and better utilize limited resources they have to remediate and respond.
- Security executives: CISOs, business information security officers (BISOs) and other security executives require accurate risk posture assessment to improve investment decisions, make decisions about insurability, meet regulatory and compliance requirements and drive organizational improvement. An exposure management platform provides actionable metrics to help security leaders measure, compare and communicate exposures and cyber risk reduction, not only to operations teams within IT and security, but also up and out to non-technical executives and operating teams throughout the enterprise.
Takeaways
With so much noise in security, what you don’t do is as important (or even more important) as what you actually do.
Exposure management is an evolutionary approach and it’s being embraced across industries and geographies as a way to remove complexity, focus teams and understand the entire attack surface. It boils down to the unification of visibility, insight and action.
Exposure management does require a shift in mindset — recognizing that not everything is critical and not all risks are created equal. This can be a challenge at first. But think about it: The everything-is-critical approach leads to burnout, inefficiency and more exposures. Exposure management lets you prioritize the things that matter most: the exposures that can have an actual impact on crown jewels and the organization.
When you embark on the exposure management journey, you’ll be part of an expanding community of security professionals who are blazing a new trail. Join them.
Watch: What is exposure management?

- Exposure Management
- Exposure Management Academy
- Vulnerability Management



