- Tenable Cloud Security
Tenable Cloud Risk Report 2024
38% of organizations have at least one critically exposed cloud workload – with a toxic cloud trilogy of:
- publicly exposed
- critically vulnerable
- highly privileged
Identifying blind spots, searching for context and addressing the toxic cloud trilogy.
As cloud infrastructure complexity increases and threat landscape targets rapidly shift, new and significant security gaps are emerging. Among these, the "toxic cloud trilogy" presents one of the most critical risks. The Tenable Cloud Risk Report 2024 dives deeply into this challenge and others, offering insights into the real and sometimes surprising risks confronting cloud environments – and ways to address them.
Your cybersecurity report for critical insights.
Dive into the Tenable Cloud Risk Report today.
Uncovering the Toxic Trilogy

Critical exposure of cloud workloads
Many global breaches in 2024 were caused by one-day vulnerabilities on exposed workloads, with some of the most severe involving lateral movement through compromised workload privileges.

IAM and credential vulnerabilities
Discovery is key. Discover, inventory and assess all assets and their vulnerabilities across your infrastructure- from IT to OT, container, web apps and identity systems.
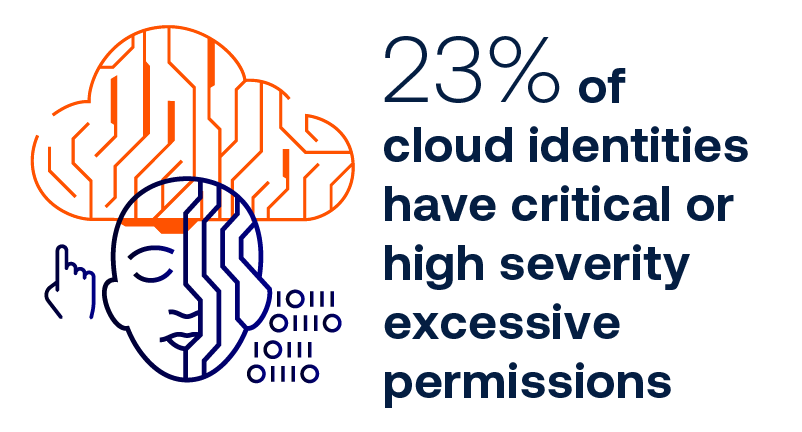
Prevalence of excessive permissions
Our research revealed extensive instances of — and issues with — excessive permissions in both human and non-human identities.
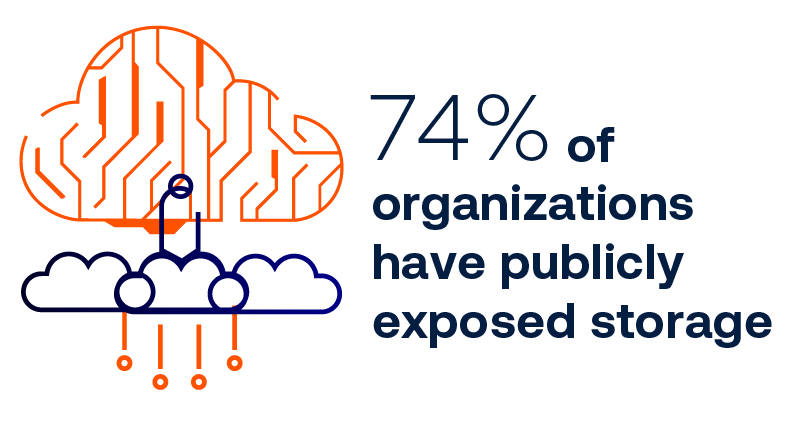
Cloud storage risks
As organizations expand their use of cloud-native applications, the amount of cloud-stored sensitive data —like customer info, employee records and business IP—grows. This makes cloud data a prime target for hackers - and highlights the need to examine exposure.
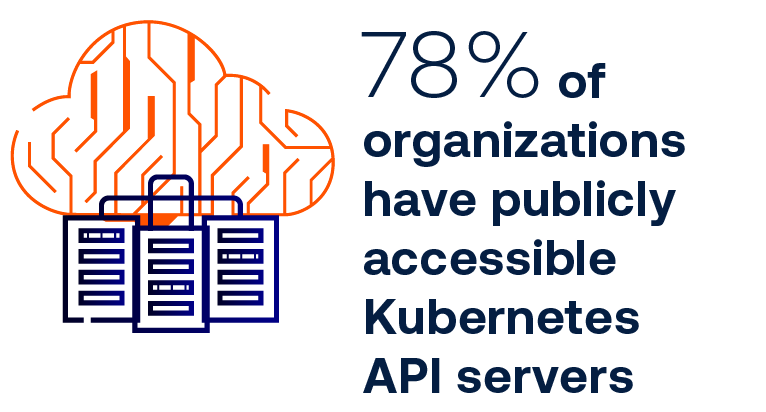
Kubernetes security challenges
As container adoption grows, with Kubernetes as the leading orchestrator, new security challenges arise that demand specialized expertise and deep knowledge of Kubernetes complexities.
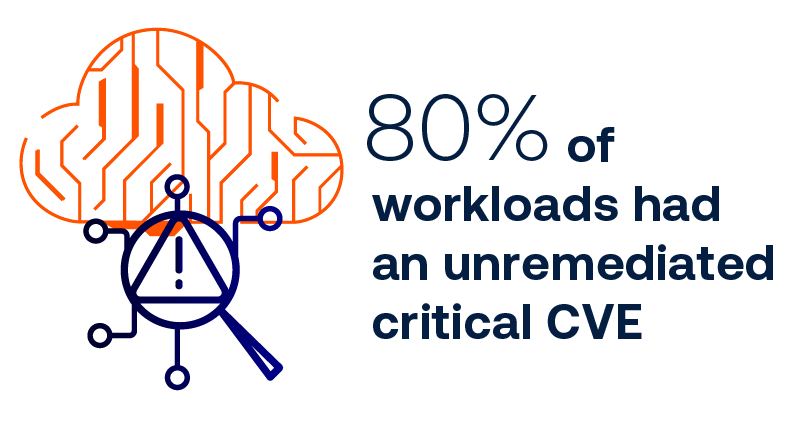
Unmanaged cloud vulnerabilities
Discovery is key. Discover, inventory and assess all assets and their vulnerabilities across your infrastructure- from IT to OT, container, web apps and identity systems.
Know your weaknesses. Expose your gaps. Close your true exposures fast.
Explore the most pressing threats and discover effective strategies to protect your cloud infrastructure from potential breaches.
