Tenable products
Isolate and eradicate the priority exposures that put you at risk
Target priority cyber weaknesses across your IT infrastructure to your cloud environment to your critical infrastructure, and everywhere in between. Choose from an individual exposure solution or protect your entire attack surface with Tenable One, the industry’s only end–to–end exposure management platform.
Tenable exposure solutions
Close the cyber gaps that leave you exposed.
Supercharge risk reduction with AI-powered exposure solutions that continuously learn from each other and provide big-picture insights to strengthen your entire cybersecurity posture.
Close cloud exposure
with the actionable cloud security platform.
Reduce risk by rapidly exposing and closing priority security gaps caused by misconfigurations, risky entitlements and vulnerabilities.
Close vulnerability exposure
with the world’s #1 vulnerability management solution.
Reduce risk by knowing your impactful IT vulnerabilities, exposing your top priorities and closing critical exposures at speed.
Close OT
exposure
with the unified industrial security solution for converged OT/IT environments.
Reduce risk by gaining unified visibility, insight and control of OT, IoT and IT assets in a single solution.
Close identity exposure
with the essential solution for the identity-intelligent enterprise.
Reduce risk by finding and fixing exposures across your end-to-end identity environment to prevent identity-based attacks.
Cloud exposure
Vulnerability exposure
OT Exposure
Identity Exposure
AI Exposure
Free products from Tenable
Tenable One
The world’s only end–to–end exposure management platform
Radically unify visibility, insight and action across the entire attack surface
Fix the fractured
Get the world’s only all–knowing view of cyber risk across your entire attack surface, exposing the lethal gaps that leave you most vulnerable to attack across all types of assets and pathways.
Connect the disconnected
Gain a single source of attack surface truth and wisdom, connecting disparate dots to identify the priority problems and toxic risk relationships that are escalating your enterprise exposure.
Unite the divided
Mobilize your business and security teams to eradicate your biggest cyber exposures, reducing enterprise risk from the network to the cloud to OT and everywhere in between.
Comprehensive asset inventory
Dynamic attack path mapping
Predictive prioritization
Orchestration and remediation
Advanced analytics and reporting
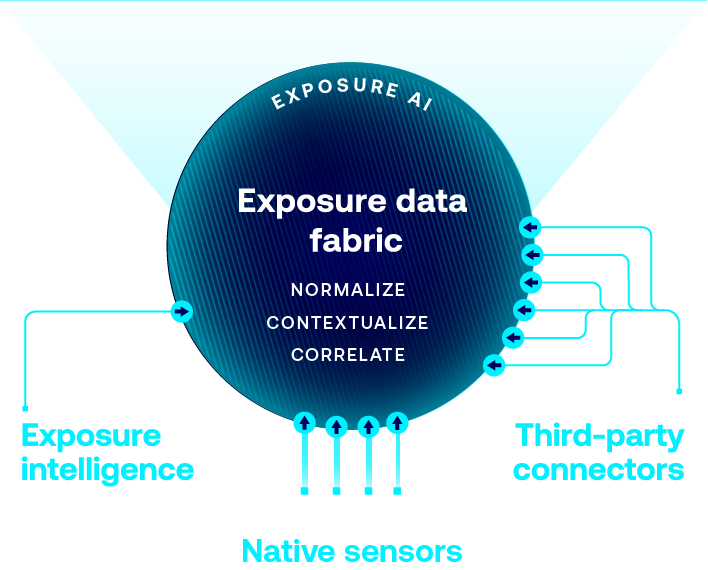

Accelerate search, insight and action with generative AI that uncovers hidden risks and amplifies security expertise across your environment.
Gain a unified view of all your assets and risk across your attack surface: unseen assets, IT, OT, IoT, cloud, identities and applications.
Understand attacker accessibility through visualizations of cross-domain relationships, so you can block your most critical attack paths.
Focus your efforts on what matters most: the critical exposures attackers are most likely to exploit.
Accelerate response with automated workflows and prescriptive guidance that streamline remediation efforts.
Streamline measurement and communication of cyber exposure with business-aligned views to optimize decision making and investments.
Tap into the most comprehensive threat and vulnerability knowledgeable, combining insights from Tenable Research, the National Vulnerability Database (NVD) and trusted third-party sources.
Use native attack surface discovery for cloud, identities, IT, IoT, OT, AI, applications, containers and Kubernetes that Tenable product sensor fuel.
Seamlessly connect asset and exposure data from your existing tools to enrich Tenable intelligence and get comprehensive exposure context.
Leverage the world’s largest repository of asset, exposure, and threat context that powers ExposureAI’s unparalleled insights.
Organize data to reduce redundancy and improve integrity, consistency and efficiency.
Enrich data with additional insights, making it more actionable and useful.
Identify and surface critical relationship context to core business services and functions.
Get Started with Tenable One
Tenable One has helped our engineers reduce the time spent on manual tasks by 75%, which allows them to focus on actual engineering work.