Tenable
Identity Exposure
The essential solution for
identity security posture management (ISPM)
Strengthen your security posture and defend against identity-based attacks.

Stop identity-based exploits
Know your complete identity reality
Collapse enterprise silos and unify your hybrid identity infrastructure, including Active Directory and Entra ID.
Expose
your top
identity gaps
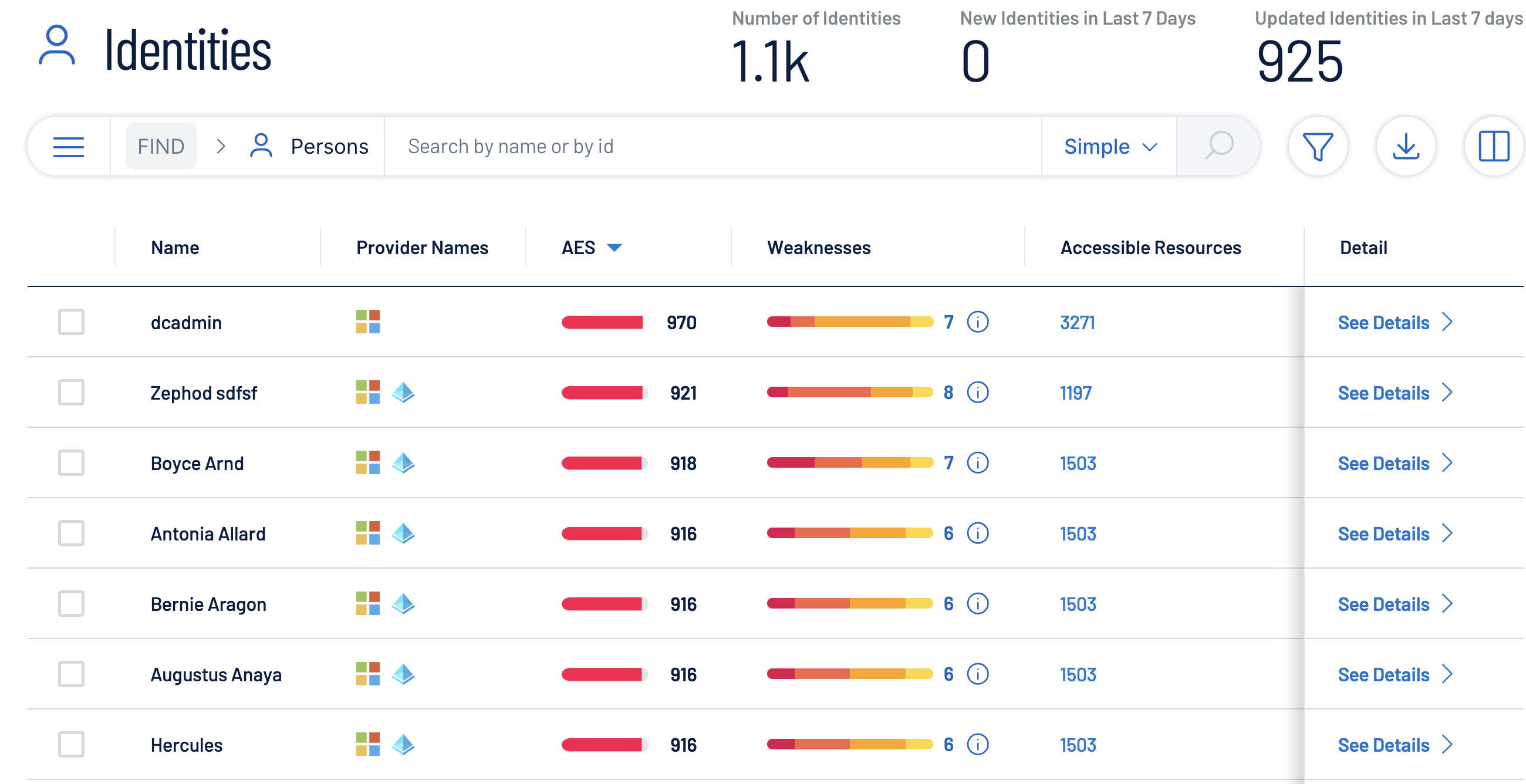
Evaluate your identities using risk scoring to locate your riskiest ones that require attention.
Close identity-based exposures with speed
Leverage detailed remediation guidance and automation-ready scripts to take immediate action.
Close identity exposure to reduce risk
Identities are the new perimeter — compromised identities are at the center of nearly every successful cyberattack. By uncovering misconfigurations, over-privileged access, and weaknesses in Active Directory (AD) and Entra ID, Tenable Identity Exposure strengthens your security posture and prevents identity-based attacks before they occur.
See the bigger picture
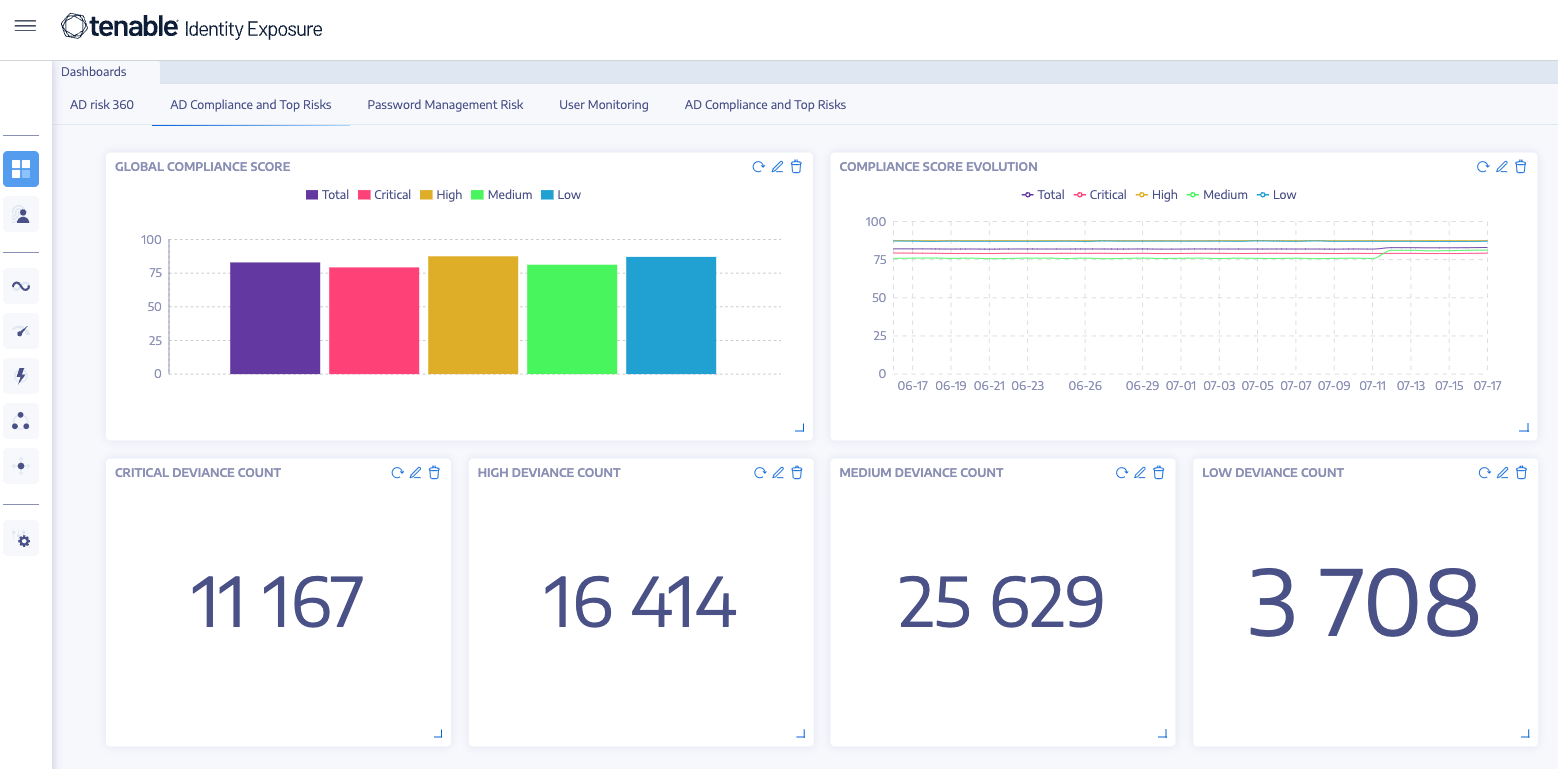
Tenable Identity Exposure unifies and analyzes your identity risk surface, continuously validating AD and Entra ID for weaknesses, misconfigurations and risky permissions. Integrating deep identity context into the Tenable One Exposure Management Platform can help eliminate silos, uncover toxic combinations and prioritize risks, so you can remediate the exposures that matter most.
Eliminate attack paths
Tenable Identity Exposure eliminates the exposures and attack paths bad actors might otherwise exploit, ensuring attackers struggle to find a foothold and have no next step if they do.
Initial
foothold
Via phishing or vulnerability
Explore
Lateral movement across the target environment
Elevate
Gain privileged access
Evade
Hide forensic footprints
Establish
Install code for permanence
Exfiltrate
Exfiltrate data or hold target to ransom
Secure hybrid identity infrastructure
- Map and consolidate identities across identity providers to eliminate blind spots identity sprawl creates and attackers depend on.
- Identify risky trust relationships and cross-domain attack paths between on-prem AD and cloud Entra ID to stop privilege escalation and lateral movement.
- Rank identities, misconfigurations and over-privileged accounts by security impact to focus remediation efforts where they’re needed most.
- Track identity changes and detect malicious activity across hybrid identity infrastructure — as it happens.
- Identify and fix stale credentials, over-privileged accounts and misconfigurations that expose AD and Entra ID to compromise.
Confidently prevent attacks before they occur

Deployed your way
Secures Active Directory (AD) and Entra ID with flexible deployment options: On-prem for full control over your identity data, or SaaS for scalable cloud-based security.

Secure without the risk
Tenable Identity Exposure is fully agentless, operating with just a standard user account to audit configurations and detect advanced identity threats in real time.

Available through Tenable One: The world’s only AI-powered exposure management platform
Tenable One solves the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk. We remove risk by unifying security visibility, insight and action across the attack surface to rapidly expose and close gaps. Customers use Tenable One to eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
Learn more
FAQs
-
What are Tenable Identity Exposure’s main capabilities?
-
Tenable Identity Exposure provides proactive identity security to protect against identity-based threats across Active Directory (AD), Entra ID and other identity providers, so you can manage your entire identity risk surface efficiently.
Tenable Identity Exposure key capabilities:
- Unify identity visibility: Gain a consolidated view of all human and machine identities across Active Directory (AD), Entra ID and other identity providers (IDPs).
- Expose identity risks: Detect and prioritize misconfigurations, excessive permissions and attack paths that adversaries can exploit.
- Streamline remediation: Provide guided remediation steps and automated scripts to fix security gaps efficiently.
-
What is identity security posture management (ISPM)?
-
Identity security posture management (ISPM) is a proactive approach to securing identity infrastructures by continuously assessing, monitoring and mitigating identity-related risks. ISPM goes beyond traditional identity and access management (IAM) by focusing on identifying misconfigurations, excessive permissions, risky trust relationships and attack paths that attackers could exploit.
Tenable Identity Exposure embodies ISPM principles by providing a 360-degree view of identity security risks across hybrid environments like Active Directory (AD) and Entra ID. It continuously maps indicators of exposure (IOEs) to identities, so you can prioritize and remediate risks before threat actors exploit them.
While traditional identity threat detection and response (ITDR) solutions react to attacks in progress, ISPM prevents attacks by addressing security gaps before they become threats. ISPM also integrates with broader continuous threat exposure management (CTEM) strategies to provide your organization with a holistic view of your identity risk surface.
-
Which Active Directory (AD) and Entra ID attacks and techniques does Tenable Identity Exposure detect?
-
Tenable Identity Exposure detects many of the techniques threat actors use in cyber attacks to gain elevated privileges and enable lateral movement, including DCShadow, Brute Force, Password Spraying, DCSync, Golden Ticket and more.
-
How does Tenable Identity Exposure audit Active Directory (AD) and Entra ID?
-
Tenable Identity Exposure is the only solution on the market that does not require deployment on domain controllers, endpoints or Entra ID environments. Additionally, Tenable Identity Exposure only requires a standard user account to operate. This unique architecture enables your security teams to rapidly audit configurations and detect sophisticated attacks in real time, eliminating deployment complexities and minimizing security risks associated with agents and privileged accounts.
-
Is Tenable Identity Exposure a point-in-time security audit tool for hybrid identity infrastructure?
-
No. Tenable Identity Exposure is not a point-in-time security audit tool. Misconfigurations and vulnerabilities in hybrid identity infrastructures, such as Active Directory (AD) and Entra ID, can occur at any time, making point-in-time audits outdated almost immediately after you complete them.
Tenable Identity Exposure continuously monitors hybrid identity infrastructures, on-prem to the cloud, for new weaknesses and advanced attack techniques. It delivers real-time alerts so you can identify and address vulnerabilities swiftly and mitigate risks effectively without relying on outdated, periodic assessments.
-
Which data sources does Tenable Identity Exposure use?
-
Tenable Identity Exposure utilizes identity data from Active Directory (AD), Entra ID and other identity providers (IDP) to assess identity exposures. It also integrates with data in the Tenable One platform, such as cloud security, vulnerability management and operational technology (OT) to provide a complete exposure management solution.
-
Is Tenable Identity Exposure a cyber asset management (CAM) solution?
-
Tenable Identity Exposure is not a traditional cyber asset management (CAM) tool. Rather, it provides identity-specific visibility and risk insights that augment a broader CAM approach. By offering a 360-degree view of all identities across Active Directory (AD) and Entra ID, Tenable Identity Exposure pinpoints vulnerabilities and risks unique to identity systems.
Through its integration with Tenable One, it aligns identity security with continuous threat exposure management (CTEM) principles, bridging the gap between asset discovery and proactive risk reduction. While CAM solutions focus on discovering and managing a broad range of cyber assets, Tenable Identity Exposure specializes in the deep, identity-focused analysis critical for preventing credential-based attacks and securing your ever-expanding identity surface.
-
Can I export data from Tenable Identity Exposure?
-
Yes. You can download findings from data tables. You can customize exports to show the specific columns you need. The file format supported currently for export is .CSV.
-
How does Tenable Identity Exposure help with centralized visibility of identity risks?
-
Tenable Identity Exposure provides a centralized view of identity weaknesses — such as misconfigurations and excessive permissions — across Active Directory (AD), Entra ID and hybrid environments. It helps your organization quickly identify, prioritize and remediate identity risks at scale, reducing attack paths and strengthening security posture.
-
What is the Identity Asset Exposure Score (AES)?
-
The Identity Asset Exposure Score (AES) is an AI-driven scoring system that evaluates and ranks each identity based on its risk level. It considers:
- Inherent vulnerabilities such as weak credentials, misconfigurations and stale accounts
- Inherited risks from associated assets like vulnerable devices or risky group memberships
-
Does Tenable Identity Exposure require agents or privileged accounts?
-
No. Tenable Identity Exposure is completely agentless and does not require privileged accounts for monitoring, making it easier to deploy while reducing security risks.
-
How does Tenable Identity Exposure integrate with other Tenable solutions?
-
Tenable Identity Exposure integrates with Tenable One, leveraging vulnerability management, cloud security, and operational technology data to provide a holistic view of identity-related risks within an organization's overall attack surface.
-
How does Tenable Identity Exposure help with compliance requirements?
-
Tenable Identity Exposure supports compliance efforts by continuously identifying and mitigating identity-related risks that could lead to regulatory violations. It helps organizations align with key security frameworks, including:
- NIST CSF & CIS Controls: By addressing identity security gaps, Tenable Identity Exposure aids in meeting critical security controls required for robust identity governance.
- ISO 27001 & SOC 2: Helps enforce identity access policies and security best practices to support regulatory compliance efforts.
- GDPR & CCPA: Ensures visibility and control over identity-related risks, contributing to data protection and privacy mandates.
- Zero Trust & Executive Orders: Strengthens identity security as part of broader Zero Trust initiatives and compliance with government cybersecurity directives.
By proactively detecting and remediating misconfigurations, over-privileged accounts, and identity attack paths, Tenable Identity Exposure helps organizations maintain security compliance while reducing the risk of credential-based breaches.
Related resources
Get started with Tenable Identity Exposure
By deploying Tenable Identity Exposure on our global perimeter, we gave stakeholders much-needed visibility of corporate cybersecurity risks.
- Tenable Identity Exposure