Tenable One
The world’s only AI-powered exposure management platform
Tenable One radically unifies security visibility, insight and action across the attack surface, equipping modern organizations to isolate and eradicate priority cyber exposures from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.

Win with one
Tenable One is a singular platform built to solve the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk.
Unify
vision
Bring enterprise views of cyber risk across the attack surface together as one, exposing the gaps that leave you vulnerable to attack across all types of assets and pathways.
Unify
insight
Analyze cyber risk context and insights from across the attack surface as one, connecting dots to identify the true exposures threatening your business value, reputation and trust.
Unify
action
Unite business leaders and security teams to do battle as one, mobilizing all organizational resources to find and fix risks with the highest likelihood of attack and business impact.
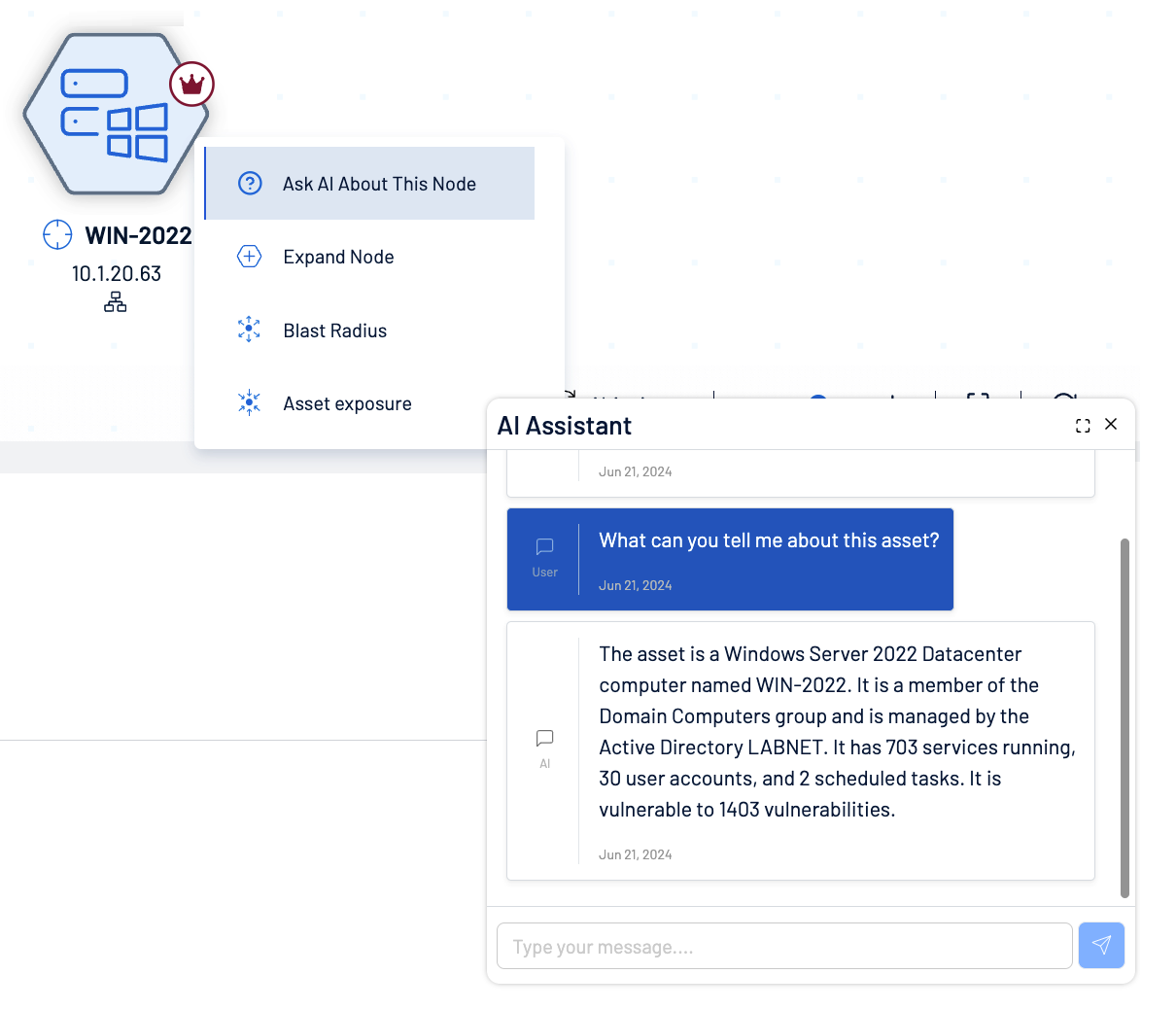
ExposureAI
Empower lightning-fast analysis and decision making with generative AI that streamlines discovery of hidden insights and deep security expertise.
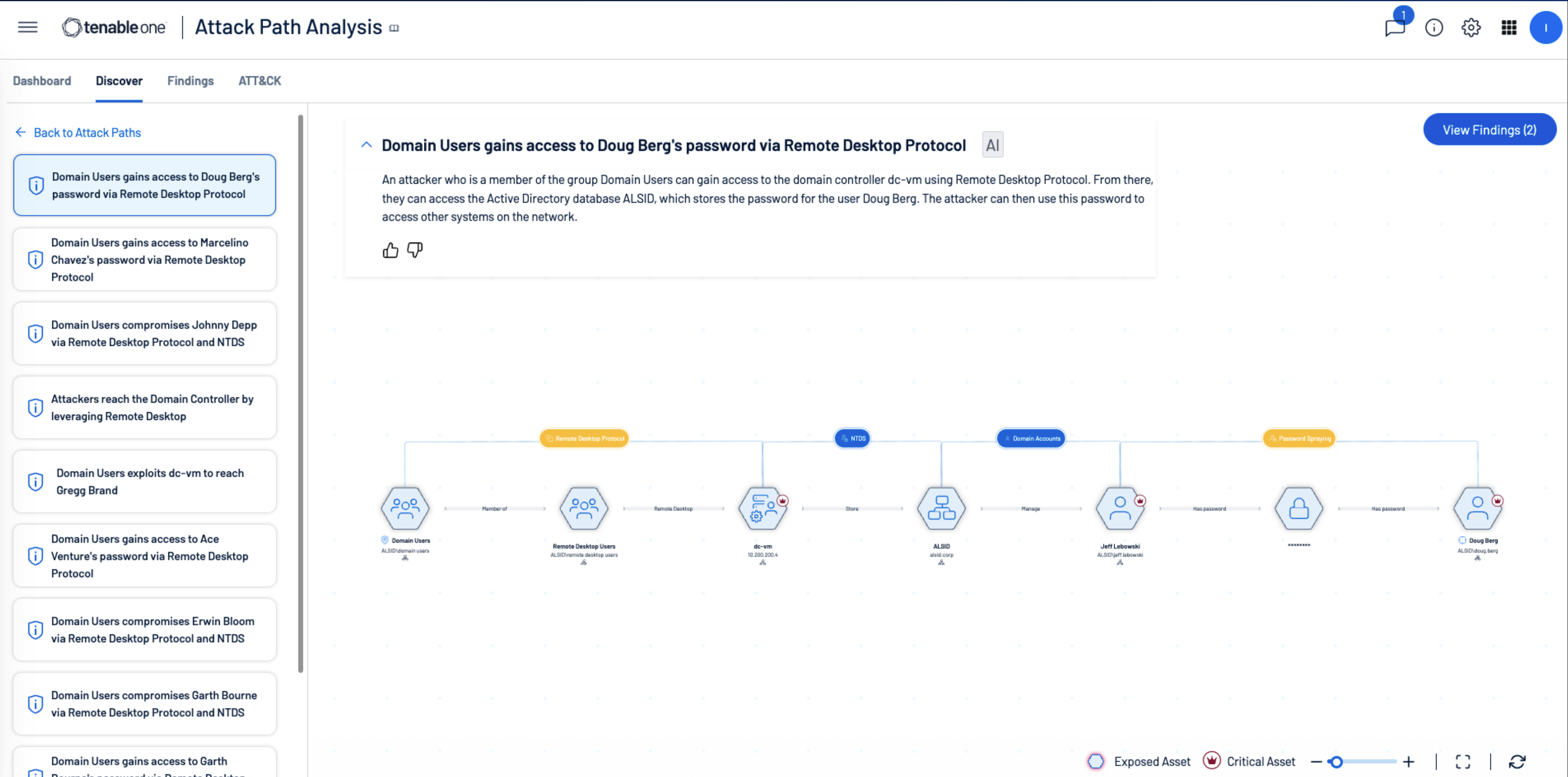
Attack path analysis
Visualize complex asset, identity and risk relationships across security domains and prioritize remediation of true exposure before breaches happen.
Exposure View
Streamline measurement and communication of cyber exposure with business-aligned views that help you optimize decision making and investments.
Exposure graph
Act confidently with the world's largest repository of contextual asset, exposure and threat data that fuels Tenable ExposureAI's unparalleled insights.
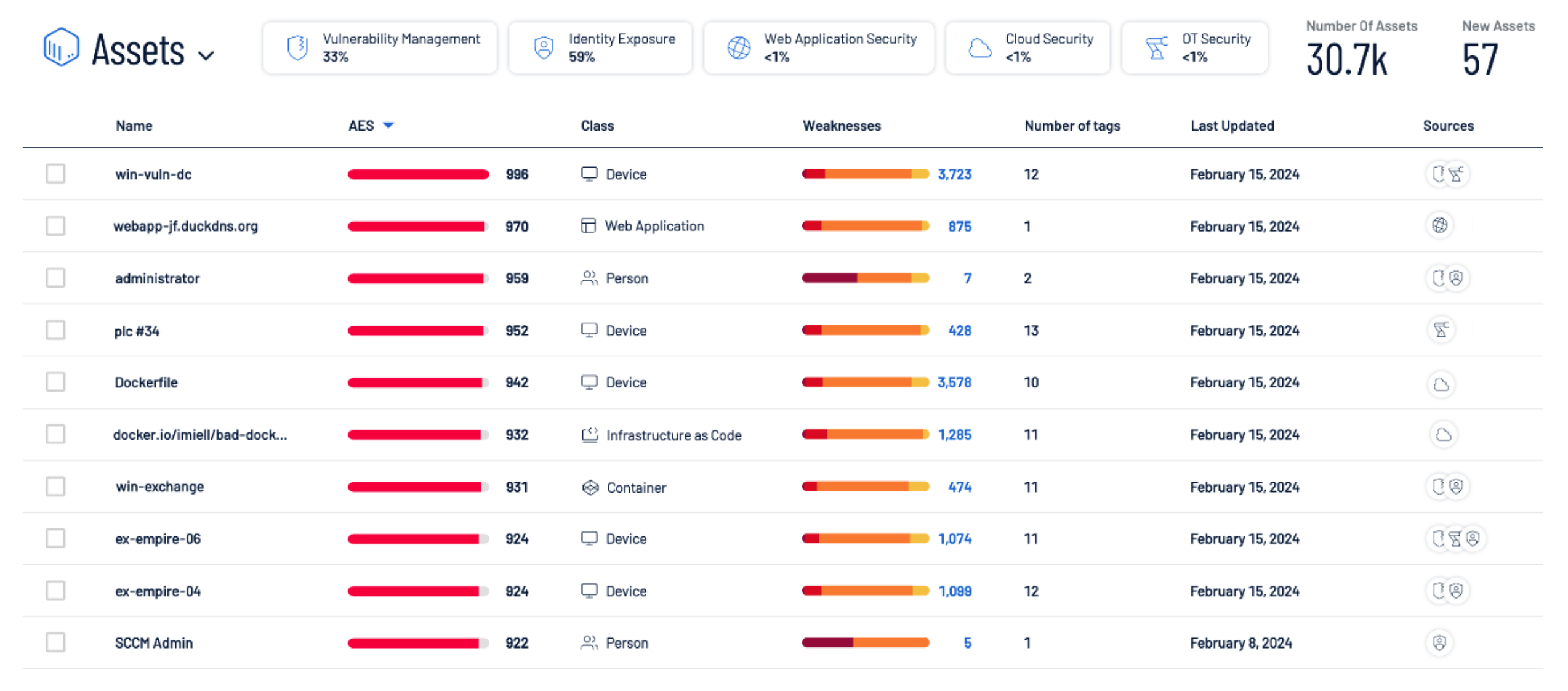
Inventory
Gain a unified view of all your assets and risk across the attack surface: unseen assets, IT, OT, IOT, cloud, identities and applications.
Vulnerability intelligence
Access the most complete knowledgebase of vulnerability and threat insights from Tenable Research, NVD and other trusted sources in a single place.
Third-party data sources
Integrate and consolidate asset and risk data from your existing tools, and put it to work along side your trusted Tenable data.
Cloud exposure
Discover and prioritize remediation of cloud exposure across all your clouds, assets and identities with the most actionable CNAPP.
Vulnerability exposure
Discover and prioritize remediation of vulnerability exposure across the modern attack surface with industry-leading vulnerability management.
OT exposure
Discover and prioritize remediation of operational exposure across your converged IT/OT/IoT environment.
Identity exposure
Discover and prioritize remediation of identity exposure across your Active Directory and Entra ID environments.
Tenable One
The AI-powered exposure management platform that unifies security visibility, insight and action across the attack surface.
End your exposure
Scattered products and siloed views have left organizations struggling to hold back threats across a fragmented attack surface. But we know the war against cyber risk won’t be won with security strategies and solutions that stand divided. Tenable One gives enterprises a single, unified view of risk truth across all types of assets and attack pathways. It connects the dots between the lethal relationships that span solution silos, rapidly finding and fixing the priority exposures that drive up business risk.
PW form misconfig
Unpatched
CVE
Excecutive permissions

commerce
offline
All types of assets. All risks. All in.
Delivering the world’s only exposure protection spanning the entire modern attack surface, Tenable One enables organizations to expose and close cyber weaknesses anywhere to reduce business risk everywhere.
Know your attack surface
All breaches start with a single compromised asset or identity. Comprehensive Inventory provides visibility into your entire external and internal attack surface, identifying unseen and unmanaged assets and risk that could open the door for attackers.
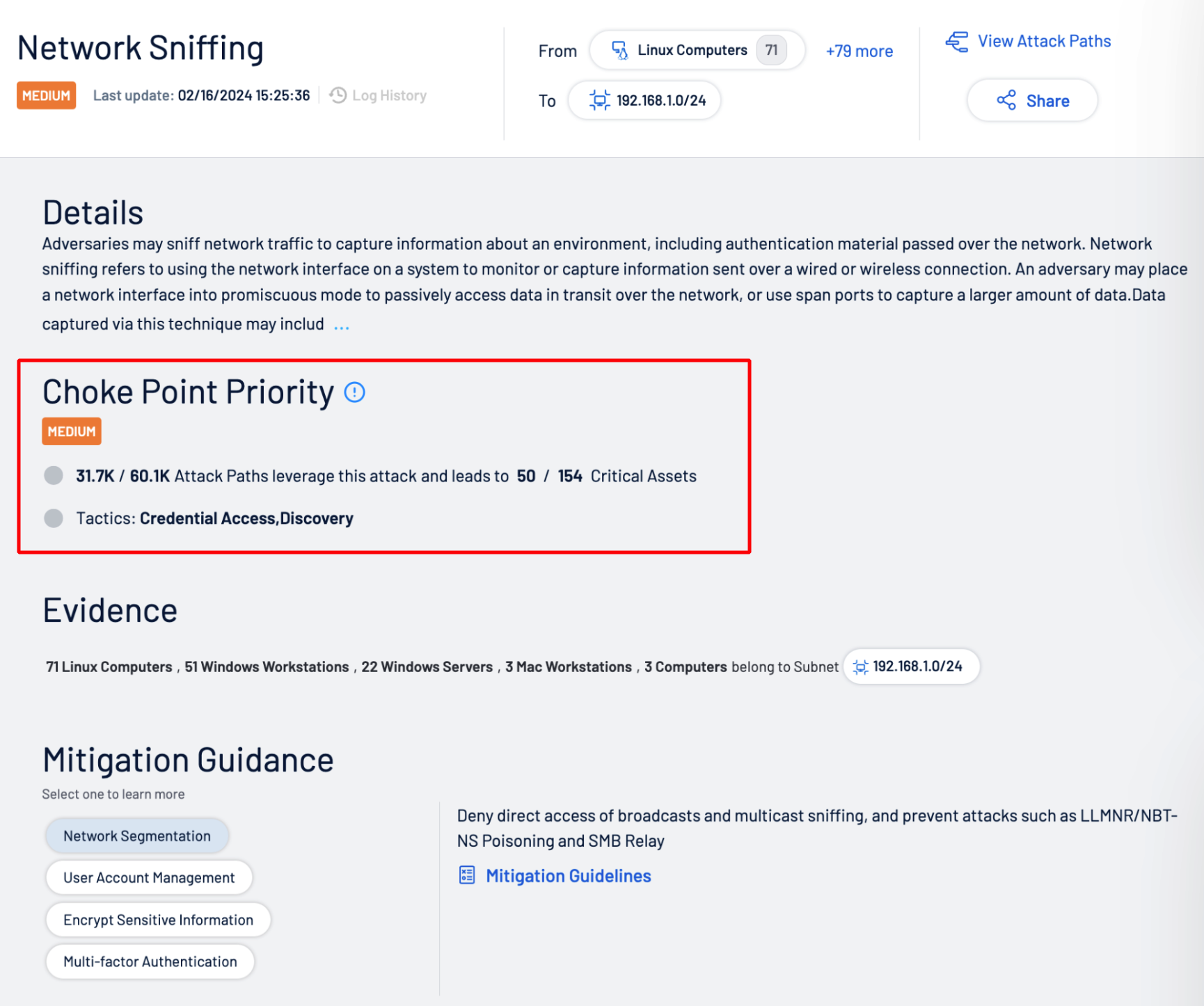
Pinpoint priority weaknesses
Focus on the actual exposures that matter to reduce cyber risk. Exposure Signals helps you find toxic combinations of vulnerabilities, identity exposure and threats impacting assets that leave you highly exposed.
See what attackers see
Attackers exploit common vulnerabilities, misconfigurations and excess permissions to move laterally and realize an intended outcome. Attack Path Analysis maps critical asset, identity and risk relationships to pinpoint high-risk attack paths before any attack or material impact to the organization is underway.
Learn moreAccelerate insight with AI
To eradicate priority exposures across domains, moving rapidly from information to intelligence is essential. With more than 1 Trillion data points, Exposure Graph is the world's largest repository of exposure data and context. By simply asking questions in natural language, ExposureAI empowers teams to access the actionable insights they need to outmaneuver adversaries. For example:
- Does this asset have an exploitable risk?
- How do I mitigate that risk?
- How many users or groups have access to this asset?
Quantify your exposure
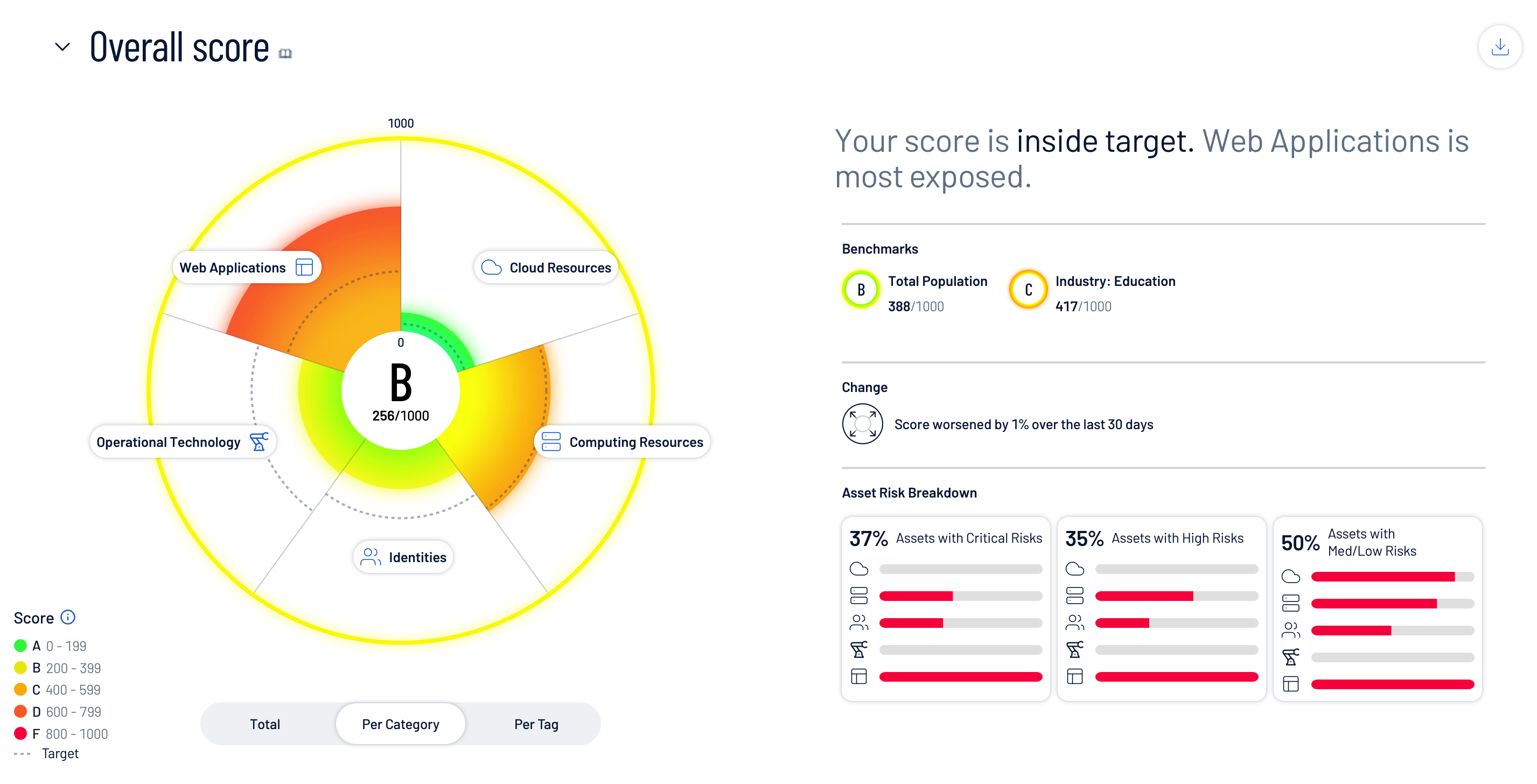
Crown jewel assets advance missions, relationships and revenue. Tailored Exposure Views provide quantified, business-aligned views of what matters most, including highest-risk assets by business function, security domains posing the greatest risk and the security posture of your peers.
Exposure views answer:
- How secure are we?
- Are we meeting our commitments?
- Where should we apply limited resources?
Eradicate your true exposures
Not every risk is created equal. Tenable One puts risk in context, enabling organizations to isolate and eradicate the exposures that represent their biggest business threats. Rather than fix every weakness, analysts can focus on choke points with the power to eliminate hundreds of interconnected attack paths. Prescriptive guidance ensures teams can act with maximum speed and confidence.
Realize better outcomes with Tenable One
Tenable One customers see measurable improvements in security posture and business outcomes.
with technology
FAQs
What is Tenable One?
-
Tenable One is an Exposure Management Platform to help organizations gain visibility across the modern attack surface, focus efforts to prevent likely attacks and accurately communicate cyber risk to support optimal business performance.
The platform combines the broadest vulnerability coverage spanning IT, OT and IoT assets, cloud resources, containers, web apps and identity systems, builds on the speed and breadth of vulnerability coverage from Tenable Research and adds comprehensive analytics to prioritize actions and communicate cyber risk. Tenable One allows organizations to:
- Gain comprehensive visibility across the modern attack surface
- Anticipate threats and prioritize efforts to prevent attacks
- Communicate cyber risk to make better decisions
What is Exposure AI?
-
ExposureAI is how Tenable uses AI (generative artificial intelligence, deep learning, AI and machine learning) to fuel our exposure management capabilities. ExposureAI helps to improve end user productivity to enable preventive security with the following use cases:
- Explain: Derive succinct guidance to better understand product findings.
- Search: Simplify search across your asset inventory for complete visibility.
- Action: Proactively deliver insights for actions with the most impact.
What is Tenable Exposure Graph?
-
Tenable Exposure Graph is the unified data platform in Tenable One that aggregates, normalizes and stores asset, exposure and threat data across IT assets, cloud resources, web applications and identity systems. Exposure Graph contains the largest repository of contextual exposure data in the world, which powers ExposureAI insights and our exposure management products.
How long has Tenable been using artificial intelligence?
-
Tenable has been using artificial intelligence in our products for many years. Notable examples include:
Vulnerability Priority Rating (VPR): Released in 2019, VPR incorporates machine learning-based algorithms to identify vulnerabilities most likely to be exploited in the short term, analyzing each vulnerability daily to predict the likelihood of an exploit actually being used against it.
Operating System (OS) Prediction: Released in 2020, OS Prediction leverages machine learning-based algorithms to predict an unauthenticated asset’s operating system via host response to TCP packet data in order to increase assessment and inventory accuracy.
Predictive Scoring: Released in 2020, Predictive Scoring incorporates machine learning-based algorithms to predict an asset's risk from limited, unauthenticated scan data using data derived from authenticated scans and exposure characteristics of similar assets.
Generative AI Research Tools: Tenable Research developed and released four generative AI-based research tools to help improve efficiency and effectiveness in processes, such as reverse engineering, code debugging, web app security and visibility into cloud-based tools.
Tenable Identity Exposure: Released in 2023, Tenable Identity Exposure incorporates AI-based methods to provide a unified view of all user identities and entitlement risks across on-prem and cloud environments.
Does Tenable One provide assessment capabilities to detect AI vulnerabilities?
-
Yes, Tenable One provides a wide range of detection methods that surface AI software packages, libraries and browser plugins. This helps you to monitor unauthorized AI usage, detect AI vulnerabilities and gain clarity on AI development occurring within your organization. Findings and results are available through AI Aware, reports and dashboards in Tenable One, Tenable Vulnerability Management, and Tenable Security Center.
Which Tenable products are included in Tenable One?
-
Tenable One includes the following Tenable products. The full functionality of each of these products is included in Tenable One.
Which capabilities are included in Tenable One?
-
Capabilities include:
- Exposure View: Enables focused security efforts through clear, concise insight into your organization’s security exposure answering such critical questions as “how secure are we” and “where do we stand in our preventative and mitigation efforts?” “how are we doing over time?” and “what are the key events?”
- Tag Performance: Addresses which tags make up an exposure card and how much that group of assets contributes to a given exposure score.
- Attack Path Analysis: With more than 150 supported attack techniques, Attack Path Analysis gives security practitioners a glimpse into the attacker mindset. It continuously monitors gaps across endpoint, identity and cloud to proactively visualize attack paths and mitigate high-risk exposures. It performs this function by mapping critical risks to the MITRE ATT&CK framework to visualize all viable attack paths continuously — both on-prem and in the cloud.
- Inventory: Centralized view of all assets, weaknesses and tags, including IT, OT, IoT, cloud, identities and web apps, with the ability to create specific asset tags from a variety of sources.
- External Attack Surface Management (EASM): Provides insight into the external attack surface, empowering your organization to identify and reduce risks from the attacker’s perspective.
- Custom Exposure Cards: Enables concise, flexible communication of specific security insights.
- News: Integration with Tenable Research blogs allow for creation of custom exposure cards that reflect cyber security developments.
What is the difference between the Exposure View in Tenable One and the Cyber Exposure Score in Tenable Lumin?
-
Lumin’s Cyber Exposure Score (CES) is derived from vulnerability prioritization and asset criticality scores. The Exposure View score in Tenable One is derived from the CES score along with inputs from data derived from the other products contained within Tenable One - including cloud, identity, web application security and attack surface management.
Are there other options available for Tenable One?
-
Yes, add-on SKUs are available for additional cloud scanners for WAS, Tenable Just in Time (JIT) and Identity Exposure On-Prem.
Is Tenable One cloud-based?
-
Yes, Tenable One is mainly a cloud-based solution. However, customers can deploy their vulnerability management assets in the cloud with Tenable Vulnerability Management and/or on-premises with Tenable Security Center Plus.
Related resources
Get Started with Tenable One
Tenable One has helped our engineers reduce the time spent on manual tasks by 75%, which allows them to focus on actual engineering work.
- Tenable One