Tenable versus CrowdStrike Falcon Cloud
Proactively reduce cloud risk with Tenable Cloud Security
Don’t wait to play defense. While CrowdStrike focuses on reacting to active threats, Tenable takes a proactive stance. By contextualizing all potential threats to your environment, Tenable effectively prioritizes and remediates your most critical risks - before they emerge.
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form to get a custom quote or demo.
Why customers choose Tenable Cloud Security over CrowdStrike Falcon Cloud
Compare Tenable Cloud Security to
CrowdStrike Falcon Cloud
Cloud toxic combinations
Full-stack and identity correlation for prioritization and visibility of toxic combinations
Lacks toxic combination visibility
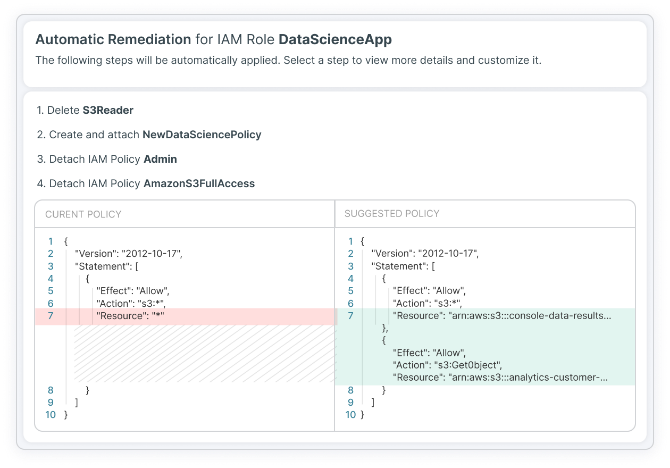
Remediation
Clear remediation details:
- Push-button IAM remediation
- Push-button IaC remediation
- Instructive guardrail guidance for modifications
Lacks IAM push-button remediation and push-button IaC remediation. Lacks instructive guardrails
Permissions query
No-code multi-cloud permission query
Lacks dedicated multi-cloud permissions query dashboard
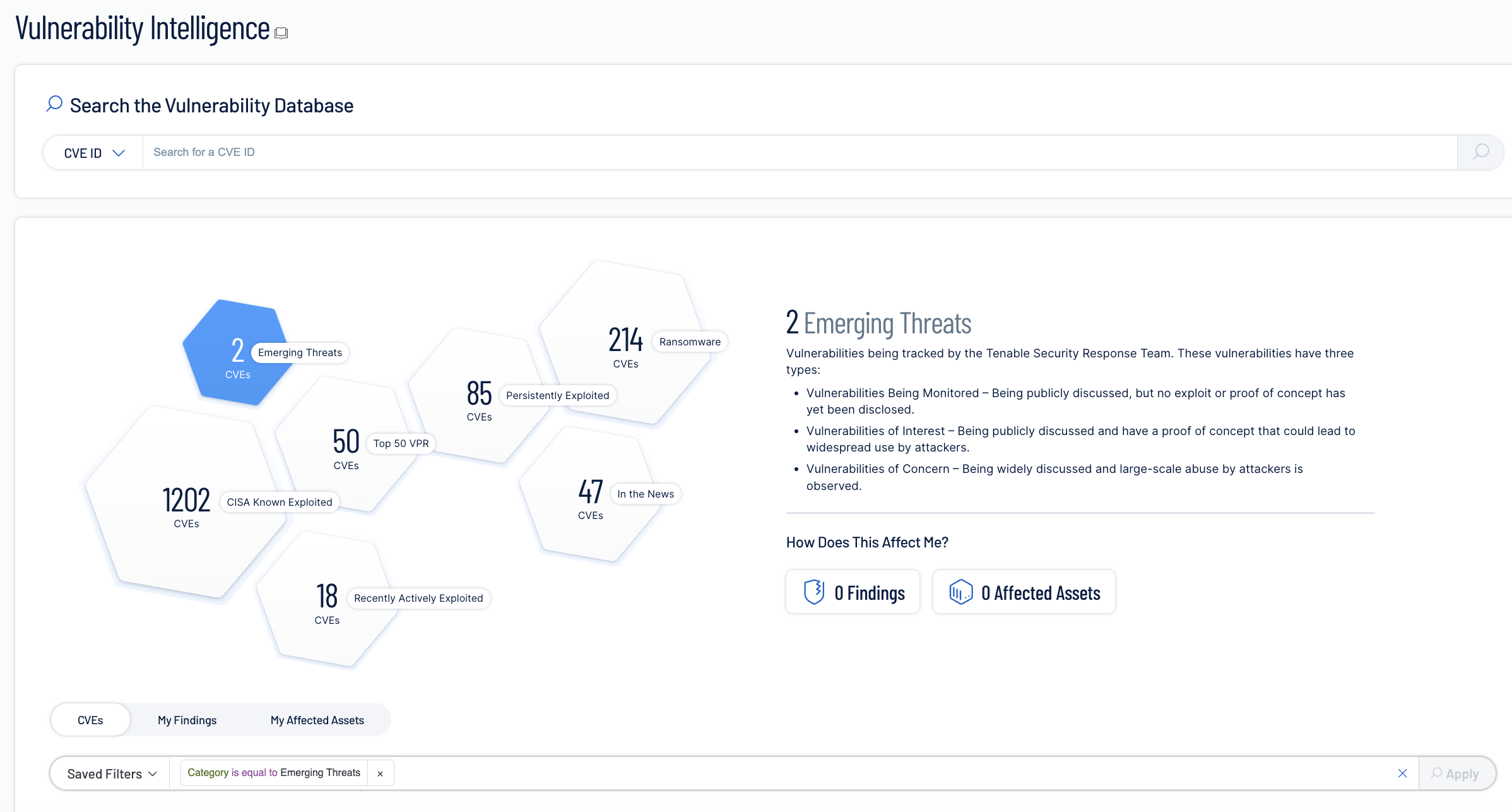
Vulnerability intelligence
Full vulnerability context fueled by Tenable Research and 50 trillion data points
Malware-focused, lacks vulnerabilities context
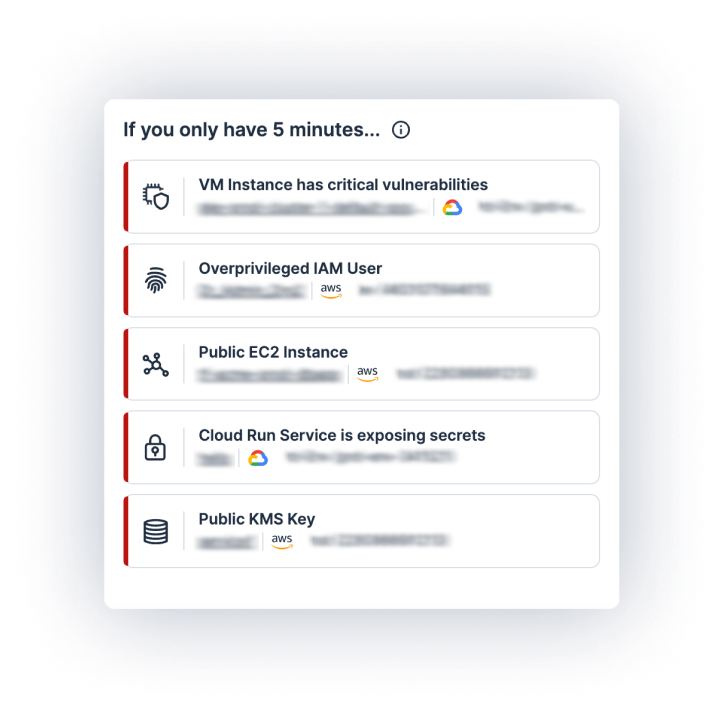
Industry-leading cloud identity visibility and security
Limited views and depth
Prioritize, remediate and optimize your cloud security
2024 Cloud Security Outlook
Tenable Cloud Security study reveals a whopping 95% of surveyed organizations suffered a cloud-related breach over an 18-month period.
Read the reportIDC Info Snapshot: Navigating cloud security complexities — Identity at the core
“39% of organizations face insufficient integration between security and IT infrastructure teams, whether at the level of people, processes or solutions…securing digital identities is foundational for establishing digital trust and ensuring cyber-resiliency.”
Read the reportSee Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form to get a custom quote or demo.