by Cesar Navas
April 23, 2024
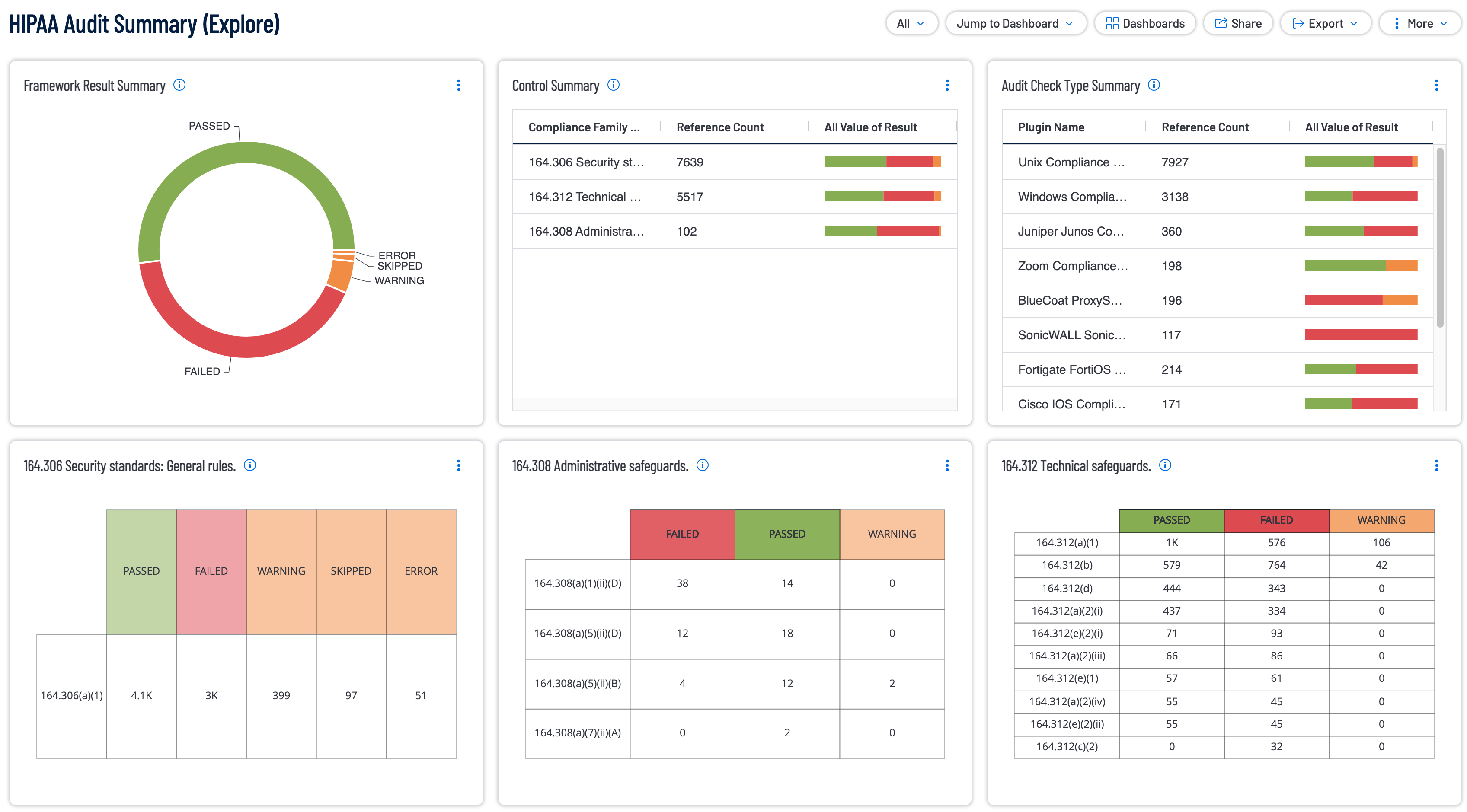
Healthcare providers involved in the transmission of Protected Health Information (PHI) or Electronic Protected Health Information (ePHI) must comply with the Health Insurance Portability and Accountability Act (HIPAA) security rules. As system configuration complexity increases, the organization’s struggle to meet hardening standards continues to rise. This dashboard provides users with a simplistic view of HIPAA related configuration audit checks.
The Administrative Simplification provisions of the Health Insurance Portability and Accountability Act of 1996 (HIPAA, Title II) required the Department of Health and Human Services (HHS) to establish national standards for the security of electronic health care information. The final rule adopting HIPAA standards for security was published in the Federal Register on February 20, 2003. The legislation specifies a series of administrative, technical, and physical safeguards for covered entities to use to assure the confidentiality, integrity, and availability of ePHI. Each safeguard category consists of standards and implementation specifications.
The Health Information Technology for Economic and Clinical Health (HITECH) Act was enacted as part of the American Recovery and Reinvestment Act of 2009. HITECH increases the scope of security and privacy protections for ePHI previously set forth by HIPAA. The HITECH Act also addresses liability and enforcement when violations or breaches occur.
This dashboard can assist an organization in monitoring and improving its compliance with HIPAA configuration requirements. Analysts can use this dashboard to further investigate configuration errors using the HIPAA related audit checks. This will, in turn, help the organization better protect itself from exploitation of network vulnerabilities, and potential intrusions, attacks, and data loss.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management (formerly Tenable.io) discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable Vulnerability Management.
Widgets:
- Framework Result Summary - This widget provides compliance results (Passed, Warning, Error, Failed) results for the compliance standard being referenced.
- Control Summary - This widget provides compliance results for each control family within the compliance standard. Each family displays information highlighting the result count and a bar chart displaying a visual overview of the results.
- Audit Check Type Summary - This widget provides compliance results for Windows and Unix hosts within the compliance standard. The rows display information highlighting the result count and a bar chart displaying a visual overview of the results.
- 164.306 Security standards: General rules - This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 164.308 Administrative safeguards - This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 164.312 Technical safeguards - This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.