Cybersecurity Snapshot: WEF Offers AI Security Best Practices, as DORA Regulation Places Strict Cyber Rules on Banks

Check out tips for adopting AI securely from the World Economic Forum. Plus, the EU’s DORA cyber rules for banks go into effect. Meanwhile, a report warns about overprivileged cloud accounts. And get the latest on ransomware trends; CIS Benchmarks; and data privacy.
Dive into six things that are top of mind for the week ending Jan. 24.
1 - WEF: Best practices to adopt AI securely
As businesses scramble to adopt artificial intelligence to boost their competitiveness, they’re also grappling with how to deploy AI systems securely and in line with policies and regulations.
If your organization is among the many that are looking for guidance on secure AI adoption, now you have have one more resource.
The latest guidance for adopting AI securely comes from the World Economic Forum, whose new “Artificial Intelligence and Cybersecurity: Balancing Risks and Rewards” report seeks to explain how organizations can benefit from AI while reducing their cybersecurity risks.
“By prioritizing cybersecurity and mitigating risks, organizations can safeguard their investments in AI and support responsible innovation,” the 28-page report reads.
Among the report’s recommended best practices are:
- Apply a risk-based approach to AI adoption, and create a cross-disciplinary risk-management team with members from departments including legal, human resources, cybersecurity, compliance and IT.
- Maintain an updated inventory of AI applications.
- Invest in essential cybersecurity controls for protecting AI systems both before and after they’re deployed, and for responding to and recovering from cyber incidents.
- Pay attention to information governance, such as what data will be exposed to AI systems and how it will be protected.

The report also suggests questions for cybersecurity leaders to ask in order to frame their AI adoption strategy, including:
- Have we established our AI risk tolerance and do all stakeholders understand it?
- Do we have a process to govern and track AI deployments?
- Do we weigh risks against rewards when considering new AI projects?
- Are we clear on who must be involved in assessing and mitigating AI adoption cyber risks?
“By assessing and mitigating cyber risks, leaders can align AI adoption with organizational goals and resilience needs,” reads the companion WEF article “Securing innovation: A leader’s guide to managing cyber risks from AI adoption.”
For more information about AI security, check out these Tenable blogs:
- “How AI Can Boost Your Cybersecurity Program”
- “6 Best Practices for Implementing AI Securely and Ethically”
- “How to Discover, Analyze and Respond to Threats Faster with Generative AI”
- “Securing the AI Attack Surface: Separating the Unknown from the Well Understood”
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources”
2 - DORA cyber regulation for banks and their tech providers goes into effect
Financial services companies doing business in the European Union, as well as their technology and communications vendors, now must comply with the Digital Operational Resilience Act (DORA).
DORA establishes strict cybersecurity requirements for financial firms including banks, insurance companies and investment firms, as well as for third-parties that provide information and communications technology (ICT) products and services to financial sector organizations.
After entering into force in January 2023, the DORA regulation became applicable last week. It covers ICT security areas including:
- Risk management, including the risk posed by third parties
- Resilience testing of digital operations
- Reporting of significant cybersecurity incidents
- Sharing of information about cyberthreats and vulnerabilities

“DORA will strengthen the ability of financial firms to withstand cyber‑related disruptions and threats and ensure a swift recovery if incidents do occur,” reads a statement from the European Commission.
“The framework also includes an oversight mechanism of critical third‑party providers of ICT services to financial entities, such as cloud service providers,” the statement adds.
To find out how Tenable can help with DORA compliance, read the “Tenable Cyber Exposure Study: DORA” document.
For more information about the EU’s DORA cybersecurity regulation for the financial sector:
- “DORA Takes Effect: Financial Firms Still Navigating Compliance Headwinds” (Infosecurity Magazine)
- “Tough new EU cyber rules require banks to ramp up security — but many aren’t ready” (CNBC)
- “DORA compliance is a strategic necessity for U.S. companies serving EU financial institutions” (Security Infowatch)
- “A guide to DORA compliance” (ComputerWeekly)
- “What CIOs should know as DORA regulations kick in” (CIO Dive)
VIDEOS
Understanding the Digital Operational Resilience Act (Deloitte)
DORA compliance for ICT Providers - What Do You Need to Do? (IT Governance)
3 - Google: Hackers shift sights to overprivileged cloud accounts
Cloud accounts that have more privileges than they should are increasingly attracting the attention of hackers.
That’s because taking over these overprivileged service accounts makes it easier for cyber crooks to move laterally within a breached cloud environment, according to Google Cloud’s “H1 2025 Threat Horizons Report.”
Cloud Risk Alerts Detected in H2 2024
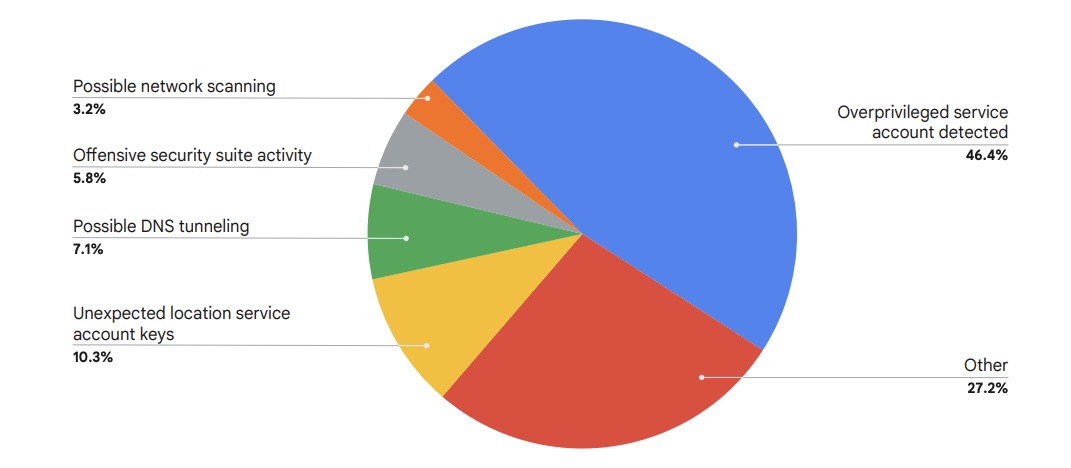
(Source: Google Cloud’s “H1 2025 Threat Horizons Report,” January 2025)
Meanwhile, weak or no credentials (45.7%) and misconfigurations (34.3%) ranked as the top two initial access vectors to cloud environments during the second half of last year.
Once in, attackers most often attempt to move laterally (62.2%). They also go looking for insecure private keys (13.7%) and attempt to manipulate access tokens (11.3%).
For more information about cloud security, check out these Tenable resources:
- “Who’s Afraid of a Toxic Cloud Trilogy?” (blog)
- “Holistic Security for AWS, Azure and GCP: Comprehensive Cloud-Native Application Protection for Multi-Cloud Environments” (white paper)
- “Identities: The Connective Tissue for Security in the Cloud” (blog)
- “Cloud Leaders Sound Off on Key Challenges” (blog)
- “Understanding Cloud-Native Application Protection Platforms” (guide)
4 - Report: Ransomware attacks uncharacteristically jumped in December
Apparently, ransomware groups didn’t take a break during the holidays, as they normally do.
NCC Group, which has been tracking ransomware activity since 2021, said it tallied the most attacks ever during December, which is usually a quieter month for ransomware attacks.
Funksec, a new cyber extortion gang, ranked first with 18% of all attacks – followed by CL0P, Akira and RansomHub, according to NCC Group’s December 2024 Monthly Threat Pulse report.
Funksec uses double extortion—encrypting and exfiltrating victims’ files—and operates a Tor-based data leak site. There, it posts breach announcements and offers a free DDoS tool.
NCC Group calls the December data a “wake-up call.”

As newer, more aggressive ransomware gangs emerge, cybersecurity teams may encounter a more challenging threat landscape in 2025, with attacks occurring more frequently and broadly. A proactive cybersecurity approach is key.
“Companies need to double down on their cybersecurity measures and ensure that their teams are trained and prepared to evolve with the changing nature of ransomware threats,” Ian Usher, NCC Group Associate Director of Threat Intelligence Operations, said in a statement.
This is especially true for the industrials sector, which includes critical infrastructure organizations and was the most targeted, receiving 24% of all December attacks.
For more information about ransomware trends:
- “Tenable Cyber Exposure Study - Defending Against Ransomware” (Tenable)
- “Threat actors abusing Microsoft Teams in ransomware attacks” (TechTarget)
- “Data recovery after fulfilling ransomware attack demands mostly unlikely” (SC World)
- “Ransomware: Predictions and Actions in 2025” (SC Magazine)
- “Ransomware is 35 years old and now a billion-dollar problem. Here’s how it could evolve” (CNBC)
5 - Survey: Practicing “privacy by design” makes a difference
Want to boost your organization’s privacy practices? A new ISACA report recommends practicing “privacy by design,” which is the process of integrating privacy considerations into the organization’s entire engineering process.
ISACA’s “State of Privacy 2025” report found that organizations that always use a “privacy by design” approach when building new applications and services do better than organizations that use it less frequently or not at all.

According to the report, based on a global survey of about 1,600 cybersecurity and privacy professionals, organizations that always use “privacy by design” tend to have more support and resources, and are more likely to have:
- A board of directors that adequately prioritizes privacy
- An appropriately funded enterprise privacy budget
- An appropriately staffed technical privacy team
- A privacy strategy aligned with organizational objectives
- Confidence in their ability to ensure data privacy and comply with privacy regulations
Other recommendations for having strong enterprise privacy programs include:
- Have one person who is primarily responsible for privacy
- Work closely with the legal and compliance teams to ensure privacy compliance
- Address privacy with documented policies, processes and standards
- Use AI to help manage and classify collected data, and to identify personal information
- Offer privacy awareness training to employees
6 - CIS updates Benchmarks for Apple, Microsoft products
Apple macOS and Microsoft Windows Server were two CIS Benchmarks updated in December by the Center for Internet Security.
Specifically, these CIS Benchmarks were updated:
- CIS Apple macOS 12.0 Monterey Benchmark v4.0.0
- CIS Apple macOS 14.0 Sonoma Cloud-tailored Benchmark v1.1.0
- CIS Microsoft Intune for Office Benchmark v1.1.0
- CIS Microsoft Windows Server 2019 STIG Benchmark v3.0.0
- CIS Microsoft Windows Server 2022 STIG Benchmark v2.0.0
- CIS Red Hat OpenShift Container Platform Benchmark v1.7.0
- CIS SUSE Linux Enterprise 15 Benchmark v2.0.0

The CIS Benchmarks’ secure-configuration guidelines are intended to help you harden products against attacks. Currently, CIS offers more than 100 Benchmarks for 25-plus vendor product families. There are CIS Benchmarks for cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks January 2025 Update.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
- AI
- Cloud
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
