CVE-2019-10149: Critical Remote Command Execution Vulnerability Discovered In Exim

Researchers discover critical remote command execution vulnerability in older versions of Exim. Over 4.1 million systems are potentially vulnerable to local exploitation and remote exploitation is possible in non-default configurations.
Background
On June 3, maintainers of the mail transfer agent (MTA) known as Exim acknowledged on the open source security (OSS) mailing list the existence of a critical vulnerability in Exim versions 4.87 through 4.91 reported to them by security researchers at Qualys. On June 5, the security researchers published an abridged advisory regarding their discovery on the same mailing list.
Update 6/13: Security researchers are now observing active exploitation attempts of this vulnerability in the wild.
Just detected the first attempts to exploit recent #exim remote command execution (RCE) security flaw (CVE-2019-10149). Tries to downloads a script located at http://173.212.214[.]137/s (careful). If you run Exim, make sure it's up-to-date. @qualys pic.twitter.com/s7veGBcKWO
— Freddie Leeman (@freddieleeman) June 9, 2019
1/n IMPORTANT, THREAD: Someone is actively exploiting vulnerable exim servers. The attackers are using that exim vuln to gain permanent root access via ssh to those exploited servers by using a script that's uploaded to that server through that exploit.
— Amit Serper (@0xAmit) June 13, 2019
Analysis
CVE-2019-10149 is a remote command execution vulnerability introduced in Exim version 4.87 which was released on April 6, 2016. In default configurations, a local attacker is capable of exploiting this vulnerability to execute commands as the “root” user “instantly” by sending mail to a specially crafted mail address on localhost that will be interpreted by the expand_string function within the deliver_message() function. Remote exploitation under the default configuration is possible, but considered to be unreliable, as an attacker would need to maintain connection to a vulnerable server for 7 days.
In certain non-default configurations, remote exploitation is possible. For instance, if the requirement for ‘verify = recipient’ ACL was removed from the the default configuration file (src/configure.default), uncommenting out the ‘local_part_suffix = +* : -*’ under the userforward router in the default configuration, or if Exim was “configured to relay mail to a remote domain, as a secondary MX (Mail eXchange).”
Proof of concept
At the time this blog was published, no proof-of-concept (PoC) was available for this vulnerability. However, further details about how to exploit the vulnerability were shared on June 6 and have been used to launch attacks, as the above update indicates.
Impact Assessment
Exim is widely distributed. At the time of publication, Shodan search results show over 4.1 million systems running versions of Exim that are considered vulnerable (4.87-4.91), while 475,591 are running the latest patched version (4.92). In other words, nearly 90% of systems with Exim are vulnerable to local exploitation and potentially to remote exploitation based on the configuration.
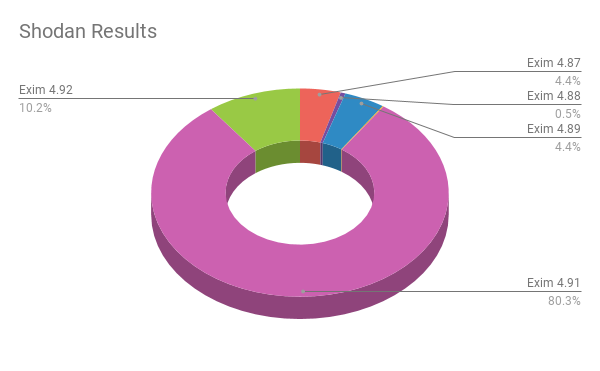
Total Results by Version Number
- Exim 4.87: 206,024
- Exim 4.88: 24,608
- Exim 4.89: 206,571
- Exim 4.90: 5,480
- Exim 4.91: 3,738,863
- Exim 4.92: 475,591
Solution
While this vulnerability was reported via the exim-security mailing list on May 27, 2019, it appears that the vulnerability was unknowingly patched in Exim version 4.92.
Exim maintainers announced that their fix for CVE-2019-10149 is now public and that it can be backported to all affected versions from 4.87 through 4.91. They note that older releases are “considered to be outdated” and are therefore no longer supported.
Some information about CVE-2019-10149 in Linux Distributions can be found here:
- Debian Security Tracker: CVE-2019-10149
- Red Hat CVE Database: CVE-2019-10149
- Ubuntu CVE Tracker: CVE-2019-10149
- Gentoo Bugzilla: CVE-2019-10149
- Amazon Linux Security Center: ALAS-2019-1221
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- Initial Report on CVE-2019-10149 on oss-security
- Abridged Advisory on CVE-2019-10149 on oss-security
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management
