Cybersecurity Snapshot: Cyber Agencies Offer Best Practices for Network Edge Security, While OWASP Ranks Top Risks of Non-Human Identities

Check out recommendations from CISA and others on how to protect network edge devices and applications. Plus, OWASP has published the 10 risks associated with non-human identities. In addition, find out why ransomware payments plunged in 2024. And a new U.K. non-profit will categorize cyber incidents’ severity. And much more!
Dive into six things that are top of mind for the week ending Feb. 7.
1 - New cyber guides unpack how to secure network edge wares
Looking for insights and best practices for preventing and mitigating cyberattacks against network edge hardware and software devices, such as routers, VPN gateways, IoT devices, web servers and internet-facing operational technology (OT) systems? You might want to check out new guidance published by several cybersecurity agencies this week.
“Foreign adversaries routinely exploit software vulnerabilities in network edge devices to infiltrate critical infrastructure networks and systems,” reads a statement from the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
“These guidance documents detail various considerations and strategies for a more secure and resilient network both before and after a compromise,” the statement adds.

These are the new guides, jointly published by cyber agencies from various countries:
- Security Considerations for Edge Devices, led by the Canadian Centre for Cyber Security (CCCS), includes:
- A description of common threats to edge devices, such as misconfigurations and mismanagement; vulnerability exploitation; and denial of service attacks
- Examples of edge device compromises
- Recommendations for mitigating threats to edge devices
- Digital Forensics Monitoring Specifications for Products of Network Devices and Applications, led by the U.K.’s National Cyber Security Centre (NCSC), explains why and how edge devices should support event logging and forensic data acquisition.
- Mitigation Strategies for Edge Devices: Executive Guidance and Mitigation Strategies for Edge Devices: Practitioner Guidance, two guides led by the Australian Cyber Security Centre (ACSC), focus on threat mitigation and are aimed, respectively, at executives responsible for enterprise network security; and at operational, cybersecurity and procurement staff for edge devices.
“As organizations scale their enterprises, even though securing all devices is important, prioritizing edge device security is vital to defend the many endpoints, critical services, and sensitive data they protect,” Eric Chudow, a U.S. National Security Agency cybersecurity vulnerability analyst, said in a statement.
For more information about network edge vulnerabilities, check out these Tenable blogs:
- “New CISA Hardening Guidance Provides Valuable Insights for Network Security Engineers”
- “Salt Typhoon: An Analysis of Vulnerabilities Exploited by this State-Sponsored Actor”
- “Volt Typhoon: U.S. Critical Infrastructure Targeted by State-Sponsored Actors”
- “CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild”
- “CVE-2024-21762: Critical Fortinet FortiOS Out-of-Bound Write SSL VPN Vulnerability”
- “Rockwell Automation: Disconnect OT Devices with Public-Facing Internet Access, Patch or Mitigate Logix, FactoryTalk CVEs”
- “CVE-2023-20198: Zero-Day Vulnerability in Cisco IOS XE Exploited in the Wild”
2 - OWASP ranks top cyber risks of non-human identities
Recognizing the significant growth in non-human identities (NHIs), such as access keys and service accounts, OWASP has published a list of the 10 most critical risks associated with them.
The goal of the “OWASP Non-Human Identities Top 10” project is to make software developers and security pros aware of NHI risks and of the best practices to prevent and mitigate related threats.
“Non-human identities are prevalent in usage for facilitating creation of applications by developers, and the project is aimed at helping security professionals thoroughly understand their non-human attack surface, so they can better protect and manage it,” reads the project’s home page.

Here’s the OWASP list of the top 10 NHI risks:
- NHI1:2025 - Improper Offboarding, which refers to inadequate deactivation or removal of NHIs after they’re no longer needed
- NHI2:2025 - Secret Leakage, which refers to the insecure exposure of NHIs such as API keys, tokens and certificates in a way that could allow attackers to exploit them
- NHI3:2025 - Vulnerable Third-Party NHI, which refers to NHIs from external sources that are integrated into a development environment and that have a security flaw
- NHI4:2025 - Insecure Authentication, which refers to NHIs whose authentication methods are unsafe because, for example, they’re obsolete or vulnerable to attacks
- NHI5:2025 - Overprivileged NHI, which refers to NHIs that are assigned excessive privileges, making them a major risk if they’re ever compromised
- NHI6:2025 - Insecure Cloud Deployment Configurations, which refers to the use of insecure NHIs, such as dedicated service accounts with static credentials, to authenticate cloud services in CI/CD pipelines
- NHI7:2025 - Long-Lived Secrets, which refers to the use of NHIs, such as API keys and encryption keys, that either expire too far off in the future or that never expire
- NHI8:2025 - Environment Isolation, which refers to the use of the same NHIs throughout an application’s lifecycle, including in its development, testing, staging and production environments
- NHI9:2025 - NHI Reuse, which refers to the use of the same NHIs in different applications, services or components
- NHI10:2025 - Human Use of NHI, which refers to the manual use by people of NHIs, which can result in elevated privileges for NHIs and other risks
“This comprehensive list highlights the most critical challenges in integrating NHIs into the development lifecycle, ranked based on exploitability, prevalence, detectability, and impact,” reads the project’s home page.
For more information about securely managing digital identities:
- “Who’s Afraid of a Toxic Cloud Trilogy?” (Tenable)
- “The State of Non-Human Identity Security” (Cloud Security Alliance)
- “Non-Human Identities Gain Momentum, Requires Both Management, Security” (TechTarget)
- “Managing Non-Human Identity Risks” (Non-Human Identity Management Group)
- “What are non-human identities and why do they matter?” (CSO)
3 - Report: Ransomware payments dropped in 2024
If your organization suffers a ransomware attack, would it be less willing to pay the attackers than, say, it would have been a few years ago? If so, then you’d be part of a growing trend.
Last year, ransomware gangs collectively pocketed less money than in 2023, as victims refused to shell out ransom payments in more than half of 2024 incidents.
That’s according to blockchain analytics firm Chainalysis, which this week said that although ransomware incidents grew in 2024, ransom payments shrunk significantly compared with 2023.
Another factor that disrupted ransomware activity was a variety of global law enforcement efforts that hobbled major ransomware players.
Specifically, ransomware groups collected about $814 million from victims last year, down 35% from $1.25 billion in 2023.
Interestingly, ransomware payments in the first half of 2024 were up about 2.4%, compared with the same period in 2023. However, payments then declined about 40% in 2024’s second half.
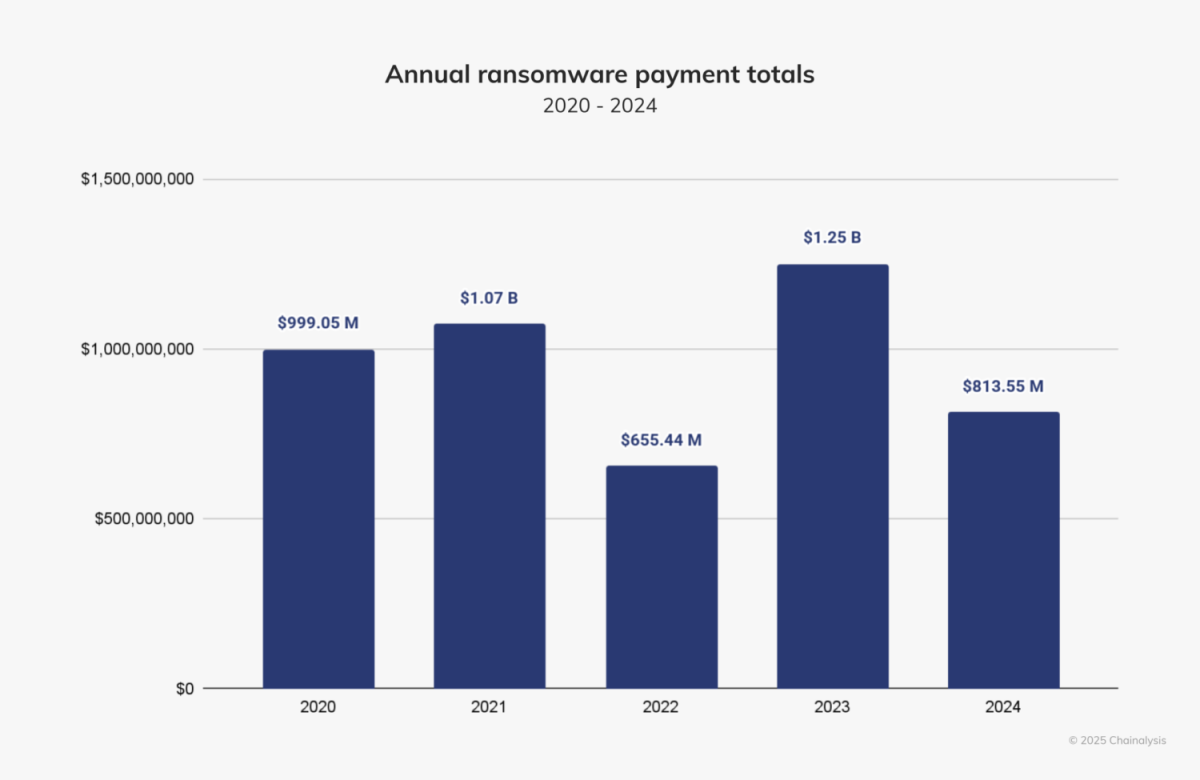
(Source: Chainalysis, February 2025)
Two large ransomware gangs whose activity plummeted in the second half of 2024 were LockBit, which was hit by law enforcement actions, and ALPHV/BlackCat.
Although lone actors and smaller new groups emerged, they weren’t able to fully fill the ransom-payment void left by disrupted larger groups, which also included Blacksuit and Silent/Luna Moth.
“Ransomware in 2024 reflected shifts driven by law enforcement action, improved victim resilience, and emerging attack trends,” reads Chainalysis’ report.
For more information about recent ransomware trends and incidents:
- “Ransomware: Predictions and Actions in 2025” (SC Magazine)
- “New ransomware group Funksec is quickly gaining traction” (CSO)
- “Lynx Ransomware Group 'Industrializes' Cybercrime With Affiliates” (Dark Reading)
- “Ransomware crew abuses AWS native encryption, sets data-destruct timer for 7 days” (The Register)
- “Act fast to blunt a new ransomware attack on AWS S3 buckets” (CSO)
4 - New non-profit will analyze and rate U.K. cyber incidents
The Cyber Monitoring Centre (CMC) went live this week with the charter of using a standard and uniform criteria for rating the severity of cybersecurity incidents that impact U.K. businesses.
An independent non-profit organization, the CMC hopes its work will help organizations more clearly grasp the consequences of cyber incidents so that they can improve their mitigaton and response.
“The CMC has the potential to help businesses and individuals better understand the implications of cyber events, mitigate their impact on people’s lives, and improve cyber resilience and response plans,” reads a CMC statement.

The CMC has developed a framework for assessing and analyzing cyber incidents that affect multiple companies and could potentially cause more than £100 million in losses. The CMC’s technical committee will gather cyber incident data and use the framework to analyze it.
“Measuring the severity of incidents has proved very challenging,” Ciaran Martin, the CMC’s technical committee chairman and a former head of the U.K. National Cyber Security Centre, said in the statement.
“I have no doubt the CMC will improve the way we tackle, learn from, and recover from cyber incidents,” he added.
Once it has completed its analysis of an incident, the CMC will rate it between 1 (least severe) and 5, and create a free report available to any interested organization.
To get more details about the CMC, check out the announcement “Cyber Monitoring Centre officially starts categorising cyber events” and the organization’s “Event Categorisation Methodology.”
5 - CISA alerts healthcare orgs about backdoor in Contec tool
Here’s one security warning for hospitals, clinics and other healthcare facilities.
The product Contec CMS8000, used to monitor patients’ vital signs, has a backdoor that can allow data leakage, remote code execution and device modification, CISA has warned.
The Contec CMS8000’s embedded backdoor function with a hard-coded IP address is present in three versions of the product’s firmware, according to CISA’s factsheet.

Two CVEs have been assigned to the issue: CVE-2025-0626 and CVE-2025-0683.
The Contec CMS8000 is also sold under different names, including Epsimed MN-120. The manufacturer, Contec Medical Systems, is based in Qinhuangdao, China.
To get more details about healthcare security, check out:
- CISA’s alert “CISA Releases Fact Sheet Detailing Embedded Backdoor Function of Contec CMS8000 Firmware”
- CISA’s factsheet “Contec CMS8000 Contains a Backdoor”
- CISA’s medical advisory “Contec Health CMS8000 Patient Monitor”
- The U.S. Food & Drug Administration’s safety communication “Cybersecurity Vulnerabilities with Certain Patient Monitors from Contec and Epsimed”
6 - E-marketplaces for cybercrime wares shut down
The U.S. Department of Justice and and Dutch National Police took down almost 40 domains and their servers that a Pakistan-based group had used for years to sell phishing toolkits, hacking wares and other cybercrime tools.
The group, known as Saim Raza and as HeartSender, had operated the now shuttered websites since at least 2020. Its customers were organized cybercrime groups that inflicted losses of more than $3 million on U.S. victims, mostly via business email compromise schemes.
“The seizure of these domains is intended to disrupt the ongoing activity of these groups and stop the proliferation of these tools within the cybercriminal community,” reads a DOJ statement.
In addition to selling cybercrime tools, Saim Raza also provided training via instructional videos posted on YouTube on how to use these products and on how to carry out cyber fraud operations.
For more information about cybercrime trends:
- “3 Cybercrime Trends Tech Pros Must Watch in 2025” (Dice)
- “Insider fraud and AI threats top forecasts of 2025 cybercrime” (American Banker)
- “DoJ Shutters Cybercrime Forums Behind Attacks on 17M Americans” (Dark Reading)
- “Cybercrime is increasingly complex. Here's how data awareness can help” (World Economic Forum)
- “Cybercriminals are using AI to target macOS in 2025” (Apple Insider)
- AI
- Cloud
- Industrial Control Systems Monitoring
- IT/OT
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Internet of Things
- OT Security


