Cybersecurity Snapshot: Beware of Mobile Spyware Attacks, Cyber Agencies Warn, While Corporate Boards Get Cyber Governance Guidance

Check out why a global geopolitical spyware campaign could ensnare mobile users outside of its target groups. Plus, the U.K.’s cyber agency offers cyber governance resources to boards of directors. Also, find out what webinar attendees told Tenable about using port scanning and service discovery to detect attack paths. And much more!
Dive into five things that are top of mind for the week ending April 11.
1 - Alert: Mobile spyware campaign could spill beyond targeted victims
Attackers are spreading two spyware variants in an attempt to infect mobile devices of individuals and groups tied to causes that the Chinese government opposes.
However, all mobile users should take heed because the campaign is global and aggressive, meaning anyone could become a victim.
So said cyber agencies from Australia, Canada, Germany, New Zealand and the U.S. in joint advisories this week, outlining how attackers are targeting supporters of various China-related movements with the BadBazaar and Moonshine spyware variants.
“The indiscriminate way this spyware is spread online also means there is a risk that infections could spread beyond intended victims,” reads one advisory.
Those targeted include journalists, non-governmental organizations, businesses and representatives of groups associated with:
- Taiwanese independence
- Tibetan rights
- Uyghur Muslims
- Hong Kong democracy advocacy
- Falun Gong movement

Moonshine and BadBazaar are two types of trojan malware, meaning attackers hide them in legit-looking mobile applications that users voluntarily download. In this particular campaign, attackers are embedding Moonshine and BadBazaar in applications designed to appeal to the intended victims, such as a Uyghur keyboard app and a Tibet-related app.
Once a user inadvertently installs a malicious app, attackers use it to obtain the mobile device’s location data in real-time; access its microphone and camera; retrieve stored messages and photos; and more.
The cyber agencies’ mitigation recommendations include:
- Don’t root or jailbreak your mobile device, as this leaves it more vulnerable to cyber attacks.
- Only download apps from trusted app stores like those from Google and Apple.
- Periodically review your installed apps and their permissions, deleting apps you no longer use and restricting excessive permissions.
- Be careful with links, files and apps shared on social media sites, online forums and messaging tools. Scan links with a URL reputation service before clicking on them, and upload suspicious files or apps to a malware analyzer.
The advisories mention a Chinese IT services firm with ties to China’s government as being possibly linked to the spyware campaign. However, the Chinese Embassy in Washington, D.C. told the Reuters news agency that the Chinese government isn’t involved in this situation.
To get more information, check out these resources from the U.K. National Cyber Security Centre (NCSC):
- The announcement “NCSC and partners share guidance for communities at high risk of digital surveillance”
- The advisory “BadBazaar and Moonshine: Spyware targeting Uyghur, Taiwanese and Tibetan groups and civil society actors”
- The technical advisory “BadBazaar and Moonshine: Technical analysis and mitigations”
For more information about protecting mobile devices against spyware attacks:
- “How to find and remove spyware from your phone” (ZDNet)
- “Did you know a VPN can protect you from spyware? Here's how” (Yahoo Tech)
- “Your Android phone could have stalkerware — here’s how to remove it” (TechCrunch)
- “Apple: Mercenary spyware attacks target iPhone users in 92 countries” (BleepingComputer)
- “Why rebooting your phone daily is your best defense against zero-click attacks” (ZDNet)
2 - NCSC offers cyber governance resources for corporate boards
With cybersecurity governance now one of their main responsibilities, boards of directors need strong cybersecurity knowledge – but many are lacking in this area.
That’s why the U.K. National Cyber Security Centre this week published a package of cyber governance resources for board members.
“From my experience of working with senior leaders across private and public sectors, I know that strong cyber governance is key to resilience, growth, and long-term success. Board members play a vital role in making this happen,” NCSC CEO Richard Horne wrote in a blog.

The NCSC cyber governance resources for board members include:
- The “Cyber Governance Code of Practice,” which outlines the board’s responsibilities in these five key governance areas:
- Risk management
- Strategy
- People
- Incident planning, response and recovery
- Assurance and oversight
- The “Cyber Governance Training” document, which provides five interactive training modules, each focusing on one of the “Code of Practice” principles
- The “Cyber Security Toolkit for Boards,” which explains how to implement the five key cyber governance areas
For example, for risk management the toolkit unpacks how to identify the organization’s critical assets and how to collaborate with its supply chain partners. In the strategy area, it goes into how to embed cybersecurity into the organization and what cybersecurity regulations are relevant to boards.
For more information about cyber governance guidance for boards of directors:
- “Principles for Board Governance of Cyber Risk” (Harvard Law School)
- “NACD Director's Handbook on Cyber-Risk Oversight” (National Association of Corporate Directors)
- “A cybersecurity guide for board directors” (Corporate Governance Institute)
- “How boards can effectively oversee AI to drive value and responsible use” (PwC)
- “Guidelines on the Corporate Governance of Cybersecurity” (Board Foundation)
3 - Tenable poll looks at port scanning for attack path detection
During a recent webinar about Tenable Nessus, we polled attendees about their use of port scanning and service discovery to detect attack paths. Check out what they said.
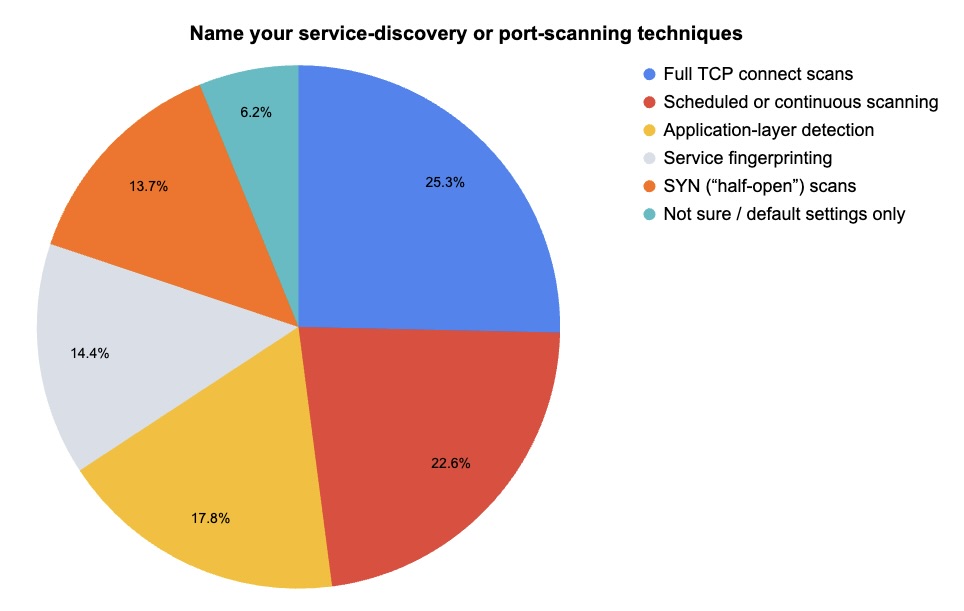
(65 webinar attendees polled by Tenable, April 2025 – Respondents could choose more than one answer.)
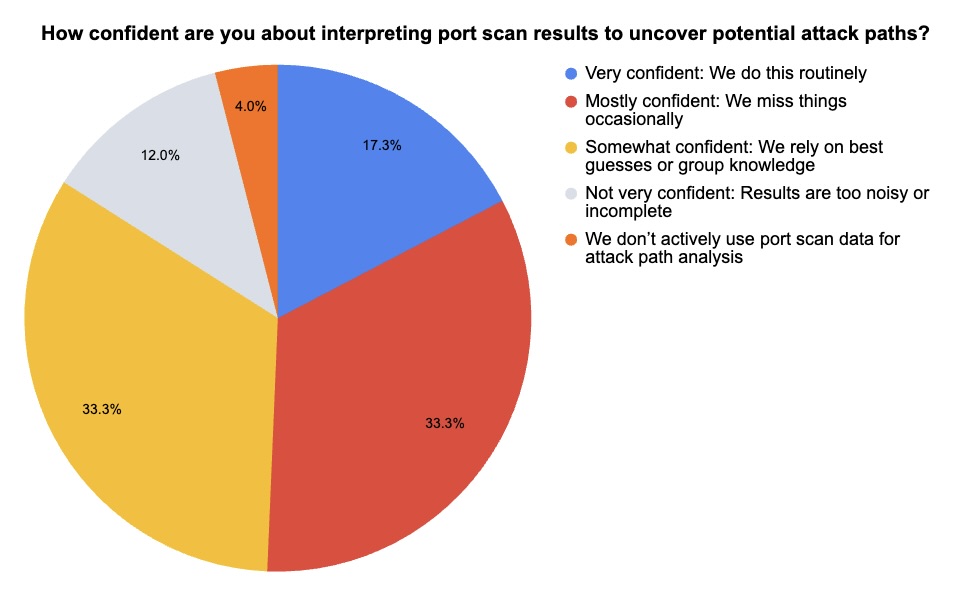
(75 webinar attendees polled by Tenable, April 2025)
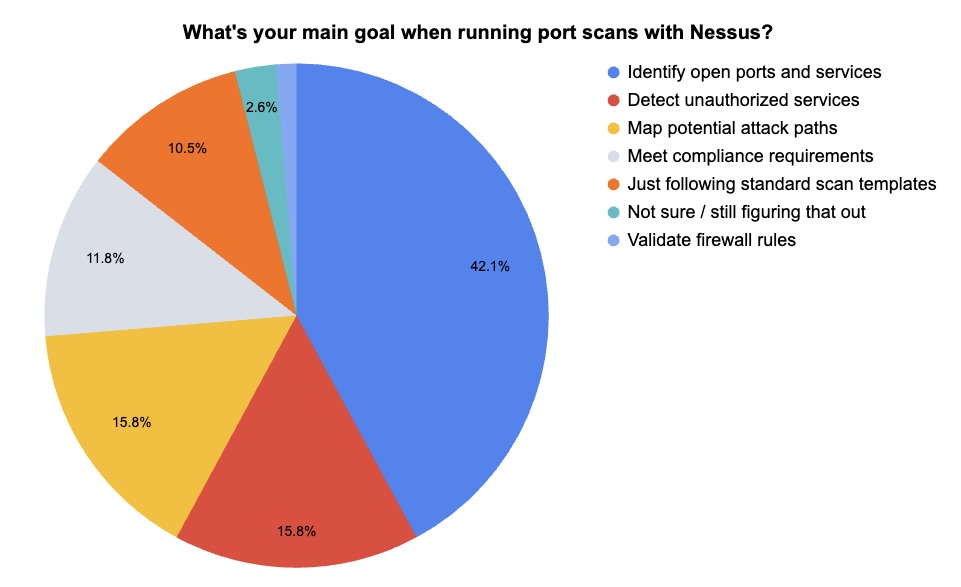
(76 webinar attendees polled by Tenable, April 2025)
Watch the full “Nessus Customer Update, April 2025” webinar on-demand to learn what’s new and coming soon in Nessus, and to get more details about identifying attack paths using port scanning and service discovery.
4 - Report: Fewer U.K. businesses hit by cyber attacks, but challenges persist
The percentage of U.K. businesses that suffered a cyber breach or attack dropped to 43% last year from 50% in 2023, but the cybersecurity challenges they face remain daunting.
That’s the main takeaway from the U.K. government’s “Cyber Security Breaches Survey 2025,” which in addition to businesses also surveyed charities and educational institutions.
“The 2025 survey emphasises that while progress is being made in certain areas, evolving threats like phishing and ransomware, and disparities between different types of organisations highlight persistent vulnerabilities,” reads the report, which was published this week.

Key findings from the report include:
- Phishing remains by far the most prevalent type of breach or attack, suffered by 85% of businesses.
- Among small businesses, the adoption of cyber hygiene practices increased, including cyber risk assessments; business continuity plans; and formal cyber policies.
- Basic cyber controls are in place in the majority of businesses, including malware protection; password policies; network firewalls; and resticted admin rights.
- Adoption of advanced controls remains low, including multi-factor authentication (40%); VPNs for remote access (31%); and user monitoring (30%).
- Management of supply chain risks is extremely low, with only 14% of businesses assessing risks from direct suppliers and only 7% doing so for their entire supply chain.
For more information about phishing protection:
- “How To Recognize and Avoid Phishing Scams” (U.S. Federal Trade Commission)
- “How to defend your organisation from email phishing attacks” (NCSC)
- “How AI is making phishing attacks more dangerous” (TechTarget)
- “Teach Employees to Avoid Phishing” (U.S. Cybersecurity and Infrastructure Security Agency)
- “Top 10 tips for employees to prevent phishing attacks” (TechTarget)
5 - CIS updates Benchmarks for Apple, Microsoft, Cisco products
Apple macOS, Microsoft Windows 11 Enterprise and Cisco NX-OS are some of the products whose Center for Internet Security (CIS) Benchmarks got an update in March.
Specifically, these secure-configuration recommendations were updated:
- CIS Amazon Web Services Foundations Benchmark v5.0.0
- CIS Apple macOS 12.0 Monterey Cloud-tailored Benchmark v1.1.0
- CIS Apple macOS 15.0 Sequoia Cloud-tailored Benchmark v1.1.0
- CIS Cisco NX-OS Benchmark v1.2.0
- CIS Kubernetes Benchmark v1.11.0
- CIS Microsoft Azure Foundations Benchmark v4.0.0
- CIS Microsoft Windows 11 Enterprise Benchmark v4.0.0
- CIS Ubuntu Linux 20.04 LTS Benchmark v3.0.0
- CIS VMware ESXi 8.0 Benchmark v1.2.0

In addition, CIS released these two brand new Benchmarks:
The CIS Benchmarks are secure-configuration guidelines designed to help organizations harden products against cyber attacks. CIS offers more than 100 Benchmarks for 25-plus vendor product families in categories including:
- cloud platforms
- databases
- desktop and server software
- mobile devices
- operating systems
To get more details, read the CIS blog “CIS Benchmarks April 2025 Update.”
For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
- Cloud
- Exposure Management
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Malware
- Nessus


