Cybersecurity Snapshot: Tips for cloud configs, MSP vetting, CISO board presentations

Get the latest on Microsoft 365 security configurations; effective CISO board presentations; rating MSPs’ cybersecurity preparedness; and hospitals’ Daixin cyberthreat.
Dive into 6 things that are top of mind for the week ending Oct. 28.
1 - CISA issues config baselines for Microsoft cloud apps
Properly configuring cloud services is critical for reducing cyber risk, so guidance in this area is always welcome. Recently, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a set of recommended configuration baselines for the Microsoft 365 product suite.

Here’s a small sample of the recommendations, which are part of CISA’s Secure Cloud Business Applications (SCuBA) project:
- Microsoft Teams
- Don’t enable anonymous users to start meetings
- Restrict unmanaged user access
- Disable Teams email integration
- Microsoft Exchange Online
- Disable automatic forwarding of emails to external domains
- Enable Sender Policy Framework (SPF)
- Enable DomainKeys Identified Mail (DKIM)
- Microsoft Azure Active Directory
- Block legacy authentication protocols
- Block users and sign-ins flagged as high risk
- Require phishing-resistant MFA for all users
- Microsoft SharePoint Online
- Set default sharing for file/folder links to “specific people”
- Don’t allow users to run custom scripts
- Set an expiration time for guest access to a Sharepoint site or OneDrive
The other four guides are for Microsoft Power Platform, Microsoft Power BI, Microsoft OneDrive for Business and Microsoft Defender for Office 365.
CISA plans to release a similar set of recommendations for Google Workspace (GWS) in the coming months.
The agency gave each Microsoft 365 guide a 0.1 version number and called them “drafts.” CISA wants users to pilot the configuration recommendations and provide feedback on them.
While the guides are aimed primarily at civilian executive branch agencies of the U.S. federal government, CISA encourages all organizations to read, pilot and react to them.
For more information, read the CISA announcement.
You can also check out Microsoft365DSC, an open source tool for managing Microsoft 365 tenant configurations. The initiative is led by Microsoft engineers.
More resources on cloud configuration best practices:
- “Hardening and monitoring cloud configuration” (SC Magazine)
- “Cloud Security Roundtable: Scaling Cloud Adoption without Sacrificing Security Standards” (Tenable webinar)
- “Security Guidance for Critical Areas of Focus in Cloud Computing” (Cloud Security Alliance)
- “How to Choose a Modern CSPM Tool to Reduce Your Cloud Infrastructure Risk” (Tenable blog)
- “The Beginner’s Guide to Secure Cloud Configurations” (Center for Internet Security)
2 - Do your security tools play well together? Kinda, sorta
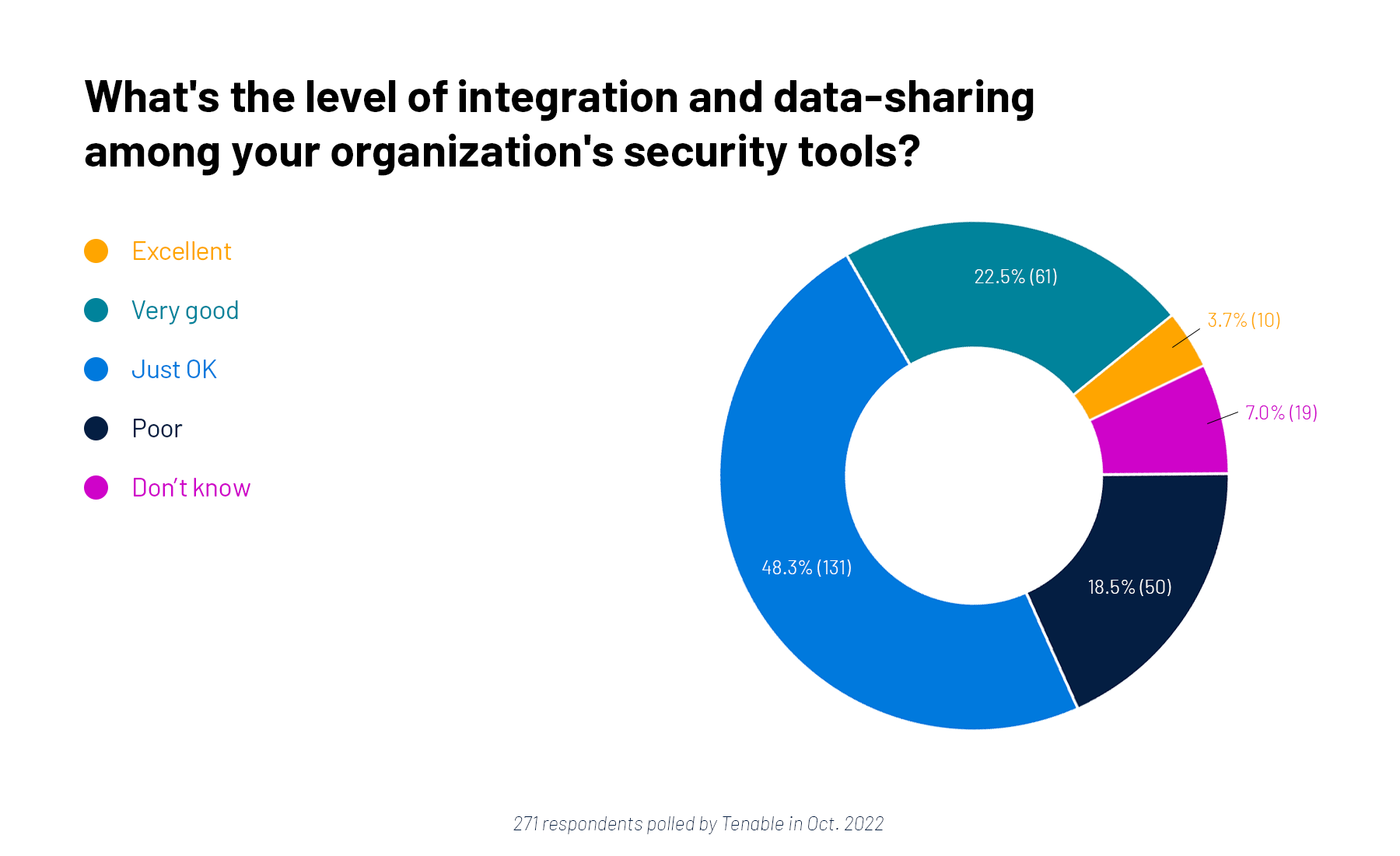
It’s a perennial item on every security leader’s wish list: More interoperability and data uniformity among cybersecurity products. At a recent Tenable webinar, we polled attendees on this issue, and as you can see from the graph below, just a small minority are very satisfied on this front.
Check out these Tenable resources for more information about this topic:
- “The shift to integrated cybersecurity platforms: a growing trend among CISOs”
- “Consolidate and Unify to Accelerate Your Security Efforts”
- “3 Real-World Challenges Facing Cybersecurity Organizations”
- “Exposure Management: Reducing Risk in the Modern Attack Surface”
- “Full IT Visibility Requires Business Risk Context”
3 - CISOs share ideas for successful board presentations
Briefing the board is one thing a CISO wants to nail every time – but there’s no standard template for structuring these presentations. Enter the Executive Security Action Forum, an RSA Conference community of security executives from Fortune 1000 companies, which just released a report to help CISOs improve their board presentations.
Titled “What Top CISOs Include in Updates to the Board,” the report is based on anonymized board presentations from – and subsequent interviews with – eight unidentified CISOs representing seven different industries. The report’s goal is to offer CISOs “food for thought” and ideas, and doesn’t aim to be a playbook nor provide formal best practices on this topic.
Here are key takeaways:
- The interviewed CISOs all touch on these five areas when briefing their respective boards:
- Risk landscape changes
- Highest-priority risk factors
- Security maturity score
- Updates on security initiatives
- Security incident highlights
- They typically update the full board once a year, and a board committee quarterly, and some topics may be covered every quarter, while others only annually.
- There should be continuity and consistency over time so that the meetings feel like an ongoing conversation.
- Risk management is typically addressed from multiple angles to show that cyber risks are being:
- Monitored, by including information on elements like new attack vectors, threat actors, vulnerabilities and regulations
- Analyzed and prioritized, by including lists of top risks, or of risks by market or product areas
- Mitigated and reduced, by including information on trend metrics, security controls, plan roadmaps, gaps and costs
- Included in overall enterprise risk management, by showing how cyber risks compare with the company’s operational and other risks
The 34-page report is packed with examples of how to structure board presentations and contains multiple chart and graph samples, such as this one below.
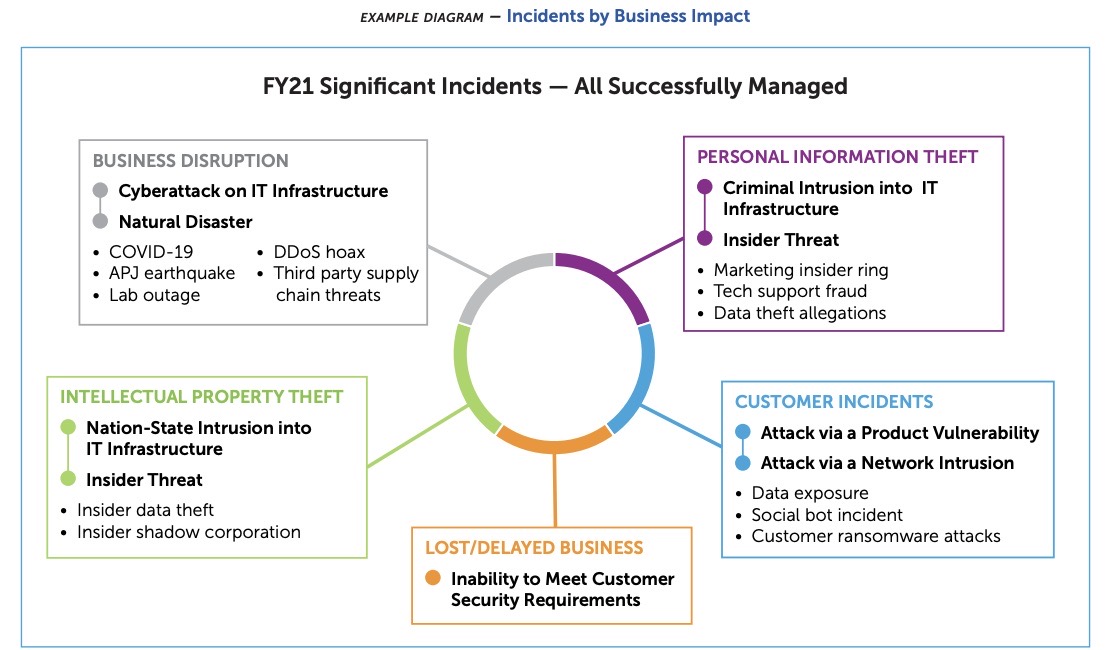 (Source: RSA Conference's “What Top CISOs Include in Updates to the Board" report, October 2022)
(Source: RSA Conference's “What Top CISOs Include in Updates to the Board" report, October 2022)
For more information, you can request a copy of the full report or watch this on-demand webinar.
To delve deeper into this topic, check out these articles and videos:
- “CxOs Need Help Educating Their Boards” (Cloud Security Alliance)
- “7 mistakes CISOs make when presenting to the board” (CSO Magazine)
- “3 Tips for a Successful CISO Board Presentation” (Fair Institute)
- “Deliver Your Board Message with Context and Confidence” (SC Magazine)
- “Highlights from CISO Series Video Chat: ‘Hacking the Boardroom Meeting’” (CISO Series video)
- “How to be an effective CISO by being an effective communicator” (Dr. Eric Cole)
4 - Cybersecurity questions to vet IT service providers
How can business leaders rate the cybersecurity preparedness and know-how of prospective IT service providers and managed service providers (MSPs)? Improperly vetting these providers’ cybersecurity capabilities and processes can put your organization's data and systems at risk.
A new guide from the non-profit Computing Technology Industry Association (CompTIA) aims to help CEOs and business leaders ask all the right questions during the process of selecting IT service providers and MSPs.

The 18-page document, created by CompTIA’s Cybersecurity Advisory Council and titled “A CEO’s Guide to Choosing an IT Service Provider,” consists of detailed questionnaires covering areas including:
- Frameworks and compliance
- Policies
- Privilege account management, including role-based access and authentication management
- Systems management
- Incident response
- Patch and vulnerability management
Of course, organizations can also use the document to evaluate IT service providers and MSPs they’re already working with.
For more information, you can read a blog about the guide or download the actual document.
To learn more about this topic:
- “Risk Considerations for Managed Service Provider Customers” (CISA)
- “How to find a security-savvy MSP” (CSO Magazine)
- “Why Is Third Party Risk Management Important?” (CIO Insight)
- “Third Party Cyber Risk is Your Cyber Risk” (American Hospital Association)
5 - Government warns healthcare orgs about new cybercrime group
Healthcare and public health organizations are being targeted with ransomware and data extortion attacks by the Daixin Team cybercrime group, according to the U.S. government.
In a joint advisory, CISA, the Federal Bureau of Investigation and the Department of Health and Human Services detailed the group’s tactics, techniques and procedures; its indicators of compromise; and recommended mitigations.
The group’s modus operandi is to first gain initial access via virtual private network (VPN) servers. In one case, it exploited an unpatched vulnerability. In another, it used credentials stolen via phishing to log into a VPN server that wasn’t protected with multifactor authentication (MFA.)
Here’s a small sampling of the advisory’s many common-sense recommendations:
- Don’t delay the installation of updates for operating systems, software and firmware, and prioritize VPN servers, remote access software, virtual machine software and known exploited vulnerabilities.
- Enable “phishing-resistant” MFA for as many services as possible, in particular for VPNs and privileged accounts.
- Secure and monitor Remote Desktop Protocol (RDP.)
- Turn off Secure Shell and other network device management interfaces.
- Keep data backups offline.
- Restrict Server Message Block Protocol within the network because it’s used to propagate malware.
For more information, read the advisory, and coverage and analysis from Infosecurity Magazine, HealthIT Security, MeriTalk, TechTarget and The Register.
6 - And here’s the CIS top 10 malware list for September
The Center for Internet Security (CIS) has released the list of the most prevalent strains of malware making the rounds last month, with Arechclient2, RedLine, and Ursnif making a comeback.
Here’s the full list:
- SocGholish, a remote access trojan (RAT) and a banking trojan that uses fake Flash updates
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI) and EternalBlue
- ZeuS, a modular banking trojan that uses keystroke logging
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- TeamSpy, spyware that uses remote access tool TeamViewer and malware to steal information
- LingyunNet, riskware that uses victims’ system resources
- Ursnif (aka Gozi and Dreambot), a banking trojan
- Arechclient2 (aka SectopRAT), is a .NET RAT whose capabilities include multiple stealth functions
- RedLine, an infostealer that can be bought on cybercriminal forums
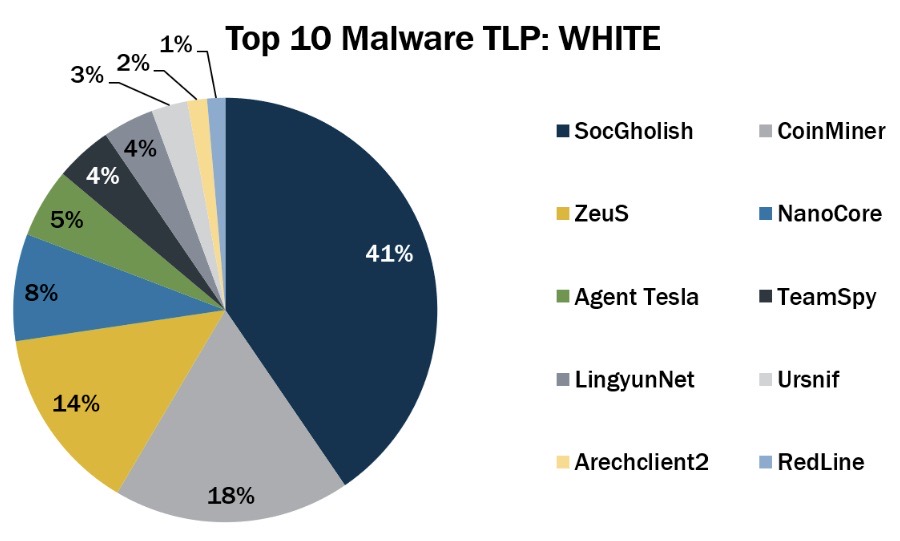
(Source: Center for Internet Security, October 2022)
To get all the details, context and indicators of compromise for each malware, read the CIS report.
- Center for Internet Security (CIS)
- Cloud
- Configuration auditing
- Cybersecurity Snapshot
- Exposure Management
- Government
- Healthcare
- Malware
