Cybersecurity Snapshot: Verizon DBIR Finds Attackers Feast on Vulnerability Exploits for Initial Access, While MITRE ATT&CK Adds Mobile, Cloud, ESXi Threat Intel

Check out highlights from this year’s Verizon DBIR, including a surge in zero-day exploits targeting edge devices and VPNs. Plus, find out what’s new in the latest version of MITRE ATT&CK. Also, see what Tenable webinar attendees said about AI security. And get the latest on ransomware preparedness for OT systems and on the FBI’s 2024 cyber crime report.
Dive into five things that are top of mind for the week ending April 25.
1 - Verizon DBIR: To break in, hackers favor credentials and vulnerabilities
As your organization fine-tunes its cyber defenses, here’s an unsurprising yet highly relevant fact: The two most common avenues for cyberattackers to hack into victims’ networks are compromised credentials and exploited vulnerabilities.
That’s according to Verizon’s “2025 Data Breach Investigations Report” (DBIR), which was published this week. The report is based on an analysis of 22,000 real-world security incidents — including about 12,200 confirmed breaches — that occurred globally between Nov. 1, 2023 and to Oct. 31, 2024.
"The DBIR's findings underscore the importance of a multi-layered defense strategy," Chris Novak, VP of Global Cybersecurity Solutions at Verizon Business, said in a statement.
"Businesses need to invest in robust security measures, including strong password policies, timely patching of vulnerabilities, and comprehensive security awareness training for employees," he added.
Cyber attackers used credential abuse as their initial access vector in 22% of breaches. Meanwhile, vulnerability exploitation came in second at 20%, a spike of 34% compared with the prior period. Phishing (16%) ranked third.

What drove the sharp rise in vulnerability exploits? The raft of zero-day bugs that attackers have exploited in network edge devices and virtual private networks. These accounted for 22% of vulnerability exploits — a proportion that rocketed from just 3% during the prior period. Organizations fully remediated only 54% of these edge vulnerabilities. The median time-to-remediate was 32 days.
Tenable Research was a key contributor to this section of the 2025 DBIR by providing enriched data on the most exploited vulnerabilities.
“We analyzed over 160 million data points and zeroed-in on the 17 edge device CVEs featured in the DBIR to understand their average remediation times,” Tenable Senior Staff Research Engineer Scott Caveza wrote in a blog that details Tenable Research’s contribution.
Other key findings in the 2025 DBIR include:
- Ransomware attacks rose 37% and were present in 44% of all breaches. However, median ransom payments fell to $115,000 from $150,000, as 64% of victims refused to pay.
- Third-party involvement in breaches surged to 30%, up from 15%, which highlights the growing cyber risks organizations face from their supply chain partners, such as vendors and contractors.
- 15% of employees routinely access generative AI systems via their work devices — at least once every two weeks. But most (72%) do so using personal accounts, suggesting they’re circumventing corporate policies that prohibit using generative AI tools for work.
- The percentage of malicious emails crafted using AI has risen from about 5% to about 10% in the past two years.
To get more details, check out: Tenable’s blog “Verizon 2025 DBIR: Tenable Research Collaboration Shines a Spotlight on CVE Remediation Trends” and these Verizon resources:
- “2025 Data Breach Investigations Report” home page
- The report’s announcement
- A complementary infographic
2 - MITRE ATT&CK update beefs up cloud, mobile security sections
Information about protecting VMWare’s ESXi hypervisor. Expanded guidance on mobile and cloud security. More intel on nation-state actors and cyber crime operations.
That’s just some of what’s new in the latest version of the MITRE ATT&CK framework, the popular knowledge base of cyberattack tactics, techniques and procedures designed to help security teams develop threat models and methodologies.
Announced this week, version 17 of MITRE ATT&CK “aims to help defenders stay aligned with where adversaries are headed by looking at where they’ve recently been,” MITRE ATT&CK officials wrote in a blog.
“This release aims to inform defensive efforts by focusing on the platforms adversaries are exploiting, the techniques they’re adapting, and the environments they’re targeting,” they added.

Here’s some of what’s new:
- In response to a spike in attacks against virtualization systems, a new platform has been added devoted to securing VMWare’s ESXi hypervisor, which hackers have targeted recently. Specifically, the new MITRE ATT&CK version adapts 34 existing techniques to ESXi and adds four new techniques for it.
There’s broader guidance on protecting mobile devices and securing cloud environments.
For example, on the cloud security front, there’s new information about how OAuth app integrations are abused in software-as-a-service (SaaS) platforms to bypass multi-factor authentication (MFA) and swipe data.
For mobile security, the new version documents recent techniques and tools that attackers are using, among other things, to make their attacks stealthier. There’s also new guidance to help developers build safer software for mobile devices.
- Regarding nation-state attackers, the new version adds information on various groups, including Salt Typhoon, RedEcho, Velvet Ant and Sea Turtle.
To get more information, check out:
- The blog “ATT&CK v17: New Platform (ESXi), Collection Optimization, & More Countermeasures”
- The MITRE ATT&CK v17 release notes
- The MITRE ATT&CK framework
- The MITRE ATT&CK FAQ
3 - Tenable polls webinar attendees on AI security
During our recent webinar “2025 Cloud AI Risk Report: Helping You Build More Secure AI Models in the Cloud,” we polled attendees on AI security, including which risks they’re most concerned about. Find out what they said.
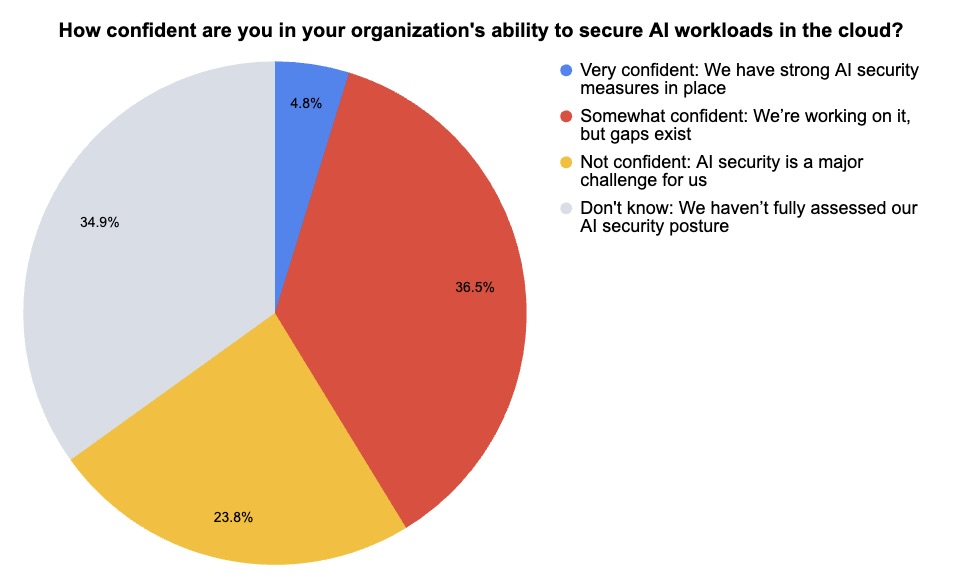
(63 webinar attendees polled by Tenable, April 2025)
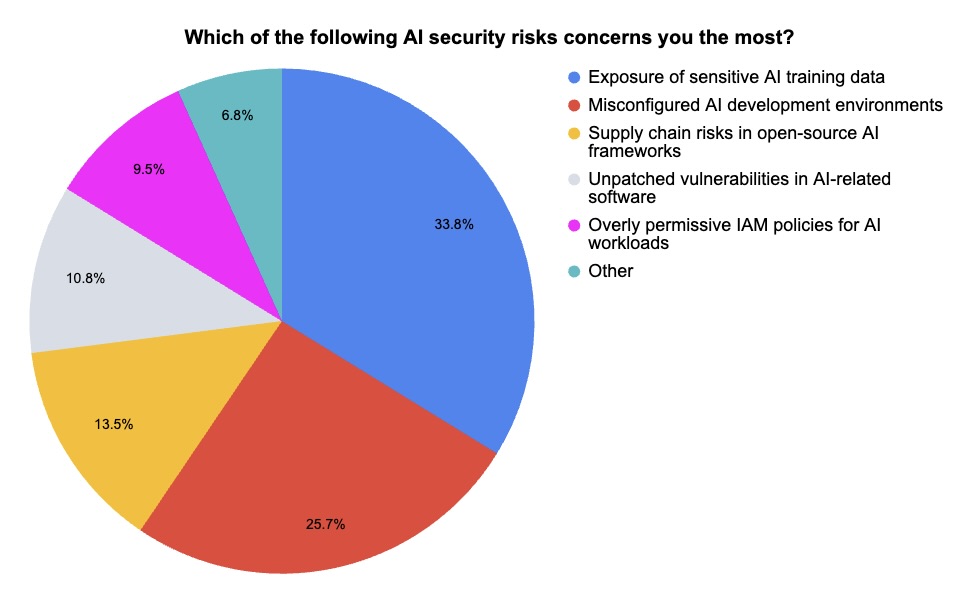
(74 webinar attendees polled by Tenable, April 2025)
Want details on the findings of our “Tenable Cloud AI Risk Report 2025” and on mitigation and security best practices for protecting your AI workloads and applications? Watch the webinar on-demand.
4 - SANS publishes ransomware response framework for ICS/OT environs
How can critical infrastructure organizations prepare an effective response plan for ransomware attacks against their industrial control systems and operational technology (OT) systems?
SANS Institute tackled that question and the result is a white paper published this week titled “A Simple Framework for OT Ransomware Preparation.”
With the document, SANS aims to outline an actionable, hands-on approach for critical infrastructure organizations seeking to build or fine-tune ransomware response playbooks.
“The key message? Preparation matters. And in the OT world, a lack of preparation can have real-world consequences,” reads a SANS blog titled “Building a Better OT Ransomware Response Plan: A Simple Framework for ICS Environments.”
At a high level, SANS recommendations for critical infrastructure organizations with OT / ICS environments include:
- Before drafting the playbook, you need to collect foundational data about your environment, such as its architecture, asset inventory, key staff and security controls.
- It’s also key to proactively foster collaboration between the IT, OT and cybersecurity teams.
- The ransomware-preparedness playbook should cover five key areas:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
“By focusing on the unique challenges of OT networks, such as their architectural immaturity and the criticality of safe operations, the framework provides actionable guidance to enhance incident response capabilities,” the white paper reads.
For more information about protecting OT systems from ransomware and other cyber attacks, check out these Tenable resources:
- “Managing OT and IT Risk: What Cybersecurity Leaders Need to Know” (blog)
- “Operational Technology (OT) Security: How to Reduce Cyber Risk When IT and OT Converge” (resource page)
- “Mind the Gap: A Roadmap to IT/OT Alignment” (white paper)
- “How to Unlock Advanced IoT Visibility for Cyber-Physical Systems” (blog)
- “Unlock advanced IoT visibility to better secure your OT environment” (on-demand webinar)
Tenable.ot Security Spotlight - Episode 1: The Ransomware Ecosystem
Tenable.ot Security Spotlight - Episode 2: The Business Risk From a Ransomware Attack on OT Systems
Tenable.ot Security Spotlight - Episode 3: Ransomware in OT Systems
5 - FBI: U.S. cyber crime losses hit “staggering” levels in 2024
Cyber crime shows no sign of abating in the U.S.
Americans lost $16.6 billion due to internet crime last year, up 33% compared with 2023 and a new record, the U.S. Federal Bureau of Investigation said in its “Internet Crime Report 2024.” The data comes from the FBI’s IC3 division, which fields internet crime complaints.
Cyber fraud schemes account for most of the monetary losses — $13.7 billion — according to the report, released this week. Investment scams ranked first, accounting for about $6.5 billion, followed by business email compromise (BEC) at around $3 billion and tech support scams at almost $2 billion.
Overall, cyber crime victims filed almost 860,000 complaints. Of those, about 256,000 included a loss of money, for an average loss per complaint of about $19,300. Although the overwhelming majority of complaints came from the U.S., the report includes complaints from 200-plus countries.
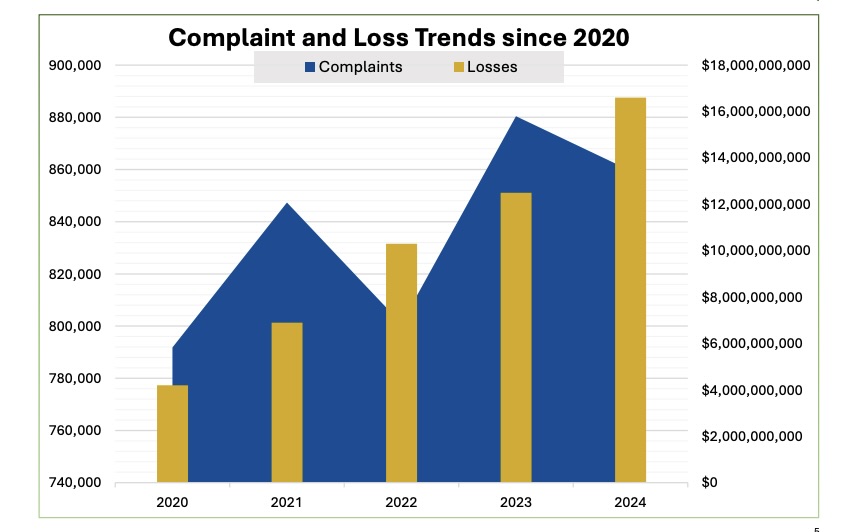
(Source: FBI’s “Internet Crime Report 2024,” May 2025)
The rest of the losses came from cyber threats: $1.57 billion. Critical infrastructure organizations filed more than 4,800 cyber threat complaints, most of them for ransomware attacks — up 9% — and data breaches. Akira, LockBit, RansomHub, Fog and Play were the top ransomware variants impacting the critical infrastructure sector.
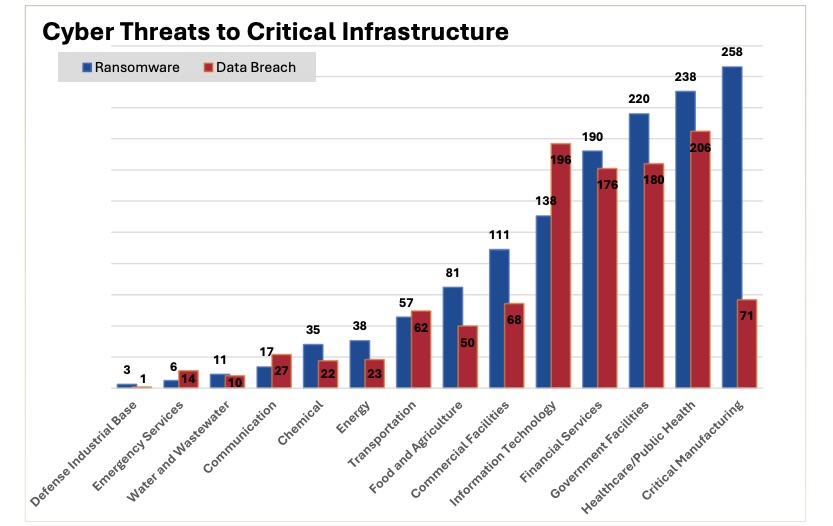
(Source: FBI’s “Internet Crime Report 2024,” May 2025)
For more information about cyber threats to critical infrastructure:
- “Critical Infrastructure Security and Resilience” (CISA)
- “Volt Typhoon: U.S. Critical Infrastructure Targeted by State-Sponsored Actors” (Tenable)
- “Critical infrastructure at state, local levels at heightened risk of cyberattacks” (Cybersecurity Dive)
- “Why using IT cybersecurity to protect OT puts industrial organizations at risk” (World Economic Forum)
- “Cybersecurity of Critical Infrastructure with ICS/SCADA Systems” (IEEE)
- AI
- Cloud
- Industrial Control Systems Monitoring
- IT/OT
- Malware & Malicious Behavior
- Mobile Device Security
- Risk-based Vulnerability Management
- Security Frameworks
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- Incident Response
- Malware
- OT Security



