Have You Been Compromised? Let’s Go Hunting!

Protecting your network against attackers is only part of the equation. You have probably seen the statistics. Research tells us that attackers spend an average of 200 days inside a network before being discovered. Prevention isn’t enough. Even with expert staff and sophisticated security solutions in place, can you confidently answer the question, “Am I compromised?” You need a way to proactively hunt for attackers who may have eluded your protective defenses.
Tenable is best recognized for our protective security solutions; those focused on eliminating vulnerabilities, misconfigurations, and malware. But SecurityCenter Continuous View™ (SecurityCenter CV™) is also a great solution for threat hunting, as announced at RSA this week. Rather than being consumed reacting to alerts, you can use SecurityCenter CV to efficiently take action; to reduce your exposure and risk by proactively hunting for compromises and addressing them before they become breaches.
Use SecurityCenter CV to reduce your exposure and risk by proactively hunting for compromises and addressing them before they become breaches
SecurityCenter CV is the only solution that collects data from five sensors: active scanning, passive network monitoring, intelligent connectors to third-party management and security products, agents and host data. These technologies combine to deliver deep insight into network and system state, and continuous visibility of network and user activity.
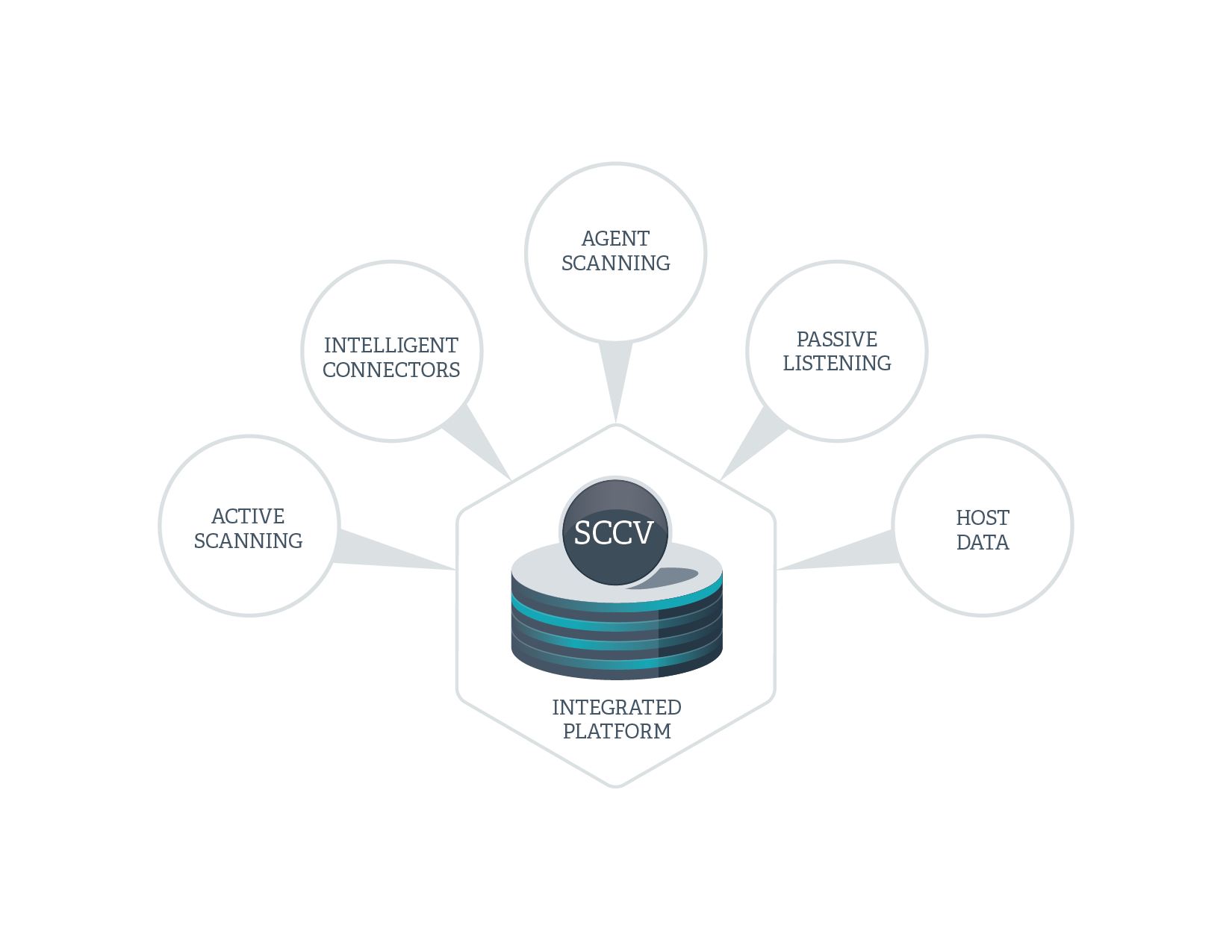
Data collected from across your environment is enhanced with indicators of compromise from leading commercial threat intelligence vendors to help you identify threats in real-time – without additional licensing and configuration costs.
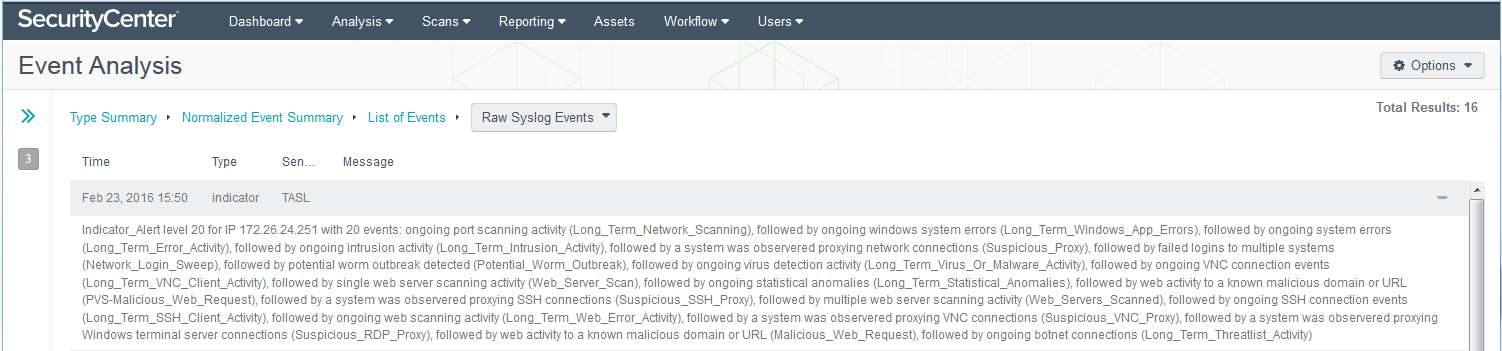
SecurityCenter CV baselines “normal” behavior for your network and then identifies and measures divergence from normal activity patterns across all types of collected event data. It also correlates chains of potentially suspicious events to uncover complex or advanced threat conditions. For example, the screenshot below shows many suspicious activities, including long-term port scanning, followed by Windows system errors, followed by long-term intrusion activity.
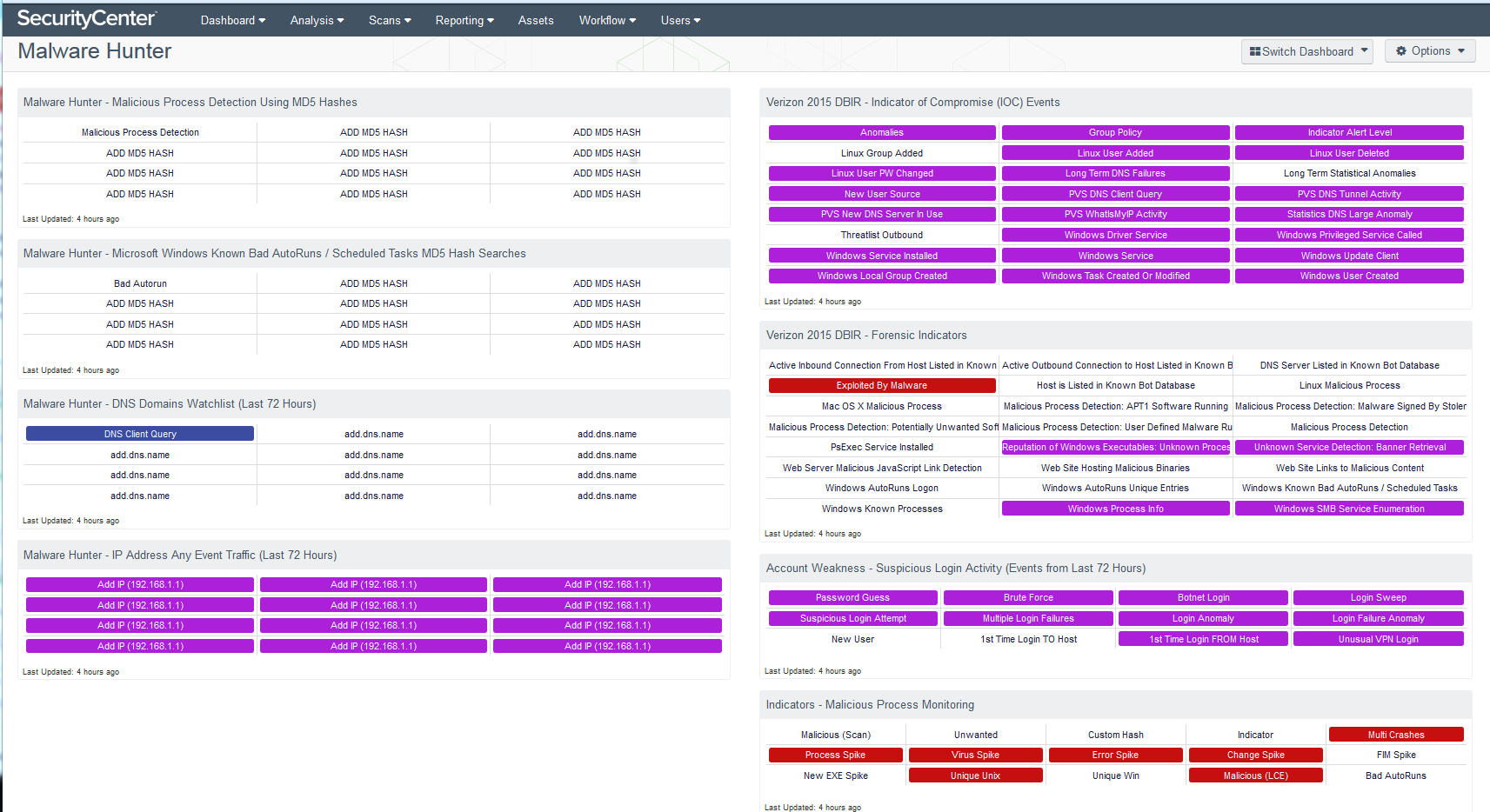
A challenge faced by many organizations is that they barely have enough staff to ensure that preventive security measures are in place. Often, dedicating staff resources to detective measures, such as threat hunting, is very difficult. There is no silver bullet. Threat hunting takes time. However, SecurityCenter CV includes interactive dashboards that highlight the most suspicious indicators and allow you to prioritize your actions and then quickly drill in to investigate. For example, the red items shown in the Malware Hunter dashboard below indicate high priority items that need immediate investigation.
Another challenge faced by organizations getting started with threat hunting is that their disparate tools require significant care and feeding. Tenable addresses this challenge head on. Our security experts are essentially an extension of your security staff. They continuously develop integrations, normalization rules, and correlation rules to gather and analyze data. Additionally, they maintain an expanding library of report, dashboard, and Assurance Report Card templates that you can use out-of-the-box or tailor to display security information in actionable formats. The result: you can focus your valuable resources on action to reduce exposure and risk.
Please check out our threat hunting resources to see how Tenable can help you learn if you have ever been compromised.
- Announcements
- SecurityCenter
- Threat hunting

