How to Unlock Advanced IoT Visibility for Cyber-Physical Systems

As the number of IoT devices deployed globally continues to rise, cyber-physical systems and business operations are exposed to greater risk. Improving asset visibility, monitoring and risk management are critical steps to preventing breaches.
As businesses continue to embrace digital transformation, the proliferation of internet of things (IoT) devices across industries has resulted in unprecedented operational benefits, from smart lighting and heating, ventilation and air conditioning (HVAC) controls to building management and smart grid systems. However, these innovations and the sheer number of IoT devices being deployed every day come with a critical challenge: securing an ever-expanding attack surface, especially for traditional operational technology (OT) and critical cyber-physical systems (CPS) that are exposed to new vulnerabilities and threat actors.
Not only do IoT devices introduce more entry points for potential attackers, but many of these devices are often overlooked by traditional security efforts. IoT systems may share characteristics with both IT and OT, but they require a dedicated strategy to ensure they don't become blind spots in your security posture.
The importance of unified visibility to secure an internet of sensors
With IoT devices embedded across operational and corporate environments, today’s security leaders struggle to track what’s connected to their networks. Securing IoT assets is especially difficult due to the diversity of these devices — whether it’s the function they serve, architecture types or the different ways they can be managed.
Additionally, many of today's commonly deployed IoT devices are "insecure by design," carrying outdated software and vulnerable configurations. For example, IoT sensors in building facilities such as smart lighting, HVAC systems and security cameras aren’t always managed by IT security teams — they’re often under the purview of facilities management and operators or external vendors.
Without a unified approach, many organizations struggle to gain visibility into these devices and their associated asset relationships and vulnerabilities. This lack of centralized management leads to a fragmented view of the attack surface, creating blind spots that threat actors can exploit.
Common pitfalls in security for IoT devices
There are five common challenges to securing IoT devices:
Limited visibility: Many organizations lack an accurate asset inventory as well as an understanding of the IoT devices on their networks, making it difficult to assess risk.
Diverse management: IoT devices often fall under the management of non-IT teams, such as facilities or external contractors, further complicating efforts to create a unified security approach that covers everything from IT infrastructure to cyber-physical systems.
Fragmented architecture: IoT ecosystems can be loosely or tightly coupled, with different network segments for different functions, making monitoring and securing them more complex. Traditional approaches to scanning IoT devices at the asset level alone fall short of providing the necessary context and insight into relationships between assets and attack paths.
Passive communication: Some IoT devices only transmit data when needed, which means traditional passive monitoring tools may miss critical vulnerabilities until it’s too late. As a result, many organizations are left vulnerable, with security leaders wondering how to effectively manage the security of these devices.
Lack of standardization: There are no universal security compliance standards for IoT. This has led to inconsistent levels of protection for these devices. This also makes it harder for security teams to respond to increasing demands for reporting for audit, compliance and internal governance.
What security leaders can do to improve IoT security
To address the challenges outlined above, security leaders must focus on several key areas:
Comprehensive visibility: Knowing which IoT devices are connected to your network is the first step to understanding how a compromised IoT device could impact critical operations. This requires adopting a unified OT/IT security solution with the ability to automatically discover and categorize IoT assets, map attack paths and prioritize how teams respond to the most critical vulnerabilities. These capabilities are important for all types of IoT architectures, whether dealing with standalone systems, mesh networks or devices embedded as part of a larger industrial control system. Without this visibility, organizations risk leaving critical vulnerabilities undetected.
Unified risk management: Once visibility is established, security leaders need a way to assess the business-critical risks posed by each device. By relying on modern OT/IT security tools and technologies that normalize data and manage exposure across all types of devices — whether IoT, OT or IT — security teams are equipped with a comprehensive, unified risk model. Not all vulnerabilities are created equal, so prioritizing the devices that present the greatest threat to operations or safety should be a focus. With this holistic view of risk, organizations can make informed decisions on where to allocate resources for the greatest security impact.
Collaboration between teams: With IoT devices often managed by non-IT teams, security teams must establish a collaborative relationship with facilities, operations and third-party vendors. This ensures a cohesive and effective approach to securing OT and IT environments from vulnerabilities created by connected IoT devices.
Proactive monitoring: Relying solely on passive monitoring can leave gaps in coverage when trying to detect and monitor IoT devices. Organizations should instead rely on hybrid discovery capabilities to actively query IoT management applications or use remote APIs to gather data passively. This application-based approach identifies every connected device and continuously monitors for new ones, helping security teams bridge the visibility gap and get a complete picture of risk.
Compliance and reporting: Maintaining compliance with evolving security standards is critical, especially for security leaders responsible for securing cyber-physical systems that include a diverse mix of interconnected IT, OT and IoT assets. As regulations become more complex and audits demand greater transparency, security leaders face increasing pressure to meet compliance requirements without disrupting operations. By leveraging modern solutions that offer detailed executive reporting and actionable insights aligned with the latest security frameworks — including the EU's Network and Information Security Directive 2 (NIS2), the U.K.'s Cyber Assessment Framework (CAF) and Saudi Arabia's Operational Technology Cybersecurity Controls (OTCC) — organizations can streamline compliance and reporting processes, efficiently communicate standings to executives and other non-technical stakeholders, and automate manual tasks. This proactive approach helps transform compliance into a competitive advantage.
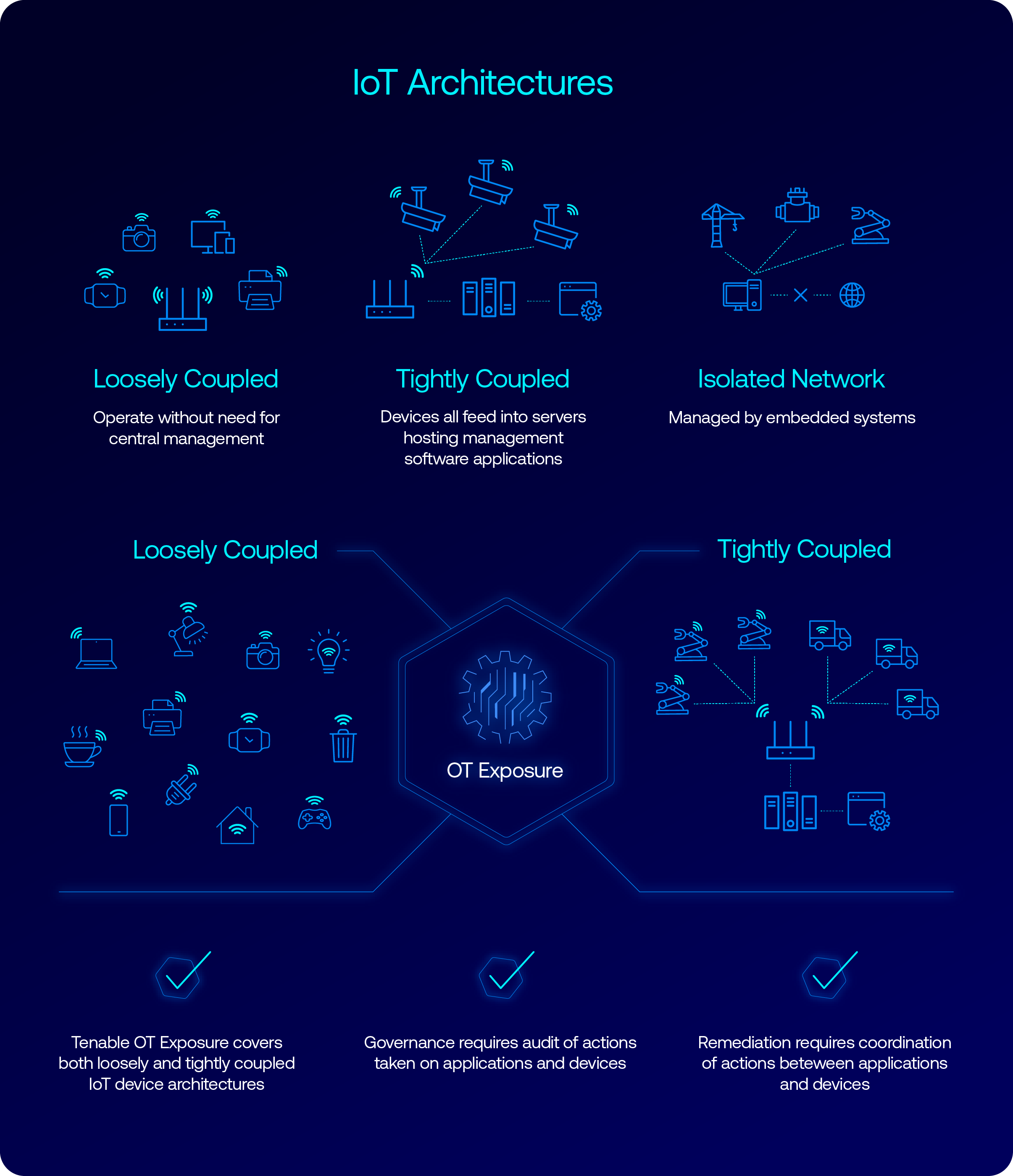
Image source: Tenable, October 2024
So, how to get started? Security leaders can begin by asking:
- Do we have full visibility into the IoT devices on our network?
- Are we prioritizing the vulnerabilities that could cause the most damage?
- Do we have the right tools in place to monitor all types of IoT architectures?
- Are we collaborating effectively across internal silos and vendors to secure all asset types?
These questions can guide the development of a more robust cybersecurity strategy. However, understanding what’s connected to your network is just the start — having the right tools to assess and mitigate risks is what will truly secure your IoT landscape.
A step forward: Advanced IoT visibility
Effectively managing the security of your IT, OT and IoT assets requires a tailored approach. Each asset type comes with its own challenges — ranging from legacy OT systems to the rapidly expanding deployment of IoT devices and sensors. A one-size-fits-all approach simply will not provide the level of visibility and control needed to safeguard such a diverse environment.
For organizations looking to tackle the challenges of IoT security, advanced solutions are available to help you automate IoT asset discovery, assess risk, and manage vulnerabilities in a unified way. Watch our latest webinar to learn more about how our advanced IoT visibility capabilities in Tenable OT Security, such as contextual IoT asset discovery and relationship mapping, can help accelerate your security strategy. This webinar explores the latest approaches to securing IoT environments and how Tenable solutions help security teams across industries manage risk and compliance.
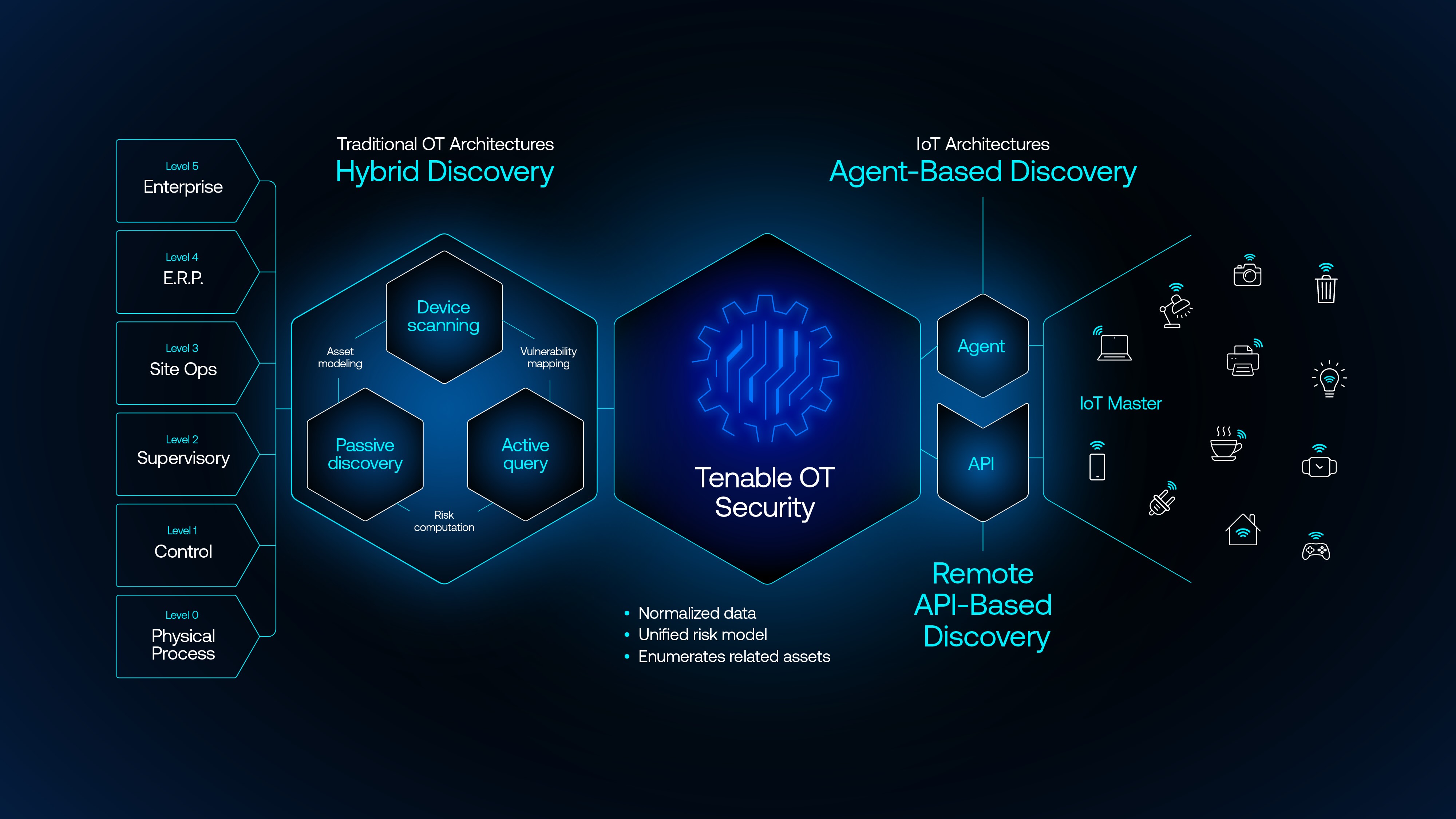
Image Source: Tenable, October 2024
In a hyper-connected world, securing IoT isn’t just about protecting devices — it’s about safeguarding the entire connected enterprise. By focusing on the latest best practices for managing exposures — asset visibility, risk management and proactive monitoring — security leaders can stay ahead of threats and build a more resilient cybersecurity strategy.
#CPS #OTSecurity #ICSSecurity #SmartBuildings #DigitalTransformation #IoT #RiskManagement
Learn moreJoin us for an expert discussion on how to unlock advanced IoT visibility to secure connected OT/IT environments Discover how the latest release of Tenable OT Security redefines discovery and classification of IoT device relationships Find actionable strategies for securing the modern attack surface in our security leader's guide to managing OT and IT risk Explore how Tenable helps assess NIS2 risk‑based security measures from three key perspectives across the enterprise Find out how Splunk and Tenable together deliver more robust OT/IT security Learn how to get started with Tenable OT Security |
- Attack Surface Management
- Internet of Things
- OT Security
- Vulnerability Management



