Tenable Internship Takeaways: Understanding Different Port Scanning Techniques

As a summer intern for the research and development department at Tenable, I was surprised when my manager gave me a relatively straightforward first task: find every machine in the lab. I knew that some form of port scan was needed. Maybe I could start with a ping sweep of some IP range, or maybe something more comprehensive. But my manager also added some nuance to the project. I had to put myself in the shoes of a Tenable customer, and my objective was to present a plan to discover machines and to identify the Cyber Exposure risk on the lab network using Tenable.io. The first step was to define the network subnets, and then I had to scan the networks for vulnerabilities.
TCP Handshaking
TCP and SYN are two methods that stem from the concept of TCP handshaking. When two computers communicate over TCP/IP, flags are set on the TCP layer of a packet. A TCP flag is a series of bits that indicates how a packet should be handled by the server. Some important flags to remember are SYN (synchronize), ACK (acknowledge), RST (reset), FIN (no more data to send). In TCP handshaking, one computer sends a packet with the SYN flag, initiating the connection to the server. The server responds with a packet with SYN and ACK flags set, as if to acknowledge the request from the first computer to connect. If the connection is refused due to a closed port, the server responds with an RST packet. In response to the SYN/ACK packet, the first computer acknowledges with an ACK packet, completing the TCP connection. When the conversation is over, a FIN packet is sent, acknowledging the end of the conversation. We can leverage this information to understand what ports are open on a computer.
TCP Scanning vs SYN Scanning
The handshaking method is a simple way to see whether a port is open on a computer. If the connection with the target machine is completed, then the port is open. If not, then the port is either closed or the packets are being filtered by a firewall. Depending on the firewall configurations, the scanner may receive an error message or no response at all. This method is aptly named TCP Scanning.
An SYN scan works under the assumption that if a computer receives an SYN/ACK packet from a target, then that port is open, because otherwise the scanning computer would have received an RST packet. So, if a port responds to an initial SYN packet with an SYN/ACK packet, the scanning computer sends an RST packet and moves to the next port. If the target computer responds to the initial SYN packet with an RST packet, then the port is closed. This scan is often called “stealthy.” However, “stealthy” is a relative term in this case, namely because the scanner never completes a TCP connection. However, if a wide port range is probed, the scanner’s IP address will stand out on the network traffic logs. Further, most modern Intrusion Detection Systems (IDS) and firewalls can detect an SYN Scan.
Credentialed vs. Uncredentialed Scans
Uncredentialed network scanning allows an analyst to gather information regarding running services and their respective locations. In practice, port scanning gives you insight into what an attacker can find out about your network without having credentialed access. This information could help you pinpoint weaknesses in your systems by identifying factors such as outdated services, open and commonly vulnerable ports. Tenable.io offers three types of port scanning: TCP, SYN, and UDP. UDP scanning is rarely used due to the fundamental inaccuracy and speed constraints of the scanning method.
How to Execute TCP, SYN, and UDP Scans
Tenable.io’s scan policy templates can be configured to scan some or all ports. For example, the Host Discovery Scan template is very useful for identifying assets on your network. You can select “Port scan” under the Basic section of the scan settings. By default, the Host Discovery port scanner utilizes the TCP scan technique, employing an SYN scan if the TCP scan attempts are blocked by a firewall.
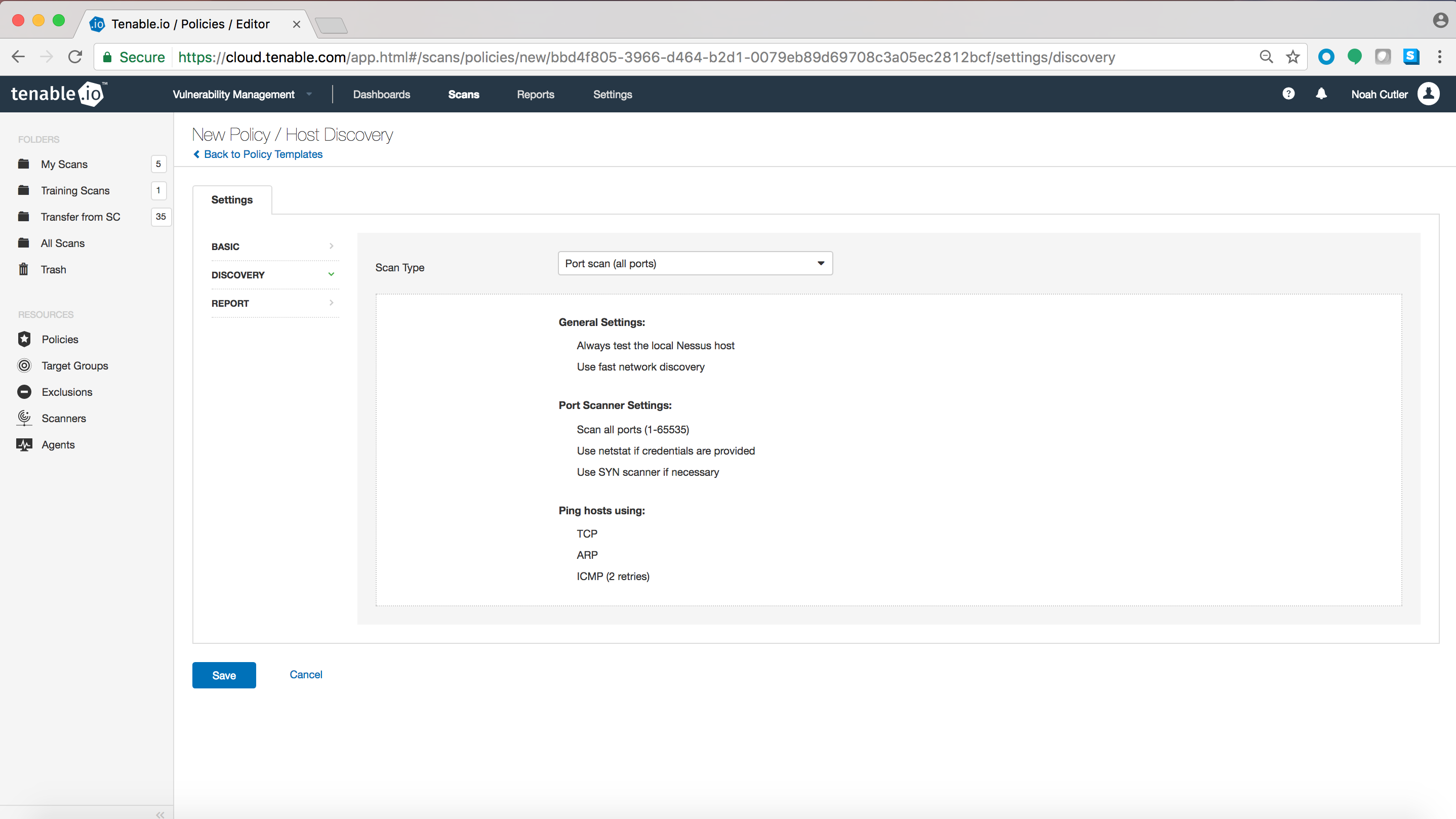
However, If you want to configure the scan yourself, select the “Custom” option in the “Scan Type” field.

Then go to “Port Scanning” and scroll down to the “Network Port Scanners” section. There you can choose any or all of the TCP, SYN and UDP port scanners.
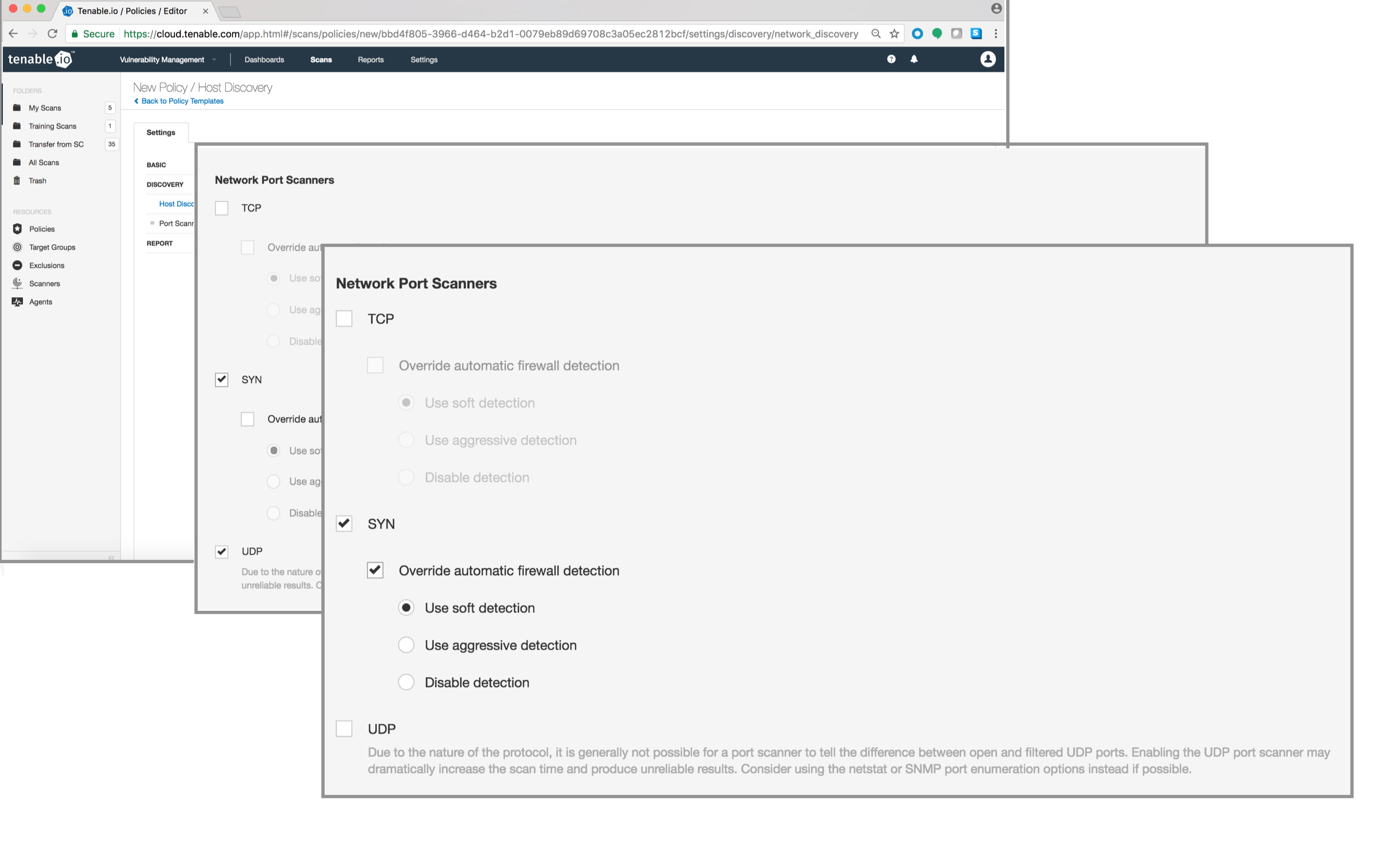
For the TCP and SYN port scanners, you also have the option to override some of the firewall detection features (firewall detection performed with Nessus Plugin ID: 27576). “Aggressive detection” runs plugins even if a port appears to be closed. “Soft detection” disables the ability to determine if a downstream network device has set a limitation of the rate at which resets are sent. Finally, “Disable detection” disables the firewall detection feature entirely.
Scanning More Than Just Ports
Port scanning can serve as a good starting point to understand and measure your Cyber Exposure, but external scans are just one part of understanding your organization’s Cyber Exposure. Once an uncredentialed network scan has been completed, you can continue with a more fine-tuned, credentialed scan.
You can input credentials manually, upload a file, or even have Tenable.io brute force default/weak credentials in the “Brute Force” section of “Settings” in an Advanced Scan Policy. An uncredentialed scan may demonstrate what your network looks like from the outside, but it is equally, if not more, important to take a look on the inside. Credentialed scans allow you to audit specific applications, evaluate program checksums against Tenable’s malware database, search through the file system of a computer and even scan individual file contents.
So, What Did I learn?
By scanning the lab, not only did I become more familiar with the Tenable.io platform, but I also learned the value of timing in vulnerability analysis. Scanning is not just about getting the information you need, it’s about getting that information as efficiently and effectively as possible.
Learning how to prioritize and map out your scans is essential to successfully managing, measuring and reducing your organization’s Cyber Exposure. With the expansion of IoT and container technology, attack surfaces are only growing, making this skill even more critical.
Tenable.io provides visibility into any asset on any computing platform and allows you to schedule scans on a regular basis, ensuring you always have the most useful, up-to-date information. Start a free 60-day trial of Tenable.io for your organization today.
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Vulnerability Management
- Vulnerability Scanning


