Verizon 2025 DBIR: Tenable Research Collaboration Shines a Spotlight on CVE Remediation Trends

The 2025 Verizon Data Breach Investigations Report (DBIR) reveals that vulnerability exploitation was present in 20% of breaches — a 34% increase year-over-year. To support the report, Tenable Research contributed enriched data on the most exploited vulnerabilities. In this blog, we analyze 17 edge-related CVEs and remediation trends across industry sectors.
Background
Since 2008, Verizon’s annual Data Breach Investigations Report (DBIR) has helped organizations understand evolving cyber threats. For the 2025 edition, Tenable Research contributed enriched data on the most exploited vulnerabilities of the past year. We analyzed over 160 million data points and zeroed-in on the 17 edge device CVEs featured in the DBIR to understand their average remediation times. In this blog, we take a closer look at these vulnerabilities, revealing industry-specific trends and highlighting where patching still lags — often by months.
In this year’s DBIR, vulnerabilities in Virtual Private Networks (VPNs) and edge devices were particular areas of concern, accounting for 22% of the CVE-related breaches in this year’s report, almost eight times the amount of 3% found in the 2024 report.
Analysis
The 2025 DBIR found that exploitation of vulnerabilities surged to be one of the top initial access vectors for 20% of data breaches. This represents a 34% increase over last year’s report and is driven in part by the zero-day exploitation of VPN and edge device vulnerabilities – asset classes that traditional endpoint detection and response (EDR) vendors struggle to assess effectively. The DBIR calls special attention to 17 CVEs affecting these edge devices, which remain valuable targets for attackers. Tenable Research analyzed these 17 CVEs and evaluated which industries had the best and worst remediation rates across the vulnerabilities. As a primer, the table below provides this list of CVEs and details for each, including their Common Vulnerability Scoring System (CVSS) and Tenable Vulnerability Priority Rating (VPR) scores. It’s worth noting that each of these CVEs was added to the U.S. Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) list in 2024.
| CVE | Description | CVSSv3 | VPR | Tenable Blog |
|---|---|---|---|---|
| CVE-2024-20359 | Cisco ASA and FTD Software Persistent Local Code Execution Vulnerability | 6.0 | 6.7 | CVE-2024-20353, CVE-2024-20359: Frequently Asked Questions About ArcaneDoor |
| CVE-2023-6548 | Citrix NetScaler ADC and Gateway Authenticated Remote Code Execution (RCE) Vulnerability | 8.8 | 7.4 | CVE-2023-6548, CVE-2023-6549: Zero-Day Vulnerabilities Exploited in Citrix NetScaler ADC and NetScaler Gateway |
| CVE-2023-6549 | Citrix NetScaler ADC and Gateway Denial of Service Vulnerability | 7.5 | 5.1 | |
| CVE-2023-48788 | FortiClient Enterprise Management Server (FortiClientEMS) SQL Injection Vulnerability | 9.8 | 9.4 | CVE-2023-48788: Critical Fortinet FortiClientEMS SQL Injection Vulnerability |
| CVE-2024-21762 | Fortinet FortiOS Out-of-bound Write Vulnerability in sslvpnd | 9.8 | 7.4 | CVE-2024-21762: Critical Fortinet FortiOS Out-of-Bound Write SSL VPN Vulnerability |
| CVE-2024-23113 | Fortinet FortiOS Format String Vulnerability | 9.8 | 7.4 | |
| CVE-2024-47575 | FortiManager Missing Authentication in fgfmsd Vulnerability (FortiJump) | 9.8 | 9.6 | CVE-2024-47575: Frequently Asked Questions About FortiJump Zero-Day in FortiManager and FortiManager Cloud |
| CVE-2023-46805 | Ivanti Connect Secure and Ivanti Policy Secure Authentication Bypass Vulnerability | 8.2 | 6.7 | CVE-2023-46805, CVE-2024-21887: Zero-Day Vulnerabilities Exploited in Ivanti Connect Secure and Policy Secure Gateways |
| CVE-2024-21887 | Ivanti Connect Secure and Ivanti Policy Secure Command Injection Vulnerability | 9.1 | 9.8 | |
| CVE-2024-21893 | Ivanti Connect Secure, Ivanti Policy Secure and Ivanti Neurons for ZTA Server-Side Request Forgery (SSRF) Vulnerability | 8.2 | 7.2 | CVE-2023-46805, CVE-2024-21887, CVE-2024-21888 and CVE-2024-21893: Frequently Asked Questions for Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways |
| CVE-2023-36844 | Juniper Networks Junos OS PHP External Variable Modification Vulnerability | 5.3 | 2.9 | Exploit Chain Targets Unpatched Juniper EX Switches and SRX Firewalls |
| CVE-2023-36845 | Juniper Networks Junos OS PHP External Variable Modification Vulnerability | 9.8 | 8.4 | |
| CVE-2023-36846 | Juniper Networks Junos OS Missing Authentication Vulnerability | 5.3 | 2.9 | |
| CVE-2023-36847 | Juniper Networks Junos OS Missing Authentication Vulnerability | 5.3 | 2.9 | |
| CVE-2023-36851 | Juniper Networks Junos OS Missing Authentication Vulnerability | 5.3 | 2.9 | |
| CVE-2024-3400 | Command Injection Vulnerability in the GlobalProtect Gateway feature of PAN-OS | 10.0 | 10 | CVE-2024-3400: Zero-Day Vulnerability in Palo Alto Networks PAN-OS GlobalProtect Gateway Exploited in the Wild |
| CVE-2024-40766 | SonicWall SonicOS Management Access and SSLVPN Improper Access Control Vulnerability | 9.8 | 7.4 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on April 23 and reflects VPR at that time.
Tenable Research Analyzes Edge CVE Remediation Trends
Featured prominently in the DBIR, these 17 edge device CVEs were further analyzed by Tenable Research and are organized by vendor with each chart below consisting of CVEs fixed in the same patch release. To understand remediation efforts from Tenable’s telemetry data, we analyzed the average time in days for remediation of these vulnerabilities. The charts shown below spotlight the three industries that had the shortest average time to remediate each vulnerability as well as the three sectors that took the longest amount of time to remediate.
Cisco
CVE-2024-20359 was highlighted in April 2024 by Cisco Talos as one of two known vulnerabilities being exploited by an advanced persistent threat (APT) actor labeled as UAT4356 by Talos and STORM-1849 by the Microsoft Threat Intelligence Center. The flaw was used as part of an espionage campaign known as ArcaneDoor. From our analysis, we found that the education, energy and utilities, and shipping and transportation industries had the longest average remediation time for this vulnerability. CVE-2024-20359 was added to the CISA KEV list on April 24, 2024; the same date Cisco Talos released its research on ArcaneDoor. This KEV addition had a due date of seven days for federal civilian executive branch (FCEB) agencies, which are mandated by Binding Operational Directive (BOD) 22-01. Despite this short patch window, we see that the government sector had a surprisingly high average remediation rate of 116 days. While this is well outside the KEV due date, government was one of the three industries with the fastest average remediation rate.
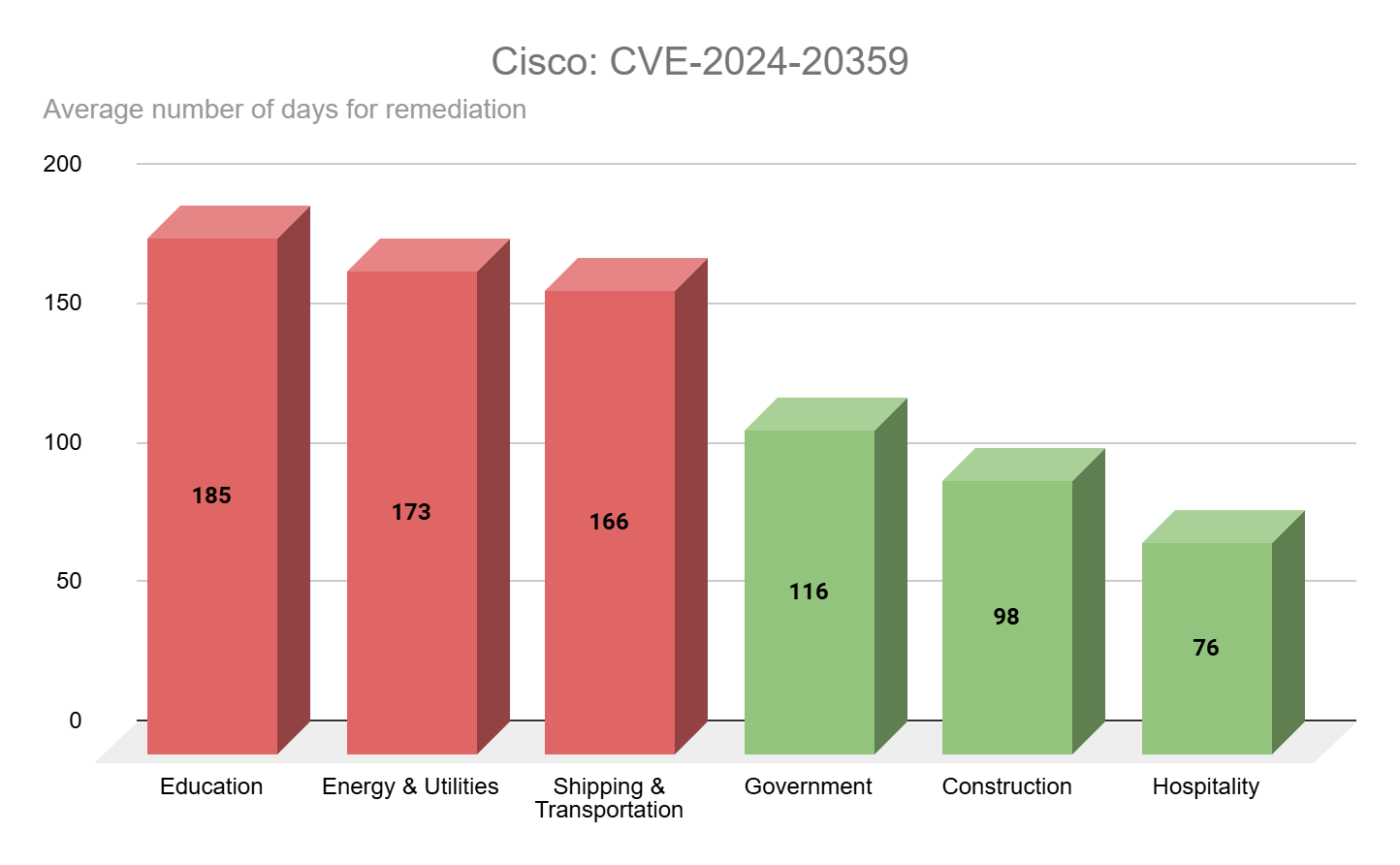
Source: Tenable Research, April 2025
Citrix
CVE-2023-6548 and CVE-2023-6549 are a pair of zero-day vulnerabilities that were exploited against Citrix NetScaler Application Delivery Controller (ADC) and NetScaler Gateway appliances. These vulnerabilities were patched in early January 2024, only months after Citrix addressed CVE-2023-4966, a critical flaw in NetScaler appliances called “CitrixBleed” that was widely exploited by a variety of attackers. While Citrix appliances continue to remain a high value target for attackers, the remediation rates, even amongst the three industries with the shortest average remediation rates, are much higher than we anticipated. The lowest average patch rate observed was 160 days for the consulting industry.
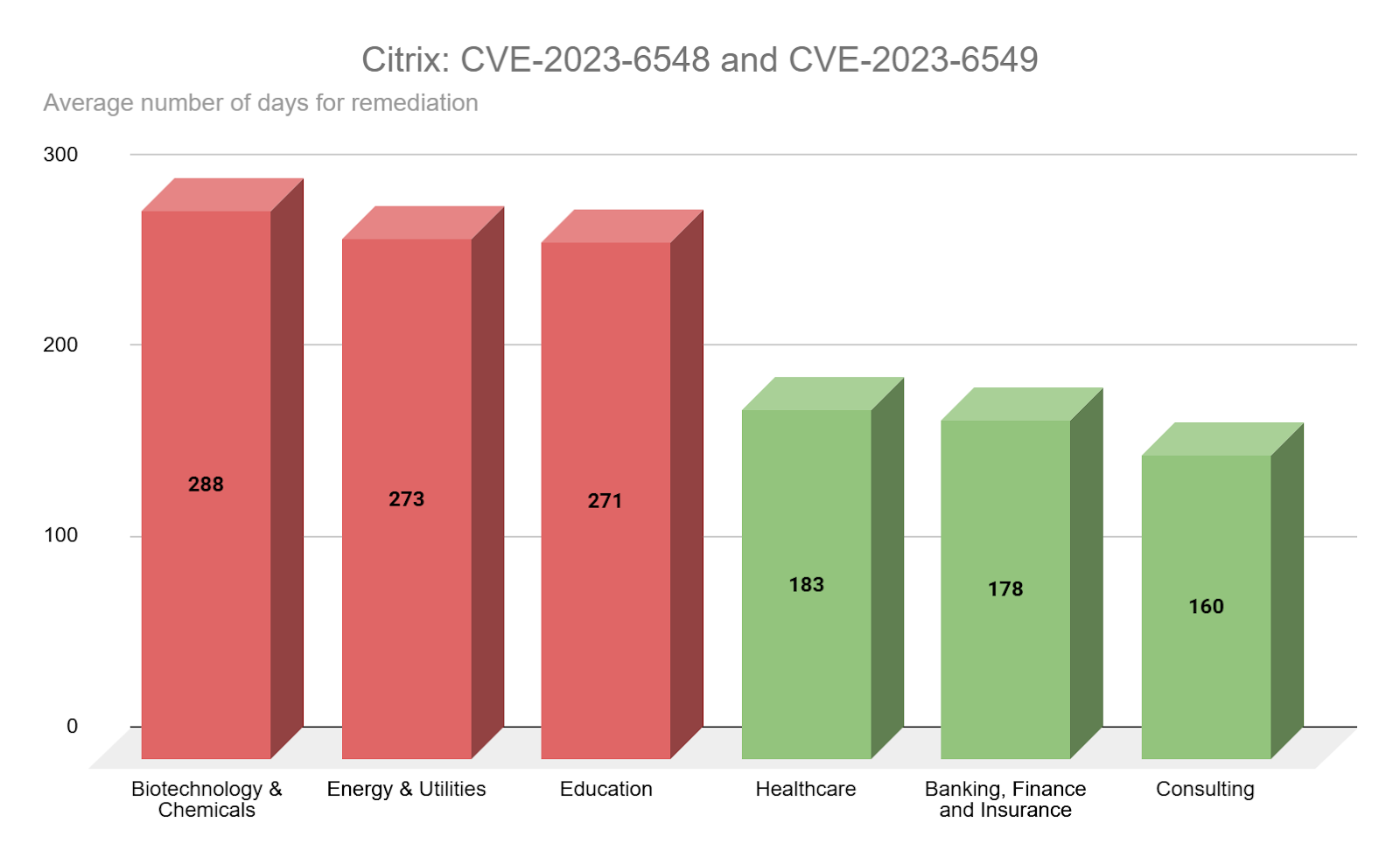
Source: Tenable Research, April 2025
Fortinet
CVE-2024-21762 and CVE-2024-23113 are two critical severity vulnerabilities affecting Fortinet’s FortiOS network operating system. At the time the Fortinet advisory was released for these vulnerabilities, CVE-2024-21762 was listed as “potentially being exploited in the wild.” Just a day later, CISA added it to the KEV list. Similar to the Citrix vulnerabilities above, the average remediation time for these vulnerabilities ranged from 172 days on the low end to over 260 days on the high end. The consulting industry had the longest average remediation rate while the software, internet and technology sector had the shortest at 172 days.
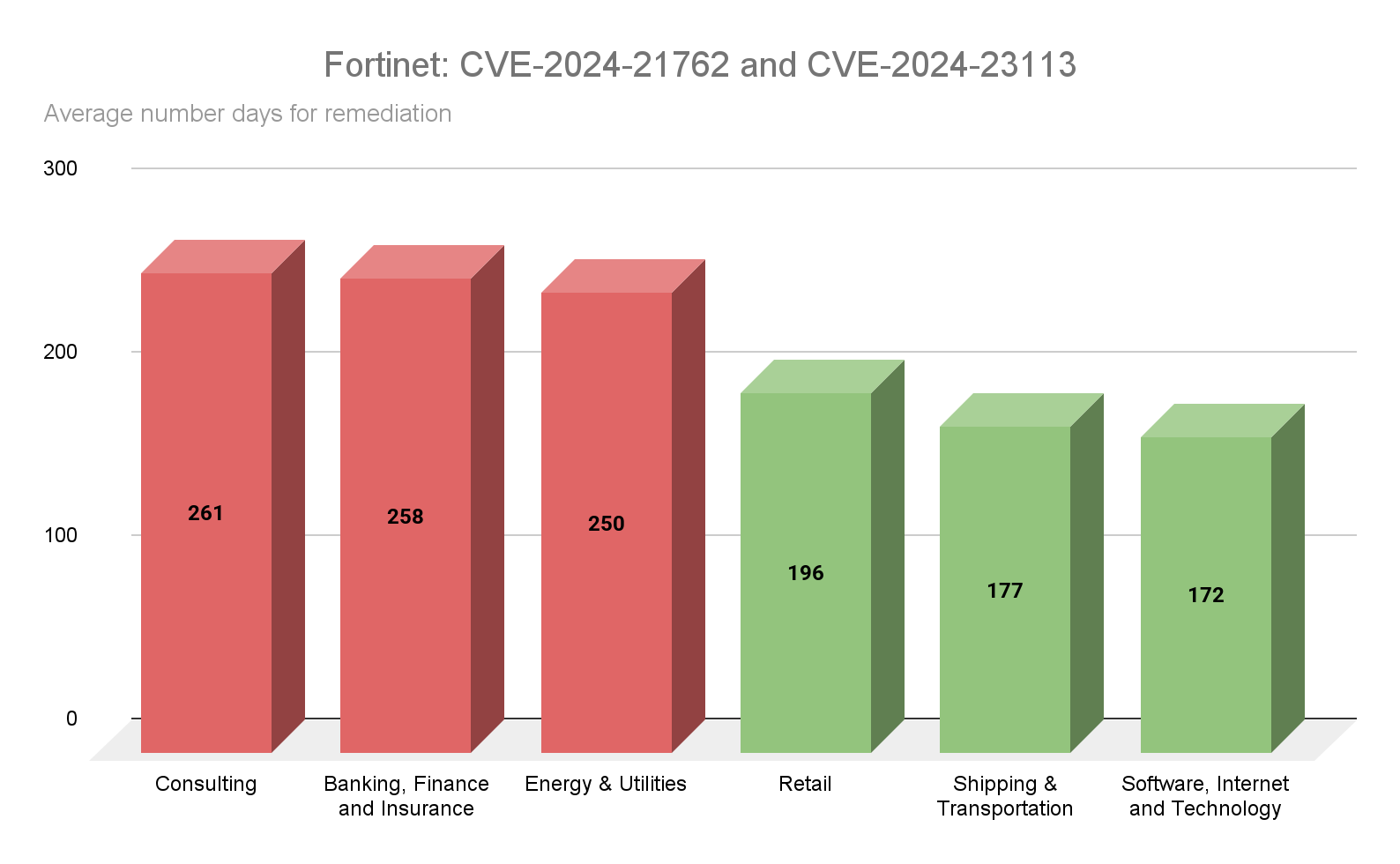
Source: Tenable Research, April 2025
In stark contrast to the Fortinet CVEs above is CVE-2023-48788, a critical SQL injection vulnerability affecting FortiClient Enterprise Management Server (FortiClientEMS). The communications and telecommunications sector led the way with an average remediation rate of only 12 days with healthcare a distant second, with an average of 71 days to remediate the flaw.
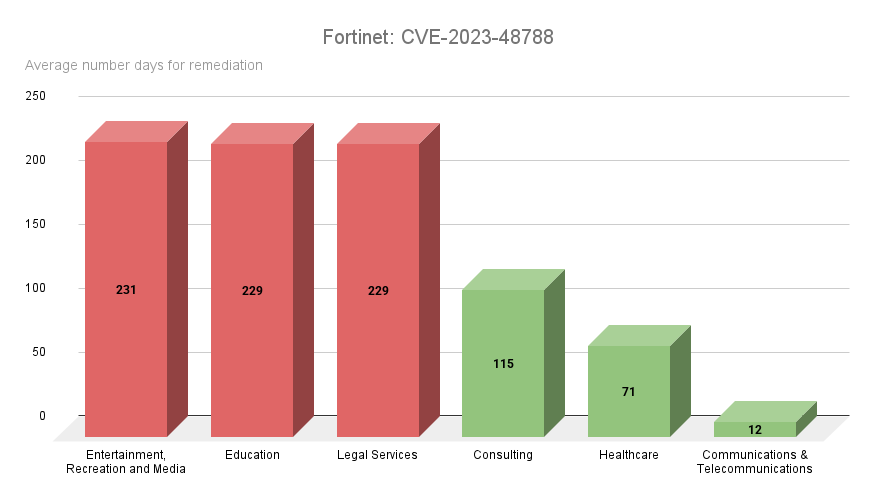
Source: Tenable Research, April 2025
Similar to CVE-2023-48788, CVE-2024-47575, a missing authentication vulnerability in FortiManager dubbed “FortiJump,” appears to have been urgently addressed by organizations. Our analysis revealed it had the lowest average remediation rates of the 17 CVEs we examined. Remediation times averaged a week, even for the slowest to patch industries.
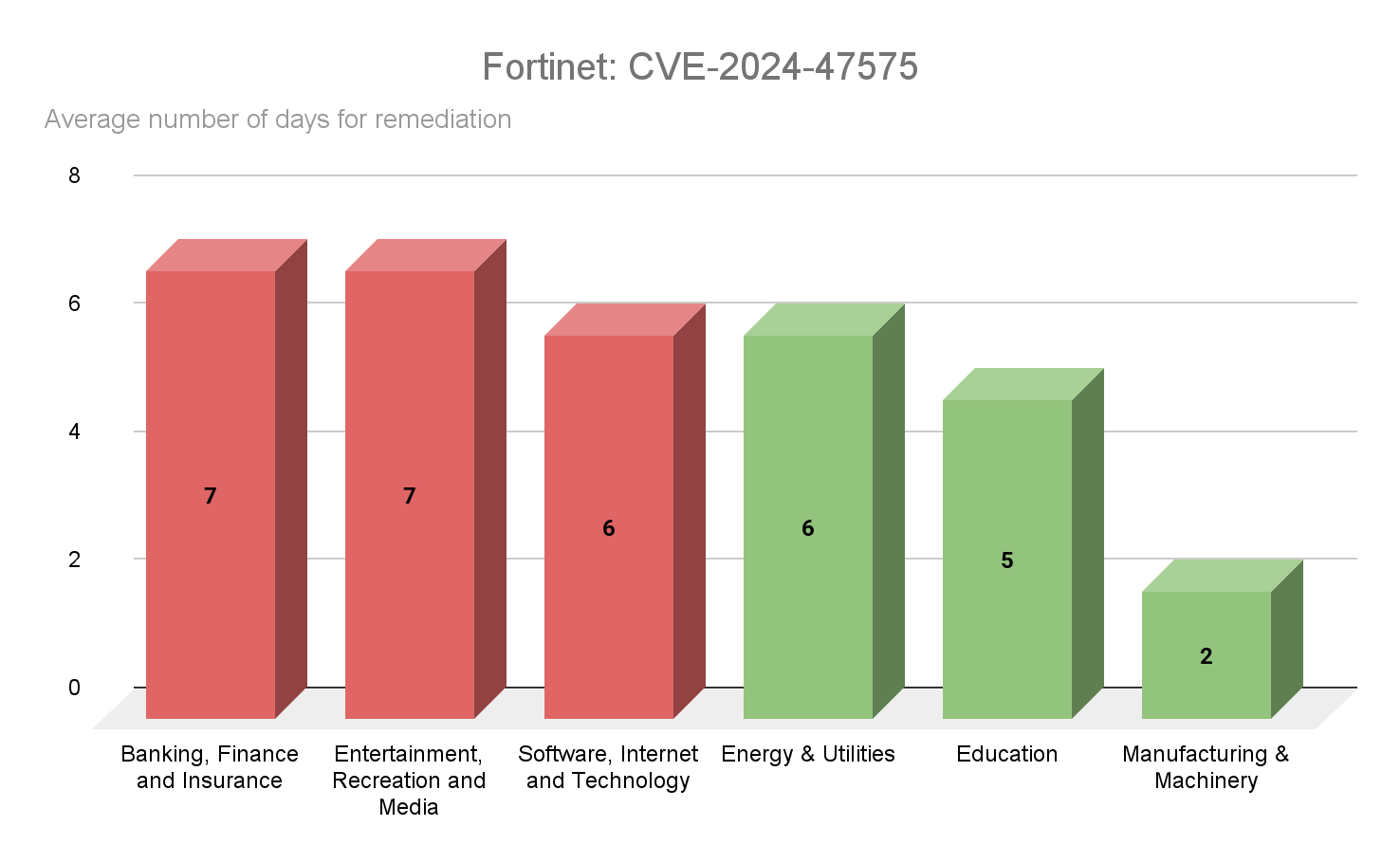
Source: Tenable Research, April 2025
Ivanti
Over the last five years, Ivanti’s Connect Secure and Policy Secure have been targeted by a variety of threat actors including ransomware groups and other nation-state aligned threat actors. Unsurprisingly, CVE-2023-46805 and CVE-2024-21887 have been reportedly abused by threat actors in chained attacks to achieve RCE. Additionally, these flaws were exploited as zero-days. From our analysis, even the quickest of industries to remediate these flaws took over 260 days to do so with the highest average just shy of 300 days.
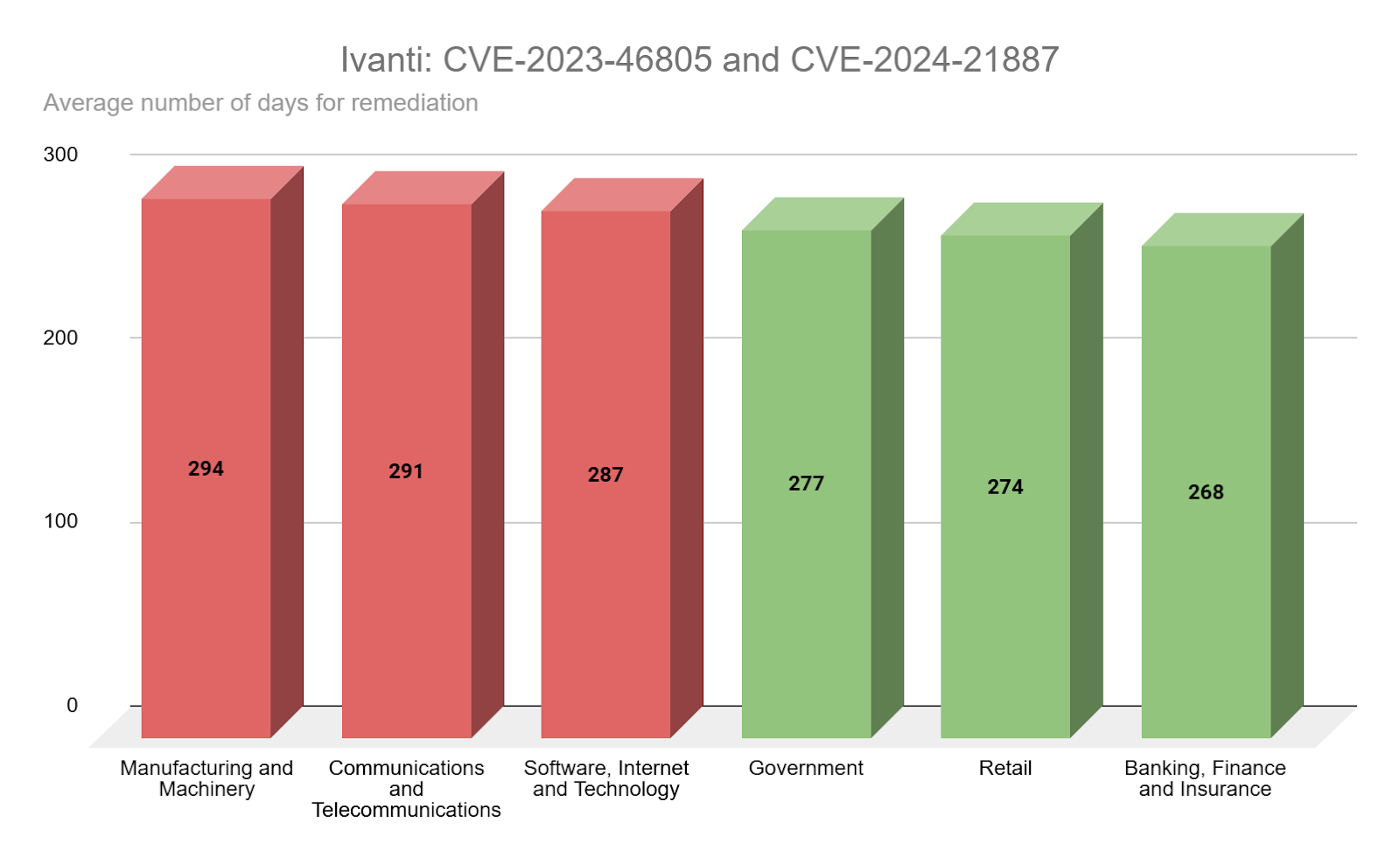
Source: Tenable Research, April 2025
Only a few weeks after patches for CVE-2023-46805 and CVE-2024-21887 were released, Ivanti released a new advisory with additional CVEs, including CVE-2024-21893. While initially it was believed that CVE-2024-21893 was only exploited in limited attacks, Shadowserver reported a major increase in exploit activity hours prior to a public proof-of-concept (PoC) being released. Interestingly this vulnerability saw some differing remediation rates with the biotechnology and chemicals sector being the fastest to patch with an average of nine days for remediation.
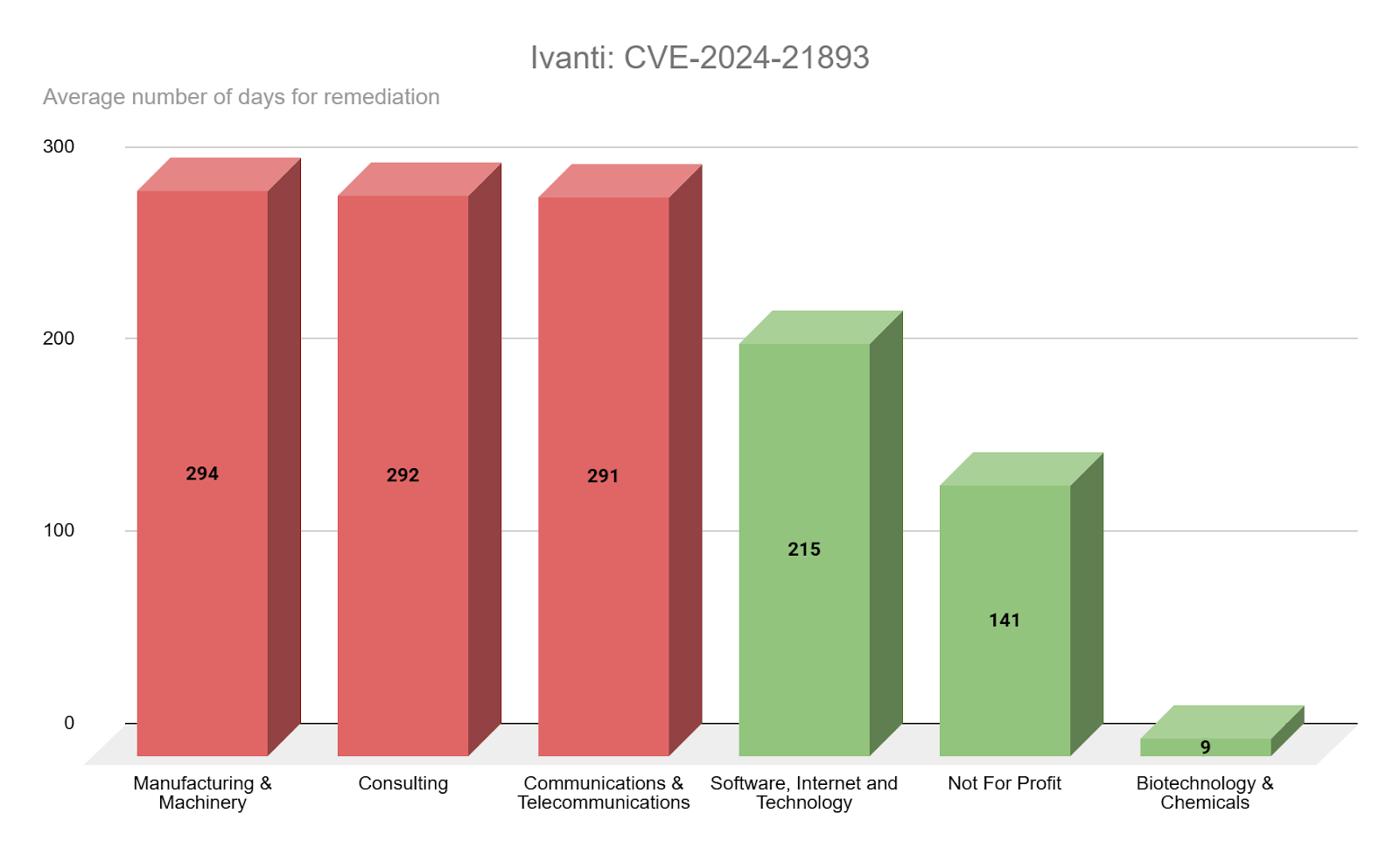
Source: Tenable Research, April 2025
Juniper Networks
Next we examined five CVEs from Juniper Networks (CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, CVE-2023-36847 and CVE-2023-36851) affecting Junos OS. These vulnerabilities were quickly exploited in a chained attack just days after being disclosed by Juniper Networks, which released its patches on August 17, 2024. While four of the five vulnerabilities had medium severity CVSSv3 scores, chaining these flaws allows for a remote, unauthenticated attacker to execute arbitrary code on unpatched devices. The average remediation rate for these vulnerabilities varied greatly, with food and beverage at over 420 days and shipping and transportation on the low end with an average remediation time of 80 days.
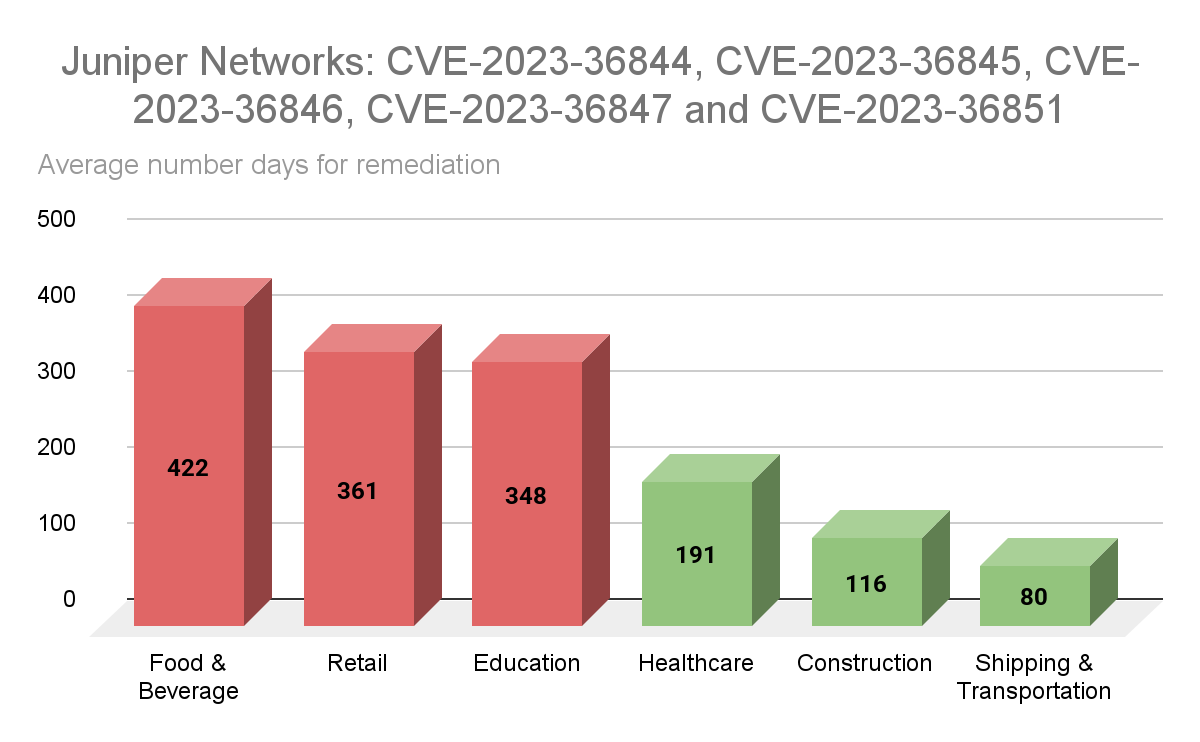
Source: Tenable Research, April 2025
Palo Alto Networks
CVE-2024-3400 is a critical command injection vulnerability affecting the Palo Alto Networks GlobalProtect Gateway feature of PAN-OS that was exploited in the wild as a zero-day. In our dataset, this CVE had a smaller footprint than others examined, yet it shared a similar trend with most industries requiring over 100 days to remediate. The banking, finance and insurance sector performed far better with an average of 45 days to close out this vulnerability.
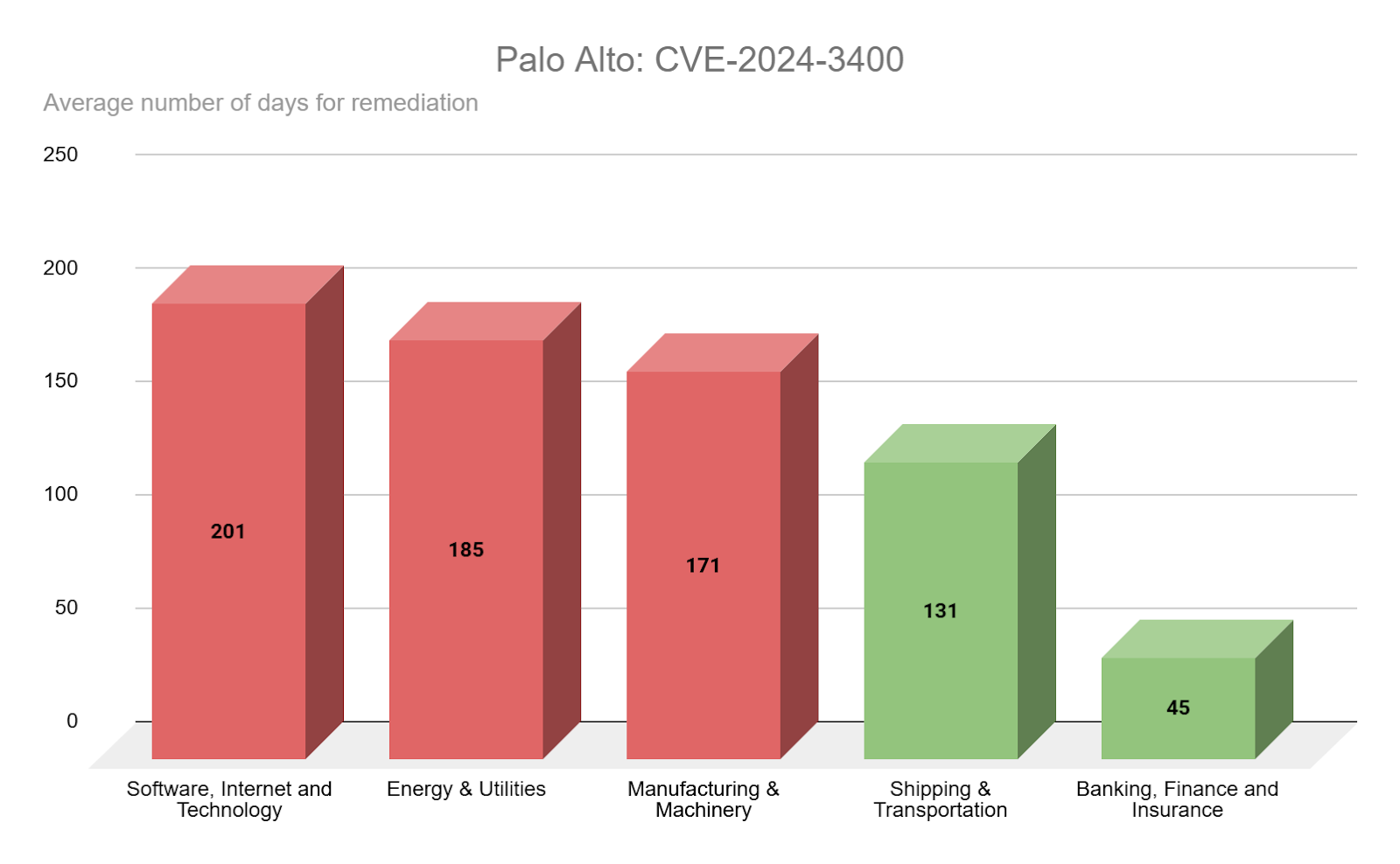
Source: Tenable Research, April 2025
SonicWall
The final CVE we examined was CVE-2024-40766, a critical improper access control vulnerability in the SonicWall SonicOS management access and SSLVPN. This flaw saw exploitation from ransomware groups, including Fog and Akira, which utilized the vulnerability to gain initial access to their victims' networks. In the case of this SonicWall vulnerability, average remediation rates were low in comparison to the other CVEs we examined, with the slowest sector taking 52 days (consulting) and the fastest (engineering) taking an average of only six days.

Source: Tenable Research, April 2025
Conclusion
The 17 CVEs we examined in our analysis, while only representing a small portion of the CISA KEV, encompass devices that have an elevated risk, due to their placement at the forefront of a network. Despite these being some of the most valuable targets for attackers, our examination of remediation rates show us that there’s still room for improvement across all industry verticals. Known and exploitable vulnerabilities continue to be abused by threat actors, many of which take advantage of readily available exploits. Data has become increasingly valuable and attackers and APT groups alike have zeroed in on the exploits and vulnerabilities that provide and help them maintain access to victim networks. In order to reduce risk and harden your networks, we recommend addressing each of the CVEs discussed in this post as well as reading the Verizon 2025 DBIR to understand the trends and tactics used by threat actors. Security isn’t just for infosec professionals — it’s everyone’s responsibility. The data compiled by Verizon, in collaboration with Tenable, offer valuable insights into today’s modern threat landscape and what you can do to better protect the networks, devices and people you defend.
Identifying affected systems
A list of Tenable plugins for the vulnerabilities discussed in the blog can be found on the individual CVE pages for each of the CVEs listed below. These links will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
- CVE-2024-20359
- CVE-2023-6548
- CVE-2023-6549
- CVE-2023-48788
- CVE-2024-21762
- CVE-2024-23113
- CVE-2024-47575
- CVE-2023-46805
- CVE-2024-21887
- CVE-2024-21893
- CVE-2023-36844
- CVE-2023-36845
- CVE-2023-36846
- CVE-2023-36847
- CVE-2023-36851
- CVE-2024-3400
- CVE-2024-40766
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Research
- Vulnerability Management
- Exposure Management
- Vulnerability Management

