by Stephanie Dunn
September 4, 2015
As the popularity of Apple products continues to grow within organizations, so has the adoption of the Apple Mac OS X systems into enterprise environments. This has also been fueled by changes in the mobile workforce, and the need for a flexible and mobile environment for employees has become essential. Many mobile workers access corporate resources from remote networks, which can potentially introduce viruses and malware into a corporate network. Macs are just as vulnerable to malware as any other platform, and the need for an organization to proactively monitor systems for vulnerabilities and protect against malware infections is vital. The Mac OS X Security dashboard provides details on installed Mac-based software, identifies Mac OS X versions, and detects OS X and software vulnerabilities.
Over the years, the Mac OS X operating system has obtained a reputation of being one of the most stable and secure operating systems (OS) due to the solid UNIX foundation, and ease of use. In addition, Mac OS X systems have been known for providing increased stability, reliability, and productivity among end users. While the Apple Mac OS X operating system is usually considered safer than most operating systems on the market, the potential for attacks are growing. Organizations should treat Mac OS-based risk management as serious as any other operating system. The potential for targeted attacks, malware infections, and exploited vulnerabilities will increase over time. The importance of securing Mac OS X systems should remain a top priority for any organization.
This dashboard provides several components that aid in ensuring the security of Mac OS X-based systems. The first column of components includes a matrix of detected hosts with Mac OS X 10.4 and later installed. This information can be used to provide a quick visual representation of the number of OS X-based systems and respective versions. The next two components present both the top Mac software vulnerabilities, along with the total number of vulnerabilities for Apple software by severity level. The analyst should review all vulnerabilities further to determine the overall risk to the organization. However, all high-risk vulnerabilities should be addressed and remediated first starting from critical on down.
This dashboard also includes a component that presents both active and passive vulnerabilities for the Chrome, Firefox, Safari, and Opera web browsers on Mac OS X systems. Web browsers regularly interact with other hosts on the Internet, making OS X browsers a prime target for attackers. Any vulnerable web browser can pose a security risk to an organization’s network, if left unpatched. Apple includes a built-in software update tool that detects, publishes, and schedules software updates for Mac OS systems. However, if the tool settings aren’t secured properly, the settings can be adjusted or turned off by corporate users. This component goes a step further by reporting on the number of hosts that have software installed, along with existing vulnerabilities, both critical and exploitable that should be remediated.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Security Center Feed under the category Monitoring.
The dashboard requirements are:
- Security Center 4.8.2
- Nessus 8.6.0
- NNM 5.9.0
When preparing initial credentialed scans, the analyst should also monitor for any failures. Credentialed scans failures can result from OS X systems being offline or unreachable, inventory changes, or invalid credentials. Failures can result in unpatched vulnerabilities on systems that can present security risks for an organization. By continuously monitoring credentialed scans, organizations will be able to obtain accurate patch and compliance auditing of OS X systems.
Tenable Security Center is the market-defining continuous network monitoring platform. Security Center includes active vulnerability detection with Nessus and passive vulnerability detection with Tenable's Nessus Network Monitor (NNM). Using Security Center, an organization will obtain the most comprehensive and integrated view of its network providing visibility and ensuring the security of Mac OS X systems.
The dashboard contains the following components:
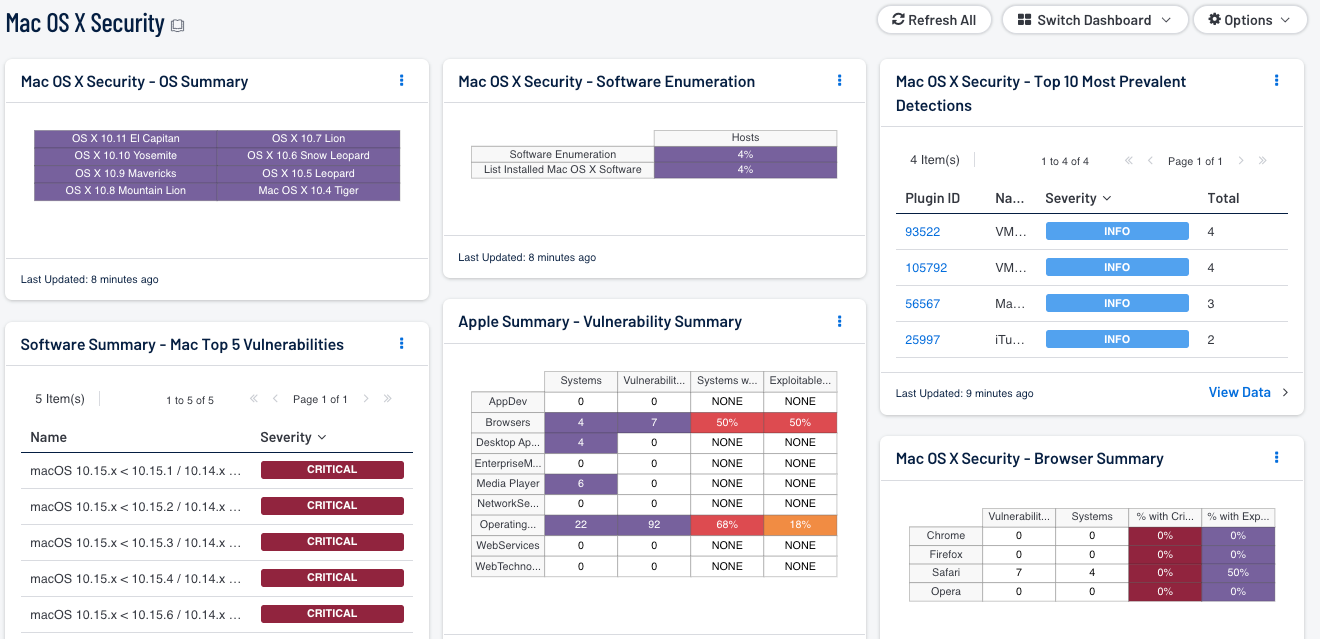
- Mac OS X Security - OS Summary: The OS Summary component presents detected OS X systems by version and code name on a network. The Vulnerability type searches for the keyword “Mac OS X 10.x” with “x” identifying the code name. When a OS X version is not present, the indication remains off (or uncolored); if a system with the specific OS X version is present, the indication changes to a purple. Clicking on the indicator will bring up the analysis screen to display details on the OS X systems. In the analysis screen, setting the tool to List OS will display the OS X version and subversion, along with the number of IP address by count. This information can be useful to the analyst in identifying OS X versions and counts for auditing purposes. Upgrading any outdated OS X systems can address multiple security flaws at once, which reduces overall risk to a network. In addition, organizations that upgrade OS X systems will be able to take advantage of the enhanced features within the new operating system, and gain improved performance.
- Apple Summary - Apple Status At a Glance: This component gives a quick visual status report on patching efforts for Apple applications. The number of critical, high, and medium vulnerabilities is displayed across three columns, as well as the number of days they have been detected. Represented are known vulnerabilities that have existed for: Over 30 Days, the Last 30 Days, or the Last 7 Days.
- Software Summary - MacOS Top 5: The Mac OS Top 5 component displays the Top 5 vulnerabilities detected on Mac OS Systems. The list is sorted by severity so that the top vulnerabilities that need to be remediated by the analyst are displayed first. In addition, the number of hosts affected by the vulnerability along with the corresponding plugin are also presented.
- Apple Summary - Vulnerability Summary: This component displays various Apple technologies by row, and enumerates any found vulnerabilities across the columns. Presented is the number of systems on which the technology has been located, the number of identified vulnerabilities, the ratio of vulnerable systems, and the count of how many are exploitable.
- Mac OS X Security - Top 10 Most Prevalent Detections: The Top 10 most prevalent detections component displays information on detected Mac OS X-based software on a network. The detected software is sorted by severity, along with the total number of system affected by host. To identify Mac OS X-based vulnerabilities, the “Mac OS X Local Security Checks” plugin family is used. In addition, the “detection” plugin name is also used to narrow down any detected vulnerabilities. The plugin ID, name, family and severity rating are also displayed for the analyst. If additional information is required, the analyst can click on the Browse Component Data icon, and click on the respective vulnerability. Details such as Plugin Name, IP address, DNS name, MAC Address, and a description of remediating the vulnerability are provided. This table can be beneficial to the analyst in detecting OS X software on a network, and assist in remediation efforts by identifying outdated software that needs to be upgraded.
- Mac OS X Security - Browser Summary: The Browser Summary component presents four of the most popular Mac OS X web browsers with active and passive vulnerabilities. This matrix includes four columns that present both count and ratio statics for each browser. The first column presents the total number of vulnerabilities by count. The systems column displays the number of systems that use the respective browser, and have vulnerabilities present. The critical and exploitable vulnerabilities columns each display a ratio of critical and exploitable vulnerabilities compared to the total number of vulnerabilities detected for each browser. This component is able to precisely identify Mac OS X-based vulnerabilities by utilizing the “Mac OS X Local Security Checks” plugin family. For each row, the respective web browser name is used within the plugin name field to detect outstanding vulnerabilities within that browser. Clicking on an indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities.
- Mac OS X Security – Software Enumeration: The Software Enumeration component uses plugin 22869 (Software Enumeration (SSH)) and plugin 83991 (List Installed Mac OS X Software) to extract a list of software from Mac OS X systems two different ways. The Software enumeration plugin works by running a command via SSH, which pulls a generic list of currently installed packages on the OS X system. The List Installed Mac OS X Software plugin gathers information on installed packages and software on the OS X system. This plugin presents a more in-depth list by providing information and versions on utilities, drivers, frameworks, and default Apple packages. Each Mac OS X host is scanned against each plugin, and presents a ratio of the total number of Mac OS X systems and compares that to the number of systems that were scanned. The analyst can obtain additional information by clicking on each indicator, and then switching the tool to Detailed Vulnerability list.