by Stephanie Dunn
August 24, 2016
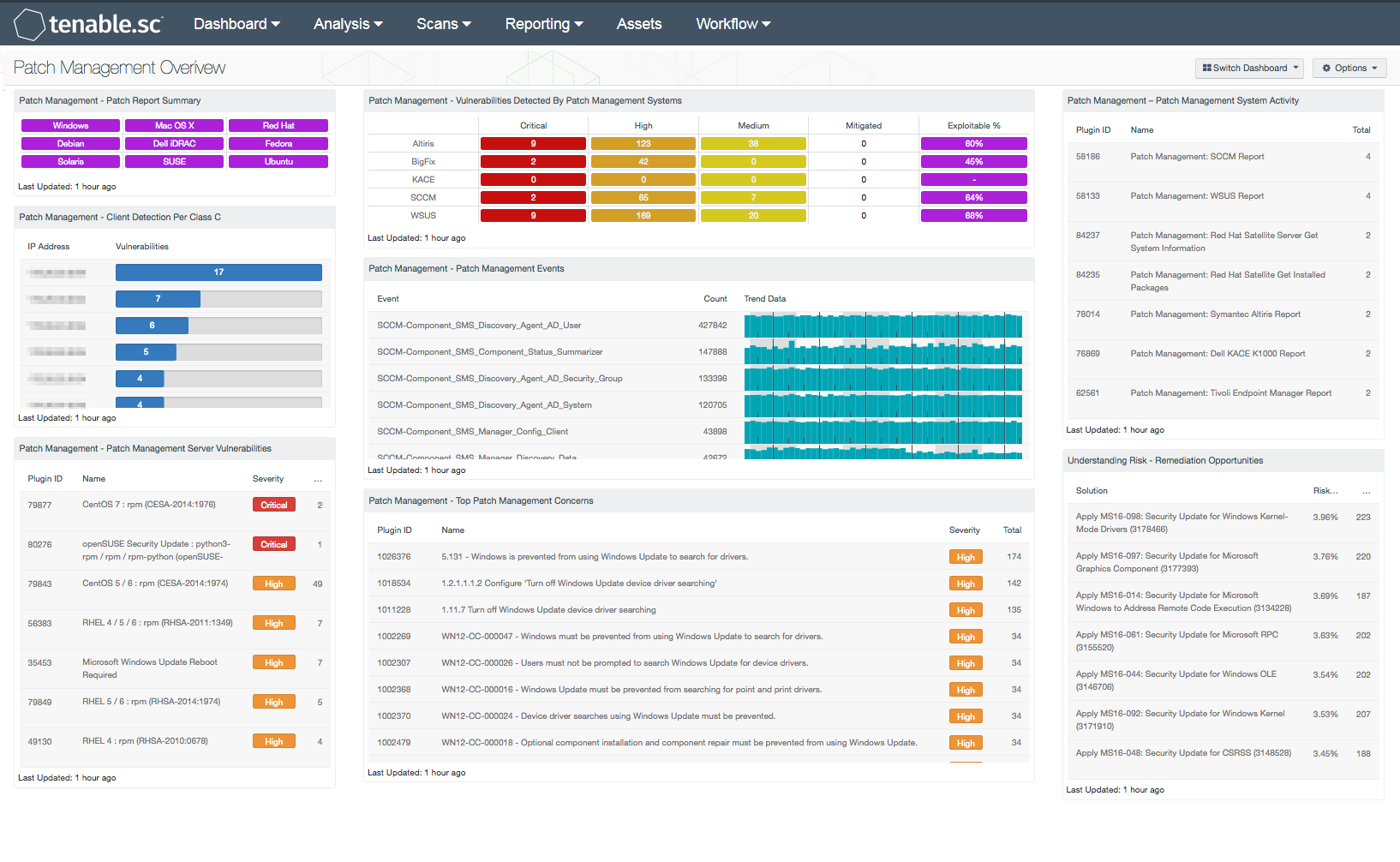
As the time between a vulnerability discovery and exploitation continues to decrease, organizations must have an effective patch management policy in place. Many organizations deploy patch management systems without additional oversight, fail to test patches before deployment, and do not re-scan systems to confirm patches have been applied properly. These issues can negatively impact critical systems due to a bad patch, and result in organizations falling behind in their patch cycle. This dashboard presents a high-level overview of vulnerabilities reported by patch management systems.
Deploying patches can become complex to manage as user mobility requirements change and additional devices are added to the network. This change may require the addition of one of more patch management systems to support an organization’s growing infrastructure needs. Tenable Nessus has the ability to query a variety of patch management solutions, and verify whether or not patches are installed on managed systems. Additionally, Nessus can also report on unmanaged hosts, or hosts that have fallen out of management, or aren’t functioning properly. Having a comprehensive patch management policy in place can provide organizations with a consistent, repeatable process that can be used to keep systems up to date.
This dashboard provides organizations with valuable information that can be used to compare patch management policies against the effectiveness of existing patch management solutions. Components included within this dashboard can be used to identify systems that may have been overlooked, fallen out of management, or aren’t functioning properly. Analysts can use this information to target and mitigate existing vulnerabilities on managed hosts, which can help to prevent attackers from injecting malicious code or compromise other systems on the network. Event data can alert analysts to issues with patch management solutions, missing clients, and patch failures on systems that need to be addressed. Other built-in patch management services can highlight vulnerabilities, potential misconfigurations, or services that need to be disabled. Information on potential remediation opportunities can assist with prioritizing patch management efforts. Using this dashboard, organizations will be able to strengthen patch management solutions and reduce overall risk for the organization.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.6.0
- NNM 5.9.0
- LCE 6.0.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network and effectively monitor patch management solutions. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor patch management solutions on the network. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to support proactive patch management efforts.
The following components are included in this dashboard:
- Patch Management – Patch Report Summary: This component presents indicators that will provide a report summary of existing vulnerabilities that need to be patched. Each indicator is separated by operating system, and will turn purple once a patch report analysis has been detected. Information presented within this component can be used to compare against vulnerabilities reported by existing patch management systems. Analysts can obtain additional information by changing the tool to Vulnerability Detail List, which will provide an output of patches that needed to be installed. Organization can use this component to gain additional insight into how often systems are being patched, and any systems that may have been overlooked within the patch management process.
- Patch Management – Client Detection Per Class C: This table presents a Class C summary of patch management clients installed on network hosts. Information presented within this list will include clients managed by Microsoft WSUS, SCCM, Symantec Altiris, and Red Hat Satellite. The table is sorted with the highest number of detected clients per subnet at the top. This information can be filtered to detect hosts that have fallen out of management, or aren’t functioning properly. Organizations can modify this table to include specific patch management clients per organizational requirements.
- Patch Management – Patch Management Server Vulnerabilities: Information presented within this component includes a list of patch management related vulnerabilities. Vulnerabilities discovered on patch management solutions such as WSUS, SCCM, Symantec Altiris, Dell KACE K1000, and Red Hat Satellite 5 and 6 servers, as well as patching services such as Linux yum, rpm, dpkg, and Spacewalk are included. Each vulnerability includes detailed information that the analyst can immediately drill down into. This table provides targeted information the analyst needs to mitigate existing vulnerabilities on patch management solutions and services, which can help to prevent attackers from injecting malicious code or compromise other systems on the network.
- Patch Management – Vulnerabilities Detected By Patch Management Systems: This matrix presents an overview of detected vulnerabilities reported by patch management systems. Tenable supports a wide variety of patch management solutions including SCCM, WSUS, IBM BigFix, Dell KACE K1000, and Symantec Altiris. Vulnerabilities are filtered by the Windows: Microsoft Bulletins plugin family, and presents a list of Microsoft vulnerabilities that have been reported by a patch management system. Each column presents the total count of vulnerabilities per severity level, mitigated vulnerabilities, and percentage of exploitable vulnerabilities. Clicking on an indicator will bring up the vulnerability analysis screen to display details on the reported vulnerabilities. In the vulnerability analysis screen, setting the tool to Vulnerability Detail List will display additional details on the vulnerabilities that have been detected by patch management systems. Analysts can use this component to compare the effectiveness of existing patch management systems, and how often systems are being patched.
- Patch Management – Patch Management Events: This component includes a list of detected events from patch management systems over the last 72 hours. The list is ordered so that the highest number of patch management events are at the top. Log events from patch management systems are forwarded to the Tenable Log Correlation Engine (LCE) server. Some events are passively detected by the Tenable Nessus Network Monitor (NNM) and then forwarded to LCE. Tenable supports a wide variety of patch management solutions and services including SCCM, WSUS, Windows Update, IBM BigFix, OS X Software Update, and Linux Yum Updates. Event data can detect changes in patch management solutions that analysts monitor to determine if further action is needed. Built-in patch management services can alert analysts if a patch failed to install correctly, or a host needs to be restarted.
- Patch Management – Top Patch Management Concerns: This component presents a list of top patch management compliance issues. The table is sorted by the highest number of hosts at the top, and includes information that can detect potential misconfigurations or services that need to be disabled on patch management systems. Compliance concerns on services such as Windows Update, WSUS, SCCM, and Linux patching services can report on potential misconfigurations, which can allow for attackers to inject malicious code into patch management systems that can be distributed out to the enterprise. Analysts can use this information to strengthen and secure patch management systems and services. Failed configuration checks are assigned a high severity, and checks requiring manual verification are assigned a medium severity, which should be reviewed further by the analyst to determine if the compliance concern is applicable to the organization.
- Patch Management – Patch Management System Activity: This table presents patch report information collected from patch management systems on the network. Nessus and Tenable.sc obtain credentials from patch management systems to perform patch auditing. Analysts can drill down into each patch management report to obtain additional information on missing updates, along with systems that are not being managed by a patch management solution. Additional information on managed host, client status, last user login, patch state, and description of the Microsoft vulnerability may be included. Information obtained within this component can be useful in detecting unmanaged systems, vulnerable hosts, or issues with clients not reporting to the patch management system.
- Understanding Risk – Remediation Opportunities: This table displays the top remediations for the network. For each remediation, the risk reduction for the network if the remediation is implemented is shown, along with the number of hosts affected. The table is sorted so that the highest risk reduction is at the top. Implementing the remediations will decrease the overall vulnerability of the network. Adding filters to the component, such as filtering on only critical severity vulnerabilities or filtering on a specific asset group, can narrow the focus of the component, giving remediation opportunities in specific areas.