by Carole Fennelly
June 22, 2022
Ransomware has evolved into an ecosystem with multiple players and an expanded threat model. Ransomware groups now deploy a double extortion technique, where they both encrypt and exfiltrate their victims’ data. The Tenable Security Research Team has released a report that enumerates common vulnerabilities exploited by ransomware affiliates and groups. The Ransomware Ecosystem dashboard enables organizations to quickly scan for the vulnerabilities commonly exploited by ransomware groups.
Organizations with effective Business Continuity and Disaster Recovery plans are protected against threats to availability of data, which can come in many forms, such as natural disasters, hardware failures, or malicious attacks. These organizations could recover operations from a traditional ransomware attack without paying the ransom. However, the vulnerabilities that gave ransomware groups the opportunity to successfully penetrate the infrastructure may still leave organizations open to significant risk. Like any good business, ransomware players discovered the advantage of threatening data confidentiality by publishing samples of their targets’ sensitive data and threatening to expose all the data unless they are paid.
Threat actors understand the economic advantage of investing in the ransomware ecosystem, becoming more sophisticated and efficient over time. Organizations often struggle to secure a budget for resources needed to protect their infrastructure and prevent attacks from succeeding.
The Ransomware Ecosystem dashboard displays assets by plugin family along with associated vulnerabilities. Operations teams use this information to evaluate risk based on the organization’s business priorities. The ability to rapidly mitigate vulnerabilities requires data to be presented in a concise manner focused on findings that pose the greatest risk to the organization. Risk managers leverage risk-based vulnerability management platforms to prioritize mitigation efforts.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 5.18.0
- Nessus 8.14.0
Tenable.sc enables organizations to quickly identify and locate vulnerabilities in their infrastructure.This dashboard displays the most common vulnerabilities sorted by platform type that are commonly exploited by ransomware groups. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives.
Components
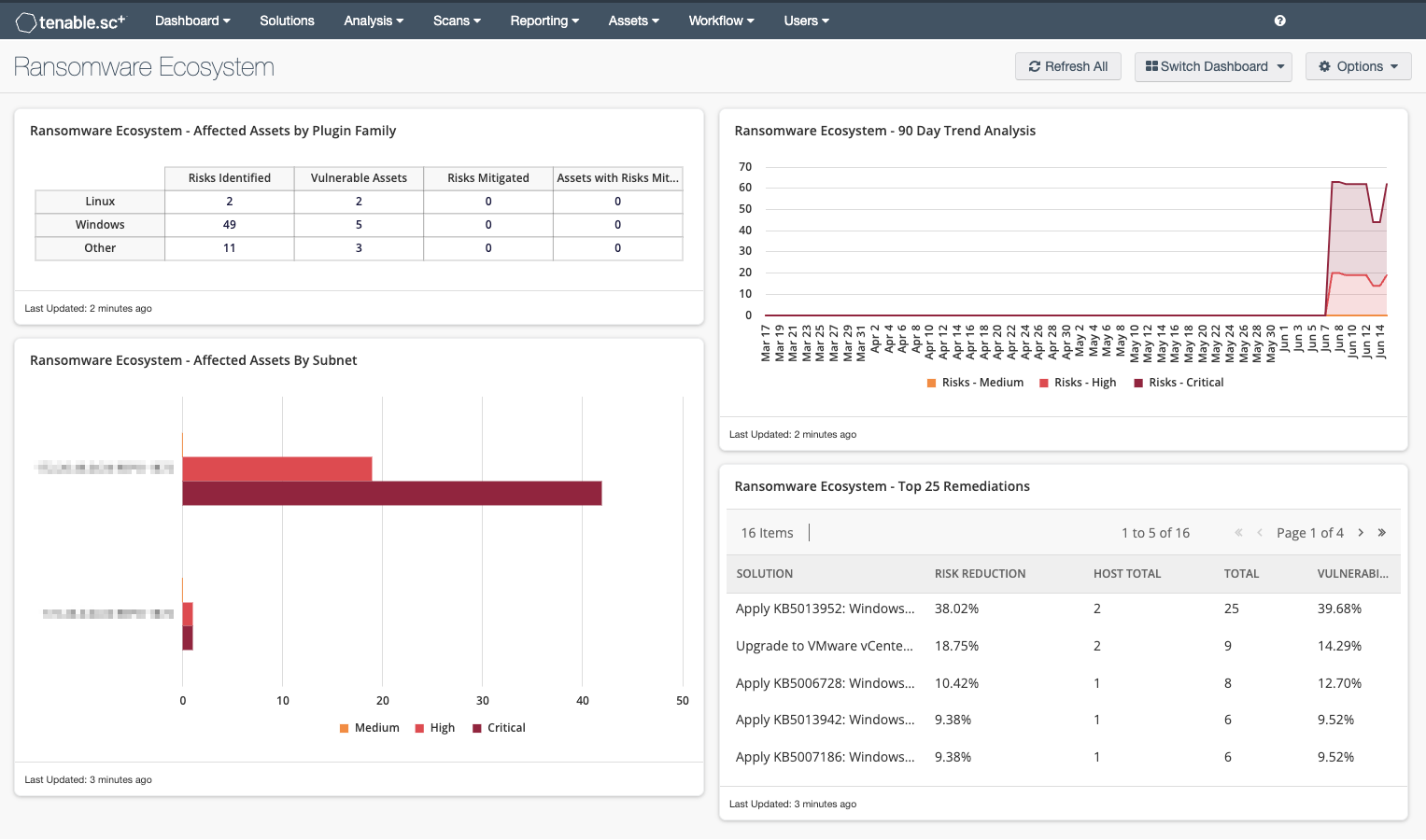
Affected Assets by Plugin Family – This matrix uses CVE(s) and Plugin Family for the Ransomware Ecosystem to present counts of the vulnerabilities and hosts that have been identified. This data helps organizations protect against threats to confidentiality and availability of data, as identified within the Ransomware Ecosystem. The number of vulnerabilities and hosts that are known to be mitigated are also displayed. A total of 77 CVEs are associated with this alert. Hosts and Vulnerabilities identified and mitigated are displayed using the referenced CVE. Rows for Linux, Windows, and other Operating Systems, enumerate the number of risks identified and mitigated. The number of assets that were found to be vulnerable and have been mitigated are also displayed.
Affected Assets By Subnet – This bar chart uses CVE(s) and Plugin Family for the Ransomware Ecosystem to present a Class C Summary analysis. Networks are sorted by vulnerability score. Affected assets on those networks are designated as having medium, high, and critical vulnerabilities. This data helps organizations protect against threats to confidentiality and availability of data, as identified within the ransomware ecosystem.
90 Day Trend Analysis – This trend line uses CVE(s) and Plugin Family Ransomware Ecosystem to present a 90-day trend analysis of medium, high, and critical vulnerabilities. A single series containing medium, high, and critical risks over the time-frame is displayed. The Last Observed filter is used to help organizations identify persistent vulnerabilities by determining if the vulnerability was detected on a recent scan. This data helps organizations protect against threats to confidentiality and availability of data, as identified within the Ransomware Ecosystem.
Top 25 Remediations – This table uses CVE(s) and Plugin Family for the Ransomware Ecosystem and the Remediation Summary Tool to present a solution, risk reduction percentage, number of hosts affected, number of vulnerabilities, and vulnerability percentage. Organizations can use the data to identify which vulnerability remediations will have the most significant impact. Guidance on mitigation techniques is provided. Vulnerabilities are sorted by risk reduction impact: remediating items at the top of the list will have the most impact in reducing risk. This data helps organizations protect against threats to confidentiality and availability of data, as identified within the Ransomware Ecosystem.