While evaluating Burp Community Edition, Tenable discovered that Burp sends a couple of HTTPS requests without verifying the server certificate. Failure to validate the remote certificate allows a man in the middle to intercept communication and inject new data.
Checking For Updates
On start up, Burp sends an HTTPS request to https://[ip]/Burp/Releases/CheckForUpdates?product=community&version=[version] without validating the server certificate. A normal response looks like the following:
{"result":"update_available","licenseId":"","manualDownloadUrl":"/burp/communitydownload/","autoDownloadUrl":"","updates":[{"description":"Various bugfixes and enhancements","builds":[{"installationType":"jar","filename":"burpsuite_community_v1.7.34.jar","fileSize":26400457},{"installationType":"linux","filename":"burpsuite_community_linux_v1_7_34.sh","fileSize":99994421},{"installationType":"macos","filename":"burpsuite_community_macos_v1_7_34.dmg","fileSize":87343864},{"installationType":"win32","filename":"burpsuite_community_windows-x86_v1_7_34.exe","fileSize":90715392},{"installationType":"win64","filename":"burpsuite_community_windows-x64_v1_7_34.exe","fileSize":94483712}],"productType":"community","releaseNotesUrl":"http://releases.portswigger.net/2018/06/1734.html","isStable":true,"version":"1.7.34","eulaContent":"","eulaSerialVersion":""}]}
A man in the middle can alter any of these fields. In particular, we found adding a malicious URL to the description field to be dangerous.
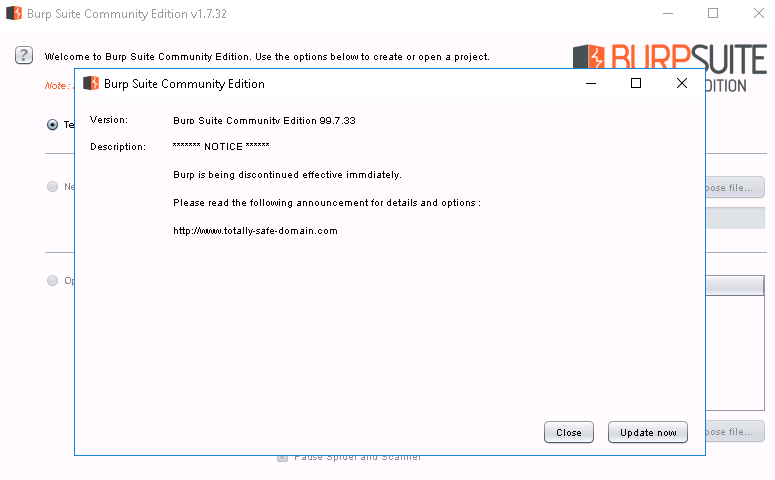
Telemetry Data
Burp fails to validate the server certificate when it sends telemetry data to https://[ip]/feedback/submit. A man in the middle can extract the following client data:
Version: 0
ProductType: Free
ProductVersion: 1.7.32
UniqueIdentifier: [removed]
Type: 4000
Version: 0
DebuggerPresent: false
JavaFX_support: true
file_encoding: Cp1252
java_runtime_name: Java(TM) SE Runtime Environment
java_runtime_version: 1.8.0_112-b15
java_specification_name: Java Platform API Specification
java_specification_vendor: Oracle Corporation
java_specification_version: 1.8
java_vendor: Oracle Corporation
java_version: 1.8.0_112
java_vm_info: mixed mode
java_vm_name: Java HotSpot(TM) 64-Bit Server VM
java_vm_specification_name: Java Virtual Machine Specification
java_vm_specification_vendor: Oracle Corporation
java_vm_specification_version: 1.8
java_vm_vendor: Oracle Corporation
java_vm_version: 25.112-b15
max_memory: 518,979,584
os_arch: amd64
os_name: Windows NT (unknown)
os_version: 10.0
sun_arch_data_model: 64
sun_cpu_endian: little
Type: 5000
Version: 0
FEATURE_TYPE: SUITE_PROCESS_BURP_LAUNCHED
TYPE: FEATURE_USE
