Exposure management: How to get ahead of cyber risk
The role of exposure management in building cybersecurity programs
Exposure management gives a broad view across your modern attack surface so you can better understand your organization’s cyber risk and make more informed business decisions. By understanding what your attack surface looks like and where you have the greatest risk, your IT and security teams can more effectively address vulnerabilities and other exposures from both a technical and business standpoint.
In this knowledgebase, take a closer look at what exposure management is, the role of risk-based vulnerability management and explore how it protects your organization from cyberattacks.
Learn more about:
7 benefits of an exposure management platform
A comprehensive exposure management platform can give you the visibility you need to reduce cyber risk without disparate tools that silo critical security data.
Learn MoreGet visibility, prevent attacks, communicate risk
How predictive threat context and objective metrics help prevent cyberattacks.
Learn MoreHow to build an exposure management program
With five steps, you’ll be on your way to building an exposure management program.
Learn MoreJoin the exposure management community
Join other professionals interested in learning more about exposure management.
Learn MoreBenefits of exposure management
Explore some of the many benefits of an exposure management strategy.
Learn MoreChoosing an exposure management solution
Here are some things you should look for in an exposure management solution.
Learn MoreAnticipate attacks. Proactively reduce risk.
Tenable One is the only exposure management platform you’ll need for a single, unified view of your modern attack surface. With Tenable One, you’ll be empowered to anticipate the consequences of cyberattacks and proactively address and manage cyber risk for all of your assets, everywhere.
Exposure Management Insights
Tenable cyber exposure study: Defending against ransomware
Threat actors are banking on the likelihood your organization hasn’t remediated common and known software vulnerabilities. They want to use those exposures to infiltrate your systems, often with malicious intent to infect your assets with ransomware.
Many ransomware infections originate from these vulnerabilities and somewhere security teams often overlook — your Active Directory (AD).
If attackers can successfully exploit just one security weakness in Active Directory, they can easily escalate privileges. And, if your organization has poor cyber hygiene, there’s a pretty good chance they’ll easily gain a foothold within your attack surface and spread ransomware.
So, what can you do? Explore this study from Tenable to learn more about:
- Most targeted attack vectors and exploits
- How to prioritize remediation to focus on vulnerabilities that pose the greatest threat to your organization
- How Tenable One can help you identify Active Directory (AD) vulnerabilities and other exposures.
How to grow vulnerability management into exposure management
Prioritizing a never-ending list of critical or high vulnerabilities will never lead to an actionable solution for your cyber exposure problem, especially if you still use traditional vulnerability scoring tools and legacy vulnerability management practices.
The reality is, current approaches for attack surface management just aren't keeping pace with today's vast and complex environments, which require a shift to a risk-based vulnerability management.
This approach to continuous threat exposure management goes beyond just evaluating cyber risk. Mature vulnerability management programs should also understand cyber threats in business context. This is critical for exposure management and your prioritization and remediation strategies.
This vulnerability management report from Gartner details how you can evolve your vulnerability management program to exposure management. Read more to find out about how to:
- Define the scope and cadence of vulnerability assessments
- Enhance asset discovery to include the cloud and digital assets
- Use prioritization and validation strategies to focus on exposures threat actors actively exploit
- How to incorporate your risk management processes into existing workflows and work more collaboratively across teams
How people process and technology challenges hurt cybersecurity teams
Tenable commissioned a study with Forrester to get insight from more than 800 IT and cybersecurity professionals about how people, process and technology challenges hamper impact risk-reduction strategies.
This report highlights the importance of why organizations must shift from reactive to preventative security.
Among some key findings:
- The average organization preventatively defended against less than 60% of cyberattacks in the past two years.
- More than half of IT and security leaders say cloud infrastructure is the greatest exposure in their organization.
- Six of 10 cybersecurity and IT pros say their security teams are too busy fighting critical incidents to take a preventative approach to reduce exposure.
Read this report to learn more about:
- The most frequently used cybersecurity tools
- The need for more cybersecurity resources
- Complexities of public, private, multi-cloud and hybrid cloud security
Five steps to prioritize true business exposure
Attackers don’t care about your business silos. In fact, they’re hoping you have disconnects between your IT and security teams. Siloed security is a natural evolution of rapid technological adoption, especially as your teams integrate more OT, IoT, and cloud assets into your workflows.
Alongside this growth, the industry is inundated with disparate vulnerability management tools, each designed to tackle just one specific part of your entire attack surface. Few operate as a comprehensive, all-in-one security solution. That leaves you with disparate data, incomplete visibility and blind spots attackers are eagerly hoping to find before you do.
Threat actors will seek out your security weaknesses and then use them to move laterally across your network, often undetected.
Read this ebook to learn more about how to unify security across your attack surface, including:
- Lessons learned from past breaches
- Common exposure management obstacles
- Five ways you can optimize your vulnerability prioritization strategies to prevent breaches.
Tenable Connect community: Your go-to resource for exposure management
Join Tenable Connect to engage with others who have similar interests in learning more about exposure management or how to mature existing risk-based vulnerability management programs to a more effective exposure management strategy.
Welcome to the Tenable One deployment guide
Tenable One is an exposure management platform that helps organizations to gain visibility across the modern attack surface, focus efforts to prevent likely attacks, and accurately communicate exposure risk to support optimal business performance.
Read MoreQuick tips for effective exposure response
In today’s fast-paced digital landscape, managing vulnerabilities is essential — but it’s about more than identifying weaknesses. Effective vulnerability management requires prioritizing and addressing risks in ways that drive security improvements and prevent major exposures.
Read MoreHybrid Cloud Security with Tenable One
Tenable Cloud Security isn't just cloud security. It's part of the larger Tenable exposure management ecosystem — and that can make a world of difference. As risks don’t live in silos and adversaries don’t attack in a box, being able to use solutions from one vendor for different types of infrastructure (on-prem, cloud, OT, ...) to detect potential attack paths is crucial.
Watch nowFrequently asked questions about exposure management
Are you new to threat exposure management? Do you have questions, but not sure where to start? Check out this FAQ about cyber exposure management.
What is exposure management?
What does exposure management do?
How can exposure management mature my cybersecurity program?
Why do I need exposure management?
What are the key roles in an exposure management program?
How can I get started with exposure management?
- Know the security of all of your assets and identify gaps.
- Look at your entire attack surface from an attacker’s perspective.
- Prioritize remediation based on actual organizational risk (not arbitrary CVSS scores).
- Measure your remediation processes with continuous improvement.
- Effectively communicate risk and take action to harden your attack surface.
What are some benefits of exposure management?
- Comprehensive visibility into your attack surface.
- Shift from reactive security to anticipate cyberattack consequences.
- Contextualized security data to prioritize remediation.
- More effective communication throughout your organization, all the way up to the C-suite and board.
What are some things I can do to get ahead of cyber risk?
How does exposure management help guide better business decisions?
How can I proactively reduce cyber exposure?
What should I look for in an exposure management platform?
- Makes it easy to see all of your assets, everywhere, all in one platform.
- Helps you make sense of security data and provides threat intelligence, supported by AI and machine learning, so you can anticipate threats and prioritize remediation.
- Helps you effectively communicate cyber risk to make better security and business decisions.
What can I learn from exposure management?
- How secure are we?
- What should we prioritize?
- How are we reducing exposure over time?
- How do we compare to our peers?
Can exposure management disrupt attack paths?
Why is asset inventory important for exposure management?
How to build an exposure management program
While shifting to a risk-based approach can help your organizations mature your vulnerability management program, the real question today is — is that enough?
The answer is not likely.
Instead, an exposure management program can help you take your cybersecurity program from one that’s reactive and bogged down in incident response to one that’s proactive and gives your team comprehensive insight into your entire attack surface. This will help you keep up with the constantly changing threat landscape and what that means for your unique organizational needs.
Implement these five recommendations to better understand all of your exposures so you can proactively reduce cyber risk:
-
Assess your current assets, on-prem and in the cloud (IT, OT, IoT, web apps, etc.).
Ask: Do our technologies work together and give us comprehensive insight into all of our exposures? Or, are they still siloed?
-
Understand your attack surface visibility.
Ask: What can we see? What do we need to see?
-
Prioritize efforts.
Ask: What should we do first? How can our remediation strategies be more predictive? Are we using threat intelligence? Can we analyze all attack paths for our most critical assets?
-
Measure remediation processes.
Ask: How well are we fixing exposures we find now? What can we do to make this more effective? What do our efforts look like compared to industry peers?
-
Communicate and take action.
Ask: How secure are we? Can we communicate our security posture effectively to executives, key stakeholders, and others? How do we utilize data to make more effective business decisions?
Which exposure management platform is right for your organization?
Finding a trusted and effective cybersecurity solution has long been frustrating and time-consuming. And, oftentimes, even after you painstakingly evaluate and implement a solution, getting everyone to use it and realize full benefits can be even more challenging.
That’s because these solutions have traditionally been hard to use or they provide so much data your teams don’t know what to do with it all.
Selecting an exposure management solution and getting your team buy-in doesn’t have to be such a headache. Here are three key features to look for to simplify the process:
-
The solution makes it simple to see all of your assets, everywhere, in one platform.
Yes, both on-prem and in the cloud. The solution should be more than just a way to inventory your assets. An effective exposure management solution should also identify asset-related vulnerabilities, misconfigurations and other security issues and enable continuous monitoring so you always know what you have and where you may have exposures.
Look for a solution that gives you a unified view of your entire modern attack surface so you can eliminate blind spots and know what you need to do to effectively manage cyber risk.
-
The solution helps you make sense of data, anticipate threats and prioritize remediation.
Look for an exposure management system that will help you use threat intelligence and other relevant data to anticipate consequences of a cyberattack — as it directly applies to your organization.
Look for a solution that identifies relationships across your attack surface between assets, exposures, privileges and threats, and that can help you prioritize risk management and remediation. Your solution should also be able to continuously identify attack paths that pose the greatest risk of exploitation, even as your attack surface rapidly changes and expands. These features will make it easier for your teams to proactively reduce risk with the least amount of effort to prevent attacks.
-
The solution should help you effectively communicate cyber risk so you can make more informed security and business decisions.
Look for an exposure management solution with a centralized and business-aligned view of your exposures, along with clear KPIs to measure progress over time.
The solution should also offer insight beyond a broad overview so you can drill down into specifics from an asset, department or operational level. Also, look for a solution with benchmarking capabilities so you can understand how well your program performs in relation to industry peers.
Exposure management benefits
Exposure management is all about moving from reactive security to a more proactive strategy that decreases your exposures. By adopting an exposure management platform, your organization will be better prepared to anticipate likely attacks while proactive reducing risk.
Here are some benefits of exposure management strategy:
Get comprehensive visibility
With a unified view of your attack surface, you can quickly identify all of your assets, everywhere, discover related security issues, and reduce time and effort you need to reduce risk.
Anticipate cyberattack consequences
An exposure management platform can help you better understand relationships between your assets, exposures, privileges and threats across your entire attack surface — on-prem and in the cloud.
Prioritize actions
By continually identifying and focusing on your exploitable vulnerabilities, and attack and breach pathways, you can improve your risk prioritization abilities for better remediation insight to more effectively reduce cyber threats and prevent attacks.
More effective communication
An exposure management program gives you a business-aligned view of your exposures so you can more effectively communicate with your key stakeholders in a way that aligns with your business goals and objectives.
See Tenable One in action
Tenable One combines risk-based vulnerability management, web app scanning, cloud security and identity security into a single exposure management platform. It gives you a unified view of your entire attack surface so you can proactively address and manage risk for all of your assets.
Exposure management blog bytes
Exposure management: Reduce risk in the modern attack surface
Many security teams are stuck being reactive and often that’s because their programs are siloed and they have so many tools generating so much data they don’t know what to do with it or what to focus on first.
This blog explores how exposure management can give you the visibility you need to more effectively anticipate threats, prioritize remediation and reduce risk. Read more to learn about how you can use an exposure management platform to unify data from each of your assessment tools and controls so you can clearly see where you have dependencies. The result is the ability to more effectively understand the true nature of where you may be exposed to an attack and its potential impact.

Exposure management: 7 benefits of a platform approach
Traditionally, most security practitioners have used a variety of disparate tools, each specifically designed for only one aspect of the attack surface. For example, one tool for IT, one tool for OT. One tool for cloud. But is that the most effective approach? These tools often silo data in proprietary platforms, making it impossible to get a comprehensive view of every asset and vulnerability across your expansive environment.
This blog looks at the question, what's more effective? Those tools or a consolidated solution? Looking closely at the pros and cons of each, learn more about seven reasons you should consider a comprehensive exposure management platform to replace these point solutions.

How exposure management can make pen testing more effective
How can you get more out of your pen tests and make them more effective? This blog takes a closer look at how an exposure management strategy can enhance your pen tests to improve your cybersecurity posture. For example, with an exposure management platform, you can conduct routine vulnerability scans, instead of waiting on pen test results.
Read this blog to learn more about exposure management benefits and how you can discover all your assets and related vulnerabilities and focus your pen tests on identifying blind spots so you can tighten up your defenses before threat actors take advantage of your exposures.

How to secure your IT, OT and IoT assets with an exposure management platform
Visibility gaps are common across converged IT/OT environments. That's because traditional IT security tools may overlook OT vulnerabilities, while OT security tools may not take into account dependent IT assets.
This blog explores the ramifications of visibility gaps within your OT environment, like for identities, which increases your business and cyber risk. It puts you at greatest risk of potential downtime and disruptions, which could lead to loss of revenue, unsafe working conditions, or, in worse cases, even loss of life. Read this blog to learn more about the holistic value of using an exposure management platform in your converged IT/OT attack surface.

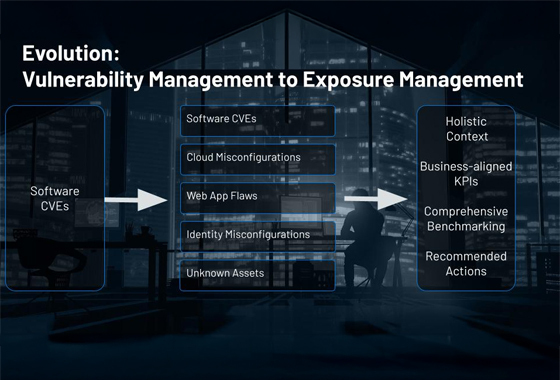
Context is king: From vulnerability management to exposure management
A vulnerability management program is key to proactive cybersecurity strategies; however, most organizations find themselves buried under a mountain of vulnerability data that has little context about real business risk. Without this context, you can't effectively prioritize high-risk exposures across your attack surface.
This blog explores the broader value of an exposure management strategy to overcome common challenges like vulnerability overload and slow remediation response. Read this blog to learn more about how you can shift from a vulnerability management to exposure management mindset, including understanding asset context, the role of identities, and threat context.

Map and close viable attack paths before breaches begin
Hybrid attack paths can easily cross security domains. If you're using point security solutions, that may mean you're overlooking these attack paths. Threat actors hope you do. They're eager to take advantage of your oversights so they can move laterally undetected through your networks.
This blog takes a closer look at lessons learned from real-world attackers and how point tools limit the visibility you need to expose and close security gaps across your attack surface. Read this blog to learn more about recent high-profile attacks and how an exposure management strategy can help your security teams drive better security outcomes.
Exposure management on demand
An adversary’s view of your attack surface
By thinking like an attacker, your security teams will be better poised to proactively secure your attack surface.
This on-demand webinar explores why comprehensive attack surface discovery is challenging for most security teams. Watch it now to learn more about:
- What your enterprise looks like from an attacker's perspective
- Lessons learned from three cyberattacks, including tactics and attack vectors
- How you can enhance your prioritization and remediation strategies with increased cross-team collaboration
How people, process and technology challenges hurt your cybersecurity team
Industry and government security regulations are increasing and becoming more complex. That's making it harder for cybersecurity professionals to keep pace with evolving compliance requirements.
This on-demand webinar explores ways your security teams can optimize their exposure management practices. Watch it now to learn more about:
- Key operational and technological silos that hinder proactive security
- Steps mature organizations take to improve their preventive security strategies and culture
- Recommendations you can quickly implement, regardless of the current maturity of your existing program
The cybersecurity threat landscape: Where are you now?
Your modern attack surface is constantly evolving, which makes it challenging to reduce complexities to protect your business from potential cyber breaches.
This on-demand webinar explores ways you can stay ahead of attackers by first understanding your current security posture. Watch this webinar to learn more about:
- Attack surface visibility challenges
- How to protect your organization from cyber threats
- Exposure management benefits
- How to avoid pitfalls as you navigate evolving security strategies
When it comes to vulnerabilities, “critical” doesn’t always mean “critical...”
The more assets you have across your attack surface, the greater the chance you could overlook vulnerabilities. If you don’t know all the assets you have and their associated vulnerabilities, it rapidly decreases the effectiveness of your patch management processes.
This on-demand webinar explores how to decrease friction between your infosec and IT teams to enhance your cybersecurity posture. Watch this webinar to learn more about:
- What makes a critical vulnerability actually critical
- How common vulnerability scoring systems can impede effective patching
- Why you should close the communication gap between your security, IT and compliance teams
- How to streamline patching to optimize remediation
Proactively identify and address your cyber risk
Many cybersecurity teams struggle with preventing cyberattacks. That’s because they’re often drowning under contextless vulnerability data and don’t have much-needed insight into their attack surface.
That means they often don’t know what needs their attention first or how to fix security issues that may have the greatest impact on their organization.
The most effective modern security teams must evolve from this reactive vulnerability management approach to a proactive exposure management strategy. That begins with breaking down the silos that have prevented security teams from getting the comprehensive attack surface insight they need to stay ahead of cyberattacks.
Know your attack surface
Effective, proactive cybersecurity depends on attack surface visibility. An exposure management platform can give you a unified view of all of your assets across your entire attack surface so you can identify related vulnerabilities, misconfigurations and other security issues. This information is an important part of understanding where you have exposures so you can prioritize and plan what to do about them.
Understand your exposure
It’s important to understand your exposure to make actionable decisions on how to address them. Exposure management can help measure your current security posture and evaluate how well your teams are finding critical flaws and how quickly they can remediate issues that reduce the greatest amount of risk for your organization. By quantifying your exposure, you should be able to answer questions such as, “How secure are we?” and “Where are we with our prevention and mitigation efforts?”.
Visualize attack paths
Risk-based scoring with asset criticality and threat severity reduces noise by a factor of 23:1 and prioritizes remediation based true exposure risk to your business.
Compare risk
Exposure management gives you a business-aligned view of your cyber risk. For example, you can set up KPIs that measure how well your program performs internally over time and benchmark program maturity against industry peers. This will help you align your security program and your organization’s business goals, and improve communication with your executives and key stakeholders.
See Tenable One in action
Get comprehensive visibility into your modern attack surface. Focus efforts to prevent likely attacks. Make data-driven security and business decisions.
- Tenable One








