by Josef Weiss
August 28, 2023
Vulnerability scanning and reporting are essential steps in evaluating and improving the security of a network. This report presents extensive data about detected vulnerabilities, their origin, and mitigation solutions required to remove them. Tenable.io can use this data to help security teams coordinate their risk mitigation efforts more effectively. By providing live discovery and continuous visibility of assets, Tenable.io helps teams accurately represent and communicate cyber risk to the business.
The information in this report is first summarized by host and severity to give a condensed snapshot of an organization’s attack surface. This glance at the current state of assets provides a solid overview for mitigation planning. Knowing which assets pose the greatest risk enables the establishment of vulnerability mitigation efforts to efficiently reduce that risk.
Understanding vulnerabilities in exact detail is important for both knowing how to mitigate risk and understanding how assets can be exploited. The detailed list presented in this report gives exact detail on vulnerabilities including how they were discovered, what about them is publicly known, and how to mitigate them. Each asset can be assessed and addressed using this detailed vulnerability information when planning risk mitigation.
Cyber Exposure helps analysts drive a new level of dialogue with the business. By knowing which areas of the business are secure or exposed, analysts can effectively measure the organization's cyber risk. Analysts can use the metrics provided by Tenable.io to determine how much and where to invest in order to reduce risk to an acceptable amount. Tenable.io is the first Cyber Exposure solution that provides key risk metrics that organizations need to measure risk exposure.
Chapters
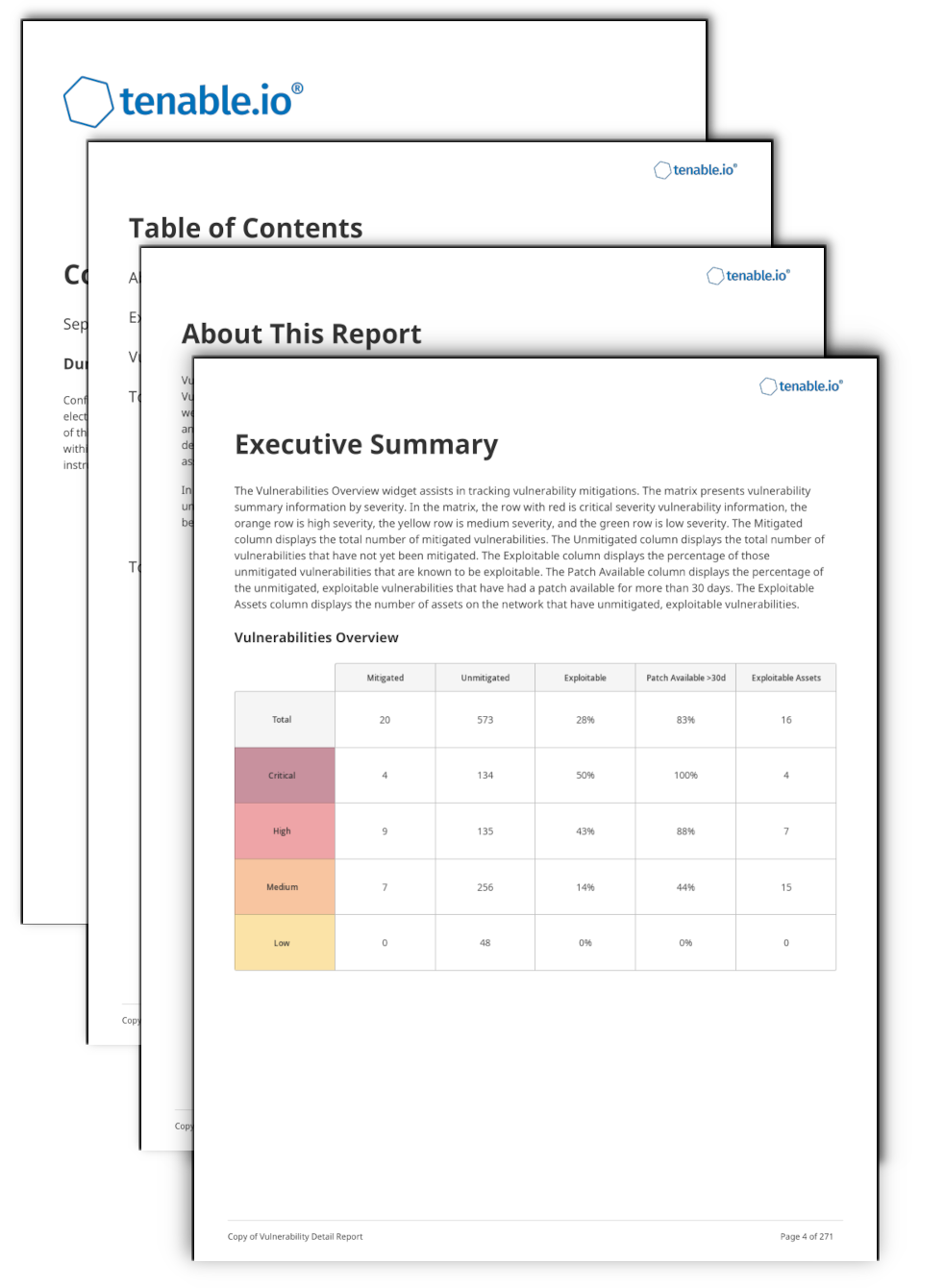
Executive Summary - This chapter offers a look at the assets that pose the greatest risk, and a look at the number of assets with severe vulnerabilities. This information can be used as a starting point when identifying areas of risk by displaying the assets that require the most attention. Assets presented at the top of this summary have the greatest impact on risk reduction.
Vulnerabilities Overview Highlighting Mitigations - This chapter provides tables of the top 100 fixed, resurfaced and active vulnerabilities. This information highlights mitigation progress and gives further details on the vulnerabilities, including the total number of assets on which a vulnerability was detected.
Top Most Vulnerable Assets - This chapter provides more details on the top most vulnerable assets at risk for exploitation. The initial table displays the top 100 assets, with the most vulnerable asset at the top. Assets with high or critical severity vulnerabilities that are also exploitable are shown, sorted by total vulnerabilities. Following the table, additional details are provided for each of the 100 assets, including a table of 25 of the critical exploitable vulnerabilities found on each asset.
Top Exploitable Vulnerabilities - This chapter contains two sections: Critical Exploitable Vulnerabilities This section provides more details on the top critical exploitable vulnerabilities detected on the network. These vulnerabilities are dangerous because they are critical severity and are known to be exploitable. Tenable recommends prioritizing remediation of these critical vulnerabilities. The second section, Critical Exploitable Vulnerabilities with Patches Available Over 30 Days, This section provides more details on the top critical exploitable vulnerabilities detected on the network. The vulnerabilities noted in this section have already had a patch available for more than 30 days. Tenable recommends prioritizing remediation of these critical vulnerabilities.