Critical 'BlueKeep' Vulnerability CVE-2019-0708 Addressed in Patch Tuesday Updates

Microsoft has released its May 2019 Security Updates, which includes a fix for BlueKeep (CVE-2019-0708), a critical remote code execution vulnerability affecting the Remote Desktop Service.
Background
Microsoft has released its monthly security update for May. Included in this month's Patch Tuesday release is CVE-2019-0708, titled BlueKeep, a critical remote code execution vulnerability that could allow an unauthenticated remote attacker to execute remote code on a vulnerable target running Remote Desktop Protocol (RDP).
Analysis
The vulnerability exists in the way that the RDP service handles incoming requests. An attacker can send a malicious request to the RDP service and, due to improperly sanitized request handling, the target will execute the malicious code injected into the request. CVE-2019-0708 is a pre-authentication vulnerability that requires no user interaction, which would result in attacks exploiting it to spread in a manner similar to WannaCry. While there isn’t any public proof-of-concept (PoC) or exploit script code available at this time, we anticipate that won’t be the case for long.
Nearly 80 days after the announcement of BlueKeep, threats of exploitation remain. Learn more here.
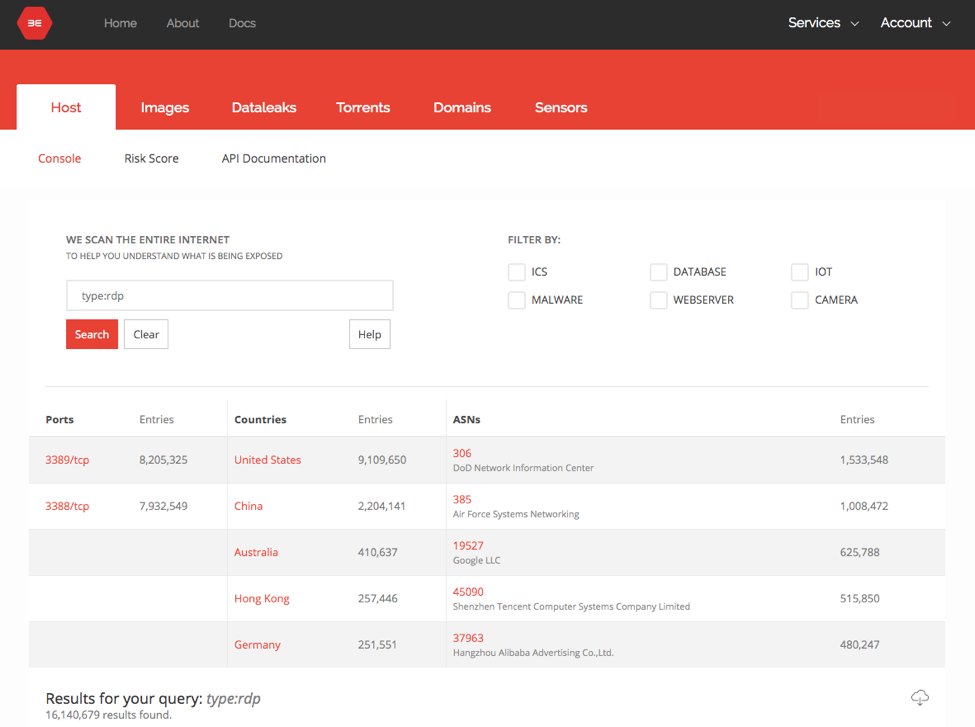
This vulnerability provides attackers with a common attack vector that many internet-facing Windows assets are likely to have running. Shodan and Binary Edge searches both show millions of internet-facing assets with actively listening RDP services.
Solution
Tenable recommends applying the full May 2019 Security Update from Microsoft for all vulnerable assets. For CVE-2019-0708, Microsoft has provided updates for Windows 7, Windows Server 2008 and Windows Server 2008 R2. Additionally, Microsoft has provided patches for out-of-support systems, including Windows XP, Windows XP Professional, Windows XP Embedded and Windows Server 2003.
Affected systems that have Network Level Authentication (NLA) enabled aren’t vulnerable to unauthenticated attack, but If an attacker has valid credentials this vulnerability is still exploitable.
Identifying affected systems
For identifying systems without NLA enabled, please use plugin 58453.
A list of Nessus plugins to identify these vulnerabilities will appear here as they’re released.
Our remote checks for CVE-2019-0708 can be found here.
Get more information
- May Patch Tuesday Information
- Microsoft's CVE-2019-0708 Advisory Page
- Security Only Update for CVE-2019-0708
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning


