Cybersecurity Snapshot: CSA Outlines Data Security Challenges and Best Practices, While ISACA Offers Tips To Retain IT Pros

Check out best practices for shoring up data security and reducing cyber risk. Plus, get tips on how to improve job satisfaction among tech staff. Meanwhile, find out why Congress wants federal contractors to adopt vulnerability disclosure programs. And get the latest on cyber scams; zero-day vulnerabilities; and critical infrastructure security.
Dive into six things that are top of mind for the week ending March 7.
1 - CSA: How to boost data security and reduce cyber risk
Risk assessment gaps. Siloed cyber tools. Misaligned priorities.
Those are some of the critical challenges that threaten data security in many enterprises today, according to the new Cloud Security Alliance report “Understanding Data Security Risk,” for which about 900 IT and security professionals were surveyed.
Here’s a high-level view of data-security obstacles faced by respondents and of CSA’s mitigation recommendations.
- Inability to effectively flag vulnerabilities and prioritize their remediation across hybrid and cloud environments
Recommendations include adopting tools that offer actionable insights into data risks by leveraging multiple risk indicators.
- Discordant priorities, as executives want to align data security with business goals, but fail to give cyber operations teams the resources they need
Recommendations include proactively improving communication and collaboration between these two camps to match cyber investments with data-security goals.

- Failure from siloed, heterogeneous tools to provide the visibility needed for proactive data security
Recommendations include adopting unified platforms for security, compliance and risk management.
- Data risk-management strategies driven by regulation compliance, creating gaps for addressing emerging threats
Recommendations include adopting proactive risk management, including vulnerability management, real-time monitoring and advanced threat detection.
For more information about data security, check out these Tenable resources:
- “The value of data security integrated into a unified cloud security strategy” (infographic)
- “Harden Your Cloud Security Posture by Protecting Your Cloud Data and AI Resources” (blog)
- “Know Your Exposure: Is Your Cloud Data Secure in the Age of AI?” (on-demand webinar)
- “Securing Financial Data in the Cloud: How Tenable Can Help” (blog)
- “Data Security in Healthcare: How Tenable Cloud Security Can Help” (blog)
2 - ISACA: Orgs struggle to retain IT pros
One-third of IT professionals switched jobs in the past two years, a churn rate that has caused almost 75% of organizations to be concerned about recruiting and retaining tech employees.
Those stats come from ISACA’s “Tech Workplace and Culture 2025” report, which is based on a survey of about 7,700 of its members who work in IT areas such as information security, governance, assurance, data privacy and risk management.
“A robust and engaged tech workforce is essential to keeping enterprises operating at the highest level,” Julia Kanouse, ISACA’s Chief Membership Officer, said in a statement this week.
Among the 71% of respondents who reported job-related stress, the top culprits were heavy workloads, long hours, tight deadlines, insufficient resources and unsupportive management.
When asked their main reasons for changing jobs, respondents cited wanting better compensation; improving their career prospects; and doing more interesting work.
So what can organizations do to attract and retain tech talent? They should focus on the factors that encourage tech employees to stay at their jobs. For example, respondents ranked work-life balance; hybrid / remote work options; and interesting and enjoyable work as top factors for job satisfaction.
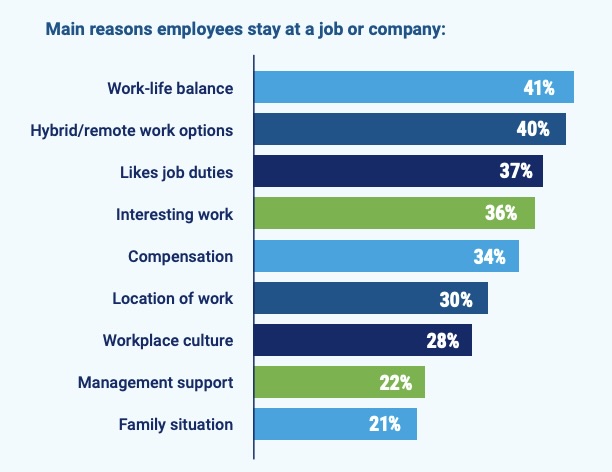
(Source: ISACA’s “Tech Workplace and Culture 2025” report, March 2025)
For more information about recruiting and retaining cybersecurity professionals:
- “10 Ways to Boost Cybersecurity Talent Retention” (InformationWeek)
- “60% of cybersecurity pros looking to change employers” (CSO)
- “The cybersecurity industry has an urgent talent shortage. Here’s how to plug the gap” (World Economic Forum)
- “Beyond the paycheck: What cybersecurity professionals really want” (CSO)
- “Cybersecurity Pros are Well-Paid But Dissatisfied, Study Finds” (MSSP Alert)
3 - ENISA assesses cyber maturity of EU critical infrastructure sectors
Electricity, telecoms and banking are among the EU’s most cyber mature critical infrastructure sectors, while laggards include health and public administration.
That’s according to the “ENISA NIS360 2024” report published this week by the European Union Agency for Cybersecurity, better known as ENISA.
The “ENISA NIS 360” report also provides recommendations for boosting the cyber maturity of the EU’s critical infrastructure sectors, as defined by the EU’s NIS2 regulation.
NIS2, the acronym for the Network and Information Systems Directive, outlines cybersecurity requirements for EU critical infrastructure organizations and digital service providers.
While the cyber maturity of the EU’s critical infrastructure sector varies, the report concludes that all of them have room for improvement.
“Overall, all sectors covered by the NIS360 face challenges in building their maturity and meeting NIS2 requirements,” the report reads.

Here are a couple of high-level ENISA recommendations for EU member states and national authorities:
- Foster stronger cybersecurity collaboration among critical infrastructure organizations both within and outside their sectors, and across borders.
- Offer sector-specific guidance for complying with NIS2, and focus on helping cybersecurity staffers expand their cyber risk-management skills.
Some sector-specific recommendations include:
- The space sector, which suffers from limited cyber knowledge and overreliance on commercial off-the-shelf products, must invest in boosting its cyber awareness and seek guidelines for testing pre-integrated components.
- The public administration sector, which is very diverse and a prime target for hacktivists and nation-state attackers, should beef up its cyber capabilities by seeking shared service models with fellow public agencies, in areas such as digital wallets.
- The maritime sector, which is hampered by outdated operational technology (OT) systems, should adopt proactive vulnerability management and secure-by-design principles.
“The ENISA NIS360 gives valuable insight into the overall maturity of NIS sectors and the challenges of individual sectors. It explains where we stand, and how to move forward,” Juhan Lepassaar, EU Agency for Cybersecurity Executive Director, said in a statement.
For more information about critical infrastructure and OT systems cybersecurity, check out these Tenable resources:
- “What is operational technology (OT)?” (guide)
- “Discover, Measure, and Minimize the Risk Posed by Your Interconnected IT/OT/IoT Environments” (on-demand webinar)
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “OT Security Master Class: Understanding the Key Principles, Challenges, and Solutions” (on-demand webinar)
4 - FBI: Scammers deliver ransomware threats via snail mail
Executives are receving letters via regular mail saying their business has been compromised by ransomware and demanding they pay a ransom of up to $500,000 within 10 days.
The scammers claim that the BianLian ransomware group swiped troves of data files from the recipient’s network, and instruct recipients to transfer the ransom money into a Bitcoin wallet using a QR code included in the letter.

Anyone receiving those letters should disregard them because they’re a scam, the U.S. Federal Bureau of Investigation (FBI) warned this week.
“We have not yet identified any connections between the senders and the widely-publicized BianLian ransomware and data extortion group,” reads the FBI’s advisory titled “Mail Scam Targeting Corporate Executives Claims Ties to Ransomware.”
The FBI further recommends that targeted executives do the following:
- Notify fellow executives in the organization about the scam so that they’re aware.
- Educate employees about proper procedures for responding to a ransom threat.
- Have the cybersecurity team double-check all network defenses are up-to-date and that there’s no ongoing malicious activity.
For more information about cybercrime and cyber scams:
- “It’s ‘never been easier’ to become an online scammer as cybercrime markets flourish, security experts warn” (CNBC)
- “How AI-driven fraud challenges the global economy – and ways to combat it” (World Economic Forum)
- “2025 Crypto Crime Trends: Illicit Volumes Portend Record Year as On-Chain Crime Becomes Increasingly Diverse and Professionalized” (Chainalysis)
- “The Biggest Online Scams to Watch for in 2025—And How to Avoid Them” (PCMag)
- “Get ready for these scams in 2025” (Mashable)
5 - U.S. House passes vulnerability disclosure bill
The U.S. House of Representatives passed a bill this week that would make it a requirement for federal government contractors to have a vulnerability disclosure policy.
The “Federal Contractor Cybersecurity Vulnerability Reduction Act of 2025” would require that contractors hired by federal agencies implement a vulnerability disclosure program in accordance with guidelines from the National Institute of Standards and Technology (NIST).
The goal is to ensure that federal contractors promptly disclose potential security vulnerabilities impacting information systems they either own or control.

Representatives Nancy Mace (R-SC) and Shontel Brown (D-OH) introduced the bill, which now goes to the U.S. Senate.
In a letter last week, various tech vendors including Tenable expressed support for the bill, calling it “important legislation” for boosting the federal government’s cyber resilience by requiring contractors to have a “structured process” for receiving and addressing security vulnerabilities.
“Contractors, given the vast amount of sensitive data they handle, are prime targets for cyber threats. As a result, the bill ensures all companies contracting with the federal government adhere to security best practices,” the letter reads.
In addition to Tenable, the other signatories were Bugcrowd, HackerOne, Infoblox, Microsoft, Rapid7, Schneider Electric and Trend Micro.
For more information about vulnerability disclosure programs:
- “What is vulnerability disclosure?” (TechTarget)
- “Vulnerability disclosure programs explained” (Australian Cyber Security Centre)
- “Vulnerability Disclosure Toolkit” (U.K. National Cyber Security Centre)
- “Developing National Vulnerabilities Programmes” (ENISA)
6 - Attackers exploit zero-day vulns in VMware products
VMware parent company Broadcom this week issued an advisory about zero-day vulnerabilities impacting VMware products that were observed being exploited in the wild.
The products in question are VMware ESXi, Workstation and Fusion, and organizations are advised to apply the available patches for the three vulnerabilities: CVE-2025-22224, CVE-2025-22225 and CVE-2025-22226.
To get all the details, check out the blog “CVE-2025-22224, CVE-2025-22225, CVE-2025-22226: Zero-Day Vulnerabilities in VMware ESXi, Workstation and Fusion Exploited” from the Tenable Security Response Team.
- Cloud
- Exposure Management
- Industrial Control Systems Monitoring
- IT/OT
- Risk-based Vulnerability Management
- Cloud
- Cybersecurity Snapshot
- Federal
- Government
- OT Security
- Risk-based Vulnerability Management


